Windows Live Response
Windows Live Response is crucial in detecting, responding to, and analyzing cybersecurity incidents. Implementing an effective Live Response strategy in a Windows environment is key to quickly detecting threats, mitigating damage, and ensuring business continuity.
System time is essential for accurately determining the timeline of events, such as whether the system is using UTC time or CST time. To determine the event timeline, it is necessary to understand the sequence of events and the timing of potential security breaches.
System Time: Live Response
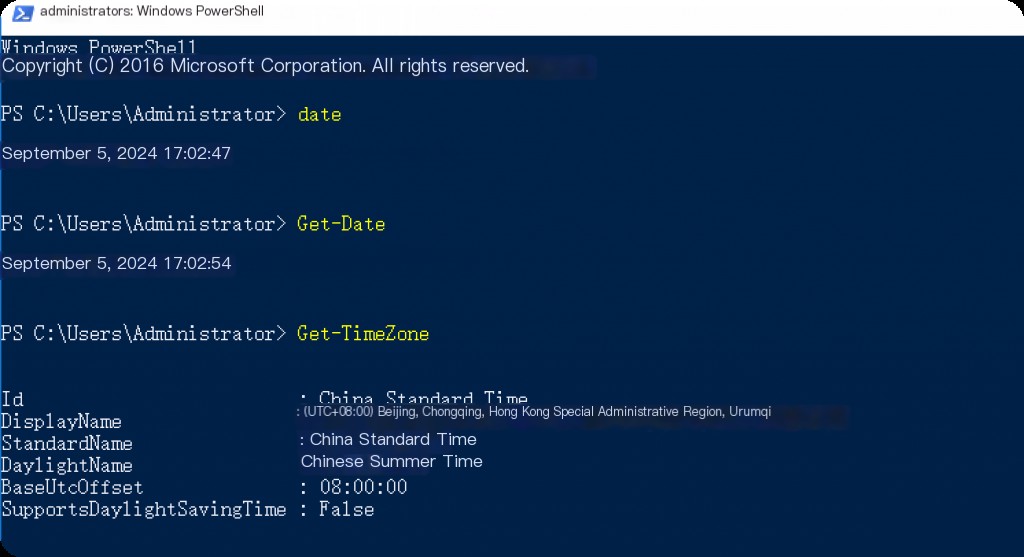
In Windows, you can use the PowerShell commands “date” or “Get-Date” to view the system time. Additionally, you must verify the accuracy of the system time and time zone. This can be done by going to the Time & Language settings.
date Get-Date Get-TimeZone
Running Processes: Live Response
Analyzing running processes is necessary for detecting anomalies or suspicious activities on the system. Malware or malicious processes are often found among the running processes on the system. You can use Task Manager, the “Tasklist” command, or the PowerShell “Get-Process” command to view the running processes on the system. These tools display the process name, ID, and resource usage.
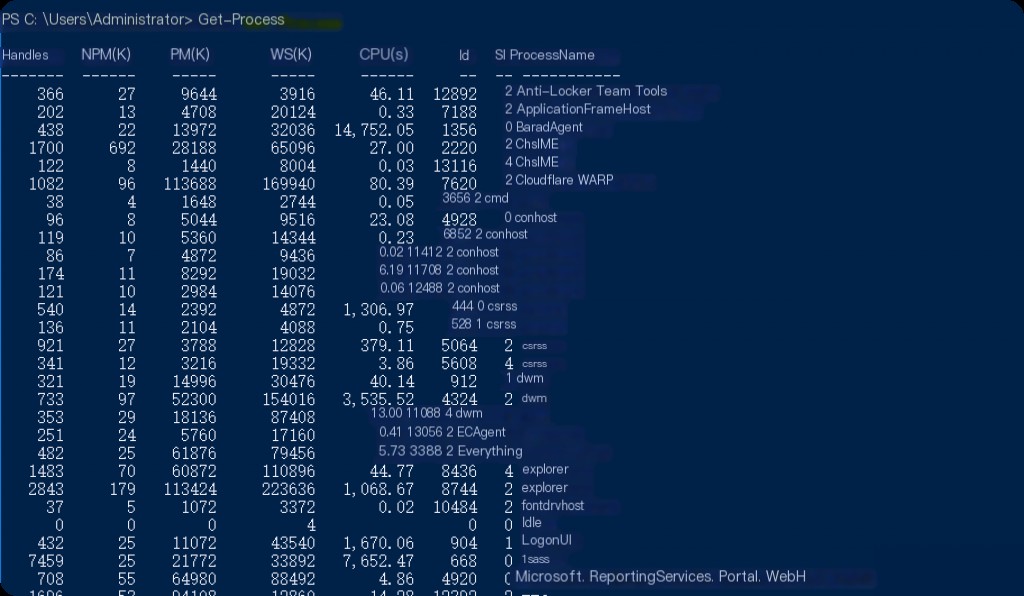
You can use the “Get-Process | findstr ” command to display information only for the searched process.
Get-Process | findstr v2ray
Clipboard: Live Response
Clipboard data can reveal what information users are copying and the risk of potential sensitive information being exploited. Malware can use the clipboard to intercept sensitive information.
Clipboard history is disabled by default and needs to be enabled manually.
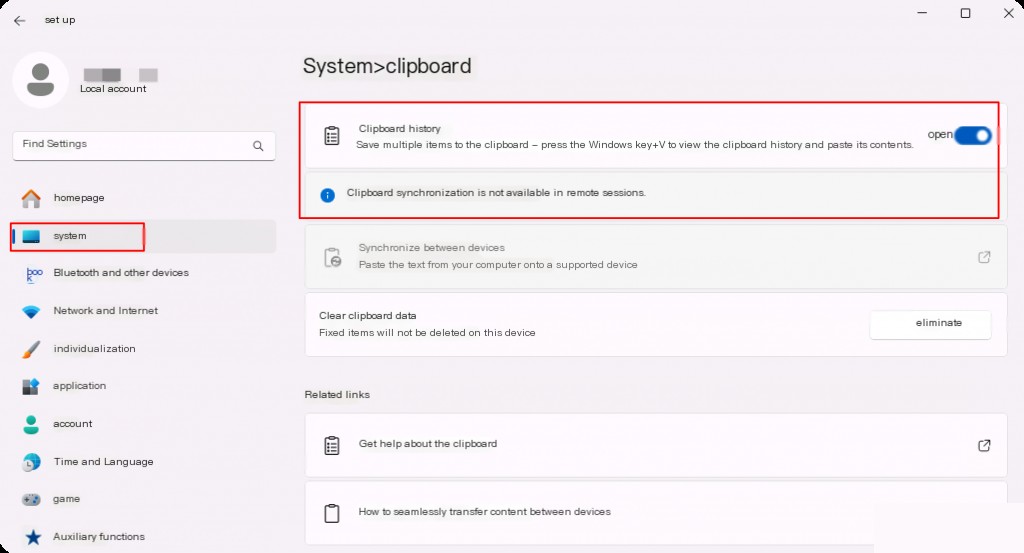
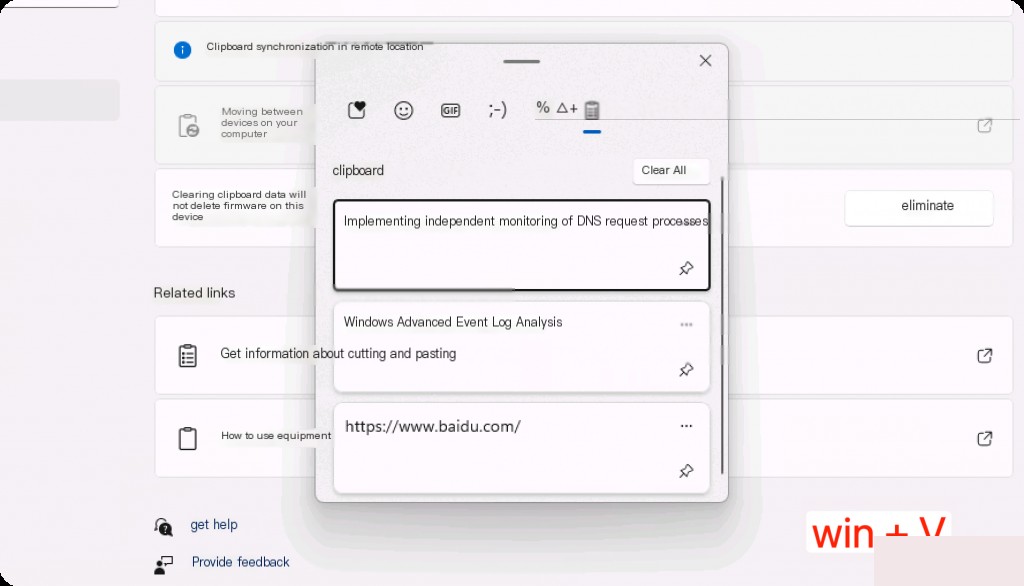
In Windows 10 and later versions, you can view the clipboard by selecting Start > Settings > System > Clipboard, or by using the Win + V shortcut.
Logged-In Users – Live Response
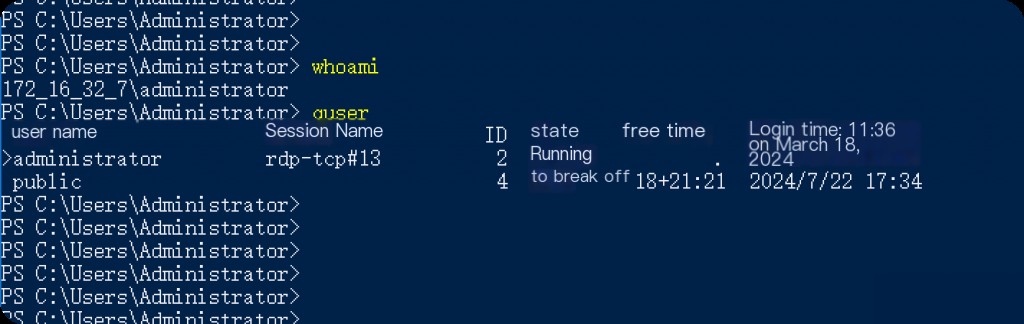
Identifying users logged into the system helps in recognizing unauthorized access or internal threats and understanding which user is active on the system. The “whoami” command can be used to get the account information of the logged-in user, while the “quser” command can be used to list active users.
whoami quser
Command History
Command history is a critical part of understanding system operations and potential malicious activities. Analyzing commands used by malicious users/software helps understand the attack vector. The “Get-History” command in PowerShell and the “doskey /history” command in CMD display the command history during a session.
Get-History
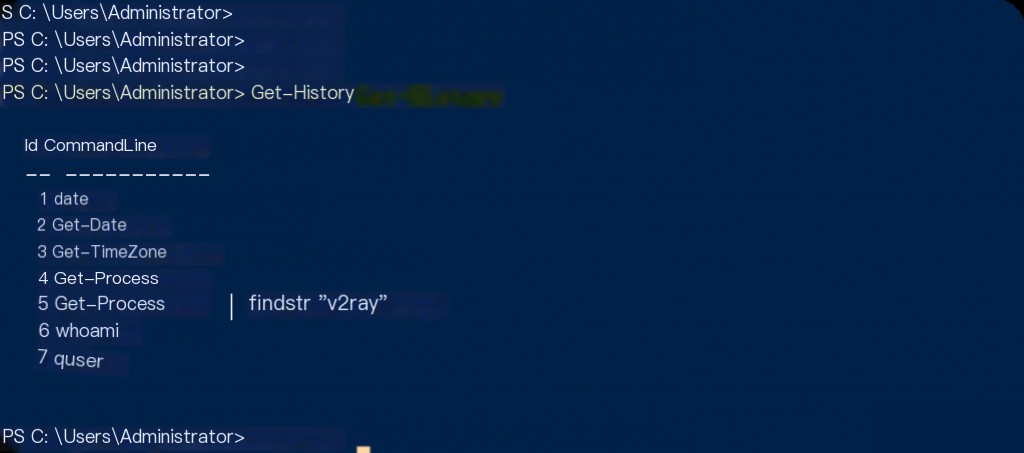
This command only displays the command log for the active session. To find the file storing commands executed in all sessions, you can run the following commands and view the file contents as output.
(Get-PSReadlineOption).HistorySavePath type C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
This will show the historical PowerShell command execution records.
Open Files
Open files show which applications and files are being used, which is crucial for detecting file-based malicious activities or data leaks. Note:
- To enable “openfiles,” you need to open PowerShell with administrator privileges and run the command
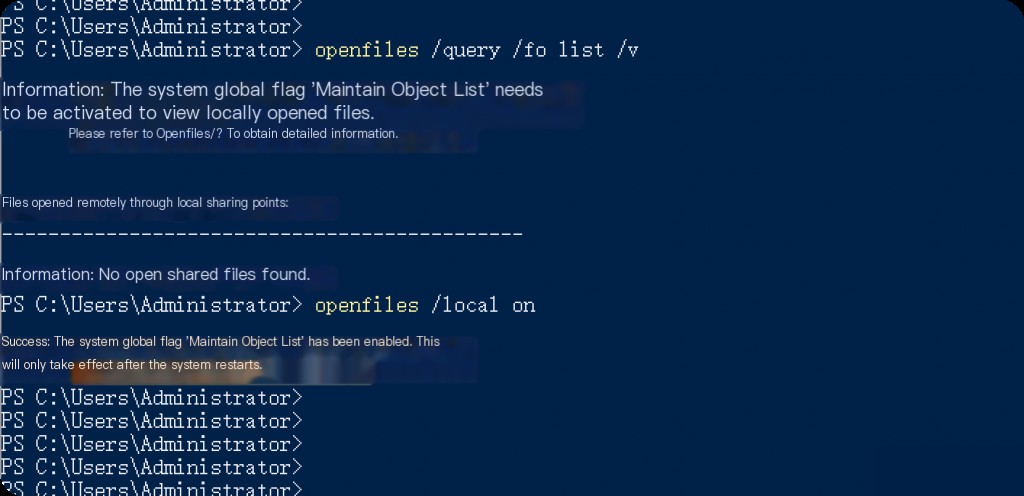
openfiles /local on, then restart the system for it to take effect. - Open the PowerShell command line with administrator privileges to use the “openfiles” command.
The openfiles command provides a list of open files on the system. It provides detailed information about file paths, file access methods, and which processes are using which files.
openfiles /local on
The openfiles command has three parameters:
- /query: Displays open files and their using processes. This helps understand which user/process is using these files.
- /disconnect: Ends the connection to open files. It is used to disconnect open files connected to a specific file, user, or session.
- /local: Displays locally open files, useful for monitoring file usage on the local system.
openfiles /query /fo list /v
Network Status and Connections
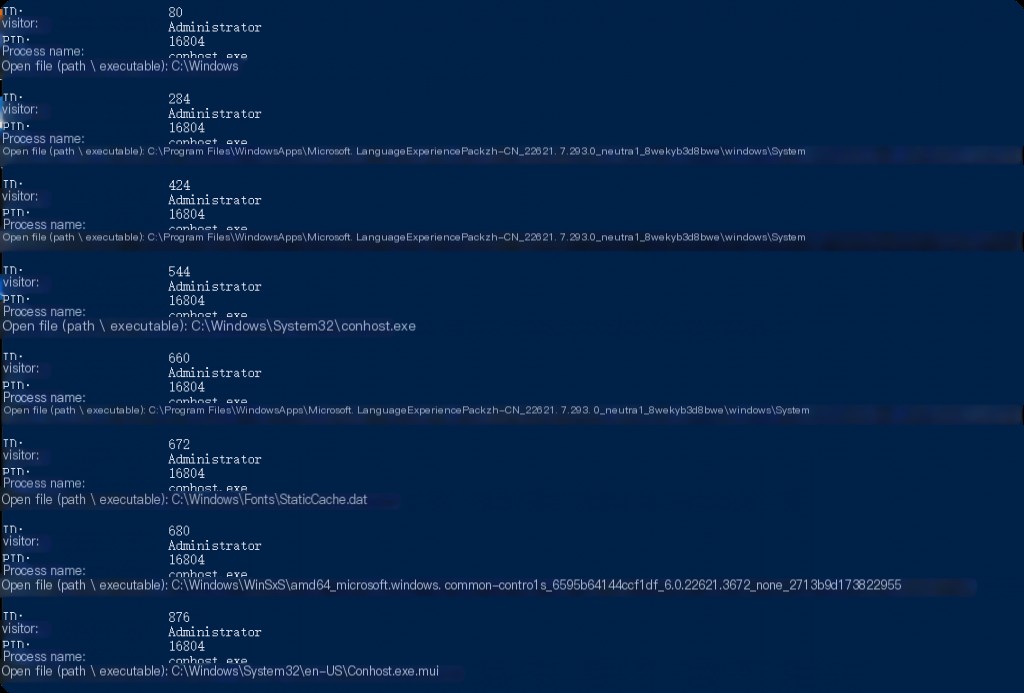
The status of the network and its connections is crucial for monitoring external communication channels and potential malicious network activities. Suspicious network traffic plays a vital role in identifying attacks, data leaks, or unauthorized access attempts.
The “ipconfig” command displays network interface information, while the “netstat -ano” command displays active connections and listening ports. For detailed output on TCP and UDP connections, use the “Get-NetTCPConnection” and “Get-NetUDPConnection” cmdlets in PowerShell.
netstat -ano netstat -ano | findstr ESTABLISHED netstat -ano | findstr LISTEN
Windows File System
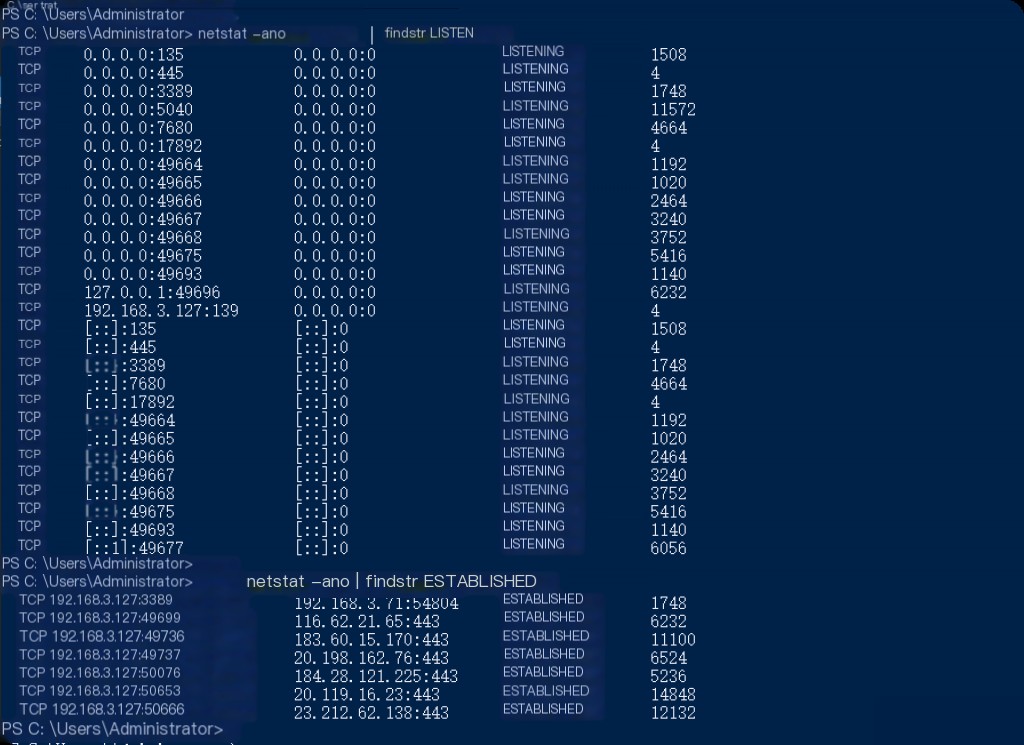
The file system in the Windows operating system provides data storage, data management, and data access information that is crucial for digital forensics. Effective Windows forensic analysis requires understanding how these file systems work, their basic attributes, and how to use them for forensic investigations.
NTFS and FAT file systems are the foundation of data management and security in Windows environments, playing a core role in collecting and analyzing digital evidence in forensics. You can use PowerShell commands to view the file system types on the system:
Get-Volume
NTFS
NTFS (New Technology File System) is a file system developed by Microsoft for the Windows operating system. It offers high performance, high reliability, and efficient use of hard disk space. It supports large disk partitions and large files, utilizes disk space more efficiently, and provides extensive file access permission options. It also has advanced features such as file compression, disk quota management, and symbolic links.
Access Control Lists (ACL): NTFS uses access control lists to control access to files and folders. These lists define and manage user and group permissions for accessing files. Permissions for specific operations (such as reading, writing, executing, and deleting) can be set for files and folders.
Encrypting File System (EFS): NTFS has built-in encryption capabilities. EFS protects users’ sensitive files from unauthorized access through encryption. Only the user who encrypted the file or an authorized recovery agent can access files encrypted with EFS.
File and Folder Logging in NTFS File System
NTFS maintains consistency even after sudden system failures through its file system logging feature. This feature ensures that file system operations can be safely undone or completed even after a system crash or power outage.
Using NTFS Metadata for Forensics
NTFS stores a wealth of metadata about files and folders. This data is crucial for digital forensic investigations.
MFT (Master File Table): Contains records for every file and folder. It includes the file name, creation date, modification date, access date, size, and location.
USN (Update Sequence Number) Journal: Tracks changes made to the file system. It is used to track the creation, modification, and deletion of files.
FAT and exFAT
FAT32 (File Allocation Table) and exFAT (Extended File Allocation Table) are two common file systems supported by the Windows operating system. FAT32 is an older and more widely used file system with higher compatibility. However, due to its maximum file size limit of 4 GB and maximum partition size of 8 TB, it requires more space to meet today’s big data needs.
exFAT overcomes these limitations of FAT32. exFAT supports larger file and partition sizes, making it ideal for large files and portable storage devices. While exFAT offers an improved file system structure, its compatibility may not be as extensive as FAT32.
Digital Forensic Investigation Strategies for FAT and exFAT
Recovering Deleted Files: In the FAT file system, recovering deleted files is relatively easy because the bookmarks for deleted files are retained for a period. In contrast, exFAT offers more advanced file management, but its management structure is different, making file recovery more challenging.
Timestamp and Metadata Analysis: Both file systems record the creation, access, and modification times of files. These timestamps play a crucial role in digital forensic investigations. In the FAT file system, the resolution of timestamps may be lower than in exFAT, so attention to detail is necessary when analyzing times.
Support for Large Files and Partitions: Unlike FAT32, exFAT supports large files and partitions. This feature is very useful when analyzing devices used for transferring and storing large amounts of data.


