1 Capturing an HTTPS Packet with Wireshark
By using Wireshark to analyze HTTP packets, whether they are GET or POST requests, everything is visible during network transmission, not to mention any privacy information. So how do we protect privacy information? HTTPS is a good choice.
The main advantage of HTTPS over HTTP is that all communication packets use encryption technology. However, there are many different encryption methods currently, and actual situations should be considered during analysis.
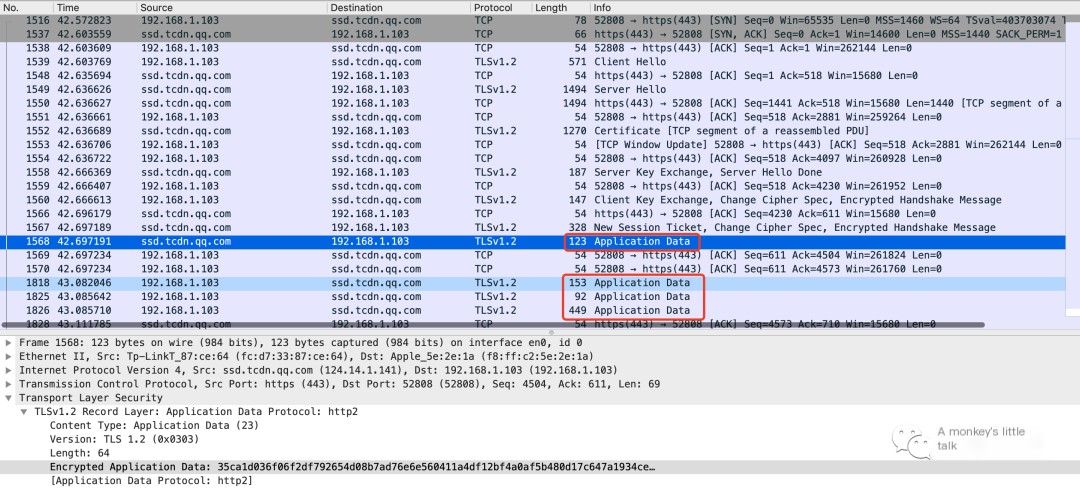
The favorite activity of programmers is listening to a song from dawn to dusk. The above image is a packet captured when opening QQ Music. A simple filter condition can be set using tcp.port == 443. Obviously, the packets are all encrypted, and we know almost nothing about them.
2 Stripping the Encryption from HTTPS with Wireshark
Encrypted packets pose significant obstacles to troubleshooting, so it is very necessary to know how to decode them. Next, let’s see how to use the Wireshark tool to strip the encryption from HTTPS.
Method One: Decrypt Using Log Files.
Step One: Record the Key, and prepare.
# Set environment variableexport SSLKEYLOGFILE=$PWD/keylog.log# Stop all other Chrome processes, then execute this command in the terminal to start a new Chrome processopen -n /Applications/Google\ Chrome.appAfter configuring as above, the browser will record the Key used for decrypting session data to the keylog file after each HTTPS session ends.
Step Two: Use the Key to decrypt byte data.
Open Wireshark, select Preferences -> Protocols -> TLS, and configure to access the keylog file, as shown in the following image.
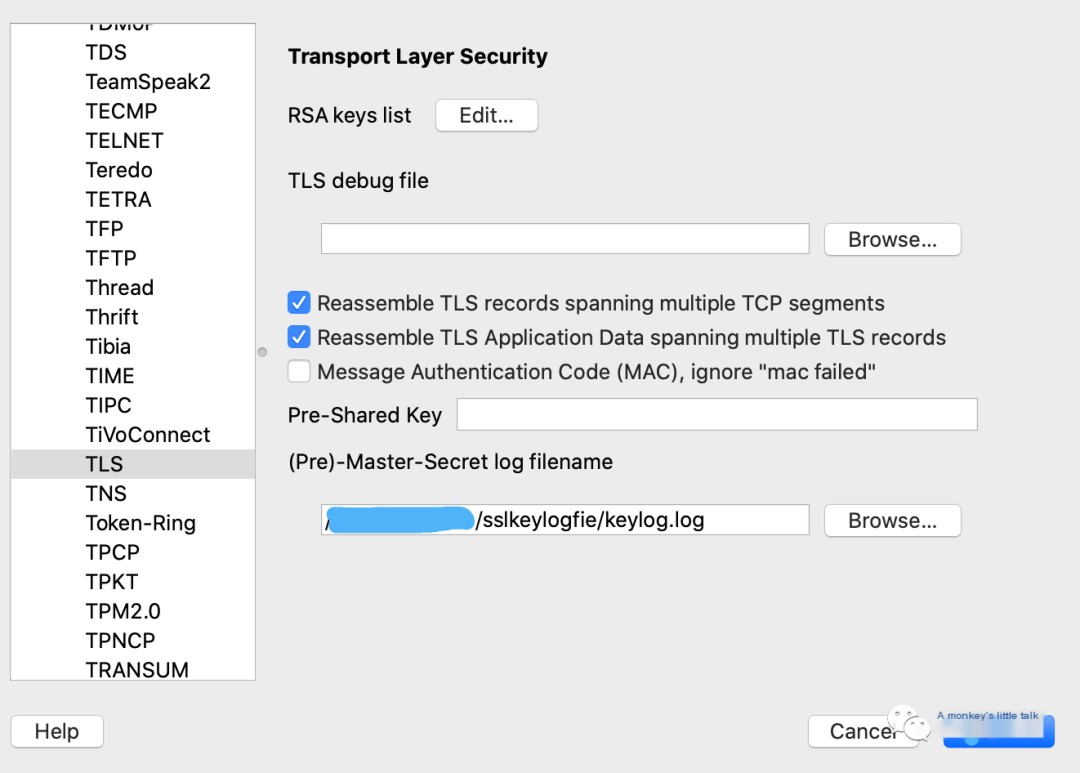
Click OK, and you will successfully decrypt the captured HTTPS session data stream. It’s really impressive.
Method Two: Decrypt Using RSA Key Files.
For convenience, let’s directly use the official example for demonstration.
Step One: Extract snakeoil2_070531.tgz and remember the location of the rsasnakeoil2.key file.
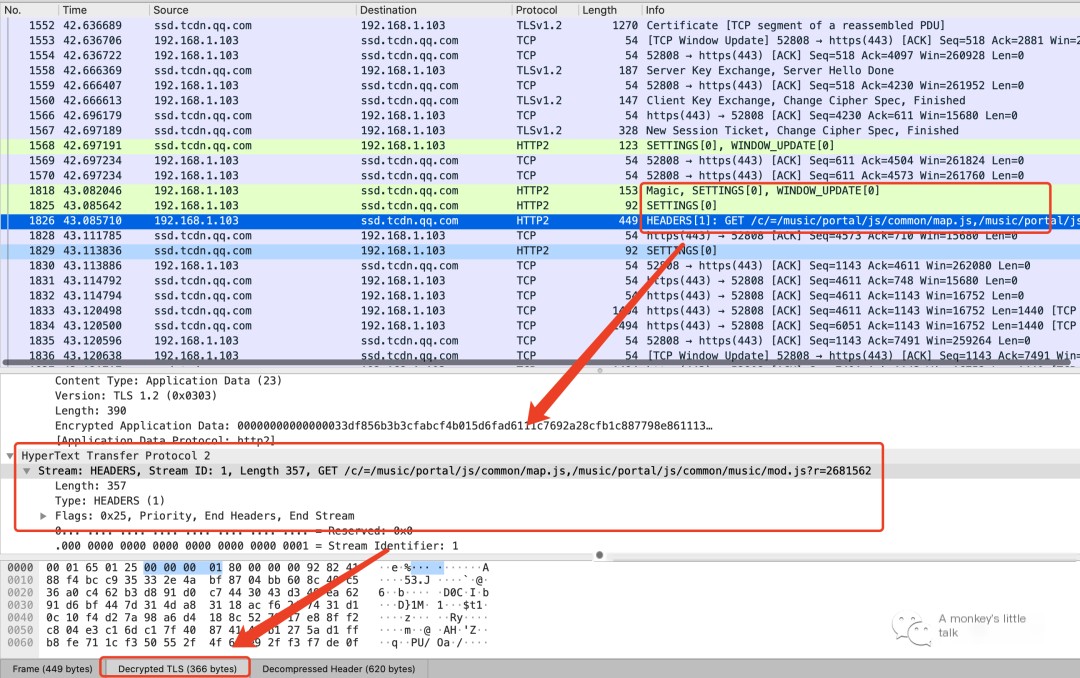
Step Two: Open rsasnakeoil2.cap with Wireshark.
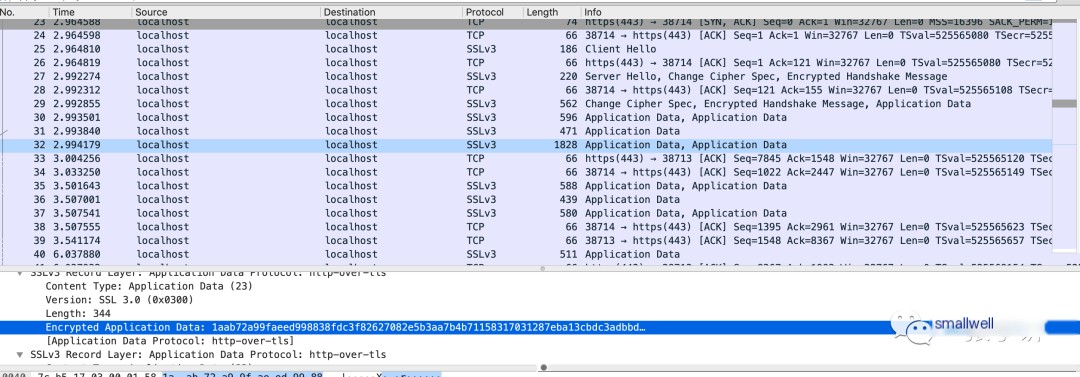
Step Three: Select the Key File to Decrypt.
Clever Tip One: In Wireshark’s menu bar, select Edit -> Preferences -> Protocols -> TLS, then configure the server address, port, protocol, and RSA key file in the pop-up window.
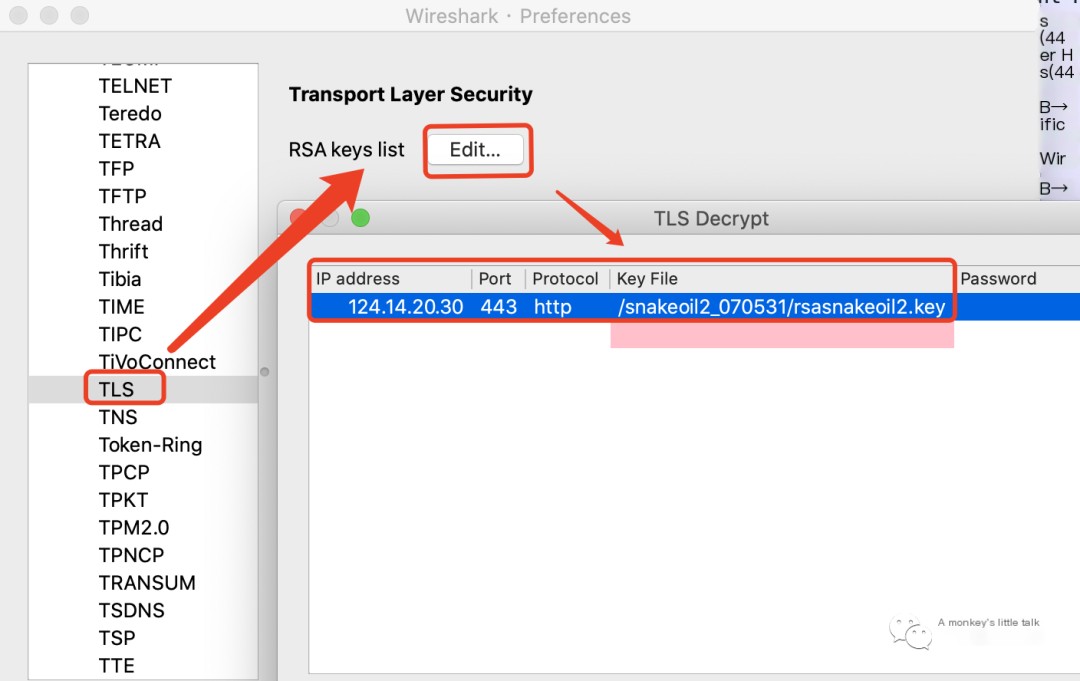
After configuration is complete, you can successfully decrypt the HTTPS packet provided by the official source.
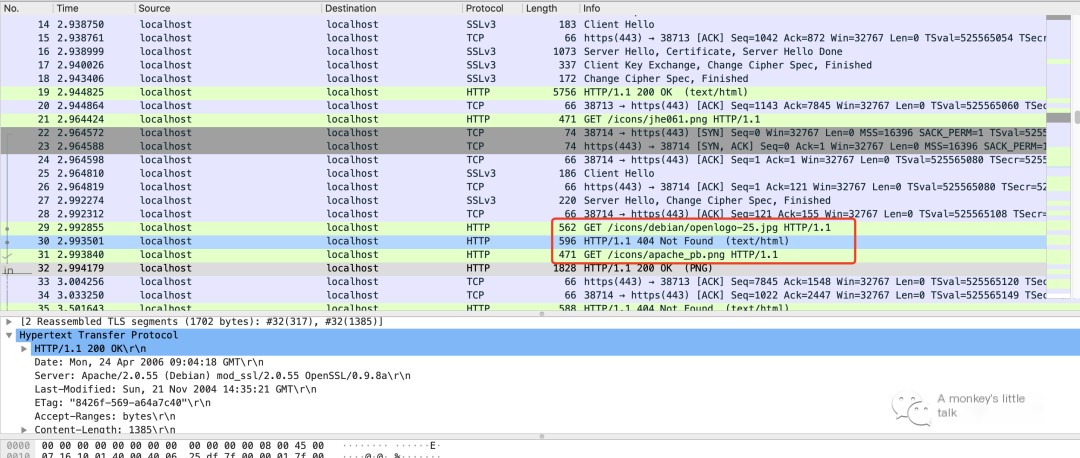
Clever Tip Two: Click Wireshark’s Edit -> Preferences -> RSA Keys. Then select the key file, as shown in the following image.
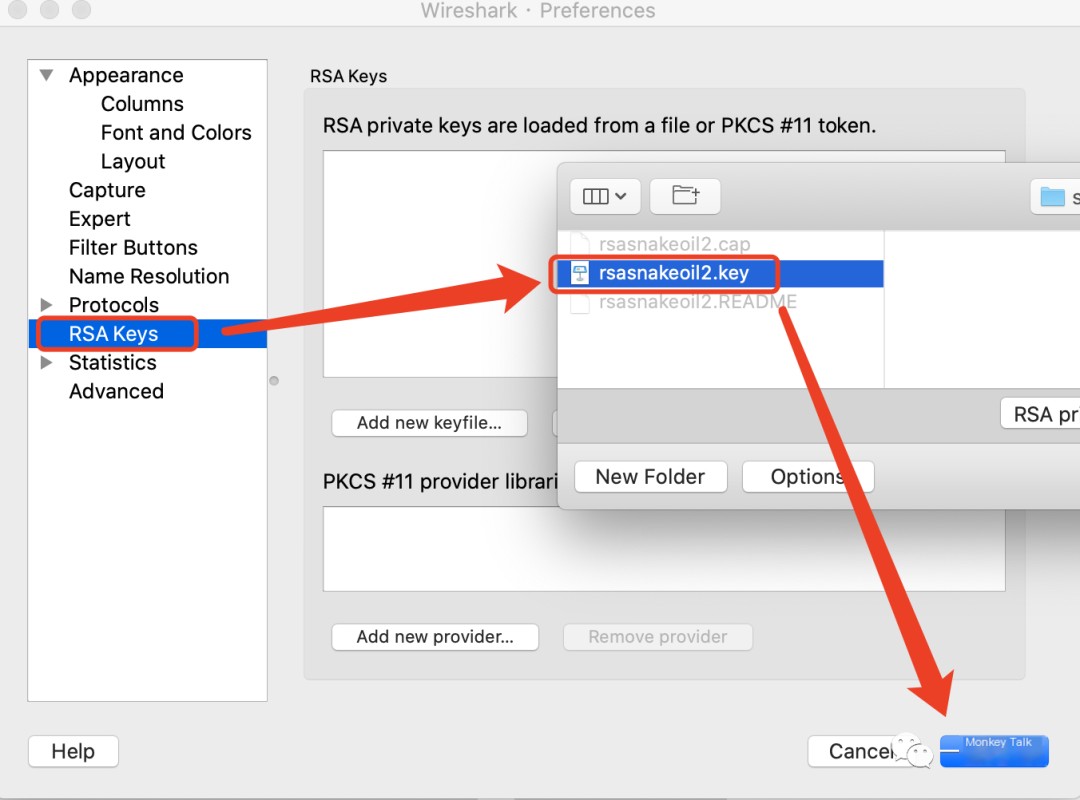
Then click Wireshark’s Edit -> Decode As -> OK, and the packet is successfully decoded. The appearance of HTTPS after stripping the encryption is once again completely visible.
3 All About the HTTPS Handshake
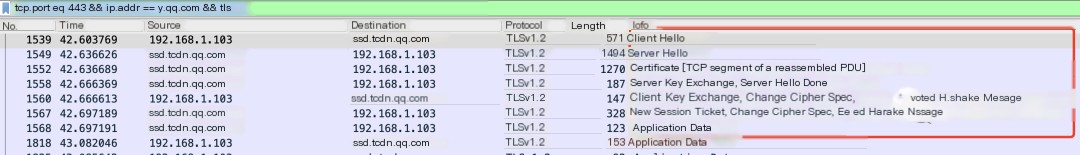
The process of HTTPS handshaking is very clear with the help of Wireshark. If you’re interested, you can peel away layer by layer like peeling an onion for analysis. This time, we will not dive deeper.
4 Conclusion
The experience gained from practical application is profound and often surpasses theoretical knowledge. This Wireshark tutorial will end here. To ensure there are no mistakes, many documents, books, and official materials were consulted, summarized, and organized for you. I hope it is helpful to you.
Resource Sharing:
Classic Example: https://gitlab.com/wireshark/wireshark/-/wikis/SampleCaptures Official Documentation: https://www.wireshark.org/docs/wsug_html_chunked/
You can get the shared data packet from here:



