In penetration testing of PC clients using C/S architecture, various communication protocols like TCP, HTTP(S), and TDS are utilized, unlike in B/S architecture. To capture packets from a PC client, commonly used tools are Wireshark, iptool, and WSExplorer.
This article captures the HTTP(S) traffic in a PC client (C/S architecture) using Fiddler+Proxifier.
Environment Preparation
1. Windows with client software installed
2. Proxifier+Fiddler software
Proxifier Configuration
1. Install Proxifier
Download link: http://www.hanzify.org/software/13717.html2. Configure proxy server
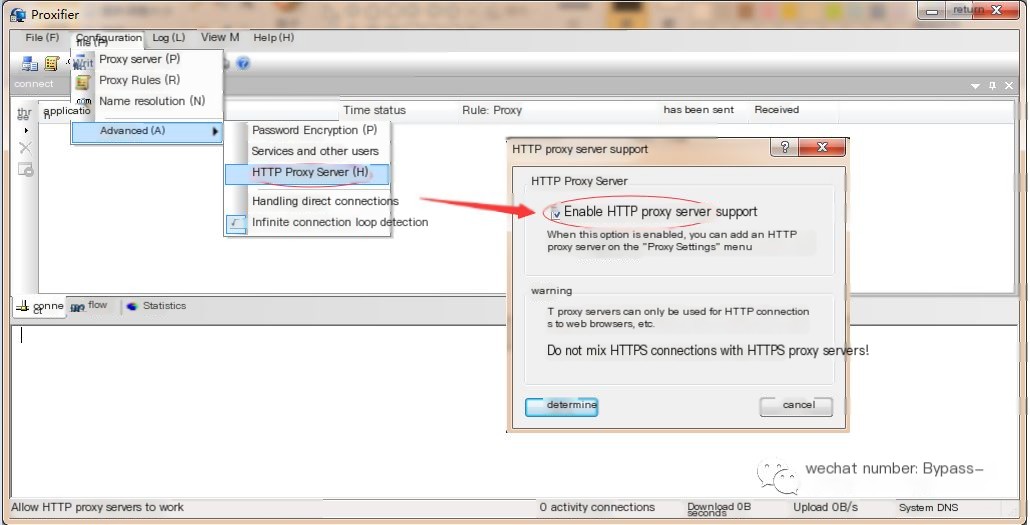
A. Enable HTTP protocol
HTTP protocol is disabled by default in Proxifier and needs to be enabled manually.
Open the software, then navigate to, Configuration File –> Advanced –> HTTP Proxy Server –> Enable HTTP Proxy Server Support.
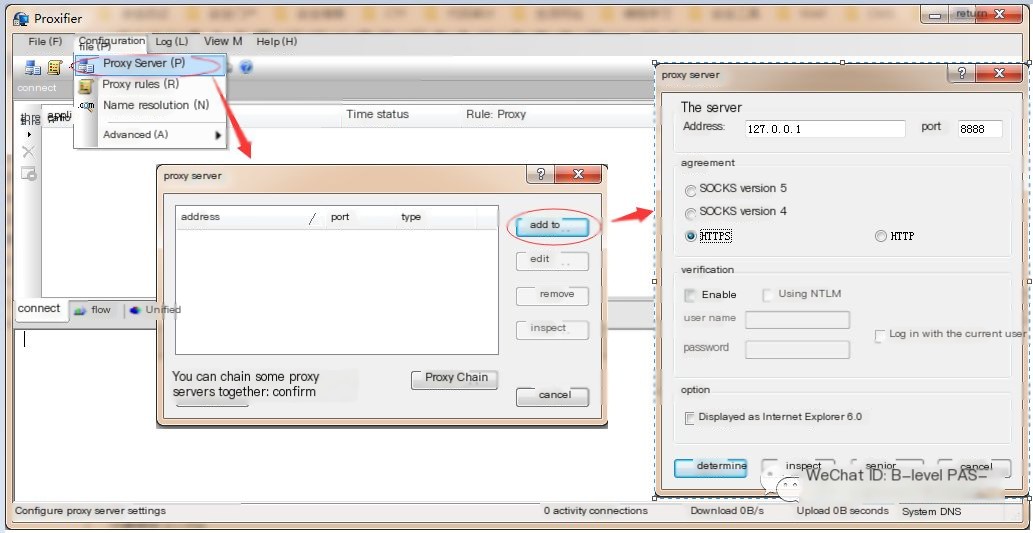
B. Match proxy server settings with Fiddler, then navigate to Configuration File –> Proxy Servers -> Add.
C. Set proxy rules, usually the default rule, Fiddler.exe [auto-created], suffices. If not available, it needs to be manually created.
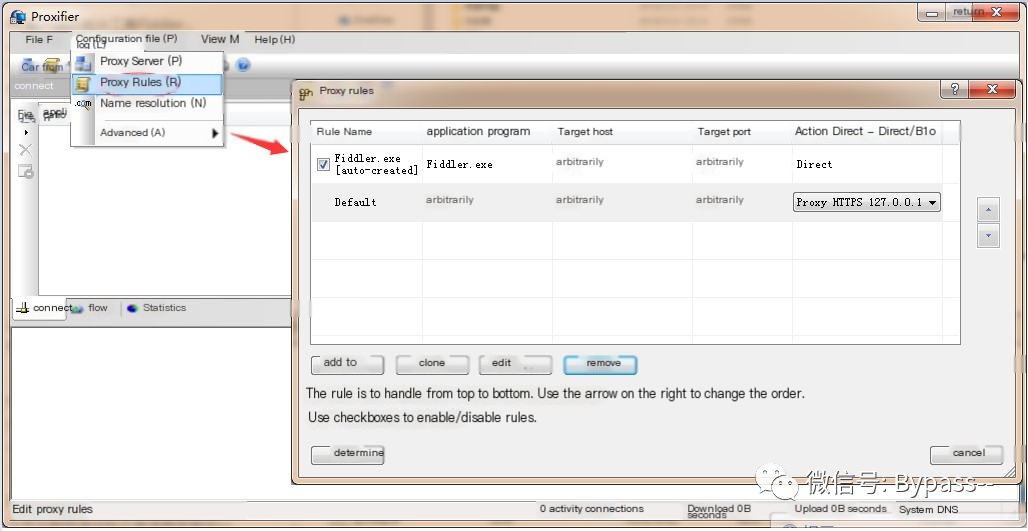
For manual creation, click Add and configure the settings as follows:
Name: Custom, check the "Enabled" option.Application: Select the Fiddler application file directory, add as required.Target Host: Our local Fiddler proxy settings, can be arbitrary.Target Port: ArbitraryAction: Direct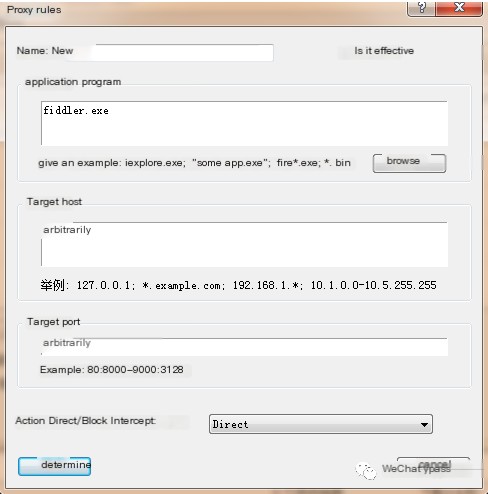
Fiddler Configuration
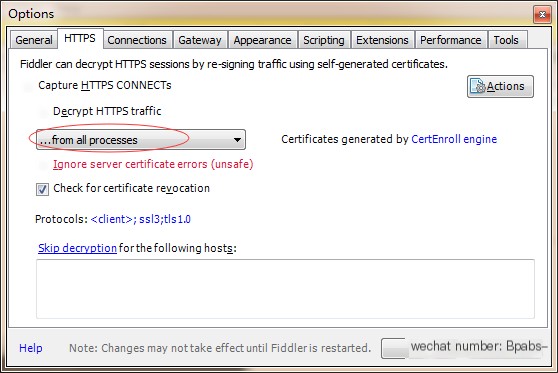
1. Open Fiddler->Tools->Options->HTTPS, then check all options, ensure “From all processes” is selected.
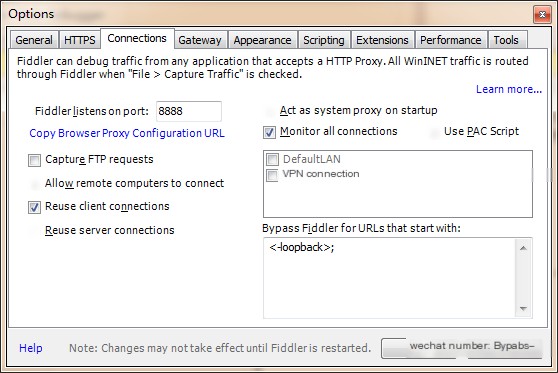
2. Connection->Fiddler Listening Port: 8888, ensure this port matches the Proxifier proxy port.
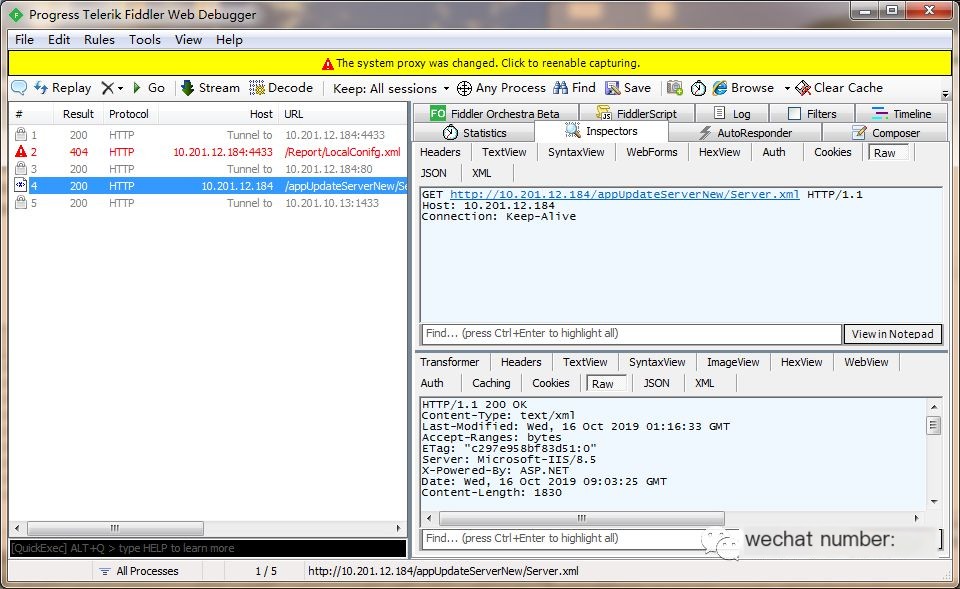
Packet Capture Test
Once setup is complete, you can observe the communication process and protocols in Proxifier.
Acquire specific HTTP request data in Fiddler: