Recently encountered a ransomware case where the encrypted file extension is .orkf. The ransom note is as follows: demanding a few hundred dollars, mainly targeting personal PCs with ransomware.
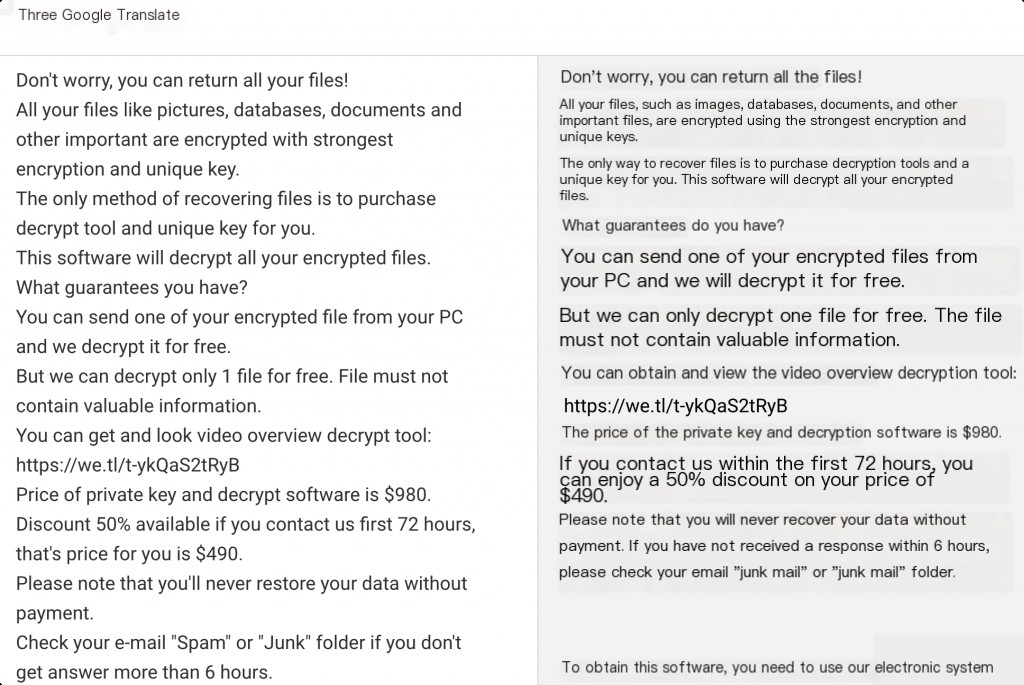
Analysis Conclusion: Based on the comparison analysis between the ransomware encryption sample and the source file, it was found that the ransomware encryption feature encrypts the file header, encrypts each file byte by byte, then saves a file copy, deletes (rather than overwrites) the original file. It also adds a virus signature code at the end of the file. Since the middle part of the file is not encrypted, it may be possible to recover some data for large files.
Information about this ransomware case:
The Orkf virus is basically similar to others in the same family: it encrypts all popular file types. Therefore, users cannot use their documents or photos. This version of ransomware adds its own “.orkf” extension to all encrypted files. For example, the file “video.avi” will be modified to “video.avi.orkf”. Once encryption is successfully completed, the virus creates a specific file “_readme.txt”.
The DJVU series uses the encryption algorithm AES-256. Files are encrypted with a specific decryption key, and there are no other copies. Without a unique key, it is impossible to recover the information. If the ransomware operates in online mode, the AES-256 key will not be accessible. It is stored on a remote server owned by the criminals distributing the Orkf virus.
Analysis Approach:
Since it is impossible to obtain the ransomware sample, the encryption logic cannot be analyzed from the code level. Here, winhex is used to compare files before and after encryption.
| File Type | Magic Number | Start Offset | End Offset |
| Windows Executable File | “MZ” | 0 | 2 |
| Linux Executable File | “\x7F\x45\x4c\x46” | 0 | 4 |
| Java Class | “\xCA\xFE\xBA\xBE” | 0 | 4 |
Executable File Magic Numbers
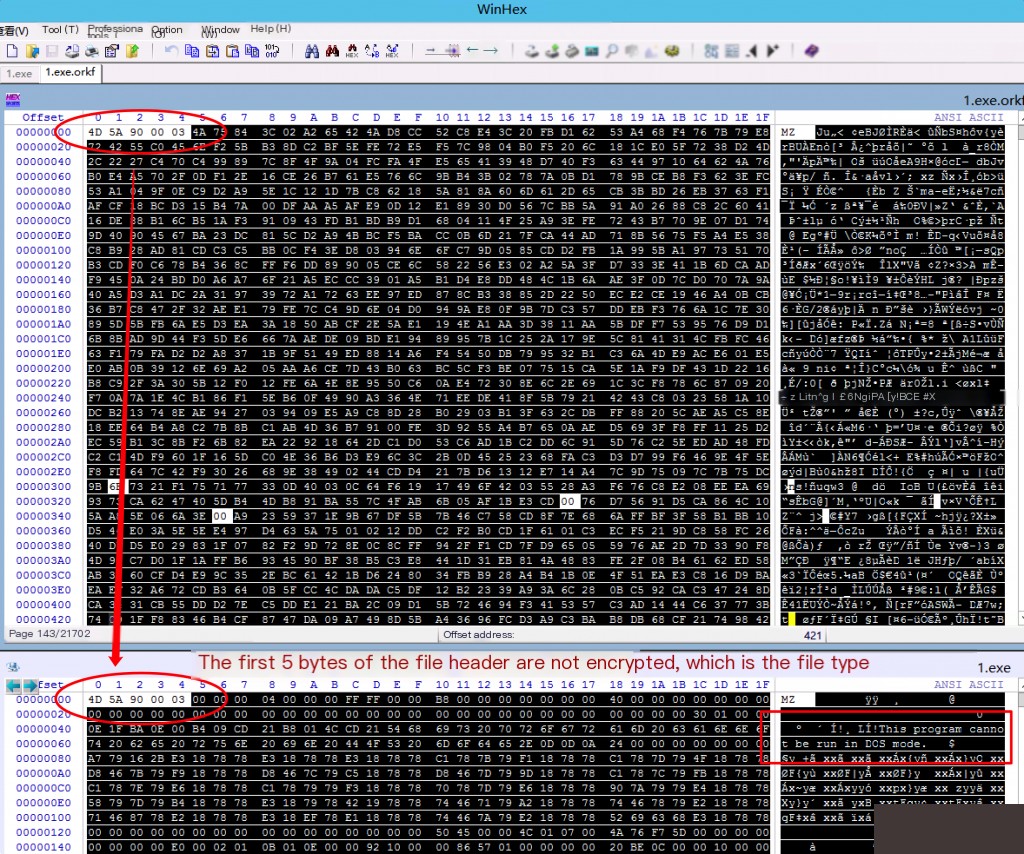
Many types of files have fixed content in the first few bytes, known as magic numbers, because these bytes can determine the file type. Magic numbers make it easy to distinguish different files.
Comparing the file header, it was found that the magic number part of the exe file is not encrypted. Similarly, the magic number part of other files encrypted by this ransomware is also not encrypted.
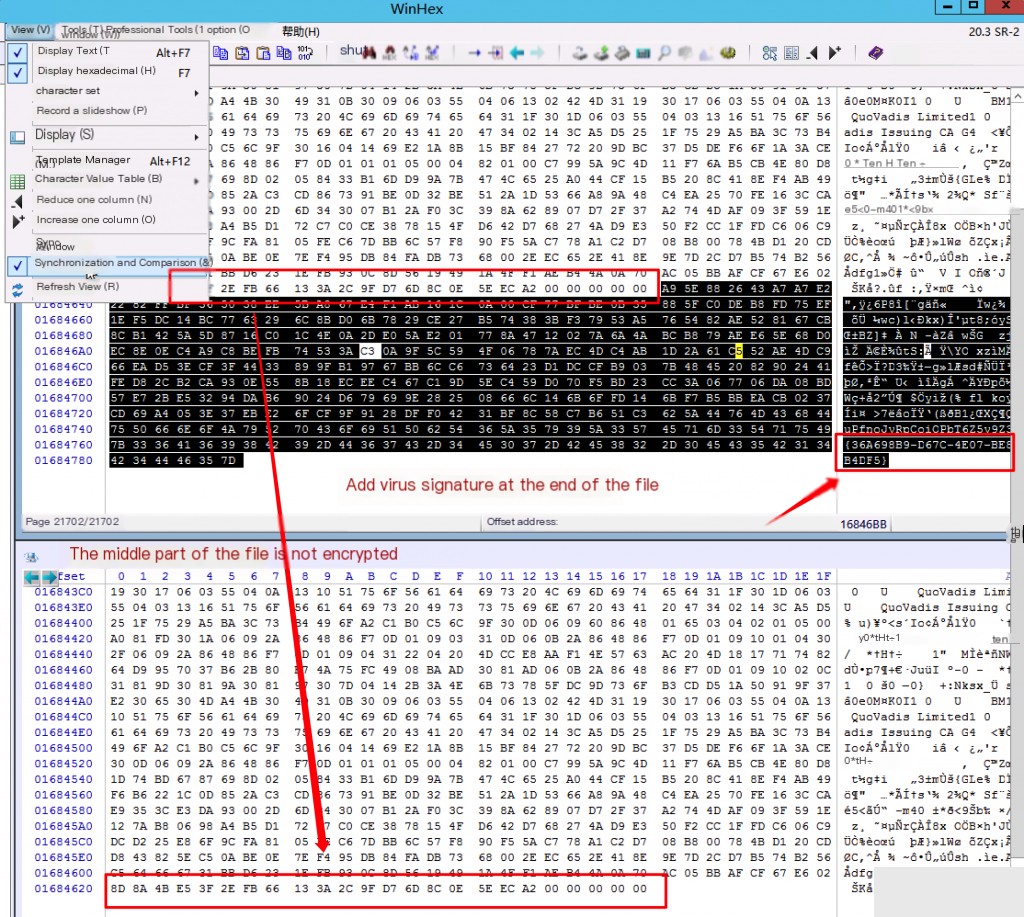
After comparing files with winhex, it was found that the end of the file only had the virus-added signature code, but the rest was not encrypted.
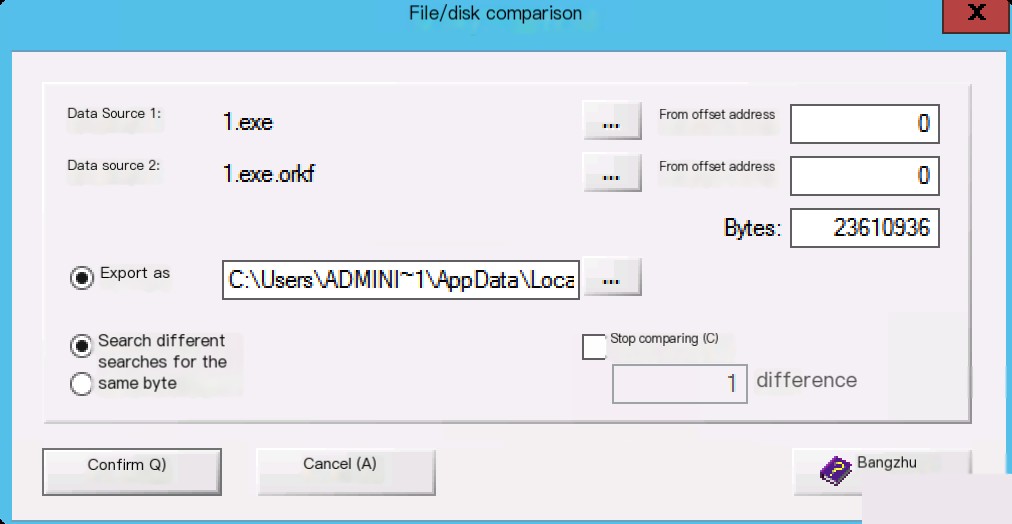
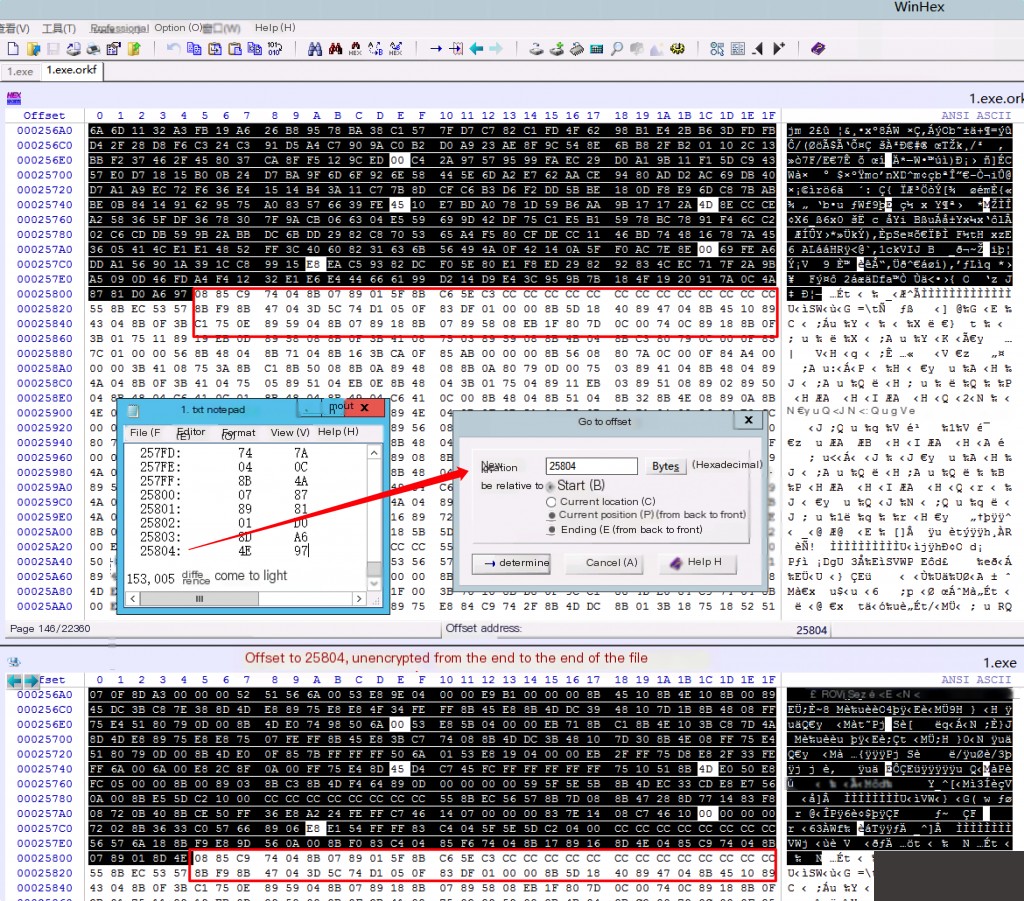
Using winhex file comparison can export the offset positions of different bytes before and after two files, and the encrypted file will have additional bytes.
According to the exported offset position found at 25804.
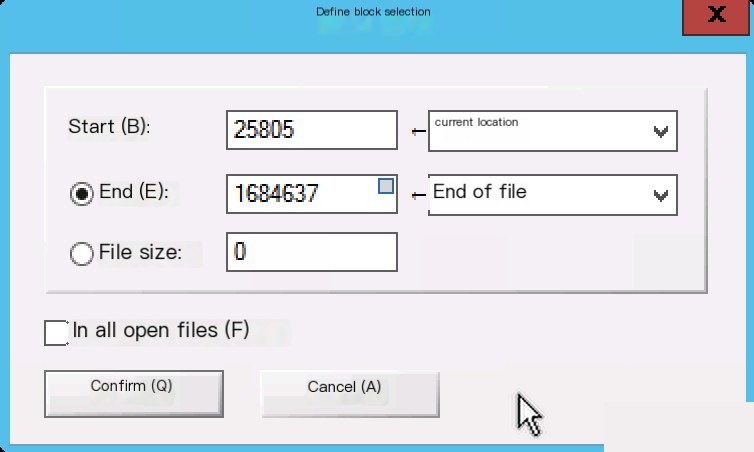
Therefore, for the unencrypted part, it can be dumped out, and blocks can be defined in winhex.
Dumping the selected block to a new file can recover data as much as possible.
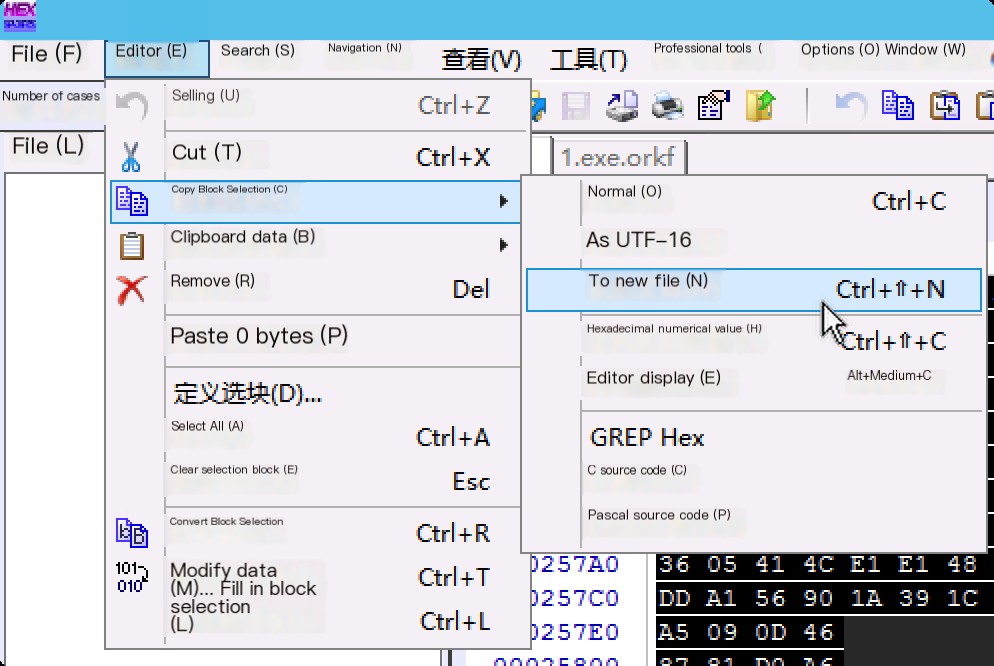
Similarly, the encrypted part can be dumped separately to obtain a separate encrypted file.
This method has a good chance of recovering large files, text, video, and compressed data files. However, this method will lose the first 150kb of data, and some small files cannot be recovered.
Disk Recovery (Partial Data Recovery):
This is a possible method, you must first back up the disk. Since the ransomware deletes (rather than overwrites) the original file, it is possible to recover the deleted original file through disk recovery. The premise is that the data has not been overwritten!
Data recovery software can recover data on the disk that has not been overwritten, but how much can be recovered still has a large element of luck. A recovery tool was tested on a ransomed host.
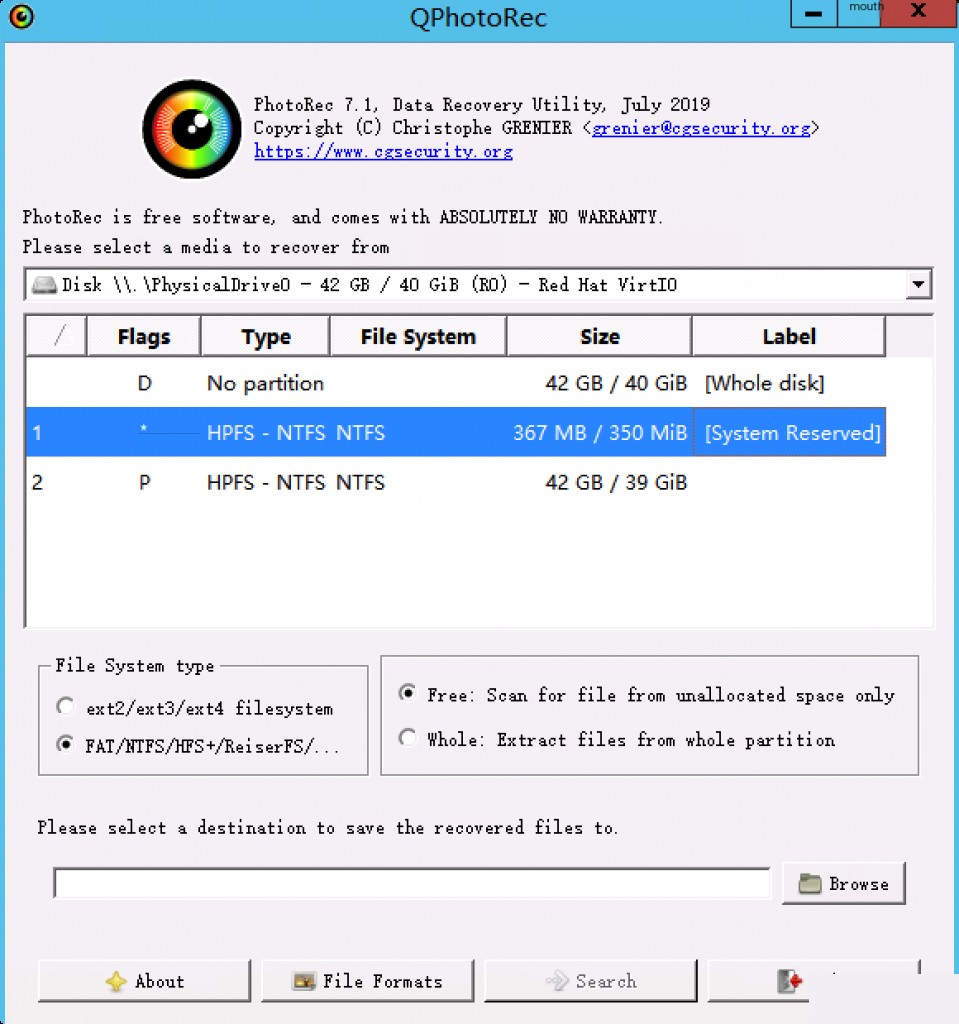
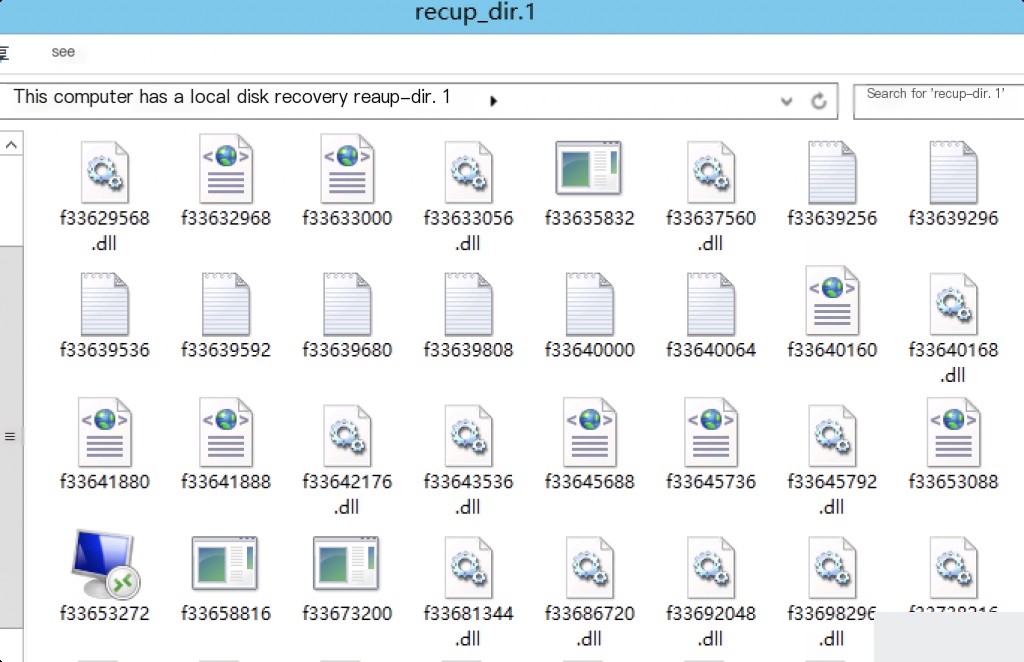 Partially recovered files from disk
Partially recovered files from disk
Testing showed that some data could be recovered, and this method can be tried first when data is urgently needed.
This family of ransomware has many suffixes. Orkf is just one of them, currently, the key for orkf is not publicly available and temporarily unavailable, but it may be updated in the future. So it’s best to back up first, as there may be a possibility of full recovery in the future.
STOP/DJVU Ransomware uses Salsa20 to encrypt victims’ files and appends one of dozens of extensions to the file name; for example, “.wrui”, “.pcqq”, “.ytbn”, “.nusm”, etc. The orkf mentioned in this article is just one of them.
Foreign security personnel are continuously collecting keys for the STOP/DJVU family and updating ransomware decryption tools.
Foreign STOP/DJVU family ransomware decryption tool
Decryptor link: Decryptor, other ransomware suffixes of the same family may be decryptable.
Summary:
Ransomware uses high-strength encryption algorithms, and without the key, decryption is impossible. Currently, the entire industry does not have a good solution. Many decryptable ransomware cases are basically using publicly available keys for decryption recovery.
Reference Links:
- https://howtofix.guide/how-to-decrypt-djvu-ransomware-files/
- https://zh.howtofix.guide/orkf-virus-file-remove-2/
- https://www.free-uninstall.org/how-to-remove-orkf-ransomware-and-decrypt-orkf-files/?lang=zh


