The installation and configuration of Snort are covered by other forums like CSDN. In this intrusion detection guide, I’ll discuss the issues I encountered during the installation and configuration.
This guide is only meant for students performing related experiments while learning intrusion detection. There’s no guarantee it will successfully detect certain attacks (though it will detect nmap’s port scanning if configured correctly). Please be advised.
Configuration environment: Windows 7 SP1, Snort 2.9.16 1. Snort 2.9 used with WinPcap 4.1.3 is verified to work. If the DAQ version prompts an issue, it’s not necessary to worry. Additionally, as WinPcap 4.1.3 is no longer updated, you may theoretically opt for npcap (as guided by nmap’s official site), but it seems Snort 2.9 does not configure well with it, as Snort -W can’t locate the network card. If anyone has succeeded, please leave a comment. Thank you.
2. Snort does not have a GUI interface; all operations are completely reliant on CMD (the terminal). After downloading the installation package from the official website and completing the installation, remember to download the related rules package. The community version’s rules package is incomplete, so it’s advisable to register for a Snort account to download the full version (though other sites may offer downloads, they might not be updated). The rules package I used is snortrules-snapshot-2900.tar.gz. After installing Snort itself, extract the rules package to the Snort root directory, and overwrite all the prompted files. 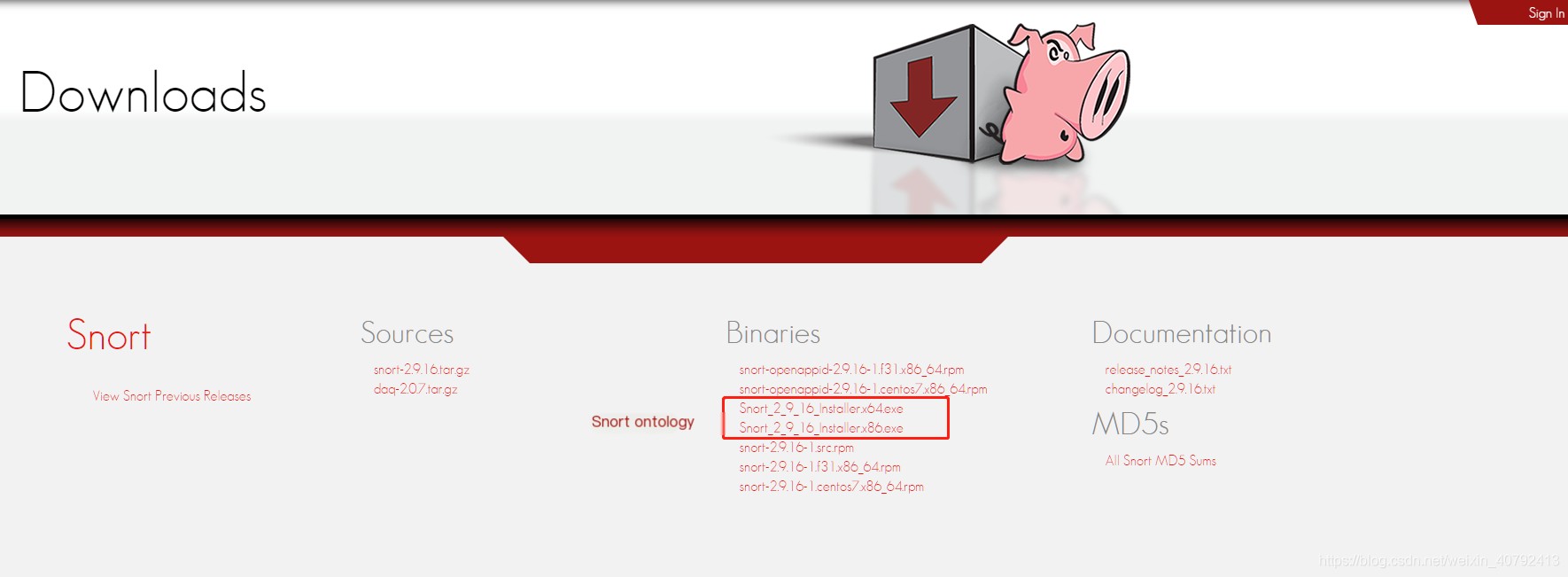
 3. After completing the installation of Snort and WinPcap, first use CMD to navigate to the Snort directory (if default installation, it’s C:/Snort/bin). Use the cd command to locate the folder, then use the Snort -W command to check if the installation is complete, and see if you can view your network card’s MAC address. Usually, if WinPcap is installed correctly, it will be visible.
3. After completing the installation of Snort and WinPcap, first use CMD to navigate to the Snort directory (if default installation, it’s C:/Snort/bin). Use the cd command to locate the folder, then use the Snort -W command to check if the installation is complete, and see if you can view your network card’s MAC address. Usually, if WinPcap is installed correctly, it will be visible. 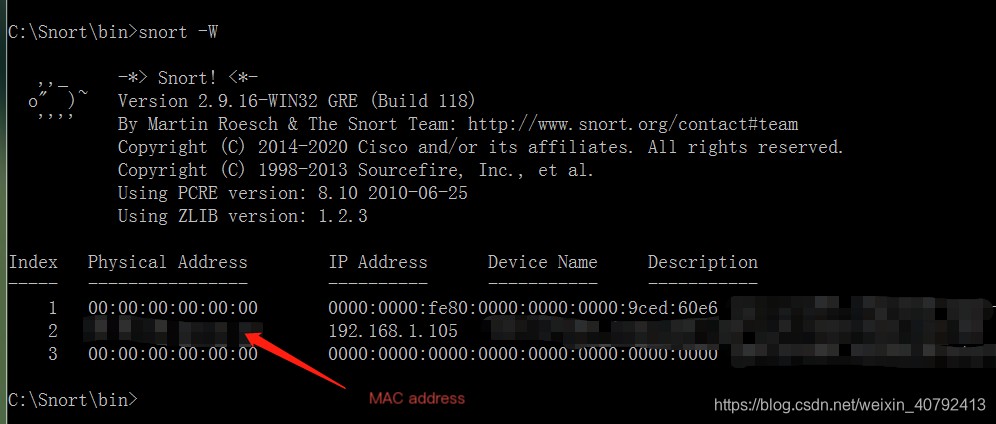 4. Now begins the process of configuring snort.conf. I suspect Snort was originally designed for systems like Linux, hence all paths in snort.conf use relative paths. In Windows, these relative paths need to be changed to absolute paths. Below are some key modifications:
4. Now begins the process of configuring snort.conf. I suspect Snort was originally designed for systems like Linux, hence all paths in snort.conf use relative paths. In Windows, these relative paths need to be changed to absolute paths. Below are some key modifications: 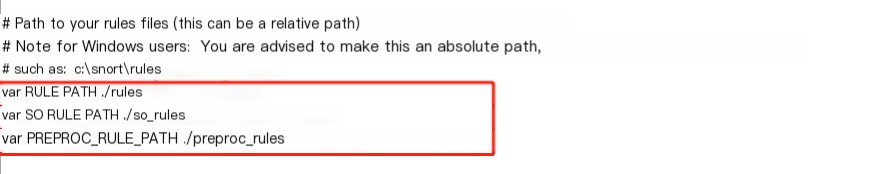
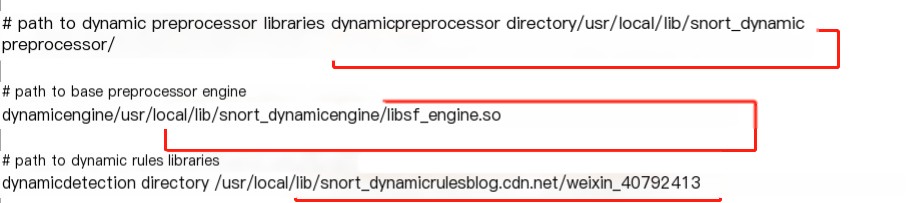 Note that the third dynamicdetection directory might not exist after extracting some rules packages, so first create a folder with the same name under lib, then copy all files from C:\Snort\so_rules\precompiled\FC-9\i386\2.9.0.1 to C:\Snort\lib\snort_dynamicrules. This may not always work. If it doesn’t produce an error here, then it’s fine.
Note that the third dynamicdetection directory might not exist after extracting some rules packages, so first create a folder with the same name under lib, then copy all files from C:\Snort\so_rules\precompiled\FC-9\i386\2.9.0.1 to C:\Snort\lib\snort_dynamicrules. This may not always work. If it doesn’t produce an error here, then it’s fine. 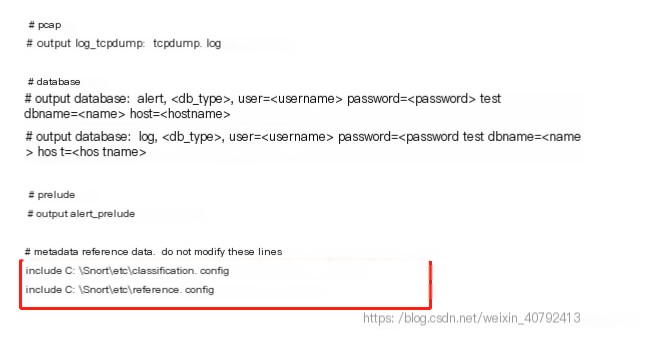
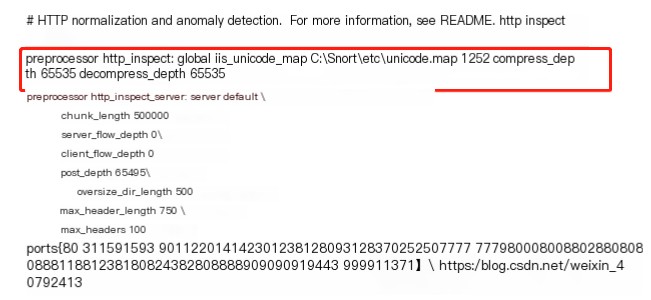 These are roughly the locations where path modifications are needed. Other sections (like the rules library) may also require path modifications but do not significantly affect the experiment, so I left them alone. After doing all this, you can say Snort is basically configured, but there will still be many issues during operation for various reasons. Here’s the simplest method: adding comments.
These are roughly the locations where path modifications are needed. Other sections (like the rules library) may also require path modifications but do not significantly affect the experiment, so I left them alone. After doing all this, you can say Snort is basically configured, but there will still be many issues during operation for various reasons. Here’s the simplest method: adding comments.
Adding comments can solve 50% of the problems. Of course, you can overdo it with comments, like this: 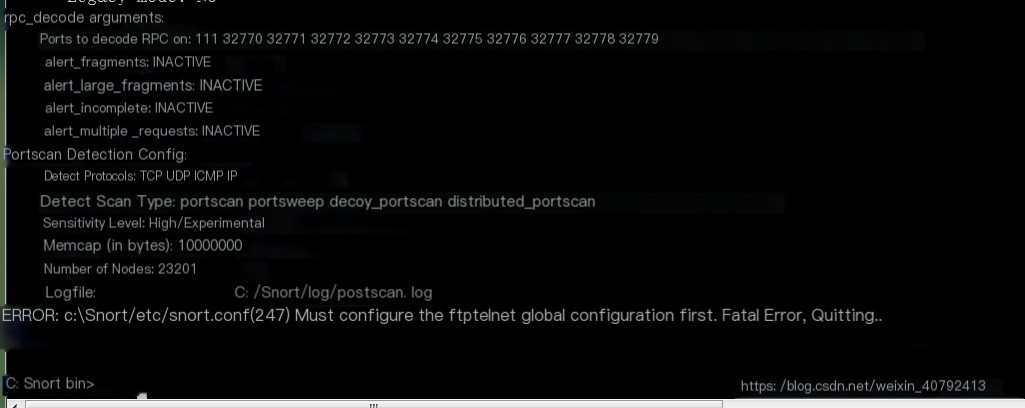 This is overdoing it. Some prerequisites are needed (like declaring variables), but if they’re commented out, errors will occur, so remove the comments and troubleshoot. The red box in the image indicates the line number of the error in the conf, which can be used for troubleshooting.
This is overdoing it. Some prerequisites are needed (like declaring variables), but if they’re commented out, errors will occur, so remove the comments and troubleshoot. The red box in the image indicates the line number of the error in the conf, which can be used for troubleshooting.
Other problem summaries: 1. In some cases, errors in the snort.conf file may be due to space issues. You can add or remove spaces in some assignments, like this segment: 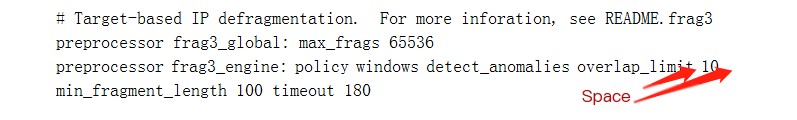 2. Some commands require position adjustment and absolute paths, for instance, the command snort -i3 -dev -l./log -h 192.168.1.0/24 -K ascii -c c:\Snort/etc/snort.conf will give an error. One issue is the position of -i3, and another is that an absolute path is needed after the -l command. It can be modified to snort -dev -i3 -l C:/Snort/log -h 192.168.1.0/24 -K ascii -c c:\Snort/etc/snort.conf
2. Some commands require position adjustment and absolute paths, for instance, the command snort -i3 -dev -l./log -h 192.168.1.0/24 -K ascii -c c:\Snort/etc/snort.conf will give an error. One issue is the position of -i3, and another is that an absolute path is needed after the -l command. It can be modified to snort -dev -i3 -l C:/Snort/log -h 192.168.1.0/24 -K ascii -c c:\Snort/etc/snort.conf
3. alert.ids error. Sometimes, you’ll encounter an error stating alert.ids cannot be found, which may be a software bug. My solution is to create a blank text file, rename it to alert.ids, and bypass this error.
4. Occasionally, reports say the generated portscan.log is empty. You can try running nmap -sS again.
5. I previously encountered an error with too many parameters, and there was no solution on the nmap forum. I resolved it by adding a few spaces. This is for reference only.
In conclusion, just like when we first learned C language and writing a “Hello, World!” program led to many errors, installing Snort is similar. It’s a slow process of troubleshooting and researching to resolve issues. I hope this blog post can help you, and for any other issues, feel free to leave comments.
2020.06.15 Update: https://download.csdn.net/download/weixin_40792413/12524662 I have uploaded a conf file, a lib, and a blank alert.ids. You can download them for reference.
2020.06.15


