A fan recently inquired about Private VLAN Configuration, prompting Lao Yang to realize that he hadn’t covered this topic yet. Today, he’s taking the opportunity to explain it in detail.
In a setup with 5,000 hosts connected to an operator’s switch within the same VLAN, there is a significant security risk. A single host could impersonate the gateway and hijack the outbound traffic of other hosts.
To prevent ARP spoofing, the operator assigns each host to a separate VLAN. However, the number of VLANs is limited, with a maximum of 4,096, making this approach impractical on a large scale.

After discovering the gateway’s MAC address via ARP broadcast, the user host can access the entire Internet through the gateway.
How can the host discover the MAC address of the gateway only through ARP broadcast, thereby preventing ARP spoofing attacks while minimizing VLAN usage?
The name of this solution is “Private VLAN”.
01 What is a private VLAN?
Private VLAN Configuration is a network technology that restricts communication between specific switch ports. In this setup, “private ports” can only connect to a designated “uplink,” usually a port connected to a router, firewall, server, or other central resource.
Private VLAN Configuration prevents direct communication between office computers or internal and external servers by routing all network traffic through an external gateway for processing.
Here are some examples where communication goes through gateway servers—whether on-premises or offsite—hosting the services we use:
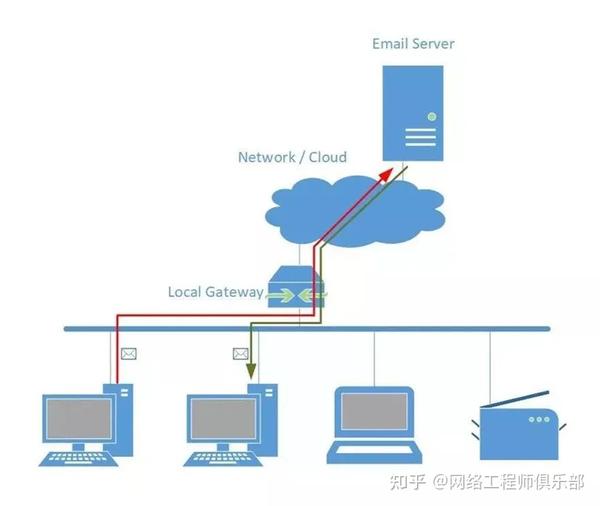
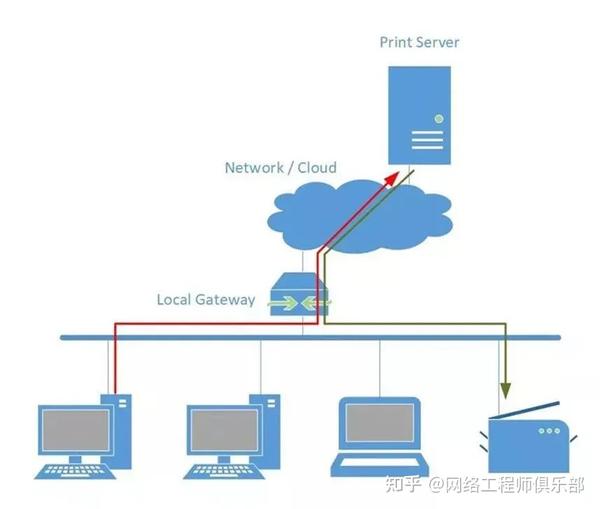
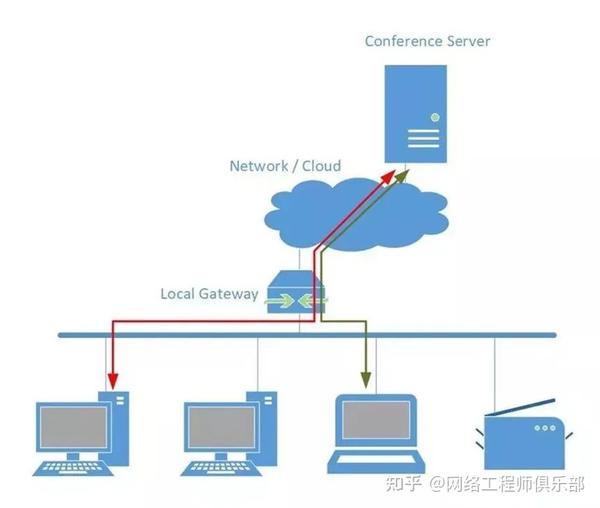
These diagrams illustrate traffic going over an uplink connection instead of directly to the destination host, indicating that direct communication with hosts on the same subnet is often more of a burden than a necessity.
02 broadcast domain
A Layer 2 switch enables devices connected to its ports to communicate directly at the data link layer without needing intermediate devices like routers or firewalls.
Therefore, hosts on the same VLAN are said to share the same broadcast domain
.
When one device is compromised, its traffic is often not analyzed or blocked, allowing the infected host to attack other machines on the same network segment.
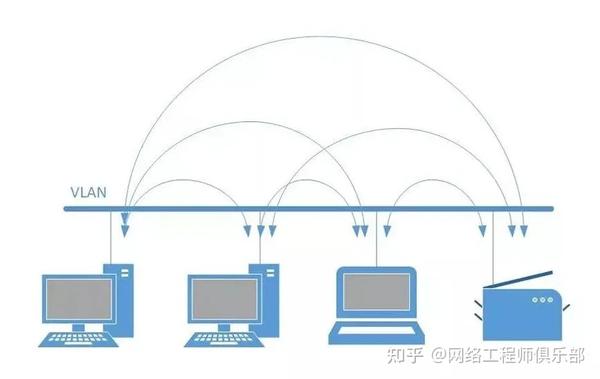
There are various techniques to prevent or mitigate such behavior, such as NAC, inline probing.
03 Network segmentation
Within an organization, departments like finance and marketing are often separated to keep their hosts distinct.
The reasons for this separation are manifold:
(1) You can easily identify which group a host belongs to by simply looking at its IP subnet
When a host exits its subnet to reach a device outside the network, it passes through an intermediate node like a router, which introduces traffic restriction rules.
To block traffic between hosts in the same VLAN, implement restrictions at a higher network layer, using access control lists (ACLs) or private VLANs to control intra-VLAN communication effectively.
Typically, it’s unnecessary for these hosts to access each other, and it’s preferable to avoid such connections.
In a shared broadcast domain, hosts communicate directly without intermediaries. To control traffic within a specific VLAN, activate the Private VLAN configuration on the switch.
04 Private VLAN Configuration Explained
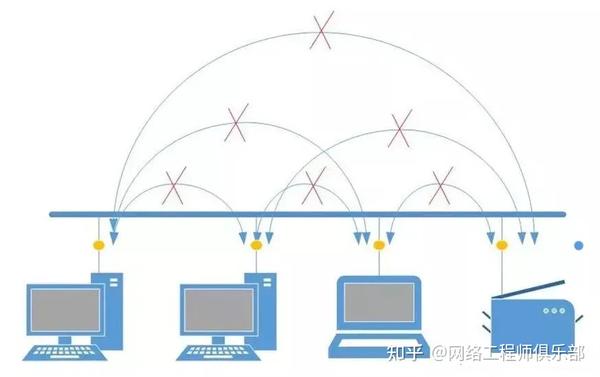
Normally, a switch enables traffic between ports within the same VLAN. For example:
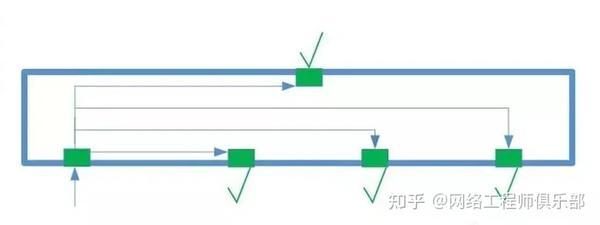
Configuring the VLAN as PRIVATE prevents traffic from flowing between ports.
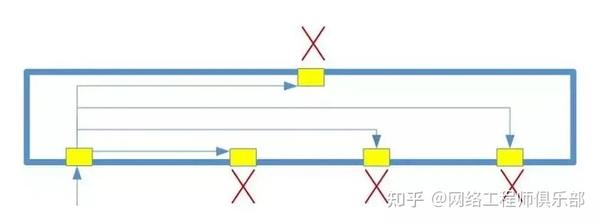
Of course, this situation is not very useful, we still need a port to receive our traffic.
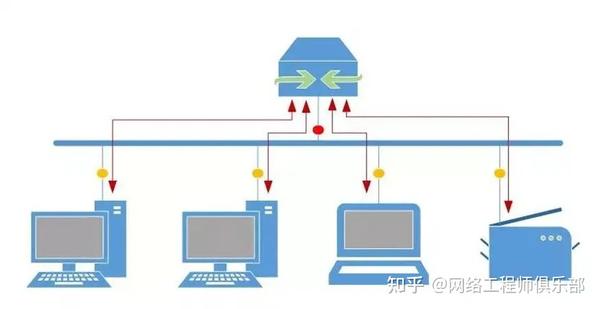
Typically this is the port our local gateway is connected to, it is named the promiscuous port:
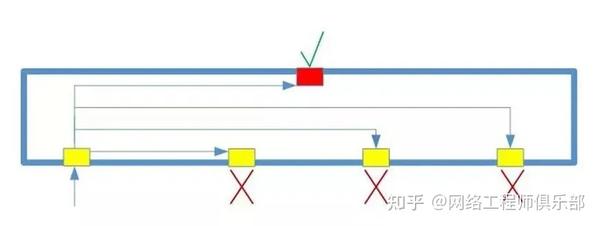
A promiscuous port can receive traffic from all isolated ports in a private VLAN, but isolated ports cannot send traffic to each other.
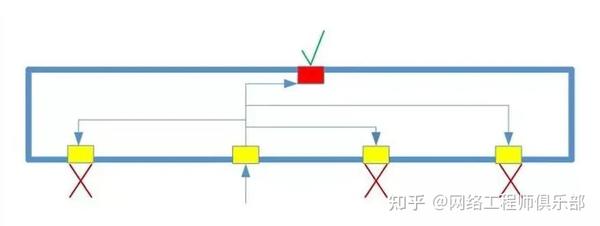
As mentioned previously, the same isolated port will continue to send and receive traffic to the promiscuous port:
To better understand the operations behind private VLANs, you need to understand the terminology involved.
Isolated port
Traffic from specific ports can reach the promiscuous port, but cannot move between isolated ports, preventing communication between hosts on the same VLAN. These ports are marked with yellow in our diagram.
promiscuous port
This port is the sole channel for sending traffic to the isolated port. Since isolated ports can’t communicate with each other, they only receive traffic from this port, marked with a red indicator in our diagram.
public port
Ports in a public VLAN are termed public ports and are represented with blue markers in our diagram.
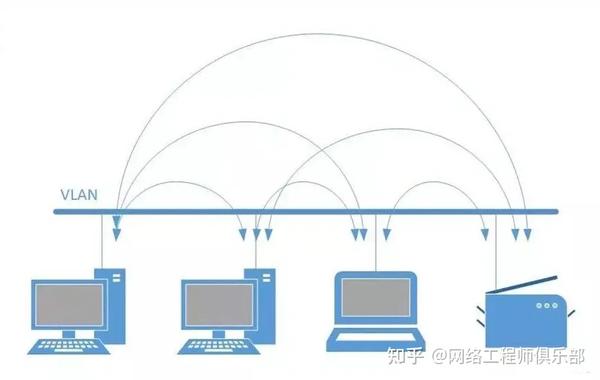
Example 1, isolated port:
In the image below we can see the hosts connected to the traditional VLAN
Traffic can move freely from one host to another to the gateway to be able to reach external subnets.
Once we configure the VLAN as private, traffic between hosts will be blocked.
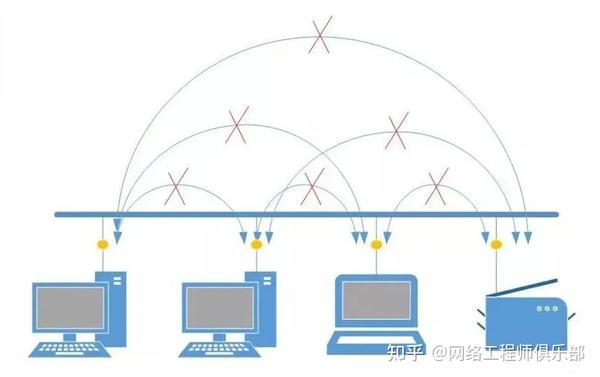
To provide external connectivity to the VLAN, we configure one port as promiscuous and connected to the local GW:
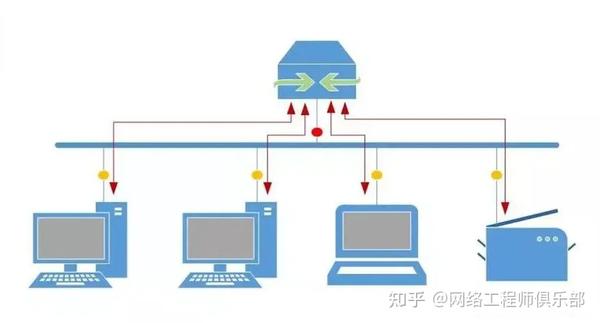
Therefore, Hosts cannot access each other at all, but they can only access services outside their VLAN.
Example 2:
If you have hosts in a VLAN needing to communicate, like two sharing a local folder that can’t be moved to a server, they still need a way to interact.
To protect VLAN hosts from other devices while allowing them to communicate directly and access promiscuous ports, implement isolation policies that restrict unwanted traffic but permit internal communication and subnet access.
By configuring the ports connected to these two hosts as public ports, allowing traffic between them and the promiscuous port, no traffic will flow from or into the isolated port.
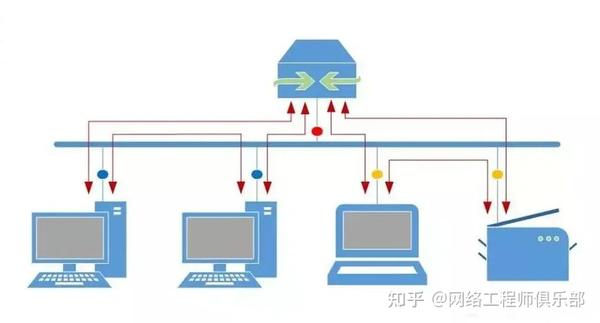
A switch needs to differentiate between traffic from promiscuous ports and traffic from isolated ports.
To define two VLANs, use a primary VLAN for traffic from the promiscuous port, and a secondary VLAN for traffic from the isolated port.

As security becomes crucial for companies, private VLANs offer a quick solution to enhance host isolation.
with physical servers .
This concept can be enhanced by adding more master and slave VLANs within the same switch or extending private VLANs to other devices for a distributed approach.
Today, private VLANs are also used in VXLAN networks with macro segmentation to support advanced security options like zero trust.



