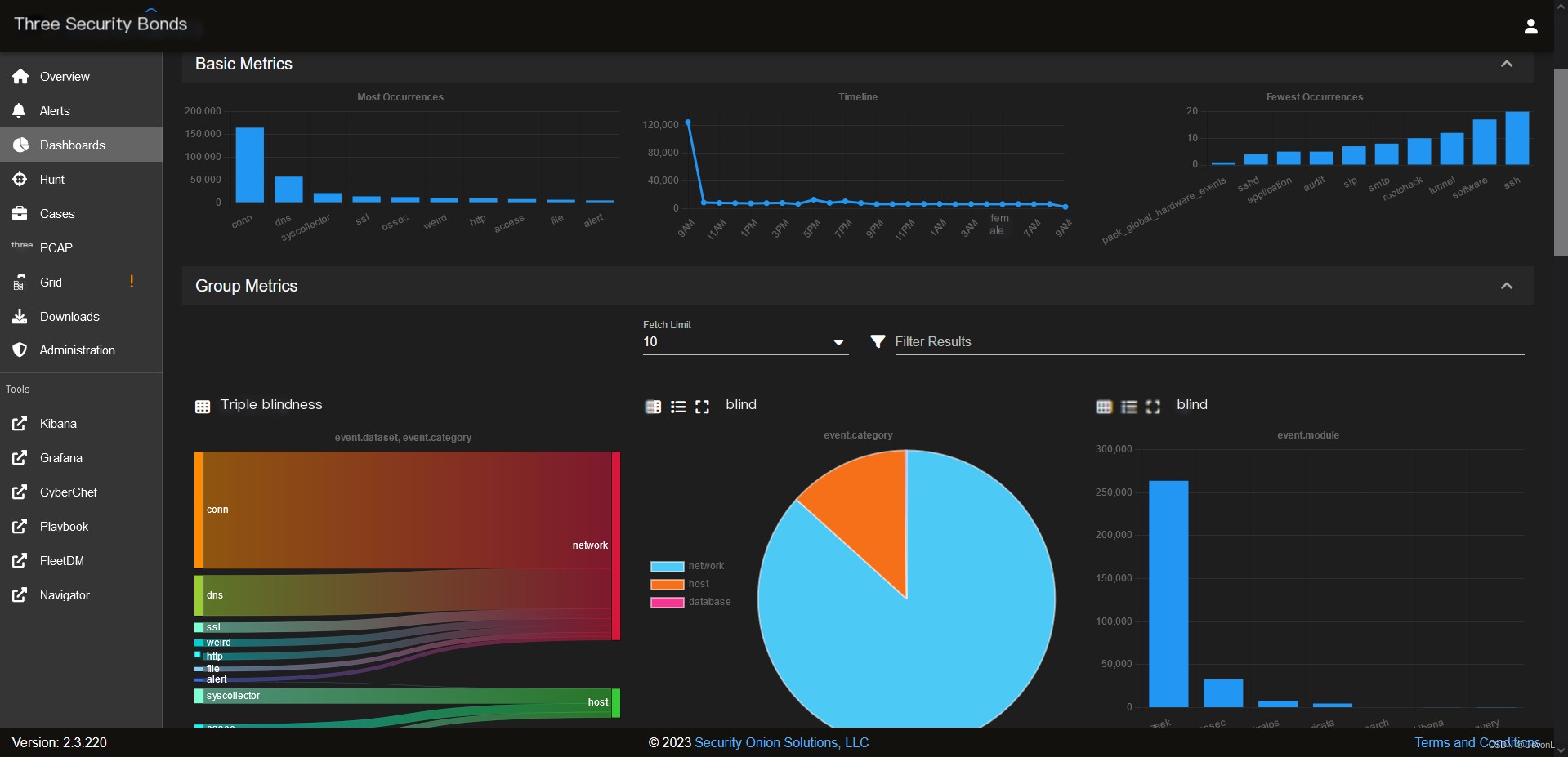
Security Onion is a free and open Linux distribution for threat hunting, enterprise security monitoring, and log management.
An easy-to-use setup wizard allows you to establish a distributed sensor army for your enterprise in minutes. Security Onion includes a native web interface with built-in tools that enable analysts to respond to alerts, hunt for threats, log evidence into cases, monitor grid performance, and more.
1. Prepare the Server Environment, Current Environment:
1. Centos 7.9 32G 8C 300G with two network cards. 2. Prepare a Docker image accelerator tool. Without acceleration, pulling images during installation will fail. After enabling the accelerator tool, you need to exclude the hostname, 127.0.0.1, and localhost, otherwise, it will result in the inability to write data to the Elasticsearch container, causing the container to fail to start.
2. Start Installation, First Configure the Accelerator
2.1. Enable the accelerator. I am using the tool below, others need to solve this themselves. Enter the accelerator directory, configure the config.json file, and start the Docker image accelerator.
2.2. Threat hunting: Inspect the accelerator’s port and configure local acceleration environment variables. Private network addresses and the local hostname do not require acceleration.
[root@220-220 v2ray]# netstat -lntup
tcp 00127.0.0.1:10808 0.0.0.0:* LISTEN 4426/
tcp 00127.0.0.1:10809 0.0.0.0:* LISTEN 4426/
[root@220-220 v2ray]# vim /etc/profile79no_proxy_192=$(echo192.168.220.{1..255}|sed's/ /,/g')#no acceleration addresses must include local addresses; modify based on your requirements80exportno_proxy="220-220,${no_proxy_192}"#no acceleration effective, includes 220-220 hostname and the above private network addresses81exporthttps_proxy=127.0.0.1:10809 #Accelerate HTTPS via local 1080982exporthttp_proxy=127.0.0.1:10809 #Accelerate HTTP via local 108093. Git Clone the Project
[root@220-220 ~]# git clone https://github.com/Security-Onion-Solutions/securityonion4. Install Security Onion
[root@220-220 v2ray]# cd /root/securityonion/[root@220-220 securityonion]# ./so-setup-network Select YES
Select YES Select EVAL
Select EVAL Fill in AGREE
Fill in AGREE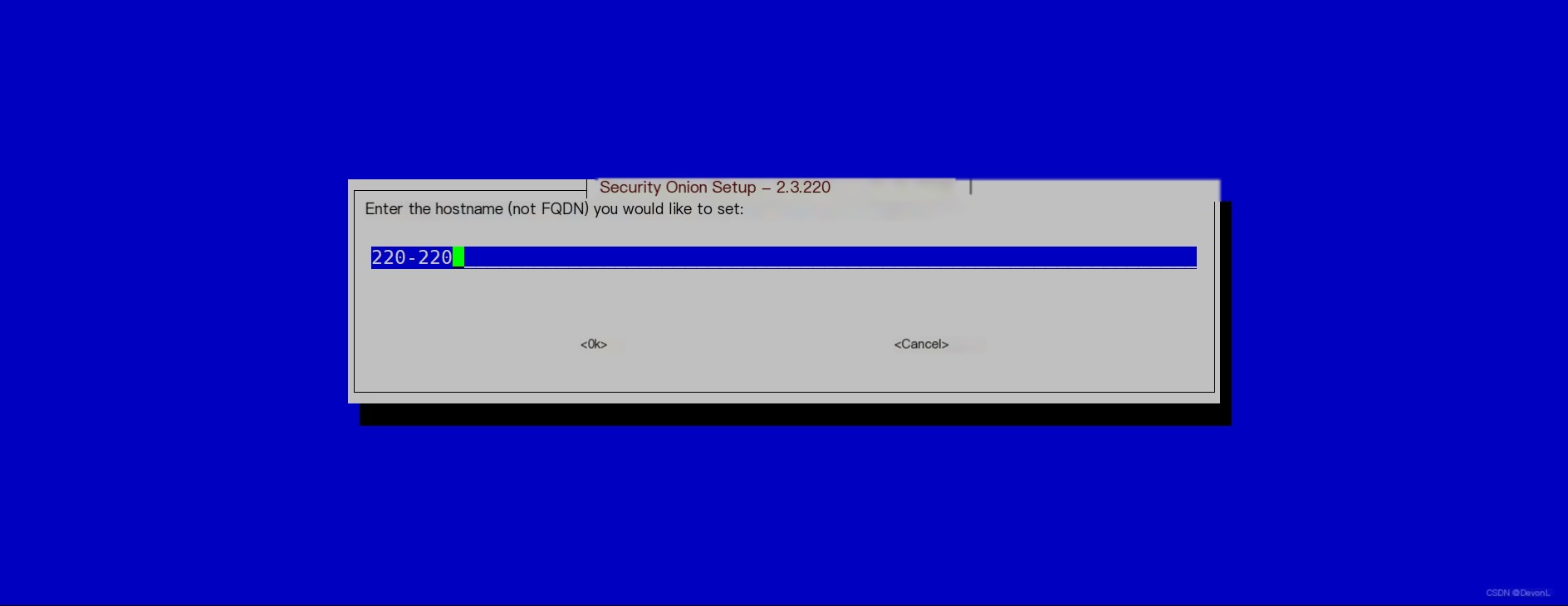 Fill in the hostname
Fill in the hostname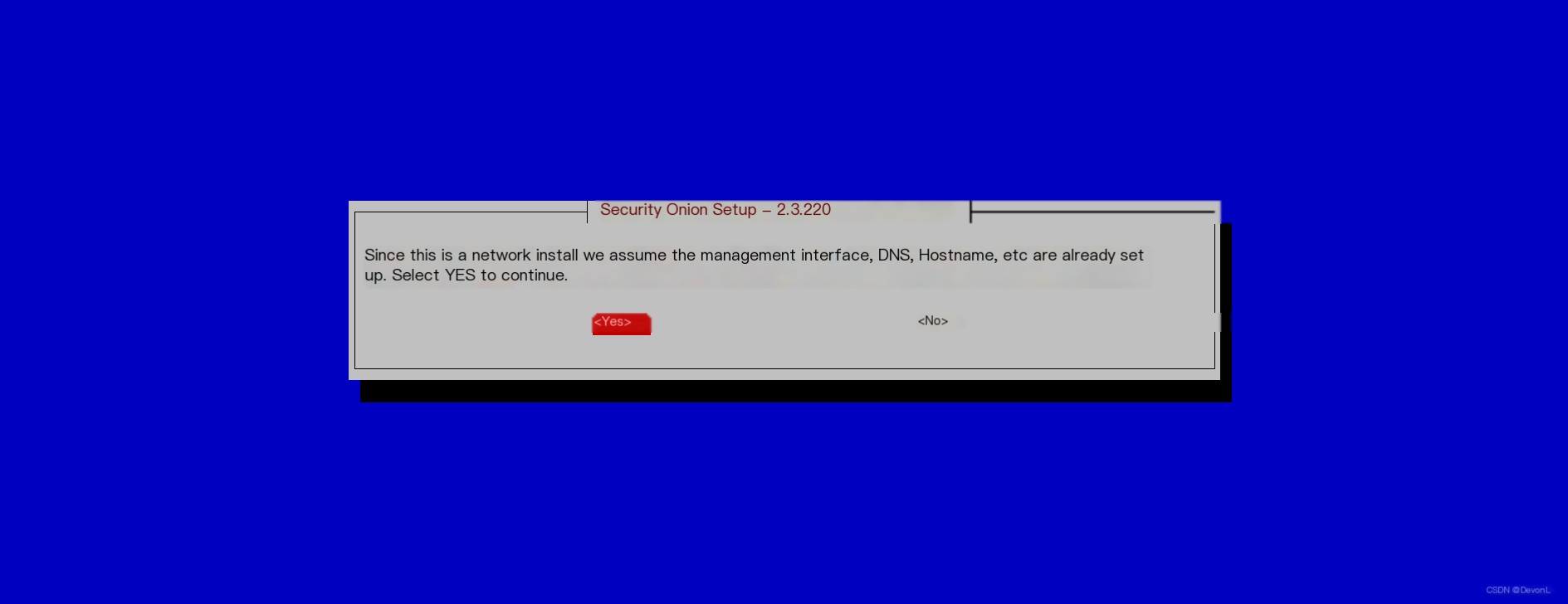 Select YES
Select YES Select Ok
Select Ok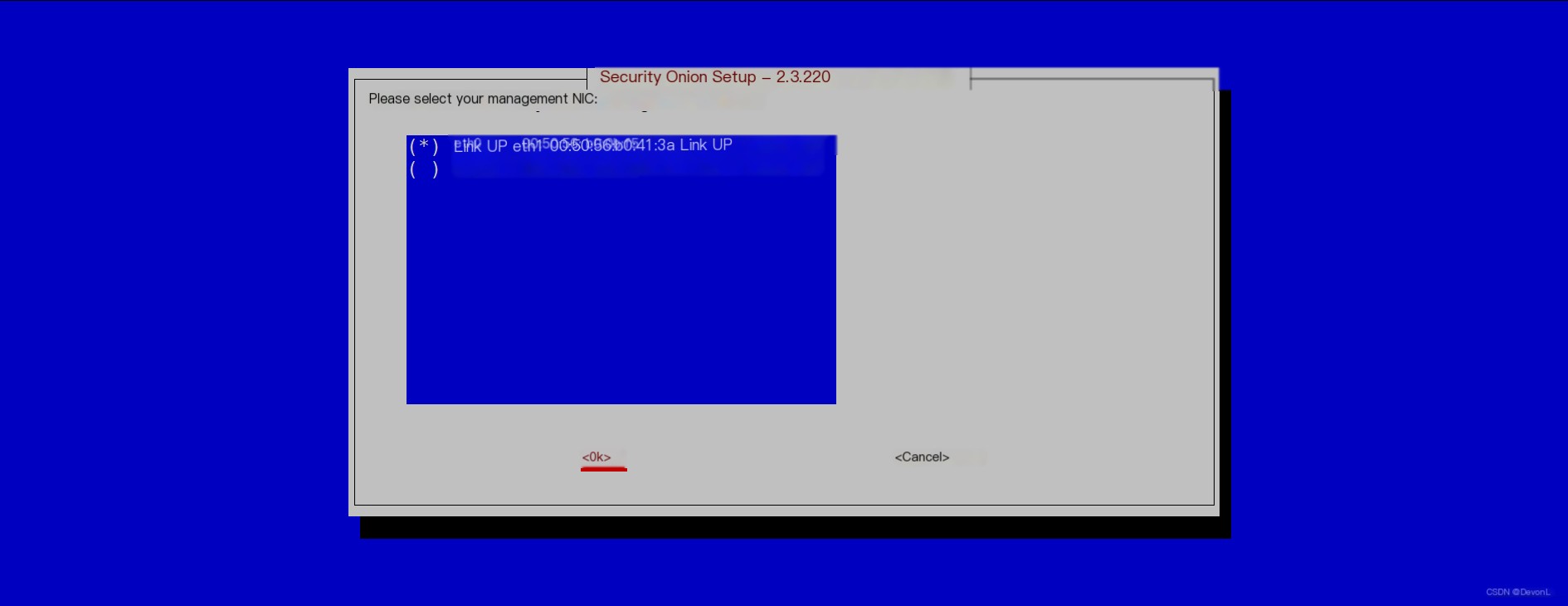
 Choose the network interface for traffic mirroring, Ok
Choose the network interface for traffic mirroring, Ok
 Select auto-update
Select auto-update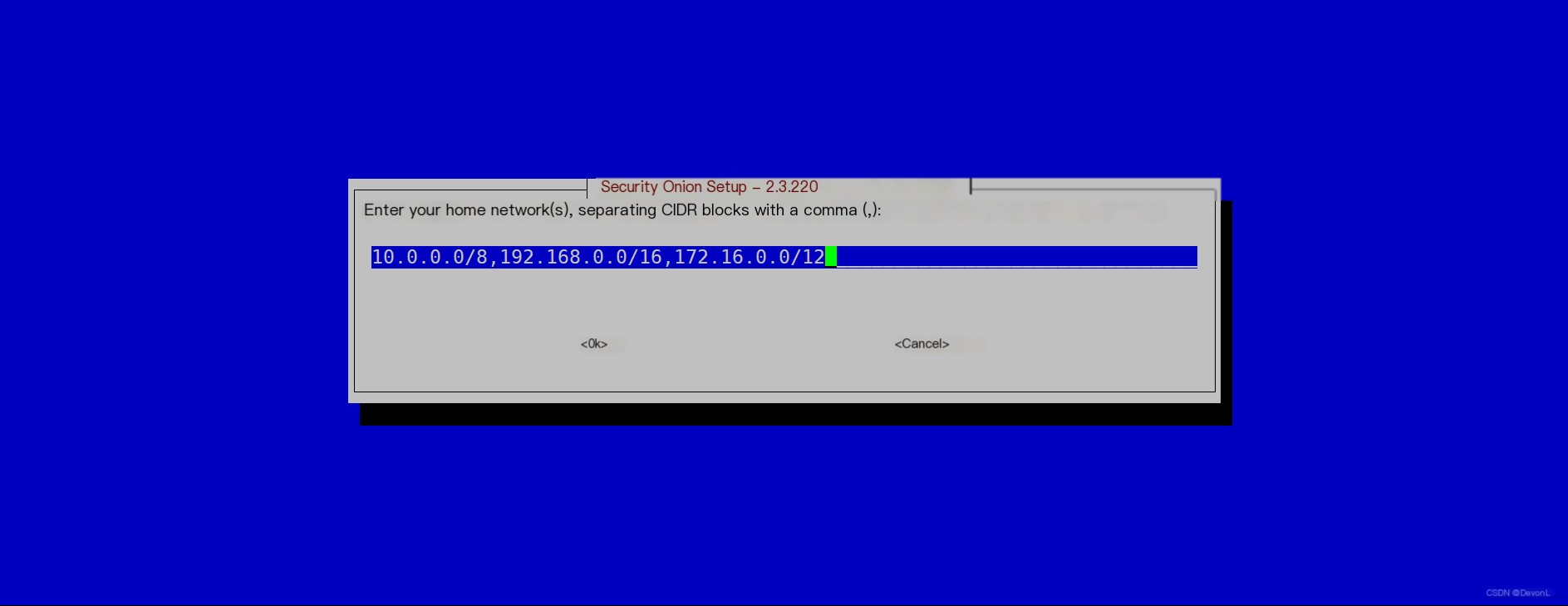 Input address
Input address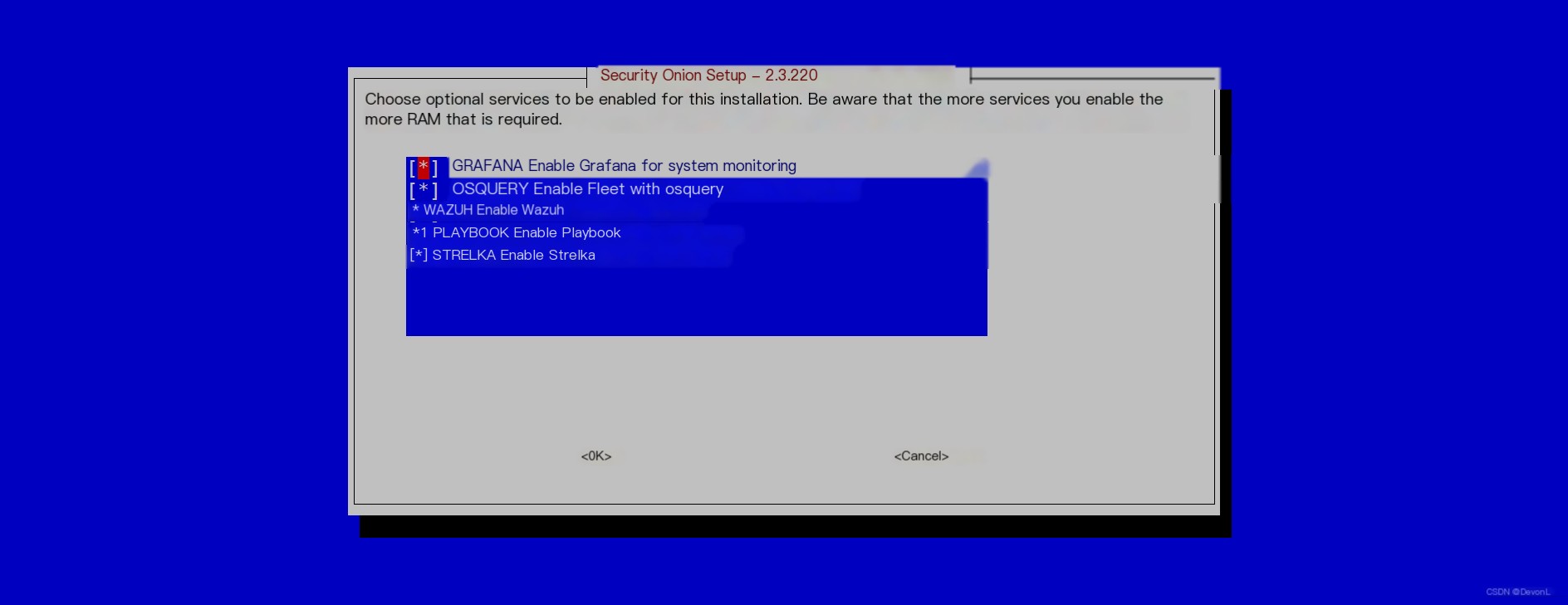 Select the plugins to install
Select the plugins to install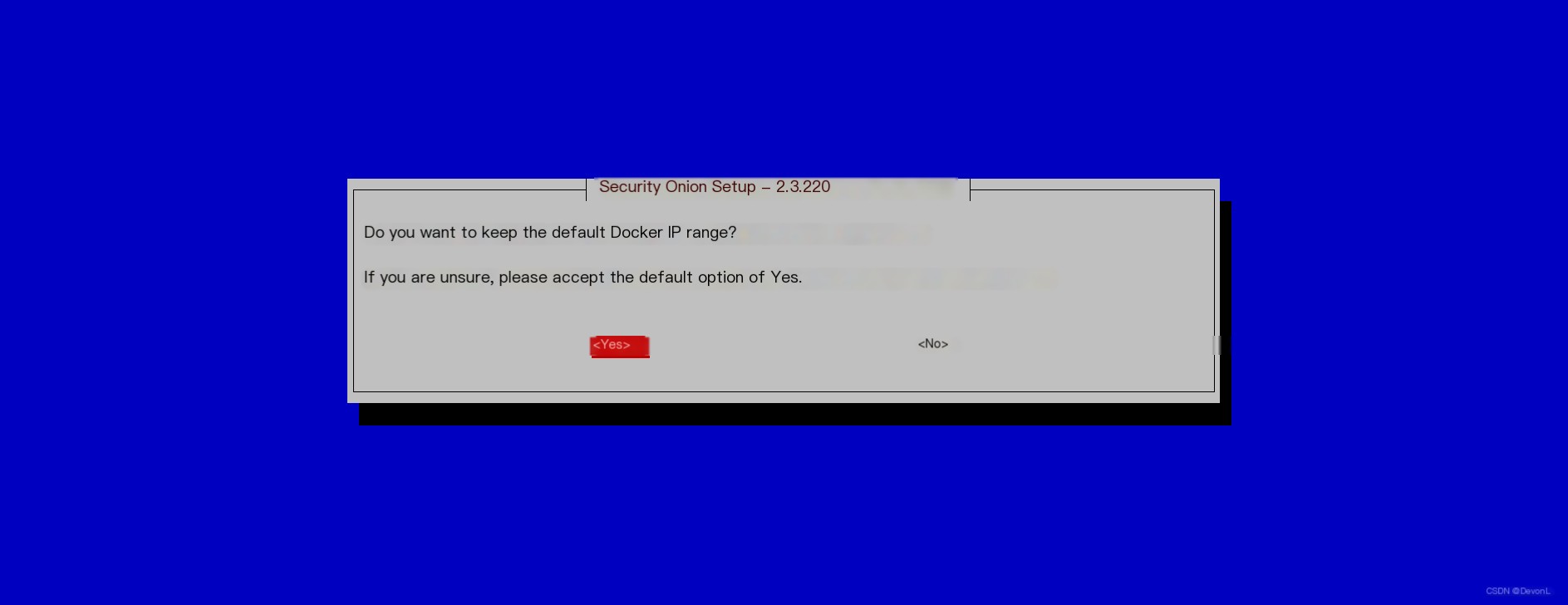 Keep Docker container IP default
Keep Docker container IP default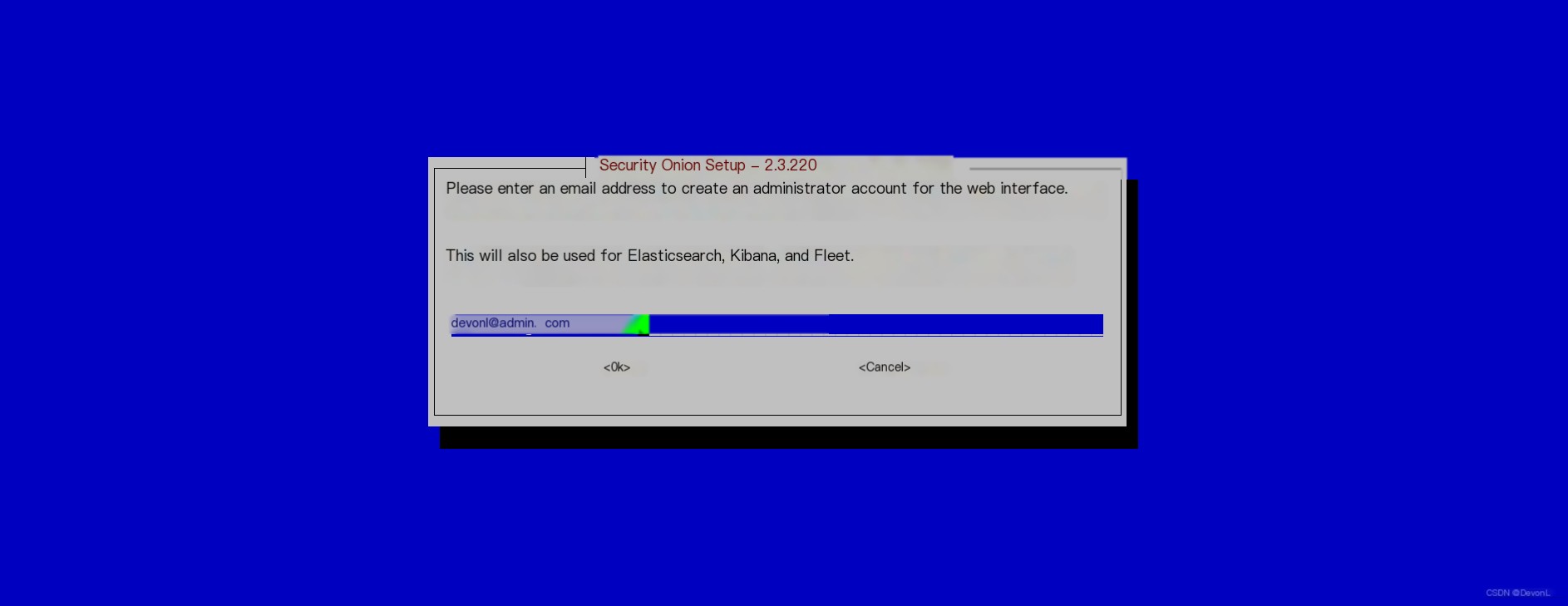 Provide the administrator’s email address
Provide the administrator’s email address
 Enter the administrator’s password twice
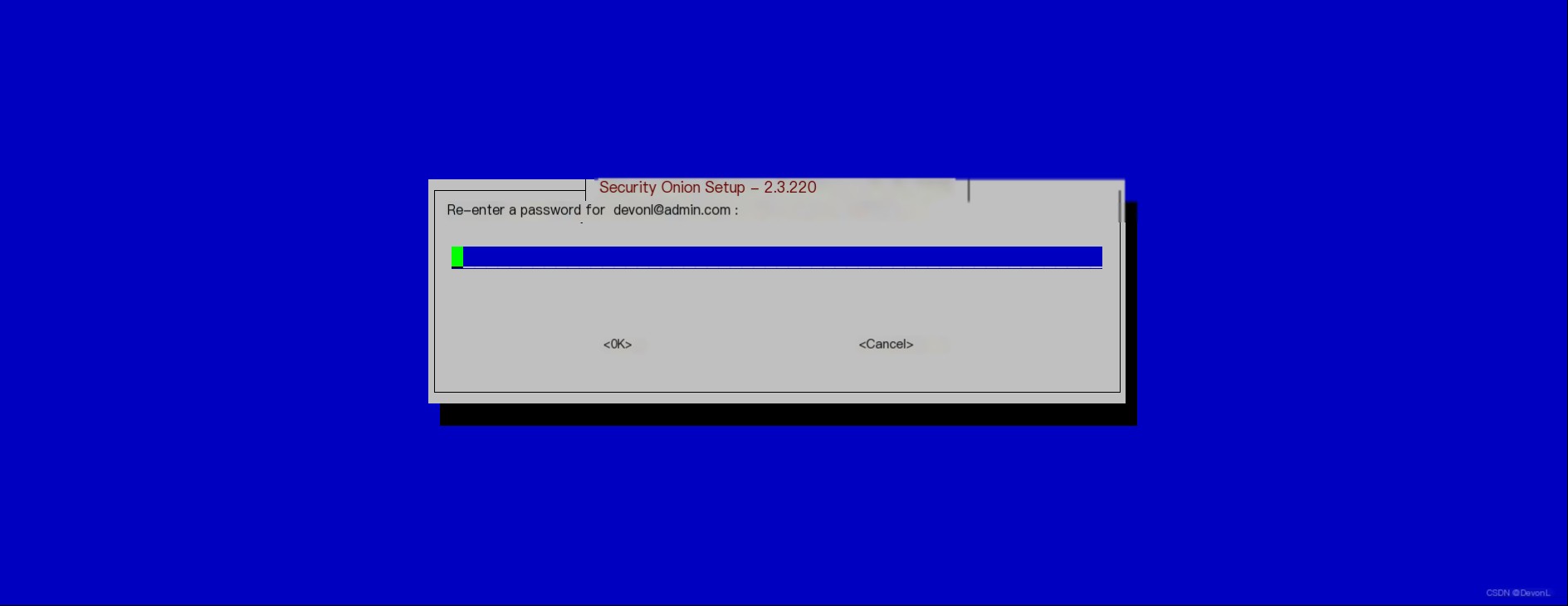
Enter the administrator’s password twice
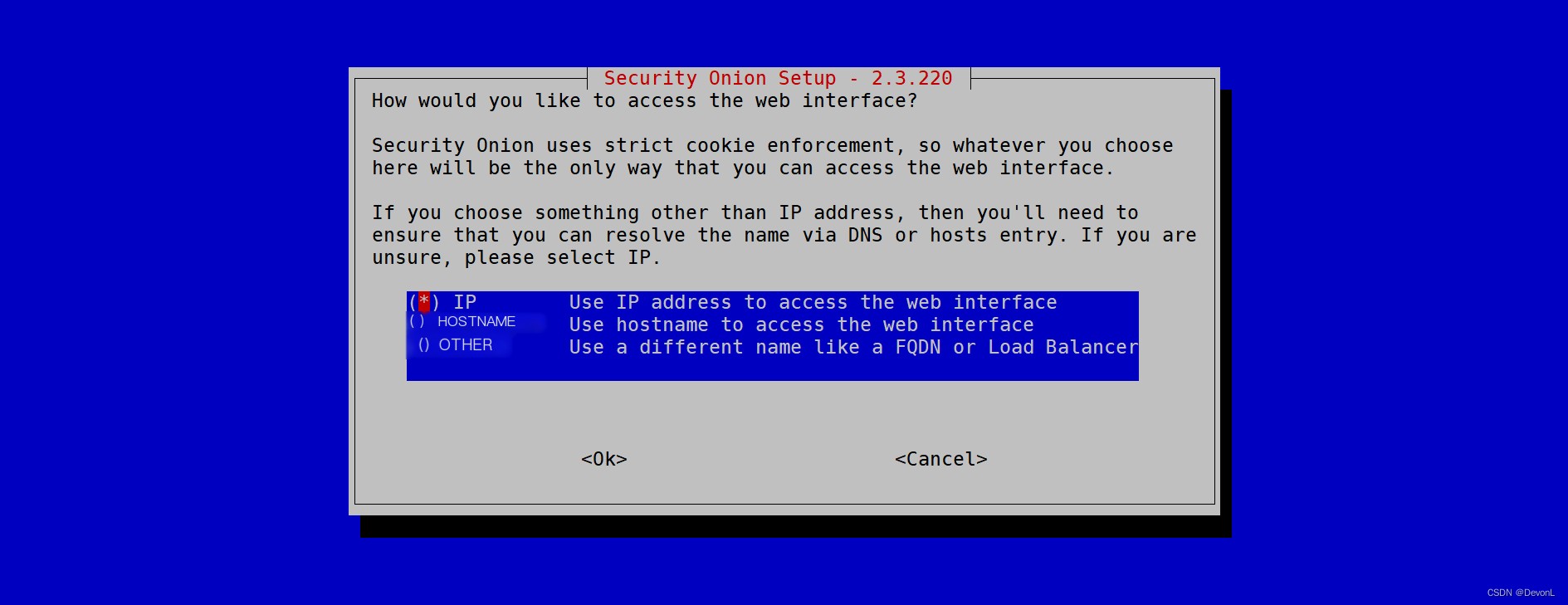 Use IP to access the WEB page
Use IP to access the WEB page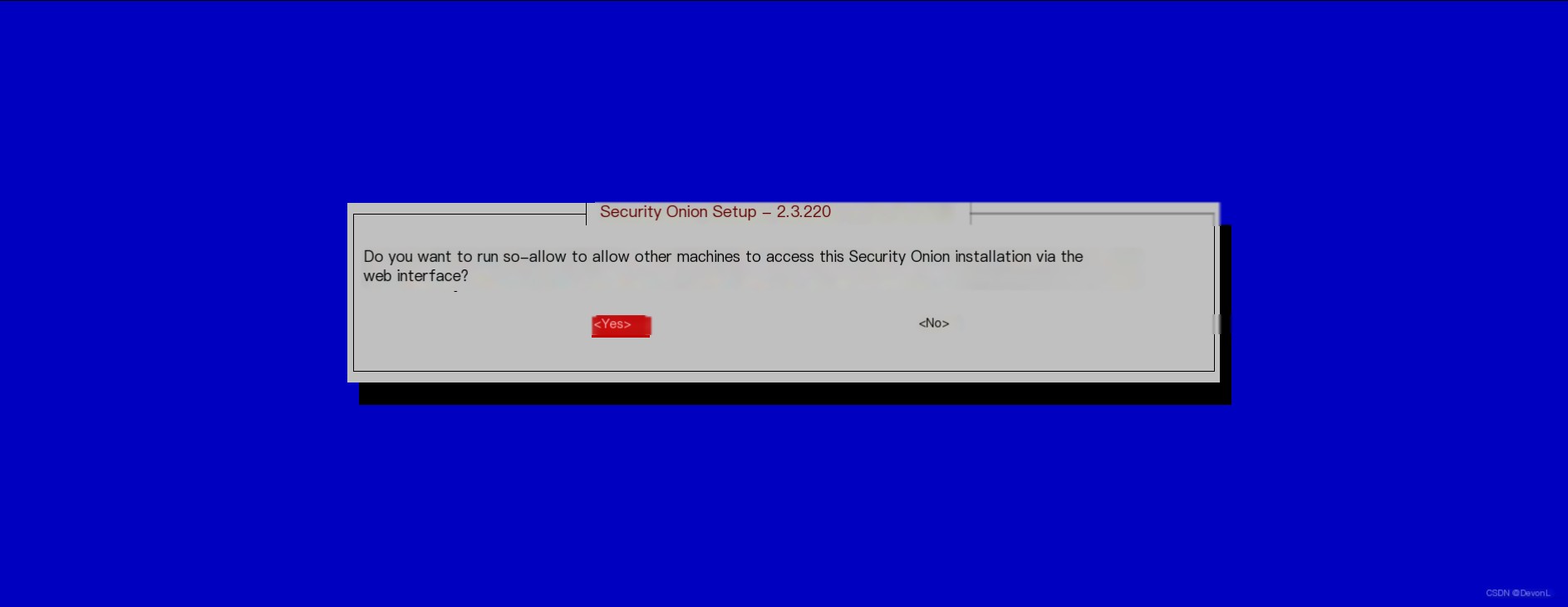 Select YES
Select YES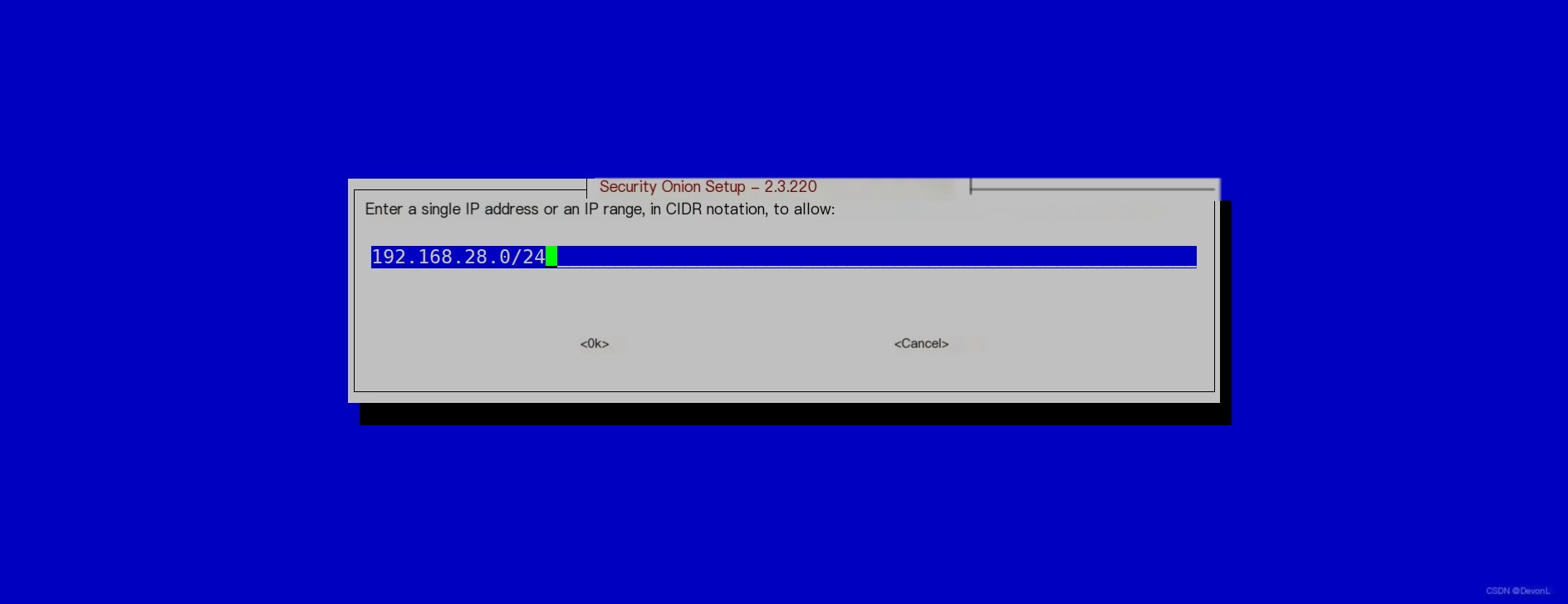 Enter the access address 0.0.0.0/0 to allow access from all addresses
Enter the access address 0.0.0.0/0 to allow access from all addresses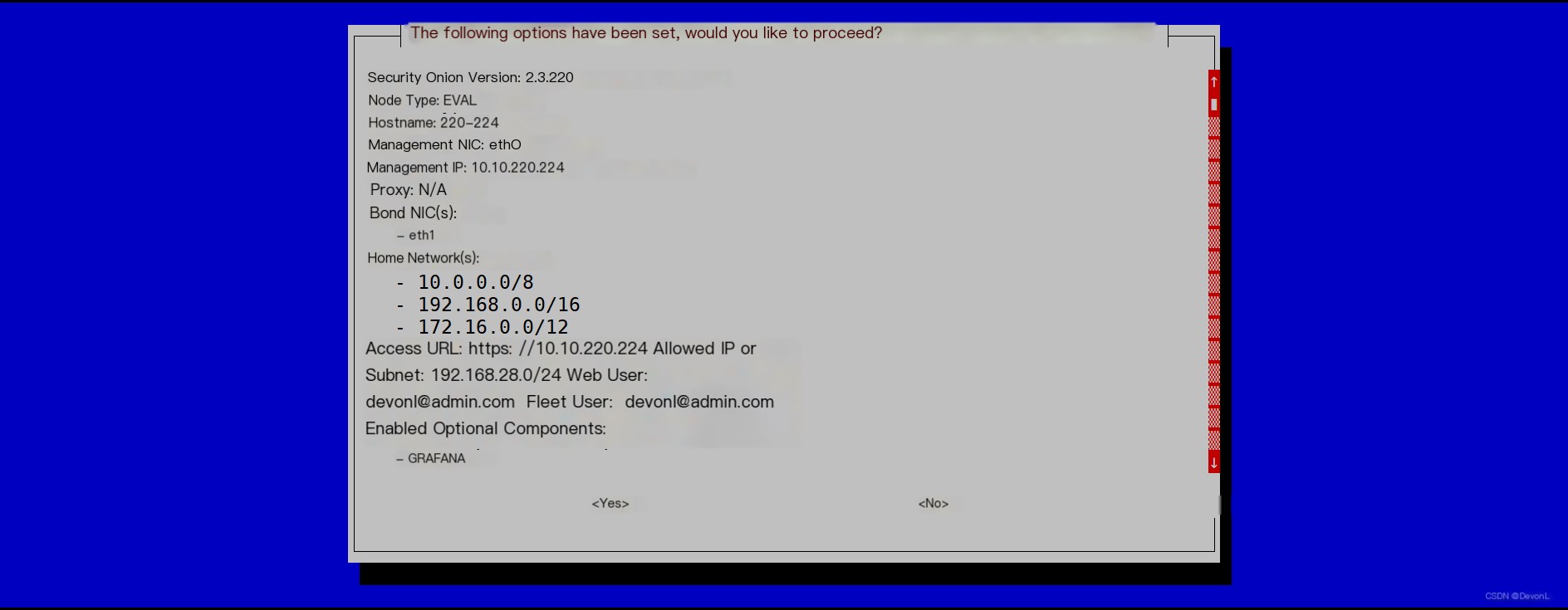 Confirm the entered information
Confirm the entered information Wait for the installation
Wait for the installation
[root@220-220 ~]# tailf sosetup.log #View installation logs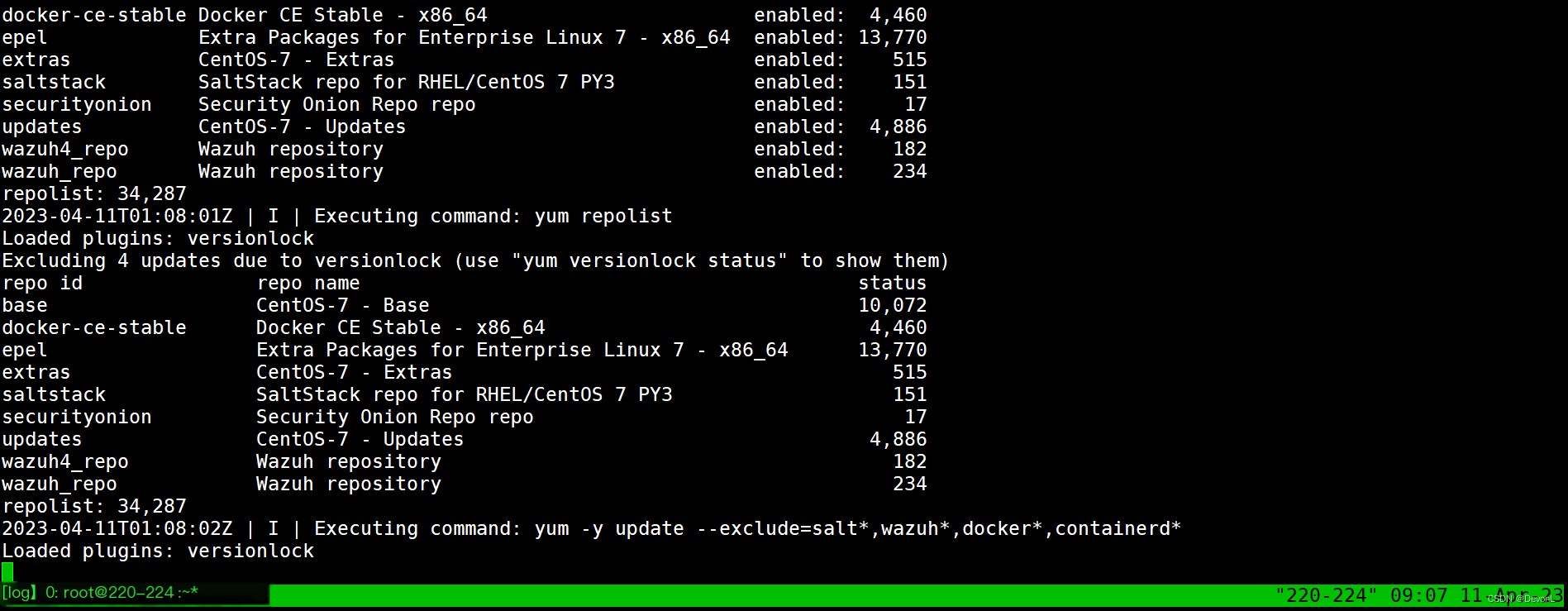
[root@220-220 ~]# while sleep 3; do docker images | grep ghcr.io | wc -l;done5#View the number of pulled images[root@220-220 ~]# docker images| grep -v 220-220 | wc -l #A total of 32 images are needed32[root@220-220 ~]# docker ps |grep -v ID |wc -l #A total of 30 containers are running30[root@220-224 ~]# so-allow #Open ports
Choose the role for the IP or Range you would like to allow
[a] - Analyst - 80/tcp, 443/tcp
[b] - Logstash Beat - 5044/tcp
[e] - Elasticsearch REST API - 9200/tcp
[f] - Strelka frontend - 57314/tcp
[o] - Osquery endpoint - 8090/tcp
[s] - Syslog device - 514/tcp/udp
[w] - Wazuh agent - 1514/tcp/udp
[p] - Wazuh API - 55000/tcp
[r] - Wazuh registration service - 1515/tcp
Please enter your selection: a #a for ports 80/443
Enter a single IP address or range to allow (ex: 10.10.10.10 or 10.10.0.0/16): 192.168.28.0/24 #Allow access for the address
Adding 192.168.28.0/24 to the analyst role. This can take a few seconds...
[root@220-220 ~]# so-status #Check the status of all components
Checking Docker status
Docker ----------------------------------------------------------------------------------------------------------------- [ OK ]
Checking container statuses
so-aptcacherng --------------------------------------------------------------------------------------------------------- [ OK ]
so-curator ------------------------------------------------------------------------------------------------------------- [ OK ]
so-dockerregistry ------------------------------------------------------------------------------------------------------ [ OK ]
so-elastalert ---------------------------------------------------------------------------------------------------------- [ OK ]
so-elasticsearch ------------------------------------------------------------------------------------------------------- [ OK ]
so-filebeat ------------------------------------------------------------------------------------------------------------ [ OK ]
so-fleet --------------------------------------------------------------------------------------------------------------- [ OK ]
so-grafana ------------------------------------------------------------------------------------------------------------- [ OK ]
so-idstools ------------------------------------------------------------------------------------------------------------ [ OK ]
so-influxdb ------------------------------------------------------------------------------------------------------------ [ OK ]
so-kibana -------------------------------------------------------------------------------------------------------------- [ OK ]
so-kratos -------------------------------------------------------------------------------------------------------------- [ OK ]
so-mysql --------------------------------------------------------------------------------------------------------------- [ OK ]
so-nginx --------------------------------------------------------------------------------------------------------------- [ OK ]
so-playbook ------------------------------------------------------------------------------------------------------------ [ OK ]
so-redis --------------------------------------------------------------------------------------------------------------- [ OK ]
so-sensoroni ----------------------------------------------------------------------------------------------------------- [ OK ]
so-soc ----------------------------------------------------------------------------------------------------------------- [ OK ]
so-soctopus ------------------------------------------------------------------------------------------------------------ [ OK ]
so-steno --------------------------------------------------------------------------------------------------------------- [ OK ]
so-strelka-backend ----------------------------------------------------------------------------------------------------- [ OK ]
so-strelka-coordinator ------------------------------------------------------------------------------------------------- [ OK ]
so-strelka-filestream -------------------------------------------------------------------------------------------------- [ OK ]
so-strelka-frontend ---------------------------------------------------------------------------------------------------- [ OK ]
so-strelka-gatekeeper -------------------------------------------------------------------------------------------------- [ OK ]
so-strelka-manager ----------------------------------------------------------------------------------------------------- [ OK ]
so-suricata ------------------------------------------------------------------------------------------------------------ [ OK ]
so-telegraf ------------------------------------------------------------------------------------------------------------ [ OK ]
so-wazuh --------------------------------------------------------------------------------------------------------------- [ OK ]
so-zeek ---------------------------------------------------------------------------------------------------------------- [ OK ]5. Page Display
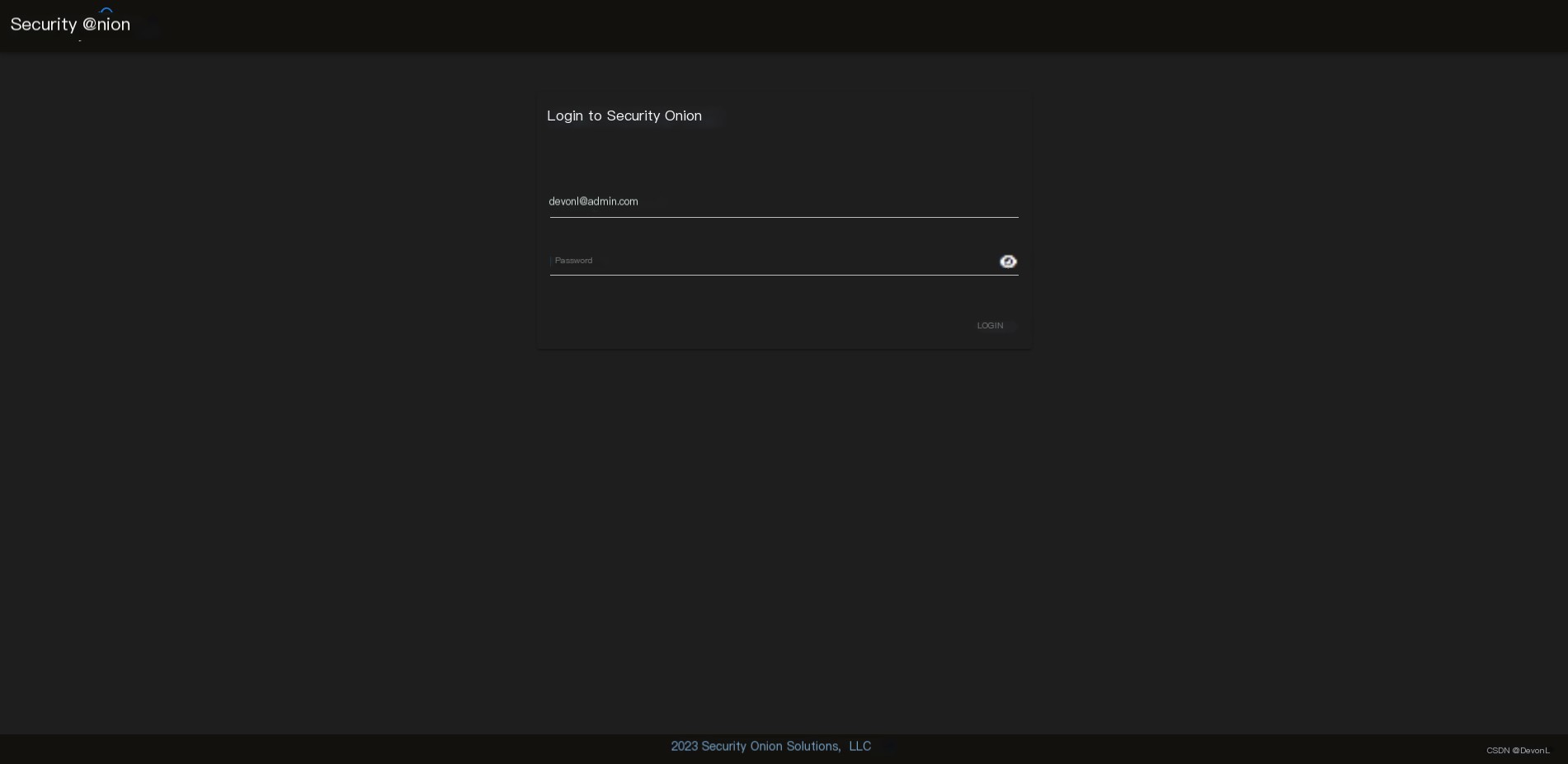 Login page
Login page
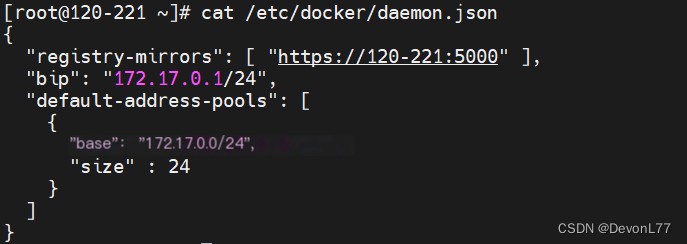
Issue Record: During the execution of the installation command, the installation process clears the registry-mirrors content in the daemon.json management configuration file. Security Onion needs to push images to the local private repository. If it cannot find the private repository address, Docker will fail to restart. The file is as follows:
[root@120-221 ~]# cat /etc/docker/daemon.json{"registry-mirrors":["https://:5000"],
"bip":"172.17.0.1/24",
"default-address-pools":[{"base":"172.17.0.0/24",
"size":24}]}Solution: After starting the installation command, manually add the local IP address to registry-mirrors: private repository address, example as follows: