Redline is FireEye’s first free endpoint security tool, providing users with host investigation capabilities by detecting signs of malicious activity through memory and file analysis as well as the development of threat assessment profiles. Use Redline to collect, analyze, and filter endpoint data and perform IOC analysis and hit review. Redline also features a nice GUI and can categorize data very neatly.
Table of Contents
- Redline Download and Installation
- Redline Collector
- Redline Collection Process
- Analyzing Data Collected by Redline
Redline Download and Installation
Visit the link below and fill out the form to download:
Run with administrator privileges after installation.
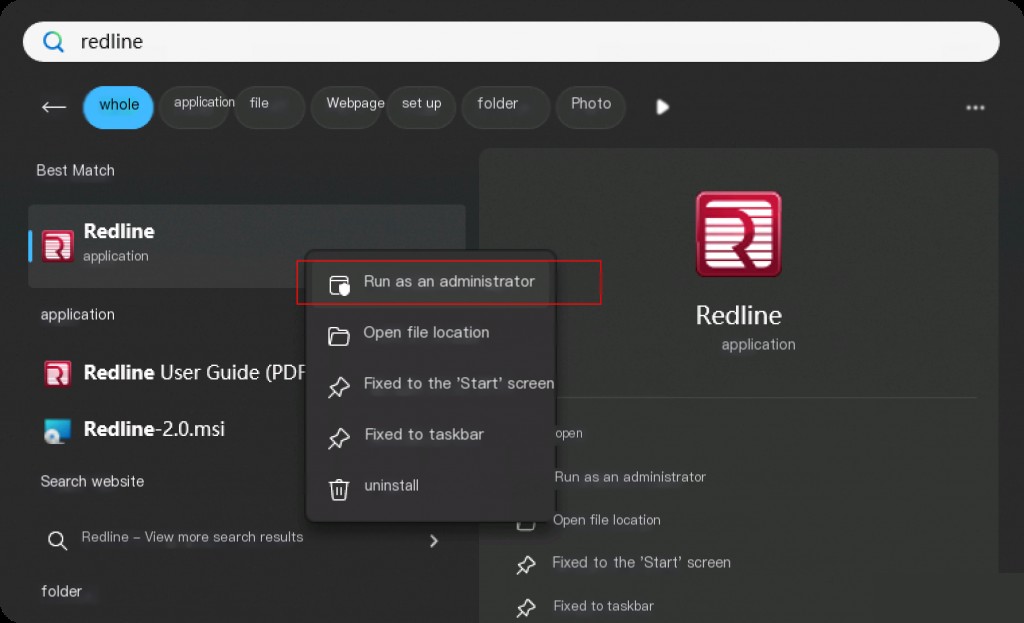
Redline can categorize registry, running processes in memory, browser data, scan known bad and suspicious strings in the system, etc. We can customize what to scan before running the Redline collector. The Redline collector is responsible for acquiring the user-configured data. It then creates a Mandiant session file for forensic personnel to quickly parse and categorize. It provides a one-stop collection and analysis service for forensic personnel.
Redline Collector
Let’s focus on the “Collect Data” section first. There are 3 types of collectors in Redline.
- Standard Collector: The standard collector configures scripts to collect the minimum amount of data required for complete analysis.
- Comprehensive Collector: The comprehensive collector configures scripts to collect most of the data that Redline collects and analyzes. If you intend to conduct a thorough analysis or have only one chance to collect data from a computer.
- IOC Search Collector (Windows only): The IOC search collector collects data that matches the selected Indicators of Compromise (IOC). If you are only looking for IOC matches and not any other potential intrusions.
By default, the IOC Search Collector filters out any data that does not match the IOC, but you can also choose to collect other data. If not using the IOC search collector, you can still analyze data collected using IOC after importing it into Redline to create an analysis session. The effectiveness of IOC analysis depends on the data available in the analysis session.
In actual investigations, if the goal is to quickly conduct a comprehensive categorization analysis, it is recommended to use the comprehensive collector. If you are in the process of emergency response and looking for specific IOCs in the network, then the IOC search collector is a better choice.
Redline Collection Process
Click “Create Standard Collector”.
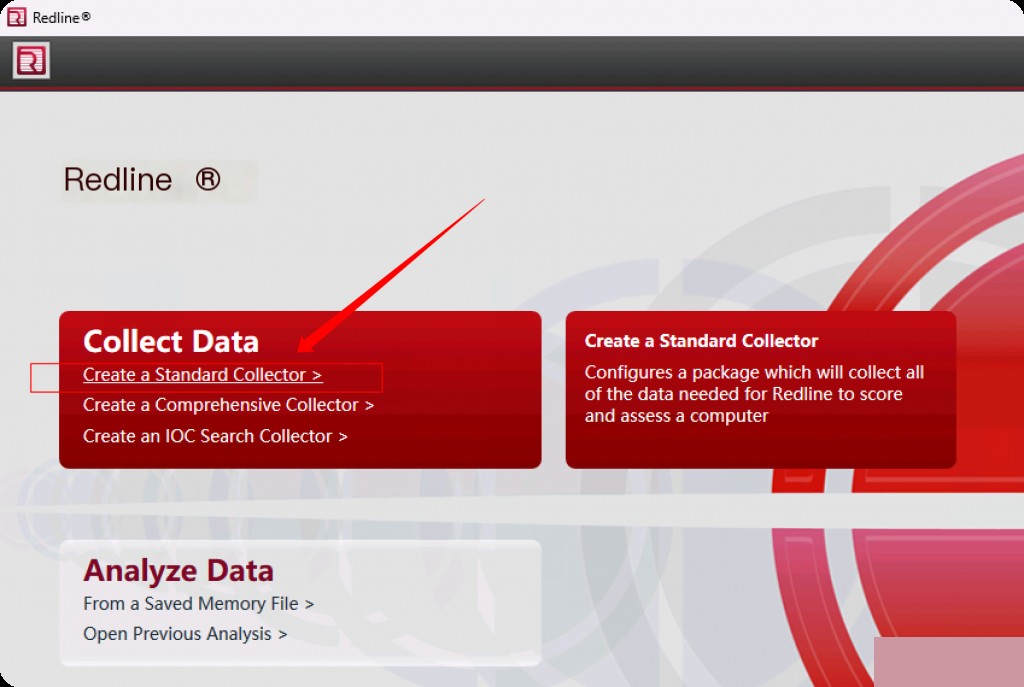
Here we select the target platform for acquiring and categorizing data as Windows. Then click the “Edit” script option, as you can configure the types of data you are interested in here. You can also remove unnecessary options that are not of interest to save time, especially during an emergency response event.
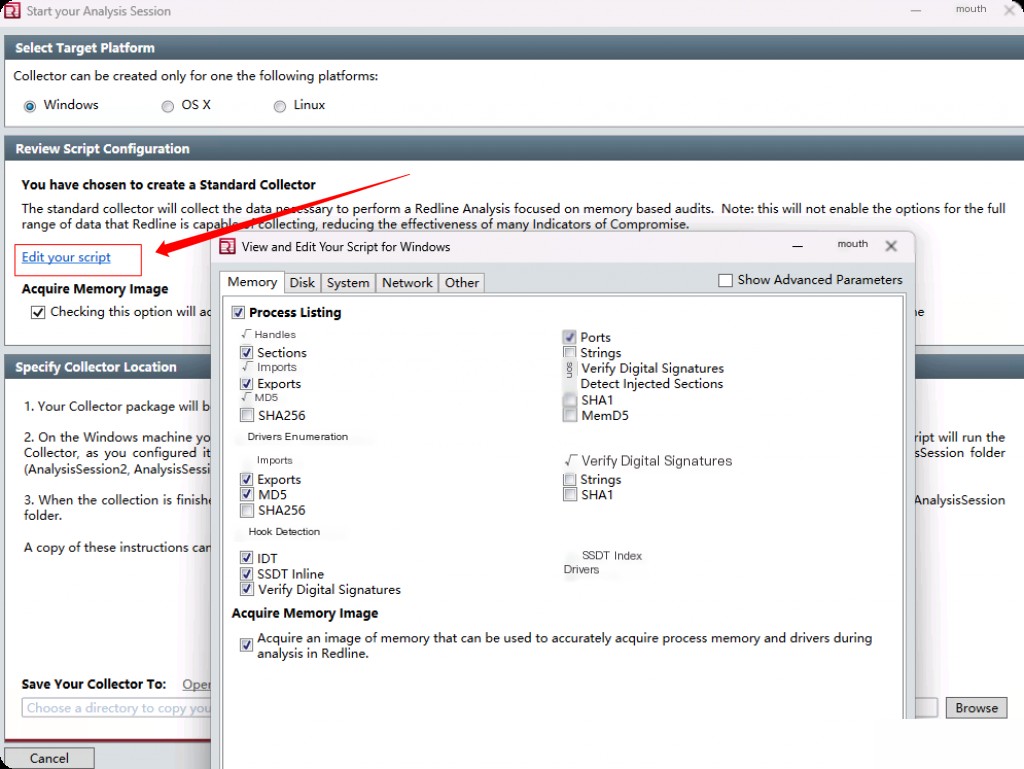
Next, enter the “Disk” section. We select the following options for quick and basic categorization.
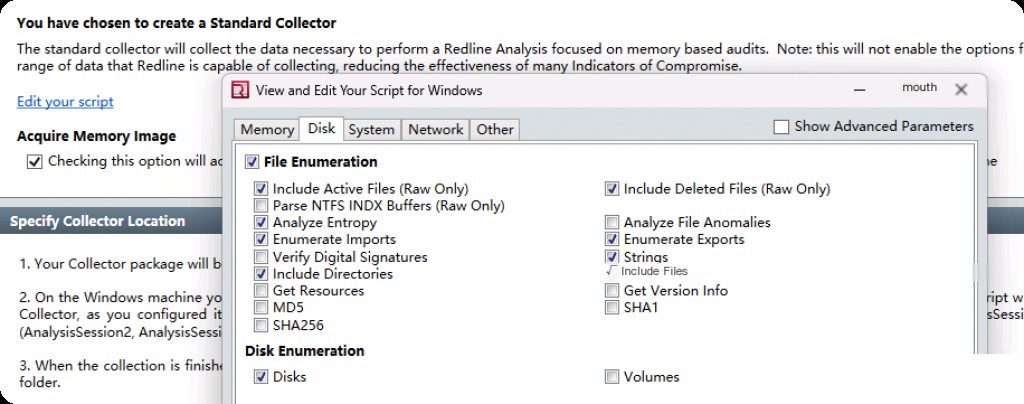
Enter the “System” section and select the following options.
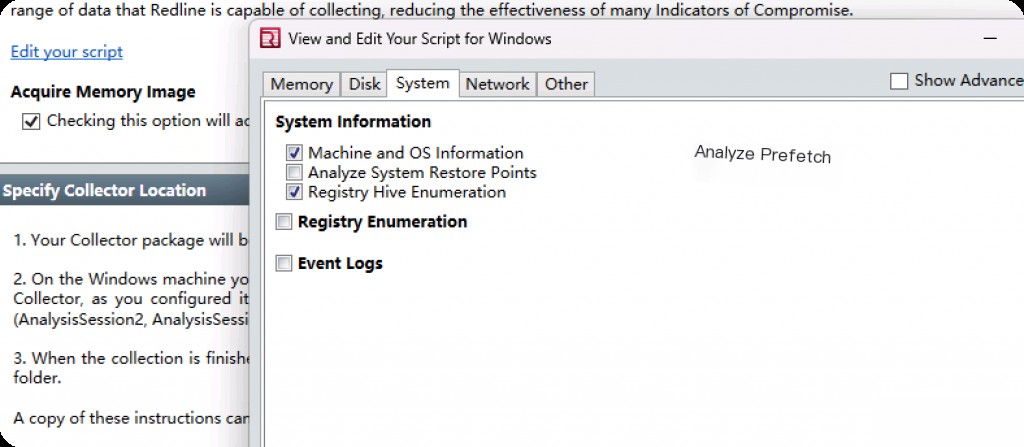
We can choose the event log option to view system restore points, which is also a good data source. It all depends on the emergency needs and how much time can be spent during the event.
Then go to the “Network” tab and select some common options. We can also choose browser data, which is likely an important source of malicious activity.
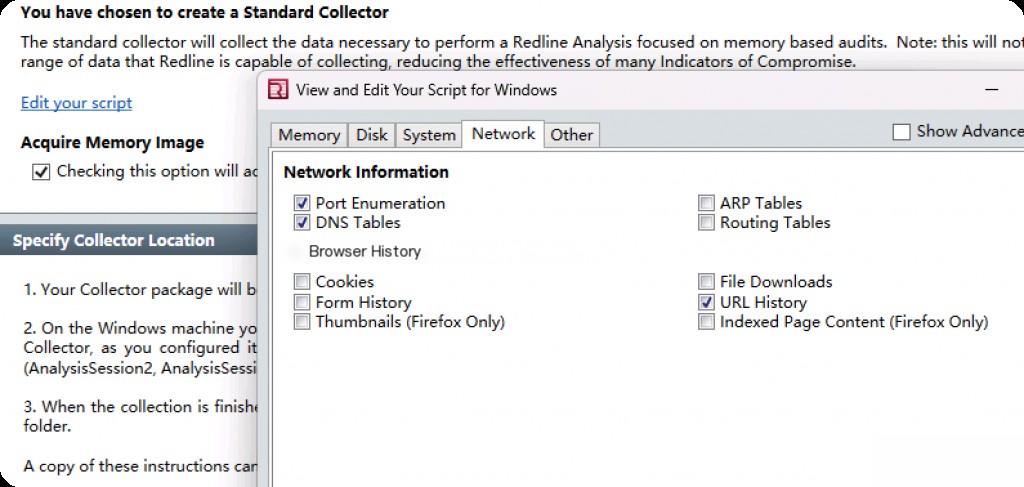
The remaining part is “Other”, which is also very useful for forensic personnel.
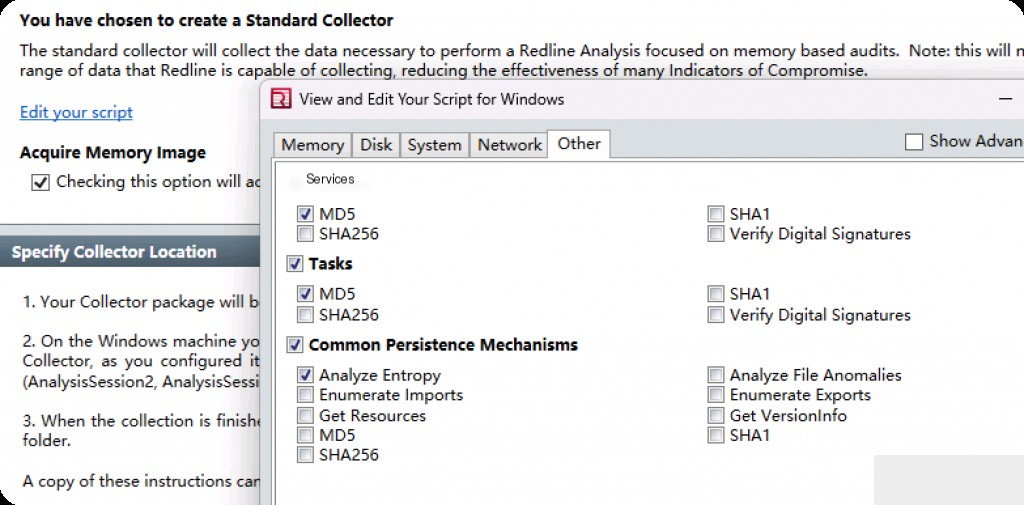
We can configure Redline to look for some abnormal behavior, especially persistence traces on the system.
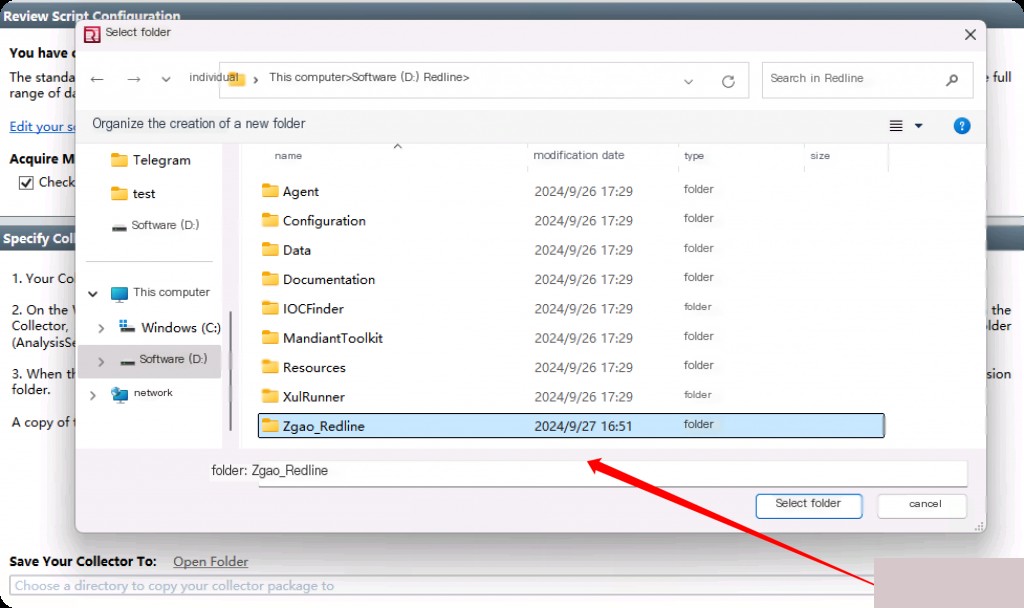
Click OK, then go to the bottom of the main interface and click Browse. Here you will select where to place the collector script and store the categorized data after running the script.
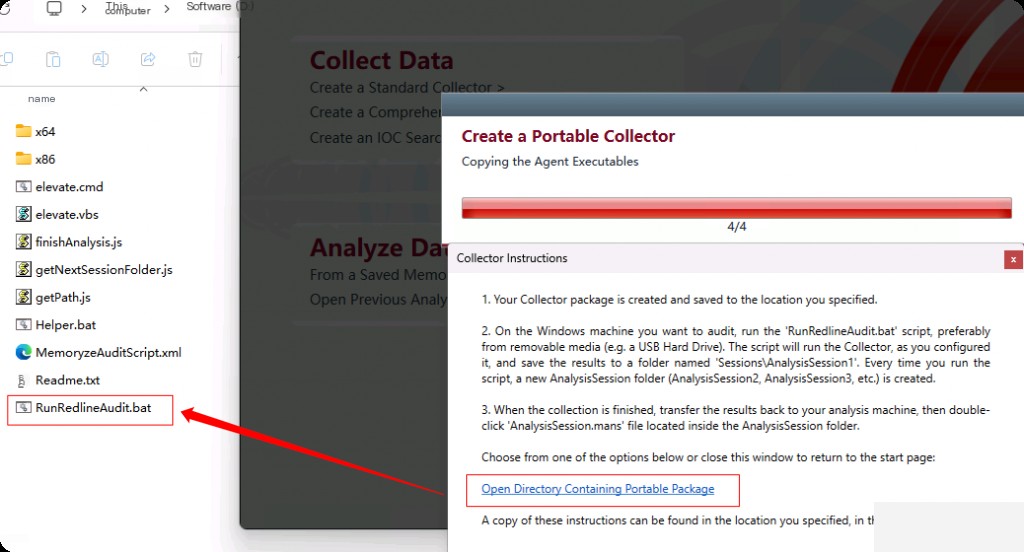
The batch script named “RunRedlineAudit” here is the main script we will execute, which acquires data and categorizes it from the system. The best feature of the collector script is that we can save the collector script on a network drive or store it on a USB, and whenever an event occurs and we want to categorize the endpoint, we can run the script directly from the USB or network drive. We can create different types of collectors through pre-configuration and saving, so we don’t need to keep creating new collectors before categorizing the endpoint.
Analyzing Data Collected by Redline
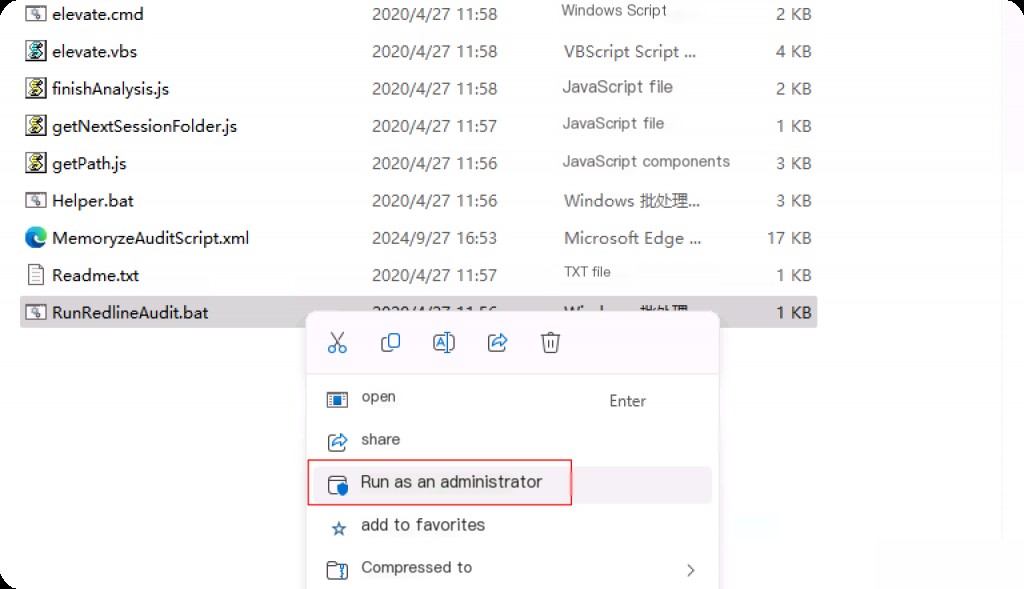
Run the collector script “RunRedLineAudit” as an administrator, which will open a cmd prompt to display the progress of the categorization.
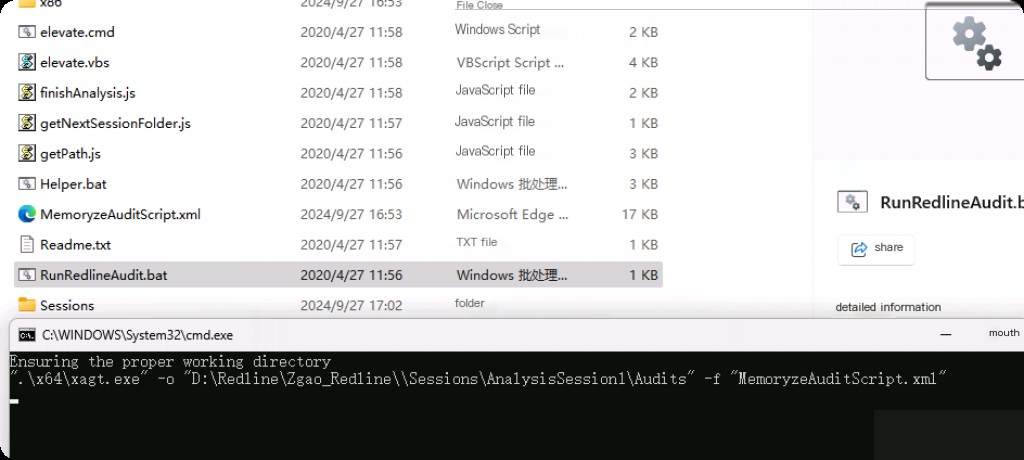
The path after the option “-o” is “D:\Redline\Zgao_Redline\\Sessions\AnalysisSession1\Audits”, and the Mandiant file will be saved at this location with the extension “.mans”. This file will contain all the categorized data, which can be analyzed in a categorized manner. When we edit the script and set the above preferences, the XML file “MemoryzeAuditScript.xml” stores our configuration.
Once completed, cmd exits. Go to the folder where the collector script was installed, and you can see a “Sessions” folder. AnalysisSession1.mans is just a file, the actual data is stored in the Audits directory.
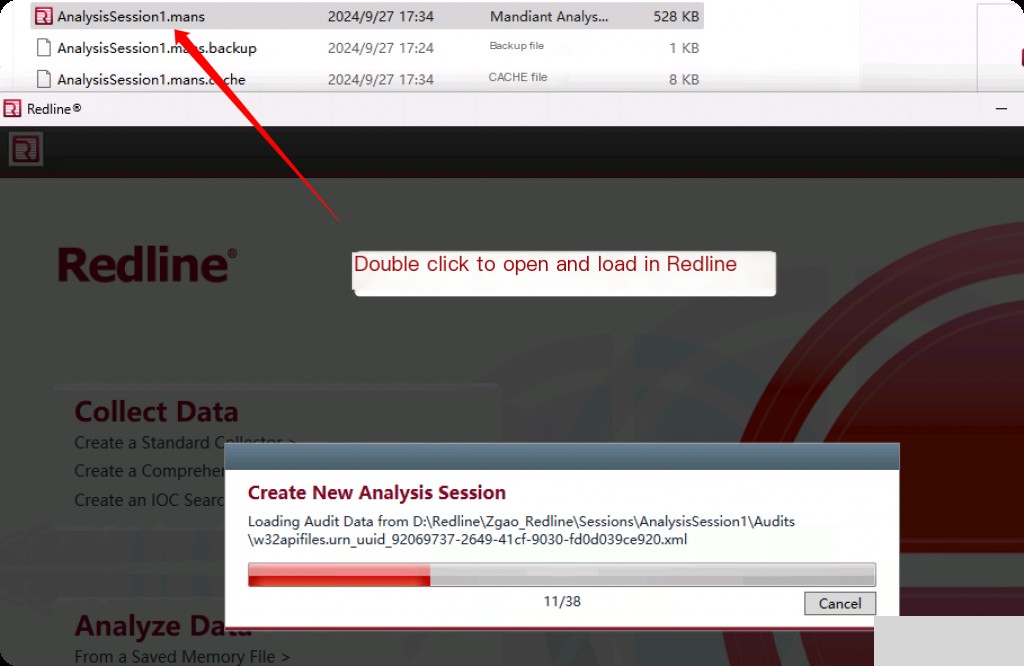
Redline takes about 10 minutes to load the file, then enters the main interface.
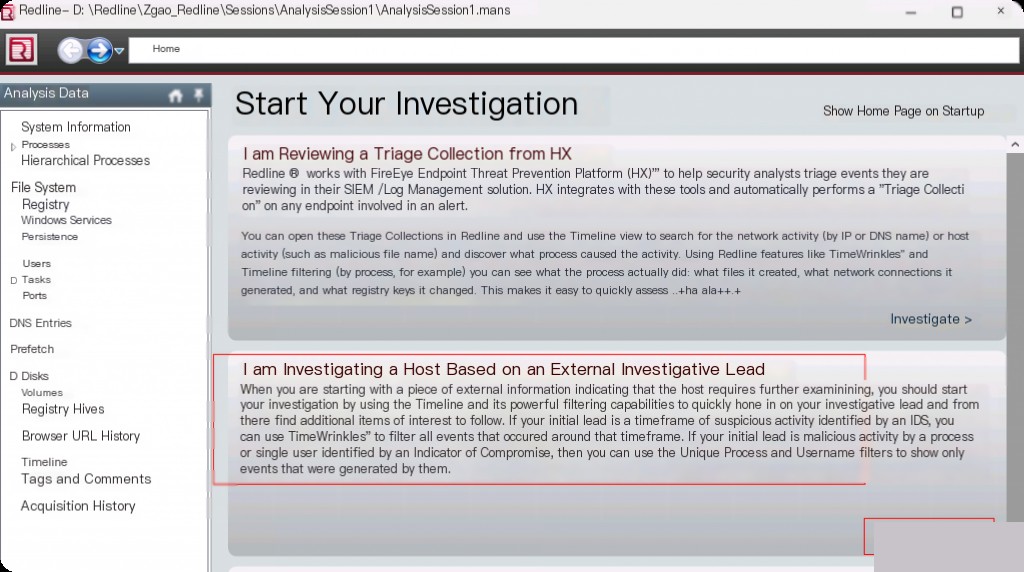
Select the second option “I am investigating a host based on external investigative leads”. If we are interested in browser forensics, select option 3. Similarly, when using known IOCs for threat hunting, you can choose the last option. If using the FireEye Endpoint Threat Prevention Platform (HX) at the same time, the first option will be useful, and the whole process will be faster and more automated.
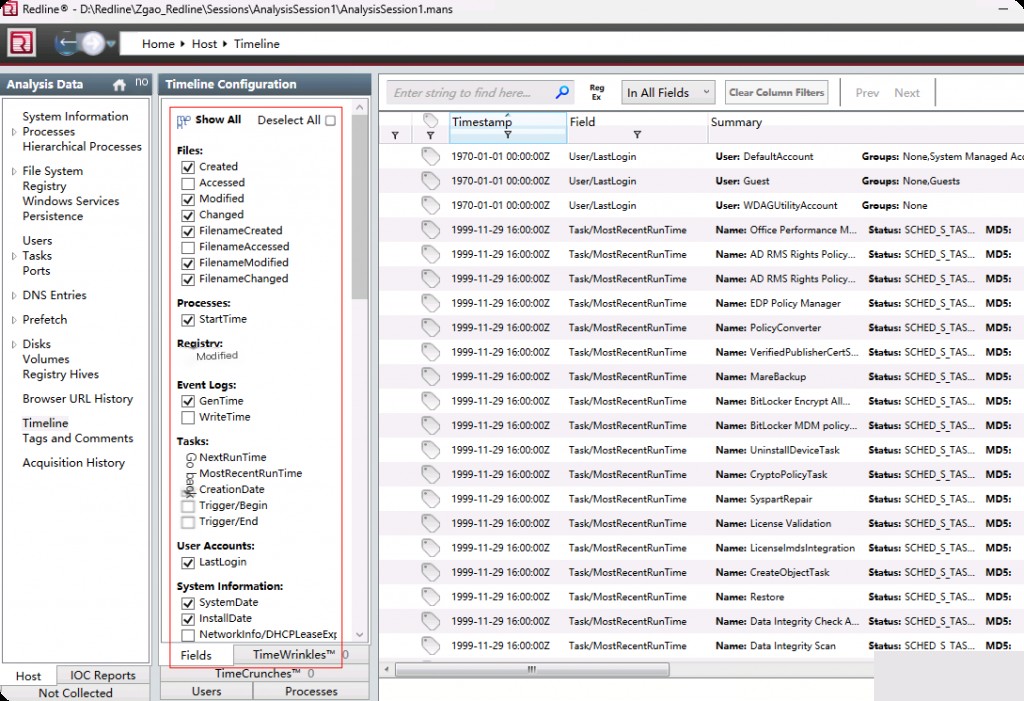
We can see different information from different data sources. If memory categorization is selected, a very detailed tab about memory-related data will be displayed. If a complete file system categorization is performed, all relevant data can be seen. We can check/uncheck any information as needed.


