Simple Explanation:
Snort is an open-source intrusion detection system based on real-time network traffic analysis and packet logging.
Official documentation: https://www.snort.org/documents
Check the official documentation "Snort 2.9.8.x on CentOS 6.x and 7.x".
Deploy and test by cloning a test machine based on "CentOS6 Experimental Machine Template Deployment".
In testing, the official Snort setup guide was found to be poorly written. This experiment involved installing Snort using the official documentation, during which some issues were encountered. This blog post serves as a record of the experiment. A subsequent post will be published as a report on a reattempt, using insights from other blogs, akin to setting up an intrusion detection system with snort+barnyard2+base.
Experimental Process:
1° Add EPEL repository and install system packages
yum -y install epel-release
yum -y install gcc flex bison tcpdump \
zlib zlib-devel libpcap libpcap-devel \
pcre pcre-devel libdnet libdnet-devel
# Also need the libdnet-debuginfo package, which can be found on the rpmfind website
axel https://www.rpmfind.net/linux/epel/6/x86_64/debug/Packages/l/libdnet-debuginfo-1.12-6.el6.x86_64.rpm
yum -y localinstall libdnet-debuginfo-1.12-6.el6.x86_64.rpm2° Download the source packages from the official website and install
cd /tmp
wget https://www.snort.org/downloads/snort/daq-2.0.6.tar.gz
wget https://www.snort.org/downloads/snort/snort-2.9.11.1.tar.gz
cd /usr/local/src
tar -xf /tmp/daq-2.0.6.tar.gz
cd daq-2.0.6./configure
make && sudo make install
cd /usr/local/lib
ldconfig -v /usr/local/lib
cd /usr/local/src
tar -xf /tmp/snort-2.9.11.1.tar.gz
cd snort-2.9.11.1./configure --enable-sourcefire
make && sudo make install
cd /usr/local/lib
ldconfig -v /usr/local/lib3° Register an official account, log in using the account, and download rule sets or VRT rules. Log in at https://www.snort.org, click Sign in, then Sign up to register, and check Snort-users 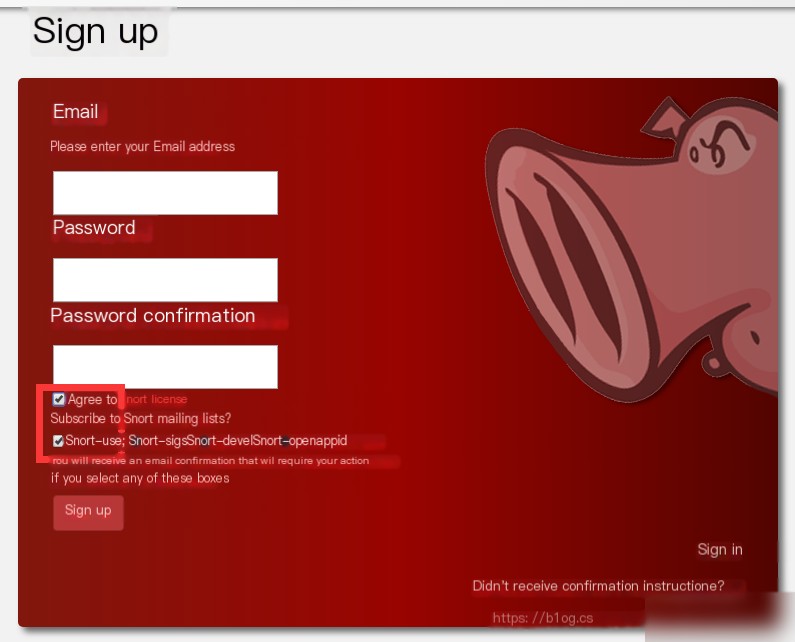
According to the email, open the link 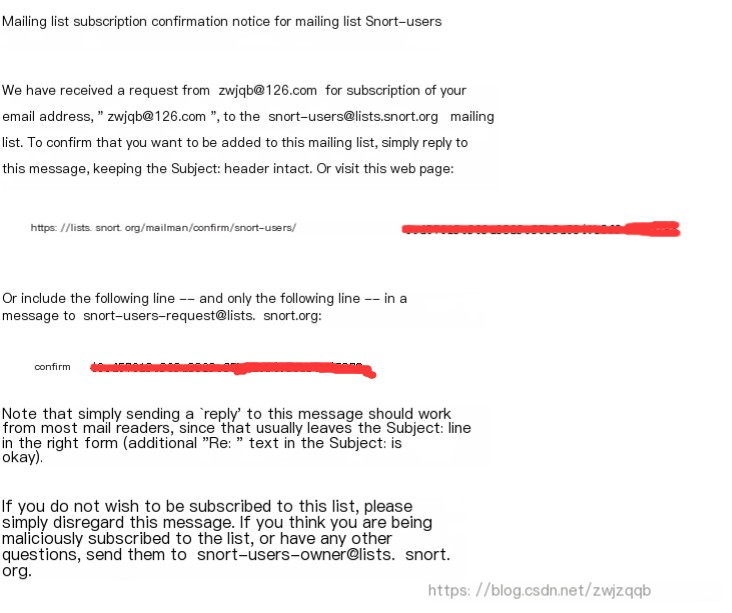
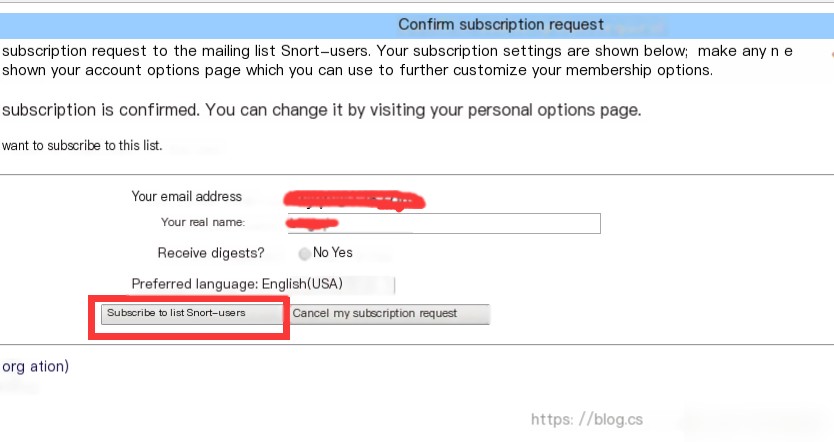
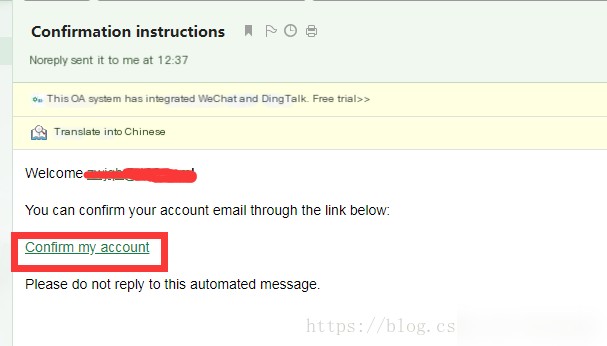
Download rule package https://www.snort.org/downloads Download snortrules-snapshot-29111.tar.gz
4° Import the downloaded rule package
cd /etc
mkdir -p snort
cd snort
cp -av /usr/local/src/snort-2.9.11.1/etc/* .
tar -xf /tmp/snortrules-snapshot-29111.tar.gz
cp ./etc/* .
touch /etc/snort/rules/white_list.rules
touch /etc/snort/rules/black_list.rules5° Add system user
groupadd -g40000 snort
useradd -u40000-d /var/log/snort -s /sbin/nologin -c SNORT_IDS -g snort snort
cd /etc/snort
chown -R snort:snort *
chown -R snort:snort /var/log/snort6° Edit configuration file /etc/snort/snort.conf
# Assume monitored subnet is 192.168.77.0/24
NET='192.168.77.0/24'
sed -i 's|^\(var RULE_PATH\).*|\1 /etc/snort/rules|g' /etc/snort/snort.conf
sed -i "s|^\(ipvar HOME_NET\).*|\1 ${NET}|g" /etc/snort/snort.conf
sed -i 's|^\(ipvar EXTERNAL_NET\).*|\1 !$HOME_NET|g' /etc/snort/snort.conf
sed -i 's|^\(var SO_RULE_PATH\).*|\1 /etc/snort/so_rules|g' /etc/snort/snort.conf
sed -i 's|^\(var PREPROC_RULE_PATH\).*|\1 /etc/snort/preproc_rules|g' /etc/snort/snort.conf
sed -i 's|^\(var WHITE_LIST_PATH\).*|\1 /etc/snort/rules|g' /etc/snort/snort.conf
sed -i 's|^\(var BLACK_LIST_PATH\).*|\1 /etc/snort/rules|g' /etc/snort/snort.conf7° Change permissions
cd /usr/local/src
chown -R snort:snort daq-2.0.6chmod -R 700 daq-2.0.6chown -R snort:snort snort-2.9.11.1chmod -R 700 snort-2.9.11.1chown -R snort:snort snort_dynamicsrc
chmod -R 700 snort_dynamicsrc8° Add a system-managed startup script
# Official website https://www.snort.org/documents# Download Snort Startup Script for CentOS
chmod +x /etc/init.d/snort
chkconfig --add snort
chkconfig snort on9° Create symlinks
cd /usr/sbin
ln -s /usr/local/bin/snort snort10° Create configuration file
vi /etc/sysconfig/snort
# /etc/sysconfig/snort# $Id: snort.sysconfig,v 1.8 2003/09/19 05:18:12 dwittenb Exp $#### General ConfigurationINTERFACE=eth0
CONF=/etc/snort/snort.conf
USER=snort
GROUP=snort
PASS_FIRST=0
#### Logging & AlertingLOGDIR=/var/log/snort
ALERTMODE=fast
DUMP_APP=1
BINARY_LOG=1
NO_PACKET_LOG=0
PRINT_INTERFACE=0
chown snort: /etc/sysconfig/snort
chmod 700 /etc/sysconfig/snort11° Create /var/log/snort if it doesn’t exist:
cd /var/logmkdir snort
chmod700 snort
chown -R snort:snort snort
# Change permissions
cd /usr/local/lib
chown -R snort:snort snort*
chown -R snort:snort snort_dynamic*
chown -R snort:snort pkgconfig
chmod -R 700 snort*
chmod -R 700 pkgconfig
cd /usr/local/bin
chown -R snort:snort daq-modules-config
chown -R snort:snort u2*
chmod -R 700 daq-modules-config
chmod700 u2*
cd /etc
chown -R snort:snort snort
chmod -R 700 snort12° Create dynamic rule directory
mkdir -p /usr/local/lib/snort_dynamicrules
chown -R snort:snort /usr/local/lib/snort_dynamicrules
chmod -R 700 /usr/local/lib/snort_dynamicrules
# The official documentation mentions importing some dynamic rules, unclear reasons# Effective lines in /etc/snort/snort.conf must end with a backslash# This configuration file contains many such erroneous lines
sed -i 's/[^\\]$/ \\/g' /etc/snort/snort.conf13° Start test mode for testing
cd /usr/local/bin
./snort -T -i eth0 -u snort -g snort -c /etc/snort/snort.conf
# Successful test output:# Snort successfully validated the configuration!# Snort exiting# Refer to official documentation for other errors14° Manually start and monitor
snort -A fast -b-d-D-i eth0 -u snort -g snort \-c /etc/snort/snort.conf -l /var/log/snort
tailf /var/log/messages15° Upgrade suggestions
# If upgrading Snort, it's strongly recommended to back up the following configuration files:
local.rules
snort.conf
threshold.conf
white_list.rules
black_list.rules[TOC]


