Our SIEM triggered an alert, and the AV blocked malware from running on an employee’s machine. To further investigate, the incident response team quickly acquired an image of the machine. Their task is to identify the entry point of the attack and trace the attacker to determine how the malware infiltrated the machine.
Challenge Link
https://app.letsdefend.io/challenge/discord-forensics
What is the attacker’s name?
Hint: Check the received job invitation email. Directly search for files with the .eml extension to locate the email files.
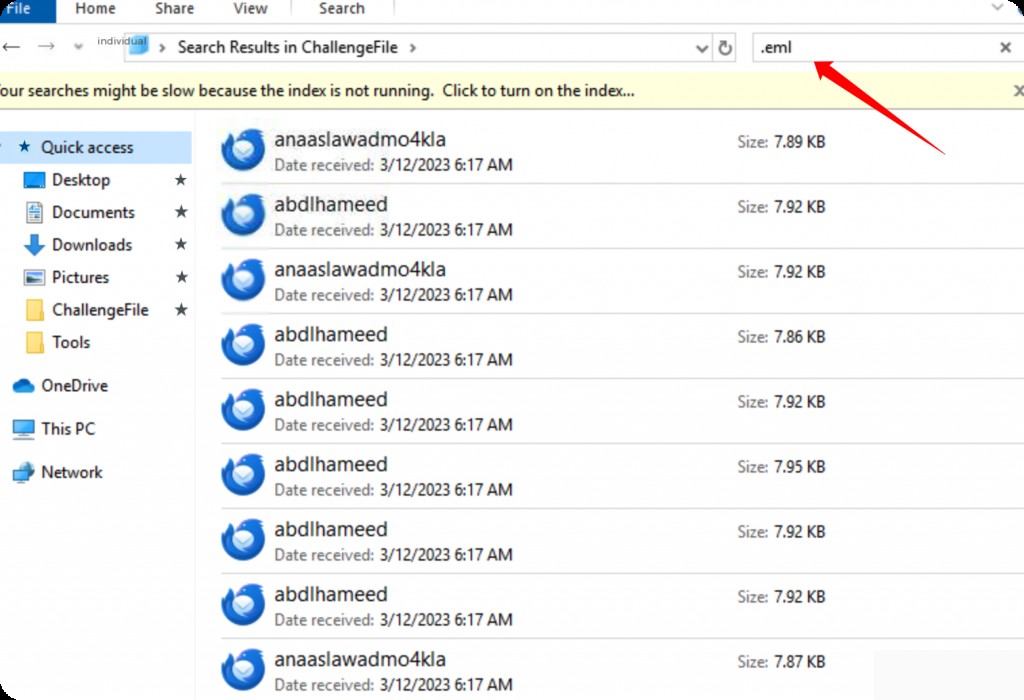
View all the .eml files.
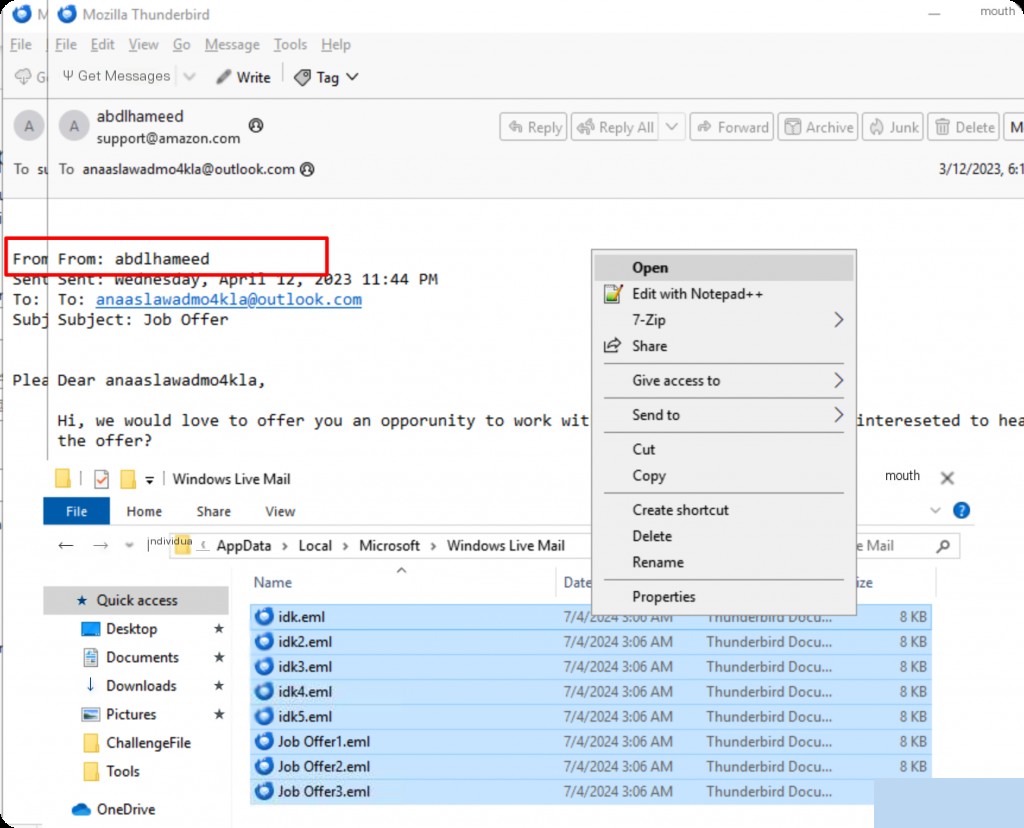
What is the communication program and username?
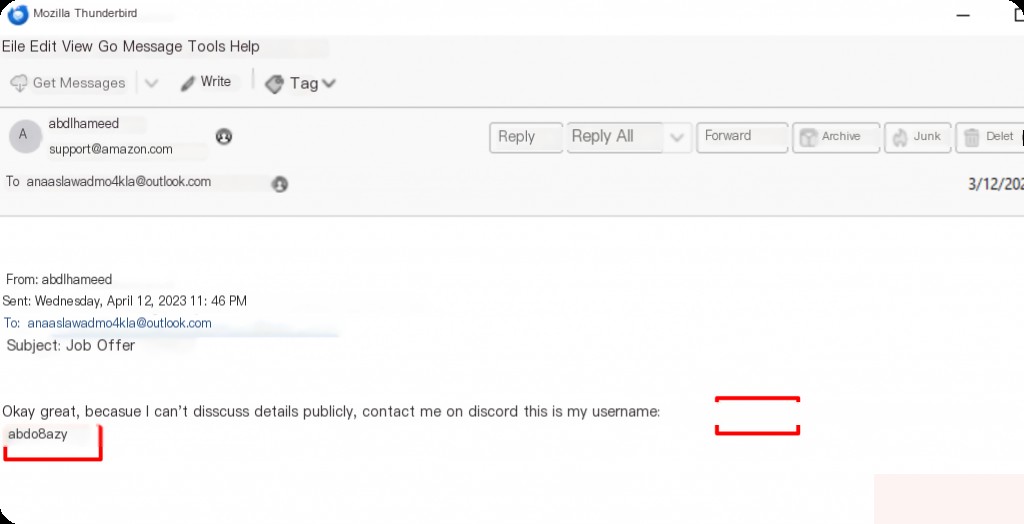
When did the attacker send the first message to the victim through the application?
It has been confirmed from the email that Discord was used for communication, leading to Discord forensics.
The Discord client is developed based on Electron.
Electron is a framework for building desktop applications using JavaScript, HTML, and CSS. Embedding Chromium and Node.js into Electron binaries allows you to maintain a single JavaScript codebase and create cross-platform applications that run on Windows, macOS, and Linux—without requiring native development experience.
Essentially, Discord is a web application embedded in the Chromium browser. Therefore, Discord forensics is essentially browser forensics.
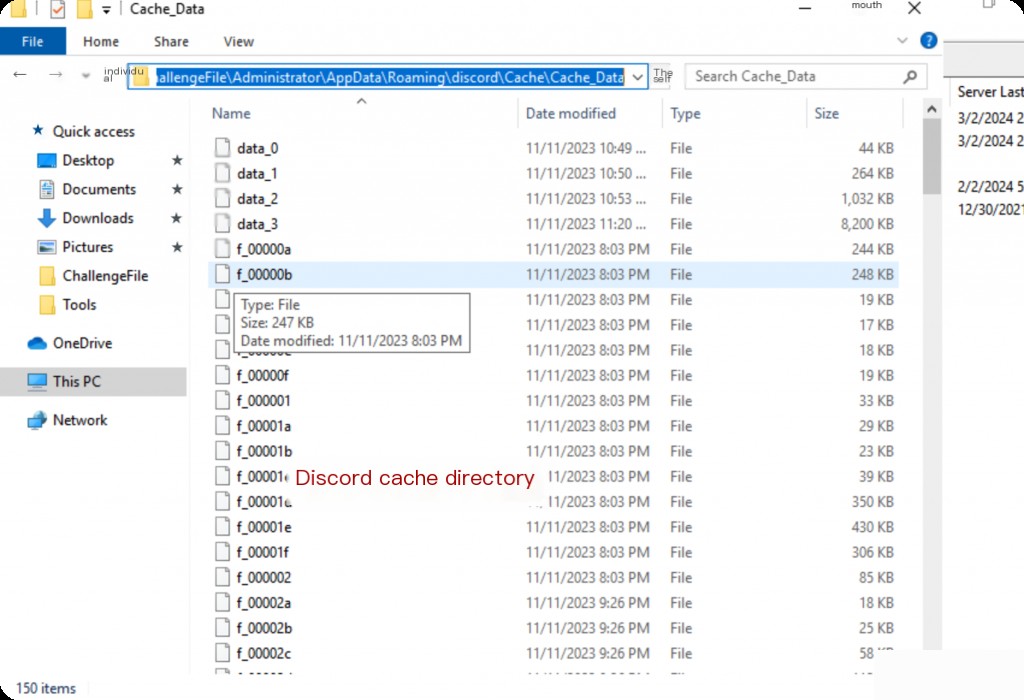
Use ChromeCacheView.exe to open the Discord cache directory.
C:\Users\LetsDefend\Desktop\ChallengeFile\Administrator\AppData\Roaming\discord\Cache\Cache_Data
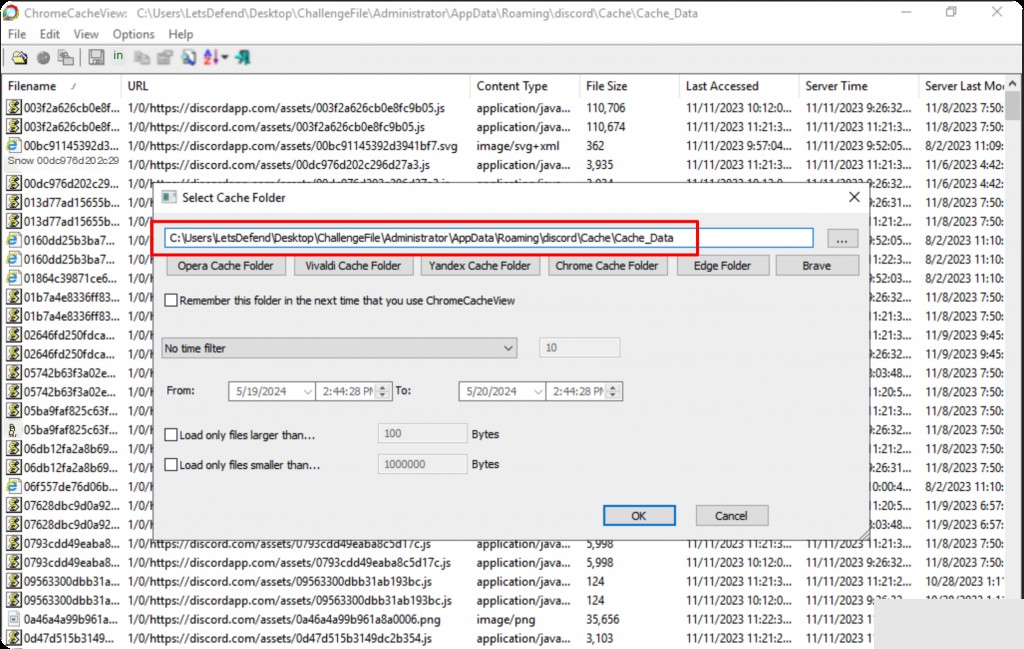
There are too many files, match keywords related to messages.
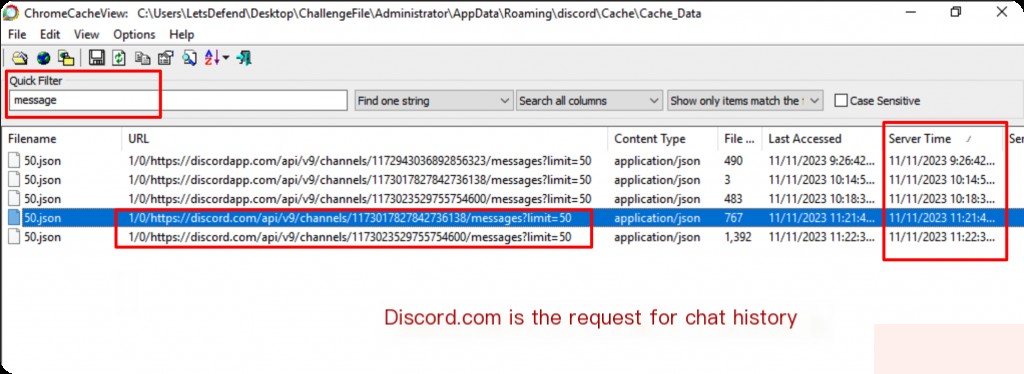
Open the 50.json file with a size of 767.
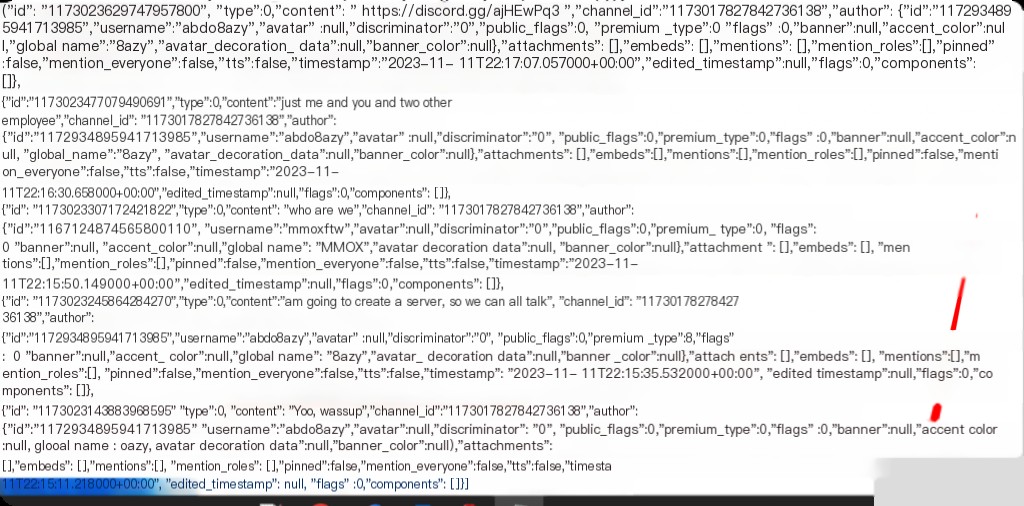
The earliest chat record time is: 2023-11-11T22:15:11.
What is the server invitation URL sent by the attacker?
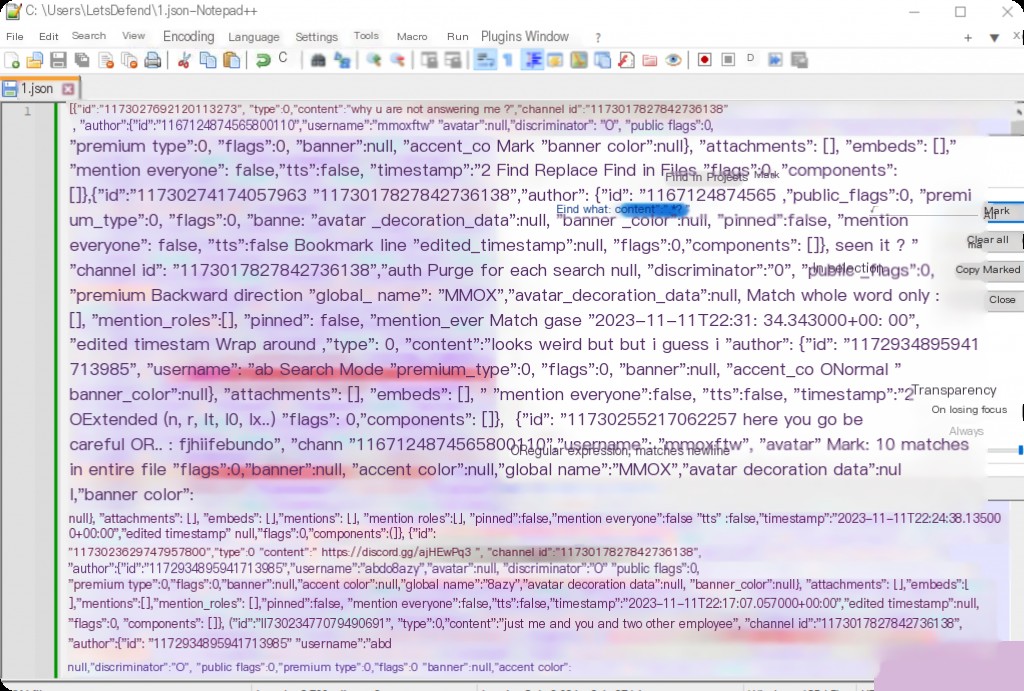
Using the system’s Notepad is cumbersome; tools like Notepad++ support regex matching and highlighting to extract chat data.
content":".*?"
How many people are on the Discord server?
A small trick is to click the Copy Marked Text button, then create a new file and paste it for clearer viewing.
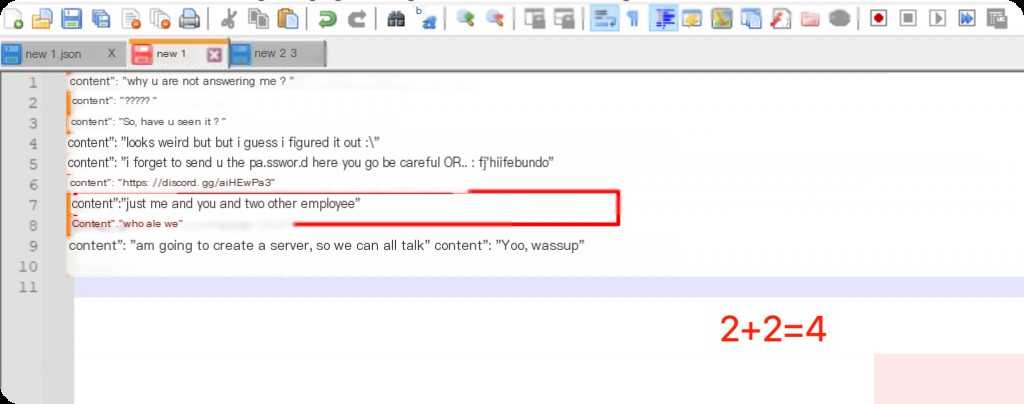
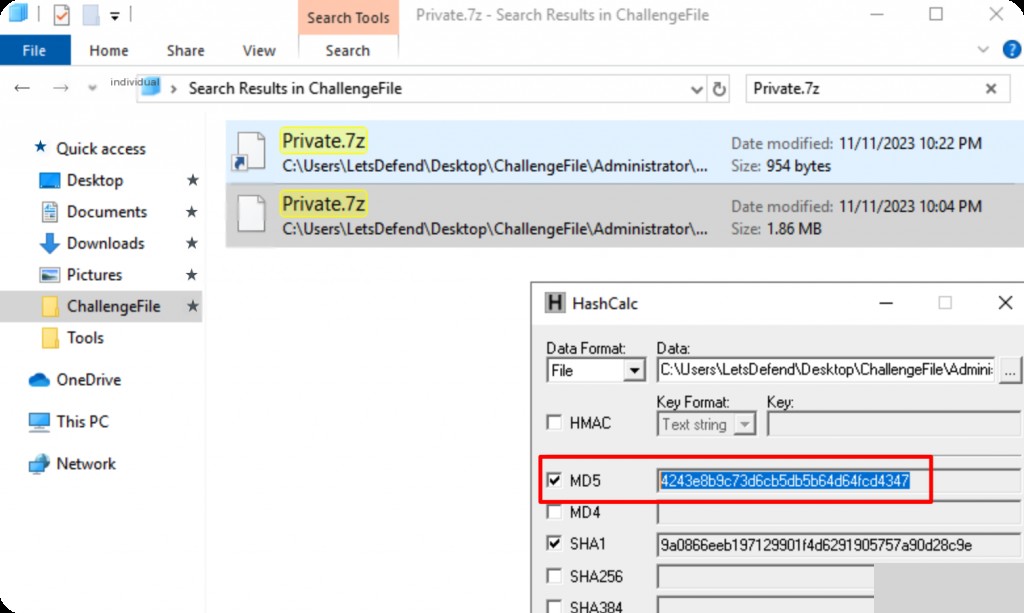
What is the MD5 hash of the attachment file sent by the victim to the attacker?
Analyze another chat record with a size of 1392.
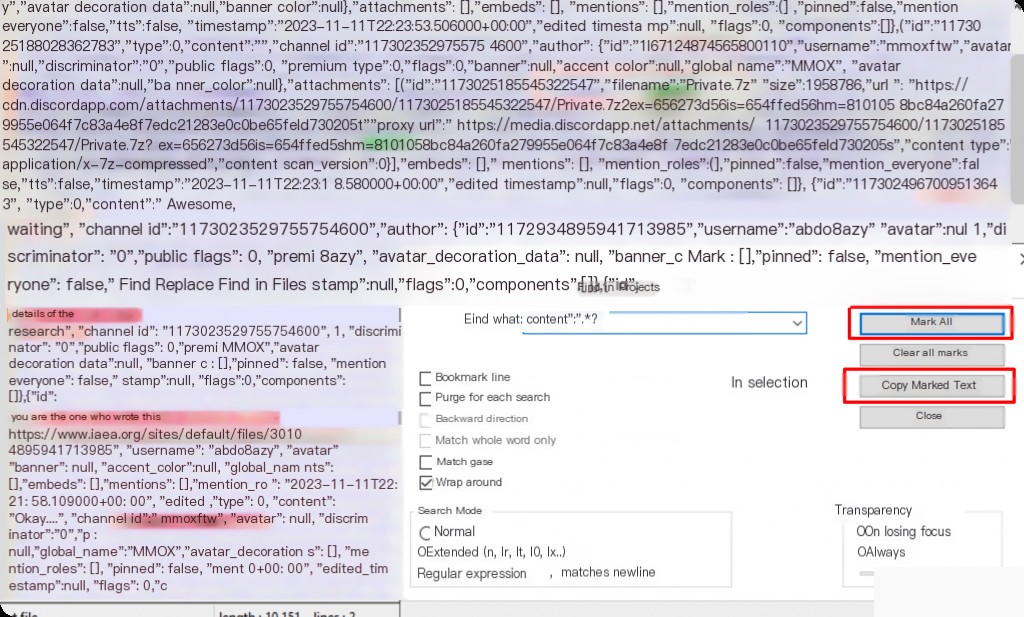
It shows that a file named Private.7z was sent, search for this file name.
Which country is the victim from?
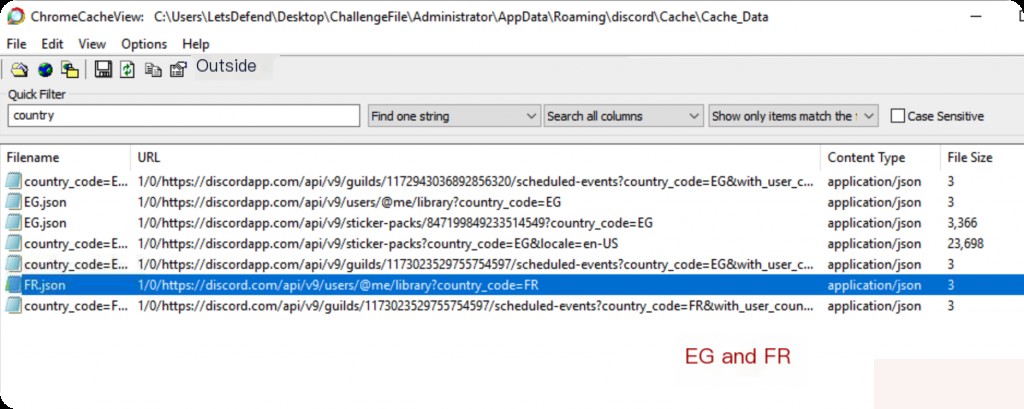
The hint says it’s not Egypt, so it’s FR. FR stands for France.
What is the URL of the attachment sent by the attacker to the victim?
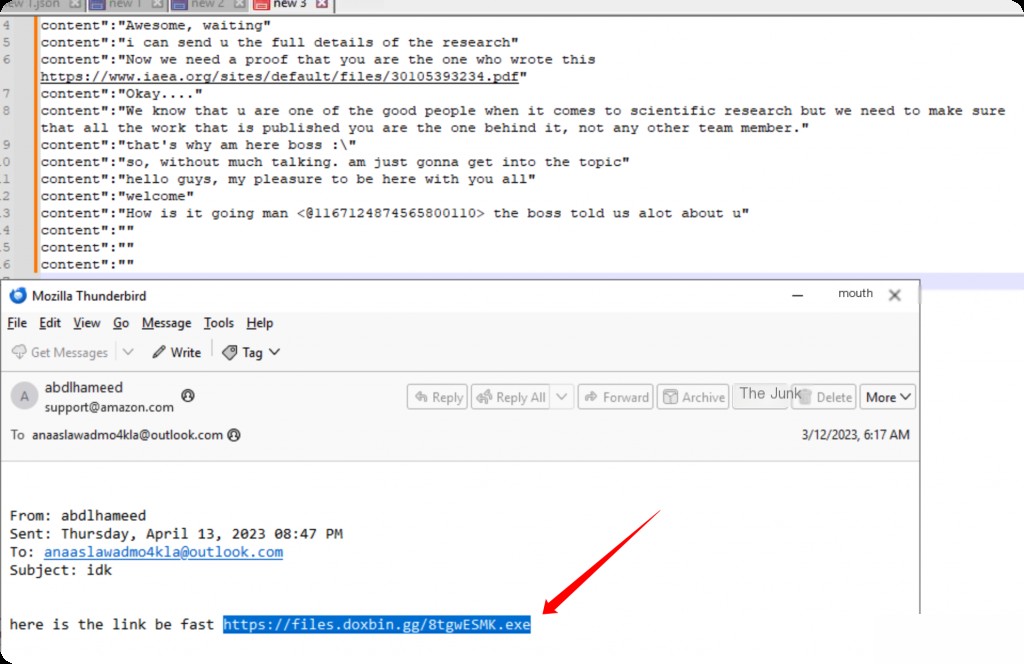
Analyzing the extracted chat content and previously analyzed .eml email content can help find the attachment URL sent by the attacker.
Summary
Analyzing the entire chat record reveals that the victim was lured to Discord by a phishing email promising a job opportunity. The victim was then persuaded to disclose sensitive research data to the attacker on the Discord server. Subsequently, the attacker attempted to blackmail the victim, forcing them to download and execute a malicious payload in exchange for not disclosing the victim’s mistake to their boss.


