Deployment Process
After downloading all necessary environment packages, you can begin the setup.
Environment package download link: https://download.csdn.net/download/weixin_42431775/19826391?spm=1001.2014.3001.5503
1. Install and Configure Snort
1. Install Snort
Using Snort_2_8_6 version here, follow the default next steps during installation without any special operations.
2. Replace Snort Rules
Copy the doc, rules, so_rules folders of the corresponding Snort version’s rule package to the Snort installation directory and choose to overwrite all files. 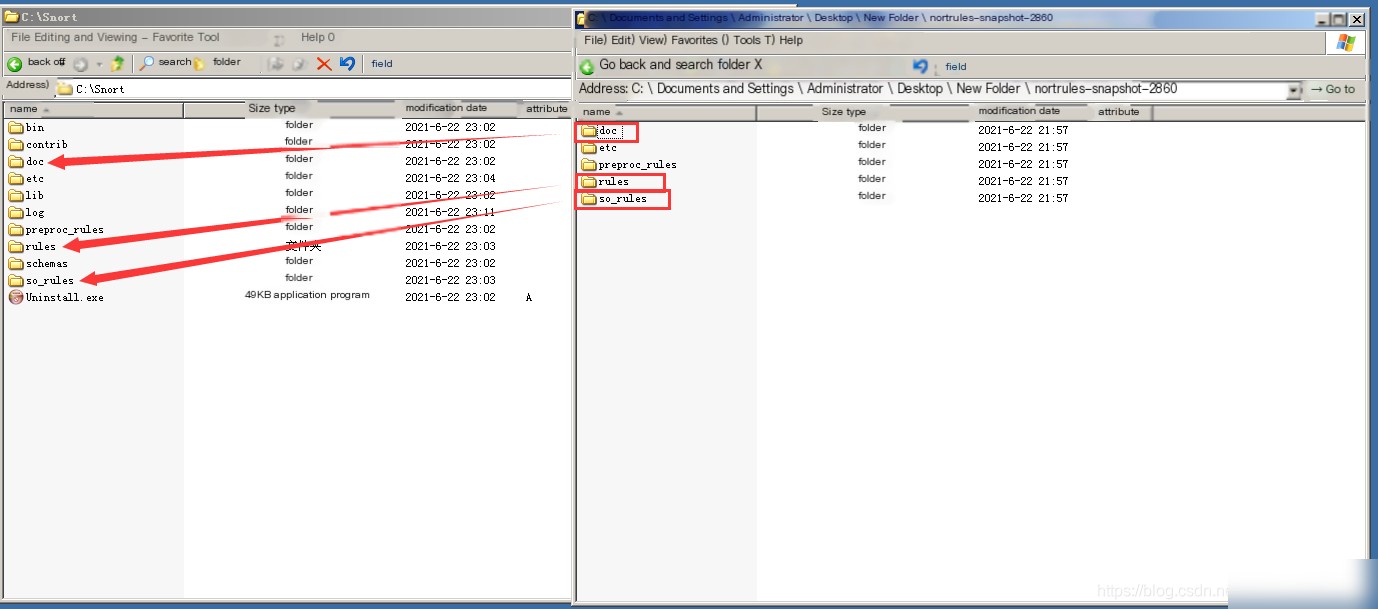
3. Open Configuration File
Open the etc folder in the Snort installation directory and open snort.conf with an editor (recommended using notepad++ or another editor, as the code is very difficult to read when opened as plain text).
4. Modify Configuration File
1. Search and modify the location of the keyword var RULE_PATH. 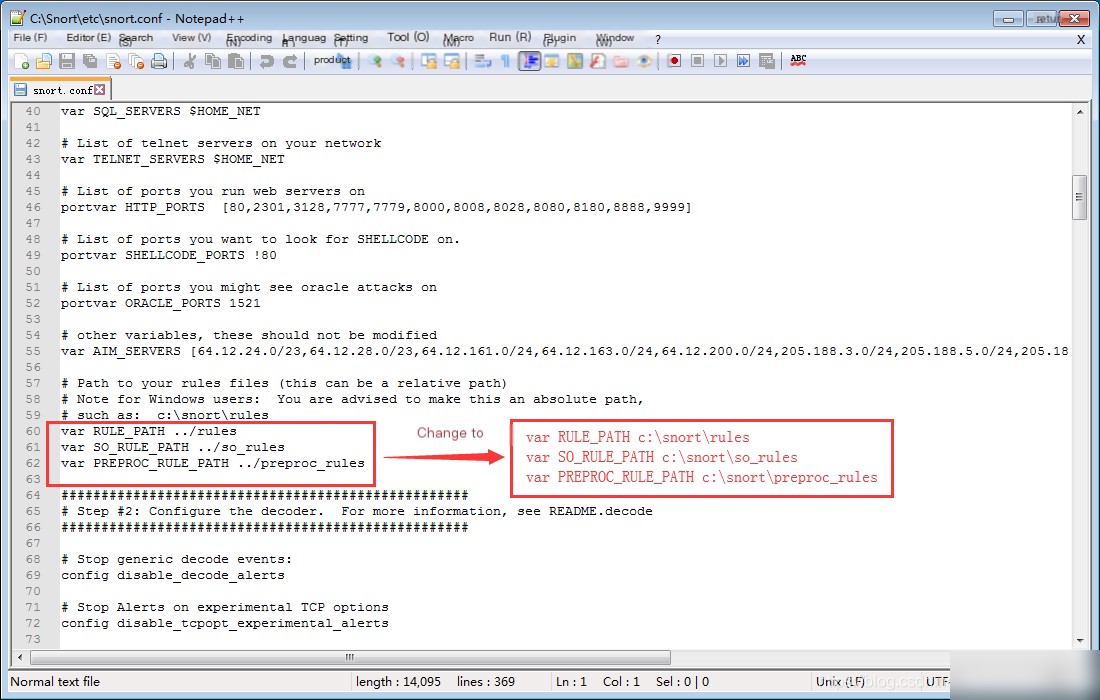
// You can directly copy to overwrite
var RULE_PATH c:\snort\rules
var SO_RULE_PATH c:\snort\so_rules
var PREPROC_RULE_PATH c:\snort\preproc_rules
2. Search for the keyword # path to dynamic preprocessor libraries and modify the location. 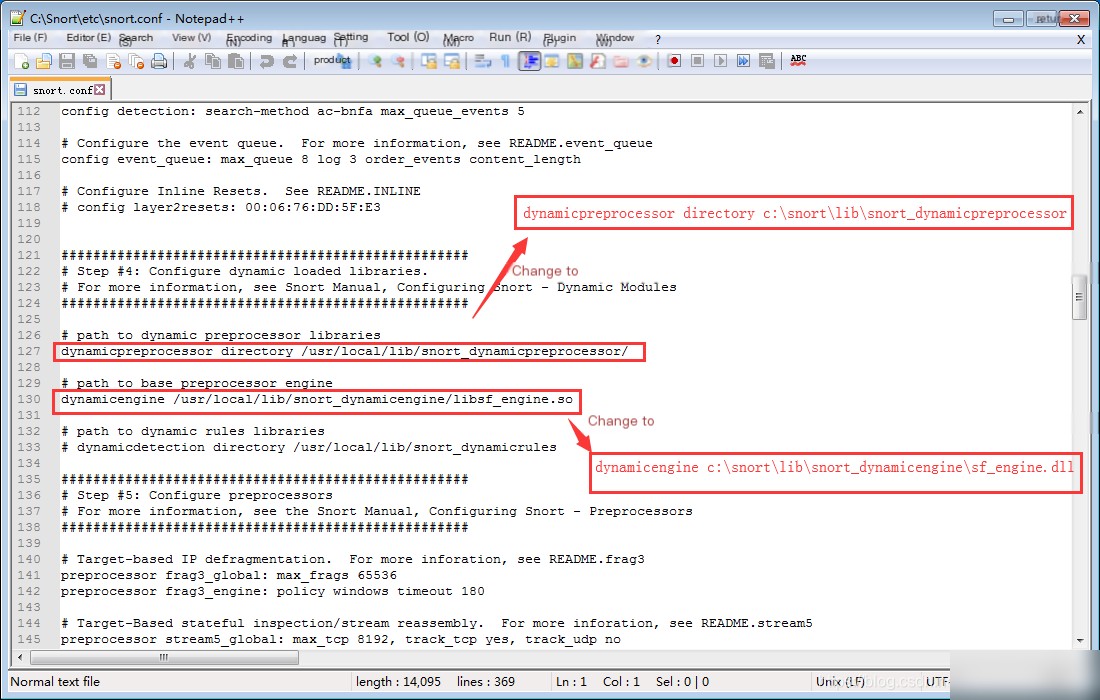
// You can directly copy to overwrite
# path to dynamic preprocessor libraries
dynamicpreprocessor directory c:\snort\lib\snort_dynamicpreprocessor
# path to base preprocessor engine
dynamicengine c:\snort\lib\snort_dynamicengine\sf_engine.dll
3. Search for the keyword preprocessor http_inspect and modify the location. 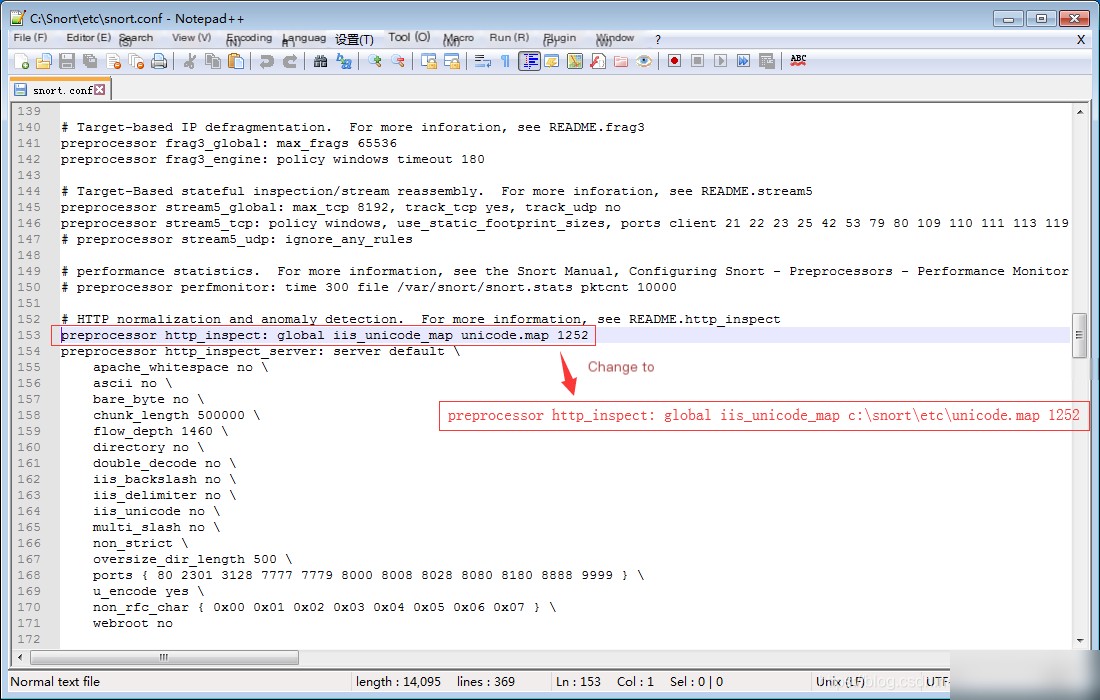
// You can directly copy to paste
preprocessor http_inspect: global iis_unicode_map c:\snort\etc\unicode.map 1252
4. Search for the keyword output database and modify the location. 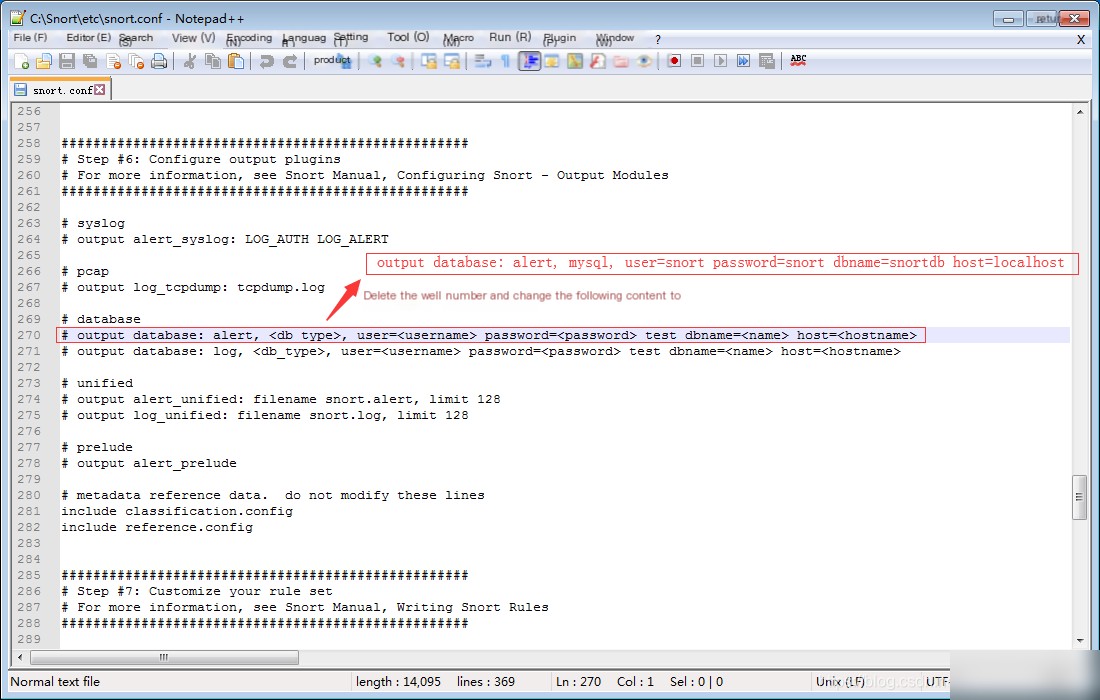
// You can directly copy to overwrite
output database: alert, mysql, user=snort password=snort dbname=snortdb host=localhost
5. Search for the keyword # decoder and preprocessor event rules, and modify the line and its surrounding lines. 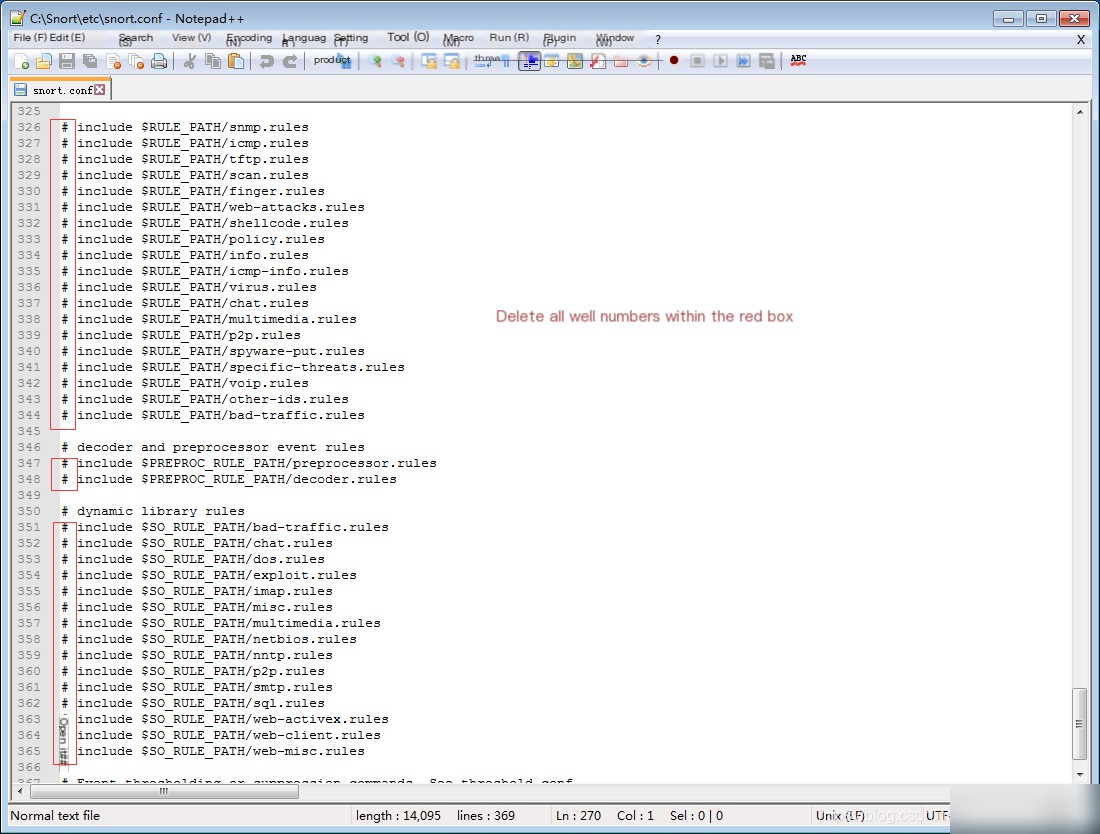
// You can directly copy to overwrite, pay attention to the coverage range! Coverage range! Coverage range!
include $RULE_PATH/snmp.rules
include $RULE_PATH/icmp.rules
include $RULE_PATH/tftp.rules
include $RULE_PATH/scan.rules
include $RULE_PATH/finger.rules
include $RULE_PATH/web-attacks.rules
include $RULE_PATH/shellcode.rules
include $RULE_PATH/policy.rules
include $RULE_PATH/info.rules
include $RULE_PATH/icmp-info.rules
include $RULE_PATH/virus.rules
include $RULE_PATH/chat.rules
include $RULE_PATH/multimedia.rules
include $RULE_PATH/p2p.rules
include $RULE_PATH/spyware-put.rules
include $RULE_PATH/specific-threats.rules
include $RULE_PATH/voip.rules
include $RULE_PATH/other-ids.rules
include $RULE_PATH/bad-traffic.rules
# decoder and preprocessor event rules
include $PREPROC_RULE_PATH/preprocessor.rules
include $PREPROC_RULE_PATH/decoder.rules
# dynamic library rules
include $SO_RULE_PATH/bad-traffic.rules
include $SO_RULE_PATH/chat.rules
include $SO_RULE_PATH/dos.rules
include $SO_RULE_PATH/exploit.rules
include $SO_RULE_PATH/imap.rules
include $SO_RULE_PATH/misc.rules
include $SO_RULE_PATH/multimedia.rules
include $SO_RULE_PATH/netbios.rules
include $SO_RULE_PATH/nntp.rules
include $SO_RULE_PATH/p2p.rules
include $SO_RULE_PATH/smtp.rules
include $SO_RULE_PATH/sql.rules
include $SO_RULE_PATH/web-activex.rules
include $SO_RULE_PATH/web-client.rules
include $SO_RULE_PATH/web-misc.rules
II. Install and Configure AppServ
1. Install AppServ
AppServ is an integrated software (which includes Apache and Mysql), follow the default options by clicking next until 
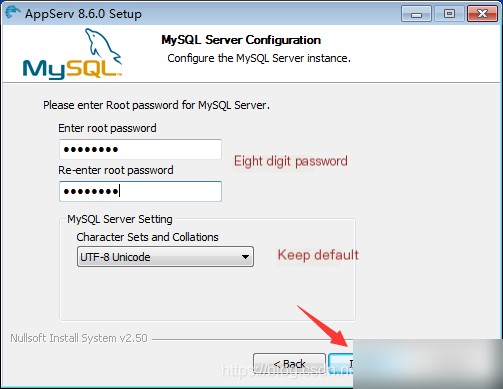
2. Check if Apache is Installed
Open the browser, enter localhost or 127.0.0.1 to check if Apache is installed correctly. If it fails to open, check if port 80 is occupied by IIS or if the Apache service has started. 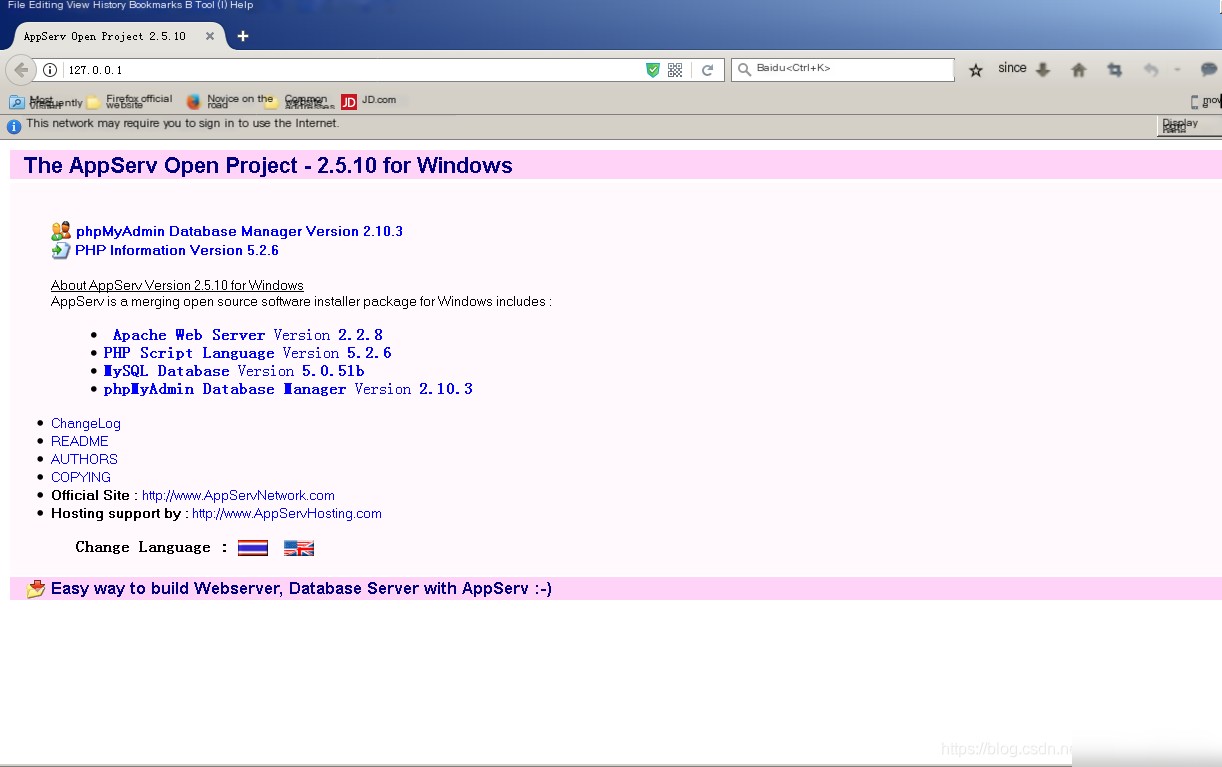
3. Create mysql Database and Tables
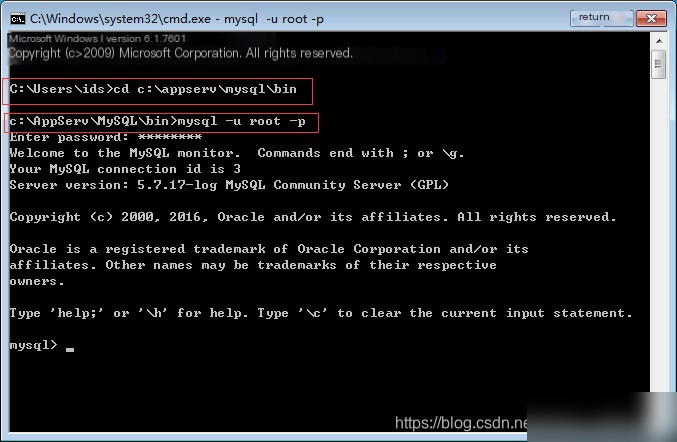
// You can directly copy and paste, attention, some require a semicolon at the end, some do not!!!
mysql> create database snortdb;
mysql> create database snortarc;
mysql> use snortdb;
mysql>source c:\snort\schemas\create_mysql
mysql> use snortarc;
mysql>source c:\snort\schemas\create_mysql
mysql> grant usage on *.* to "snort"@"localhost" identified by "snort";
mysql> grant select,insert,update,delete,create,alter on snortdb .* to "snort"@"localhost";
mysql> grant select,insert,update,delete,create,alter on snortarc .* to "snort"@"localhost";
mysql>set password for"snort"@"localhost"=password('snort');III. Configure BASE
You can use the command line or a visual window, but it’s recommended to use a visual window.
1. Copy base, adodb Folders to AppServ\www Directory
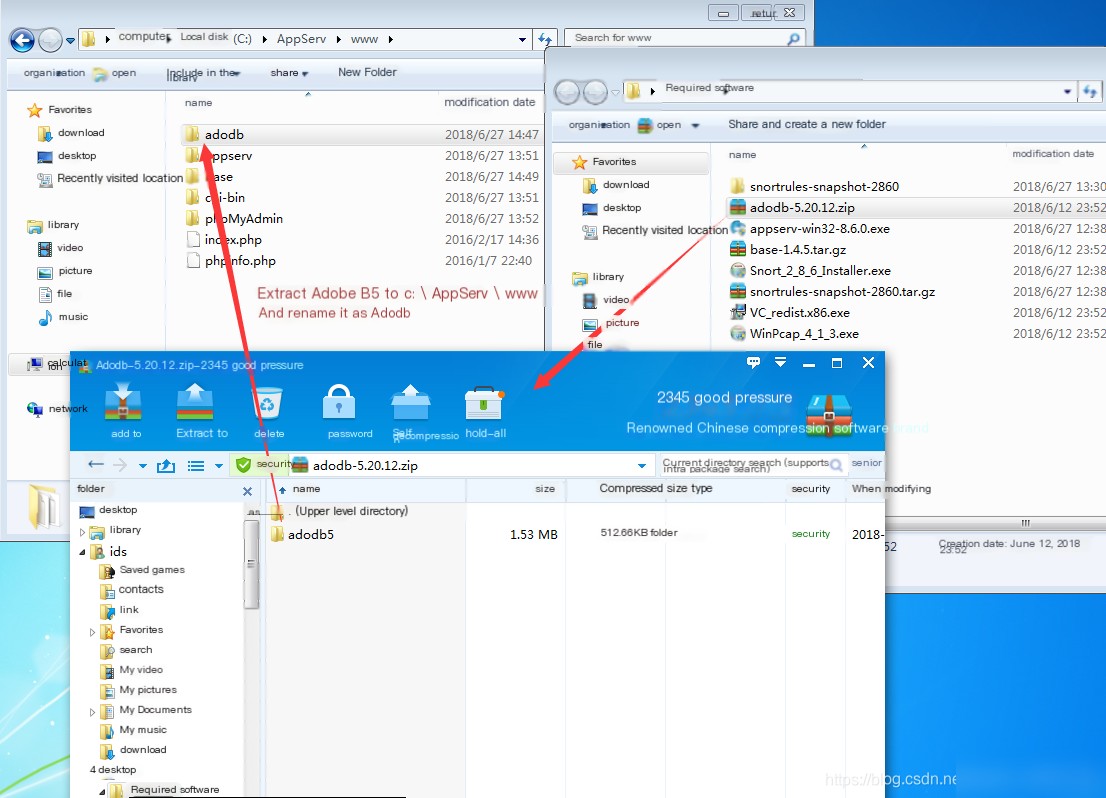
2. Perform Visual Window Operations
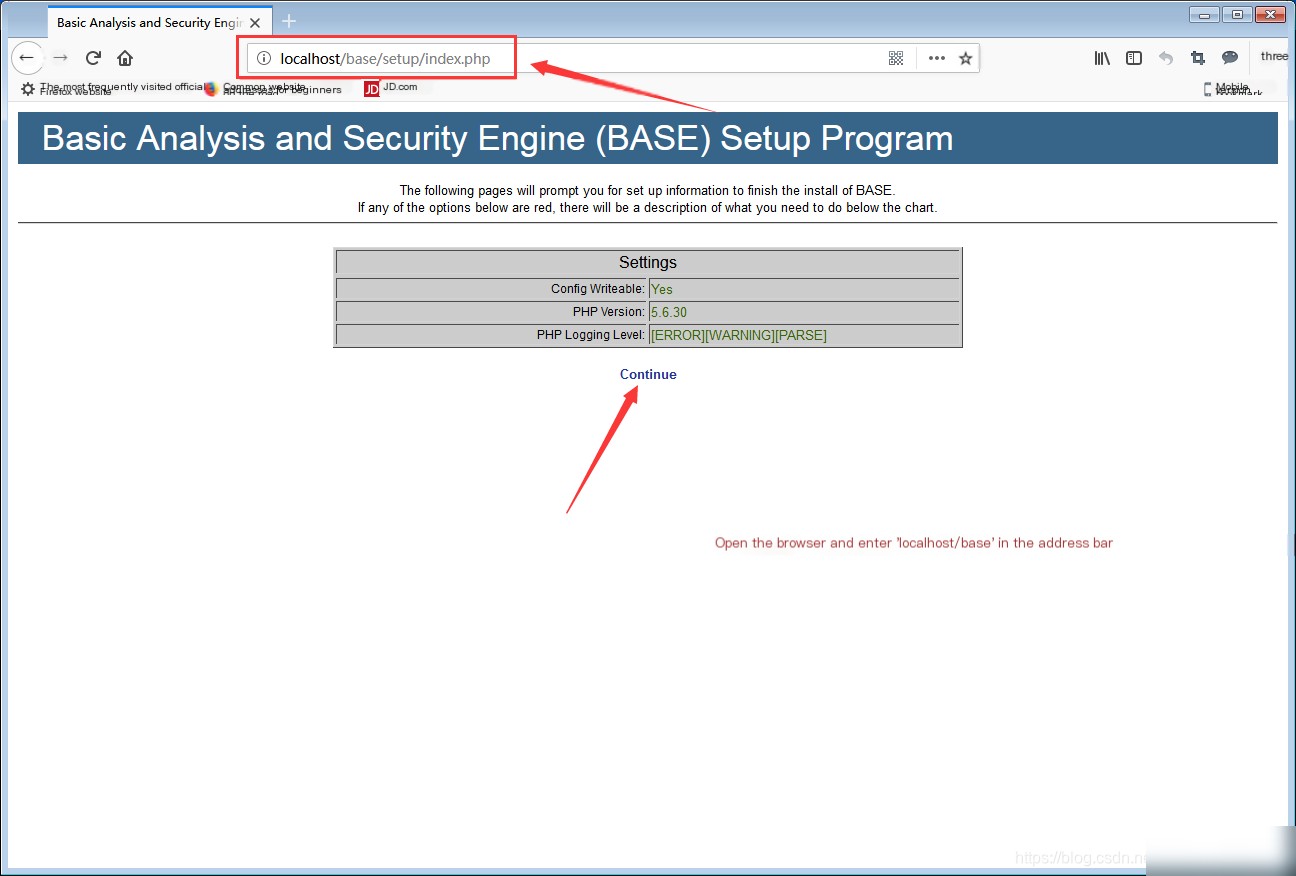
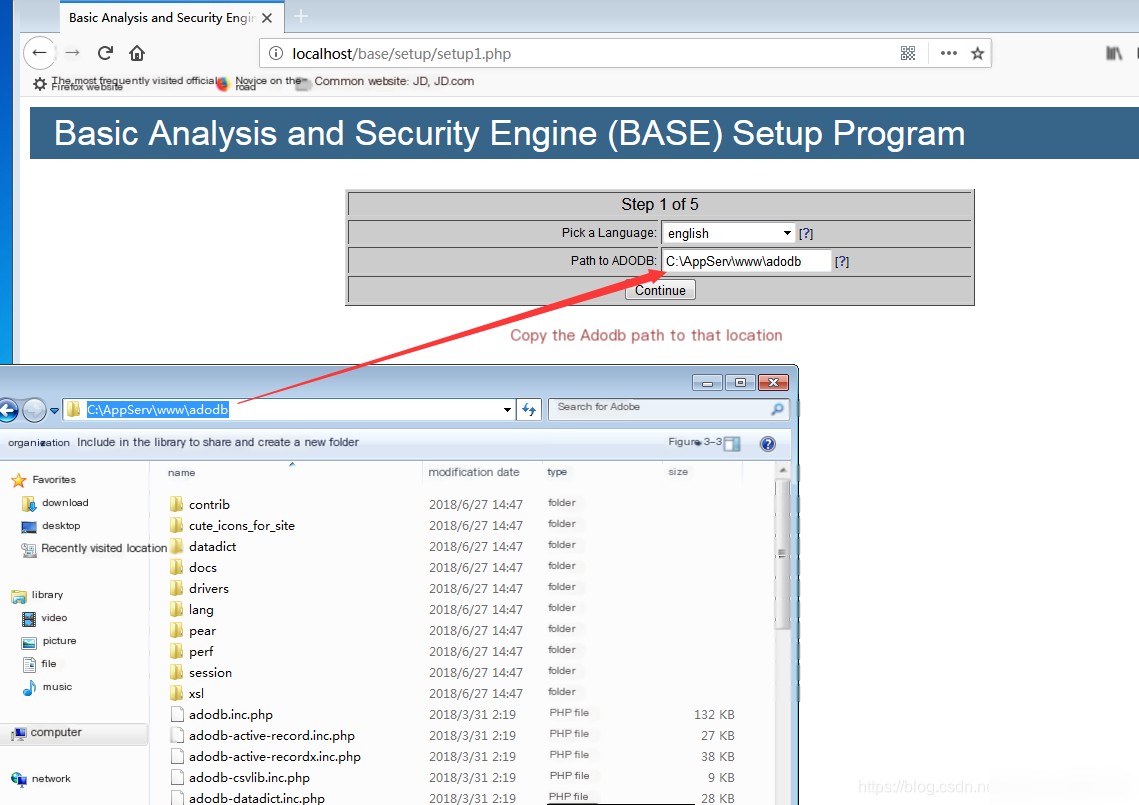
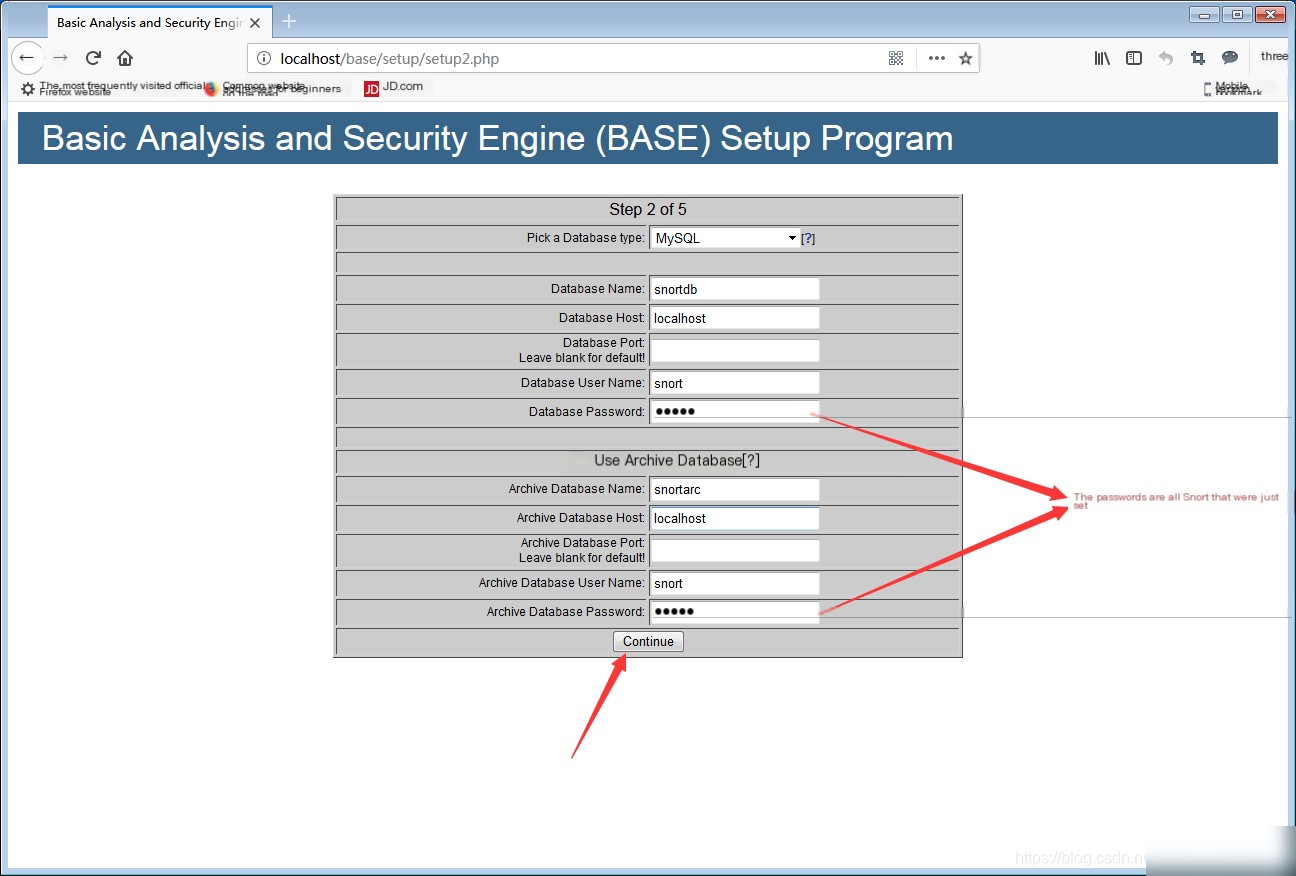
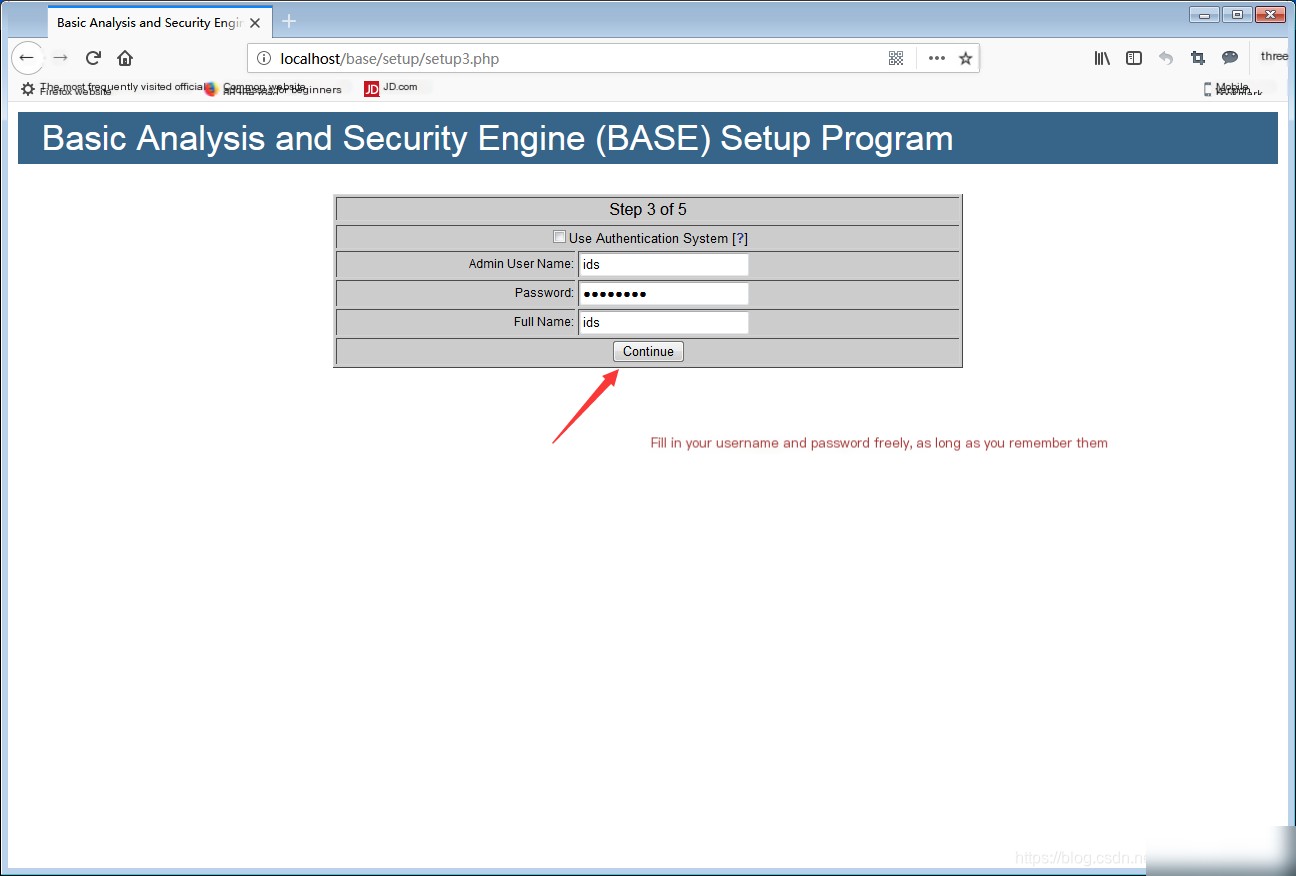
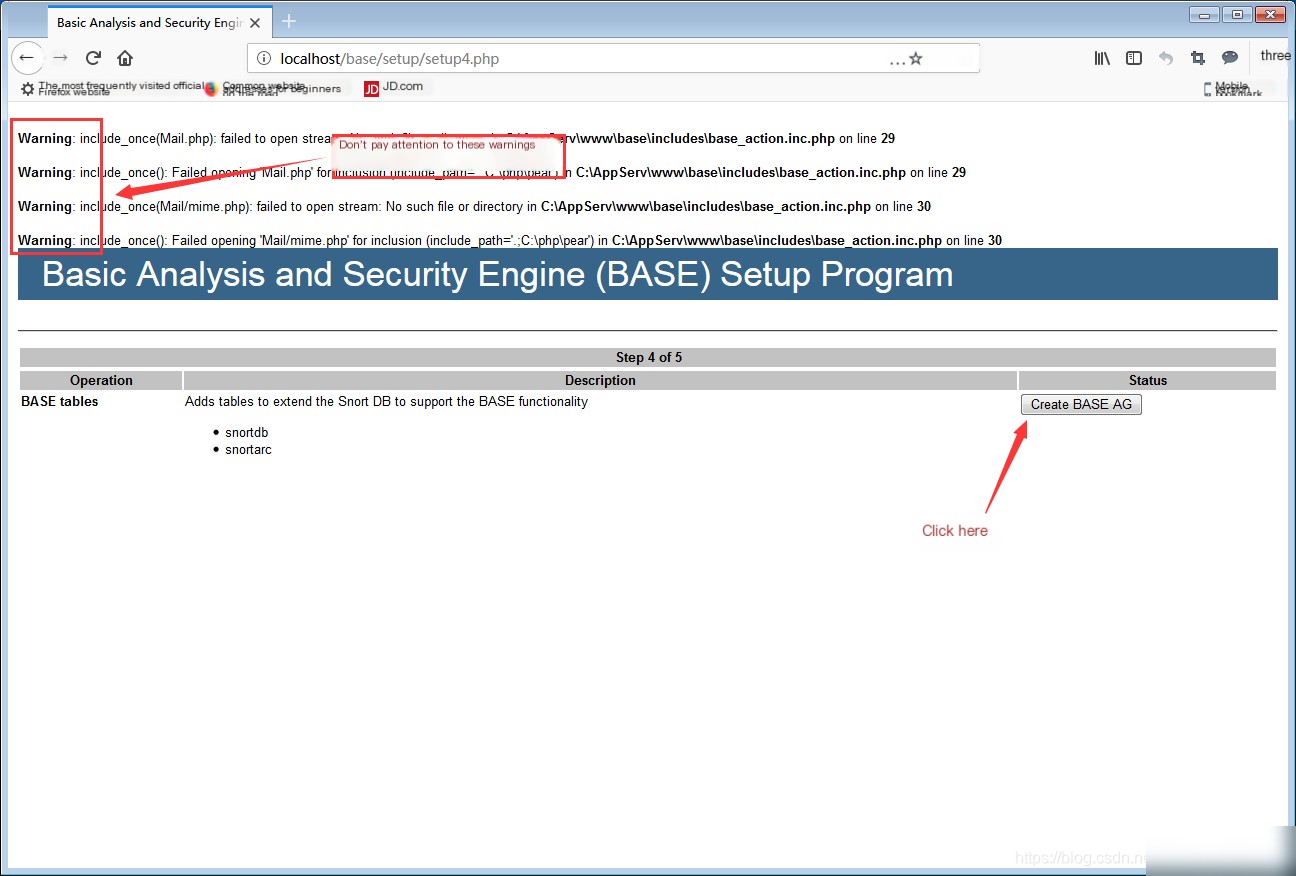
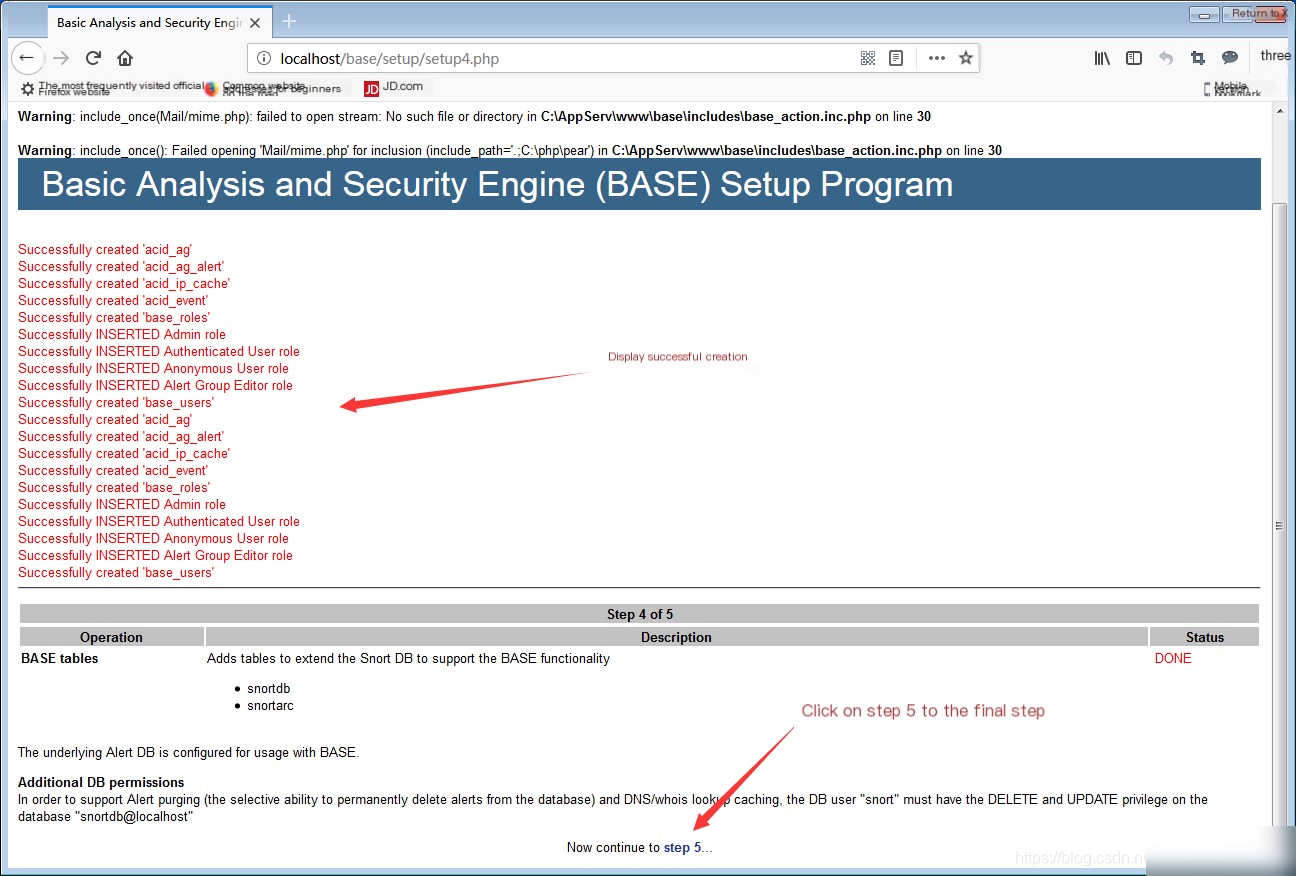 Enter in the browser: localhost\base\base_main.php or 127.0.0.1\base\base_main.php to enter the BASE visual interface.
Enter in the browser: localhost\base\base_main.php or 127.0.0.1\base\base_main.php to enter the BASE visual interface. 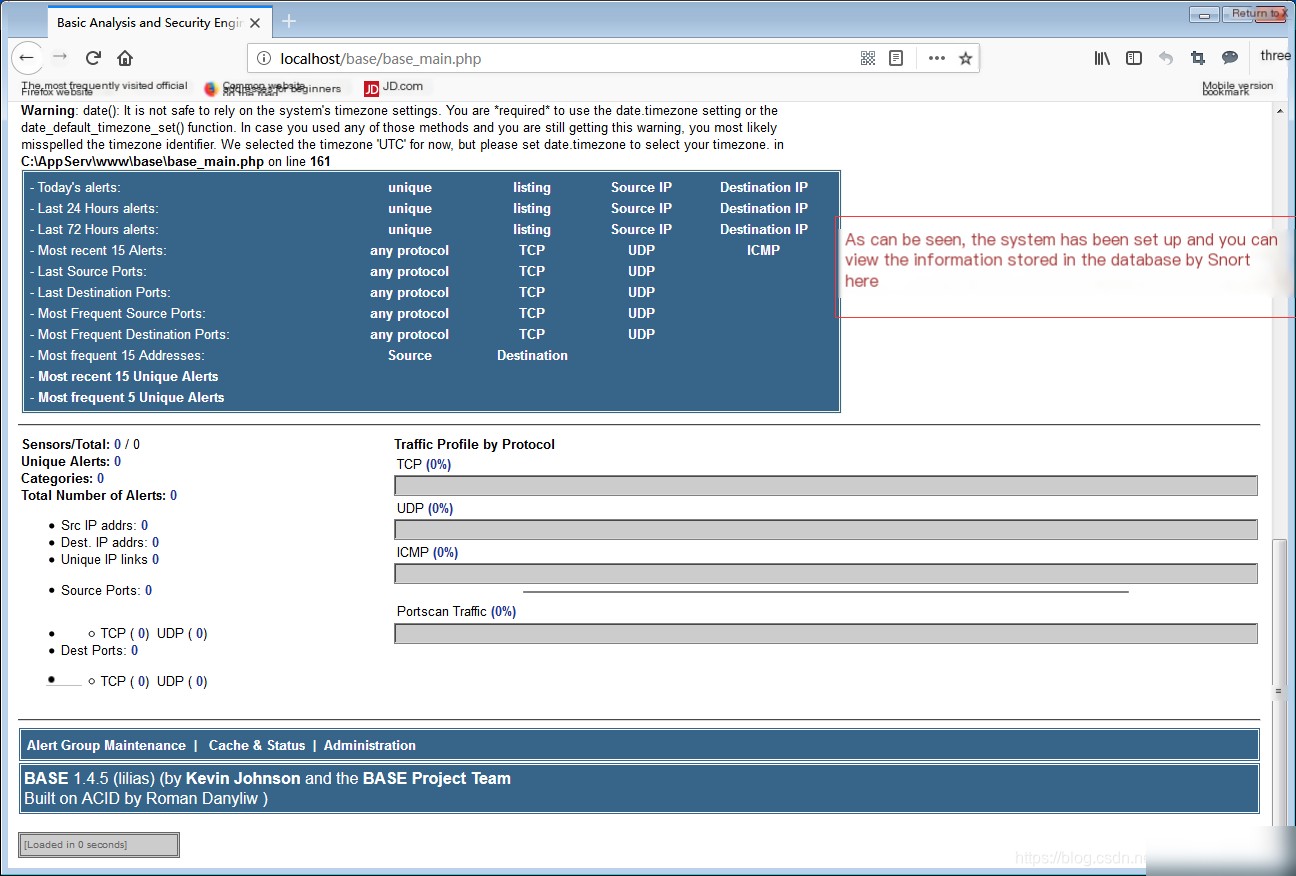
IV. Start Snort
cd /Snort/bin
2. Run Snort in Network Monitoring System Mode
snort -c c:\snort\etc\snort.conf -l c:\snort\logs -d -e -v
3. Observe Statistics
Use another host to scan this host with nmap, then you can see the statistics in the base interface (manual refresh is needed to see updated statistics) c:\snort\bin\snort -i1 -dev -c c:\snort\etc\snort.conf -l c:\snort\log
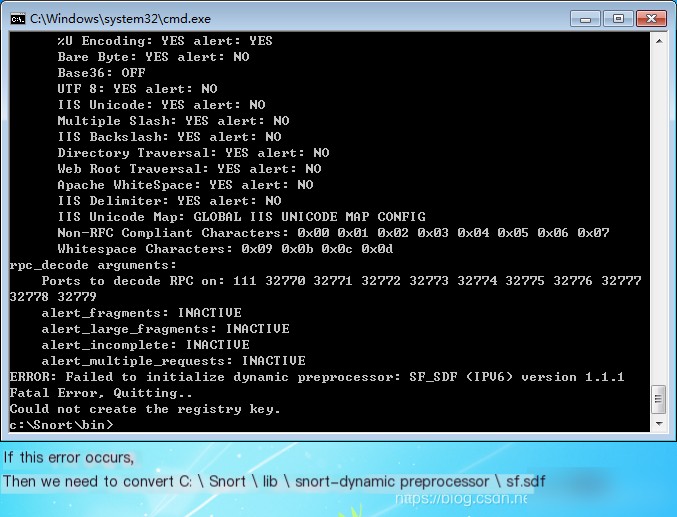
4. If Snort Fails to Start (Failure to Set Snort in Network Monitoring Mode)
If the execution fails and an error is displayed as shown below: