Preface
I’ve always heard people say not to connect to public WiFi recklessly as it may leak private information, but I never understood how such leaks occur. Recently, I learned some network security knowledge and conducted an experiment to see if it’s really possible to capture data.
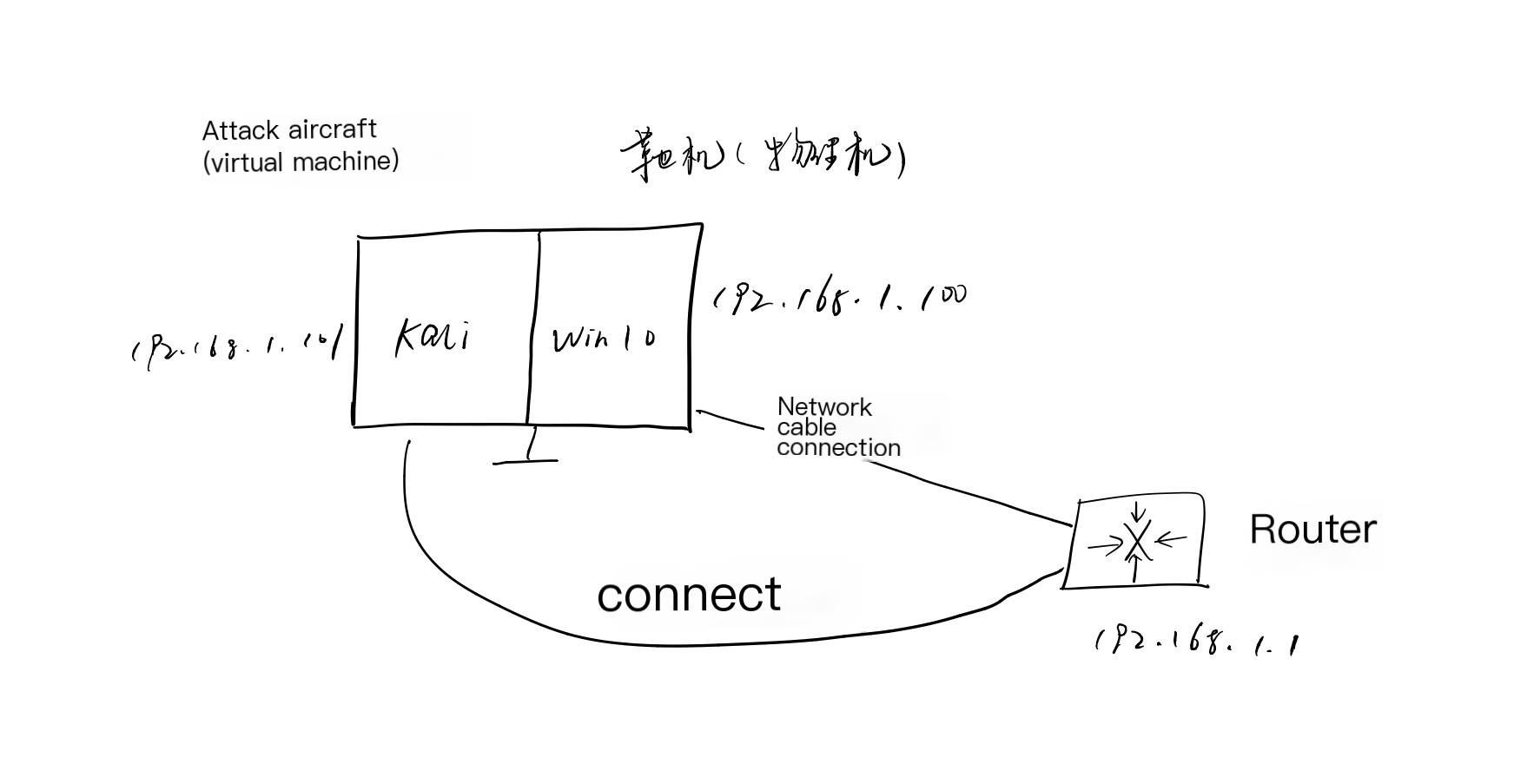
Experimental Platform:
Target Machine: Windows 10 Physical Machine
Attack Machine: Kali Linux Virtual Machine
The entire network topology is as follows:
This article is purely for raising security awareness and should not be used for illegal purposes.
ARP Protocol
First, let’s briefly explain what the ARP protocol is. In simple terms, it is the Address Resolution Protocol (Address Resolution Protocol). In network communication, for two machines to communicate, they must know each other’s MAC address. At the network layer, generally, only the IP address of the communicating host is concerned, which leads to the fact that when using the IP protocol over Ethernet, the Ethernet protocol in the data link layer only contains the IP address of the destination host. This requires the ARP protocol to resolve the IP address to the corresponding MAC address.
ARP spoofing exploits this protocol. Its operational principle involves an attacker sending fake ARP packets onto the network, especially to the gateway. The aim is to have traffic destined for a specific IP address mistakenly sent to the attacker instead. The attacker can then forward this traffic to the actual gateway (passive packet sniffing) or alter it before forwarding (man-in-the-middle attack). The attacker can also direct ARP packets to a nonexistent MAC address to conduct a denial-of-service attack, such as with Netcut software.
Ettercap
This is an ARP spoofing tool that comes with Kali Linux. Here, we’ll talk about the basic usage, and the basic principles will be detailed in another article. It can scan active hosts within a local network and carry out ARP spoofing. Firstly, ensure that our attacking machine has a network card connected to the local network. Then proceed with the steps, first opening the Ettercap GUI from the Kali command line.
 />
/>
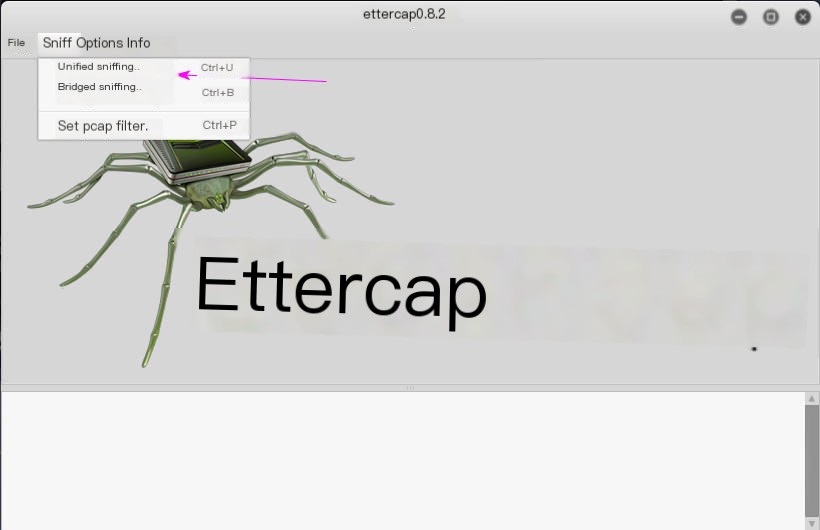
Then enable unified sniffing
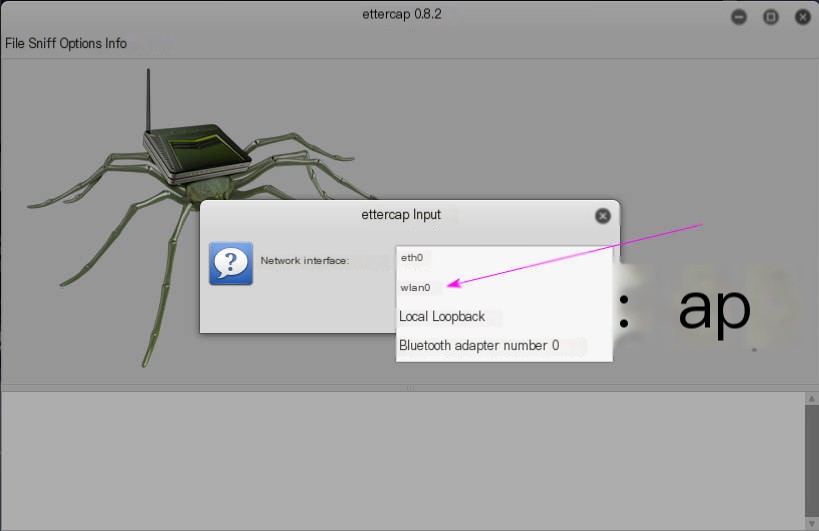
Select a network device to spoof. Since I’m connecting my router with a WiFi network card, I choose wlan0 here.
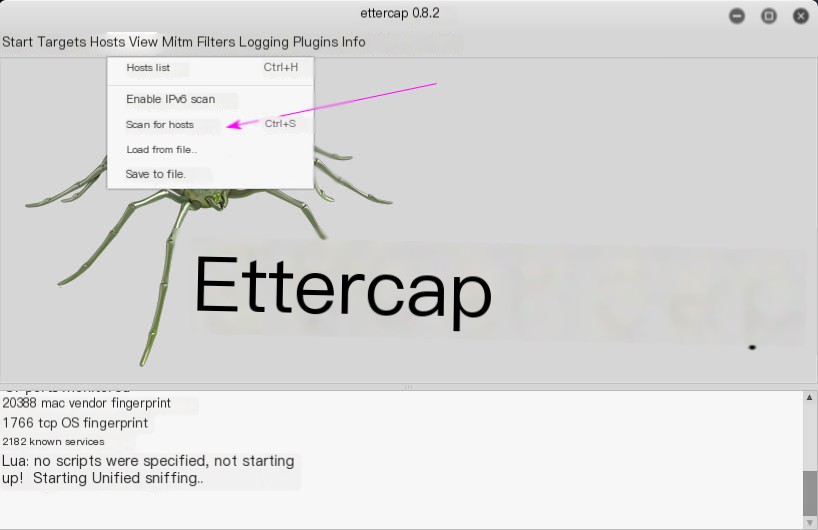
Next, scan for network devices within the local network. You can open the Hosts list to view the scanned devices.
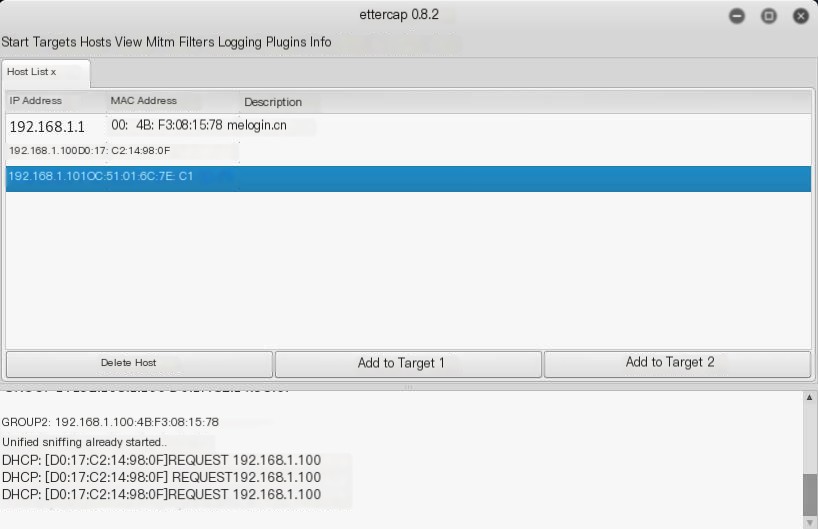
You can see the local network IP addresses of my router, physical machine, and Kali Linux attack machine. We place the attack target in Target1 and the router/gateway in Target2, preparing to start sniffing.
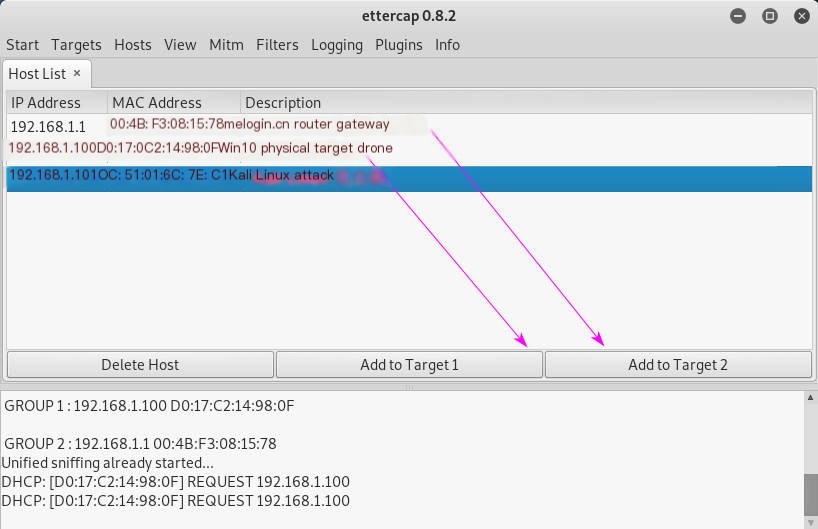
Click Mitm panel’s ARP poisoning
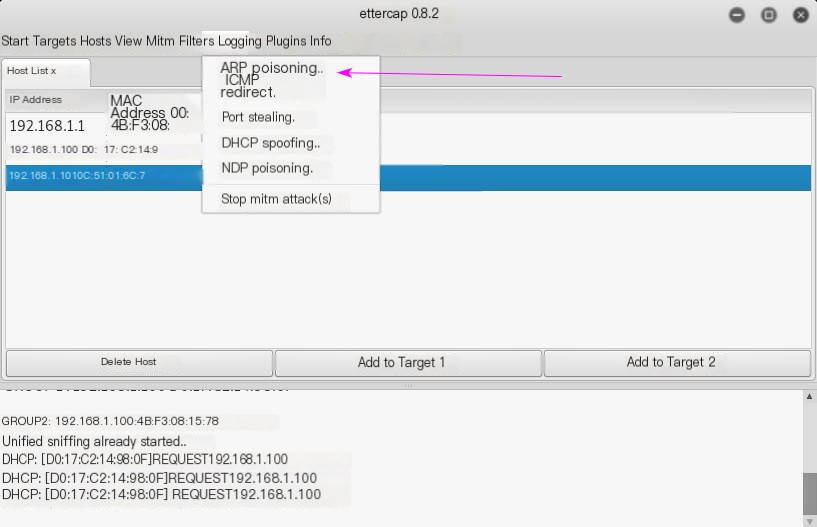
Select sniff remote connections and click OK.
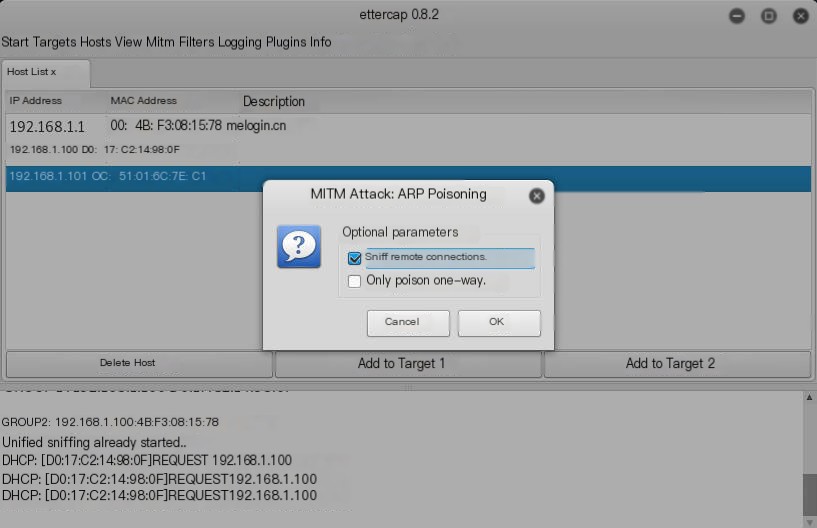
Start sniffing, and then the target machine’s traffic will pass through our attack machine first.
Wireshark Packet Capture
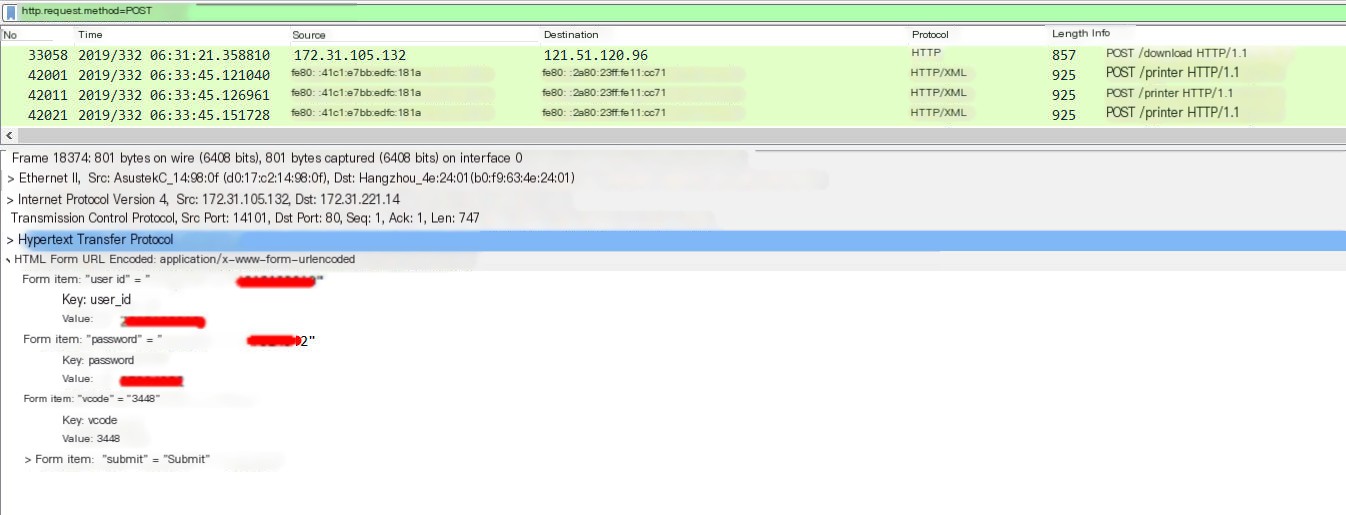
Once sniffing is enabled, all traffic on the target machine will first pass through our attack machine before being sent out. This makes us a man-in-the-middle, allowing us to use Wireshark to capture traffic packets from the target machine to obtain sensitive information. I logged into our school’s online OJ platform on the physical machine. It uses HTTP, which means all information is transmitted in plaintext. We can capture account and password information.
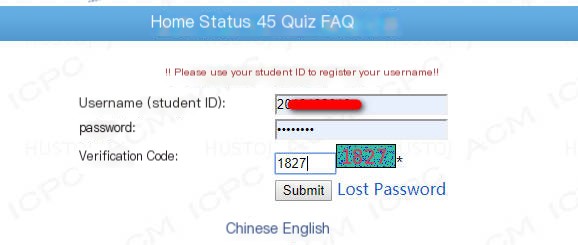
In Wireshark, we capture traffic packets that pass through wlan0, which are packets from the target machine, filtering HTTP protocol traffic. Form submissions typically use the POST method, so directly filter for POST requests in HTTP. As you can see, the account and password are fully visible. This applies to other protocols as well; ultimately, all traffic from the target machine will pass through our attacking machine. However, some protocols like HTTPS are encrypted, making them difficult to crack.
Conclusion
The campus network is a large local area network, bringing us a lot of convenience, but also causing many security risks. For example, our campus WiFi is also unencrypted, which, when connected, could easily lead to privacy information being sniffed by others. Therefore, it’s best not to connect to WiFi marked as insecure, and refrain from connecting to unknown WiFi when outside. Always be mindful of internet security.