In Linux, you can use the lsusb command, as shown in the figure:
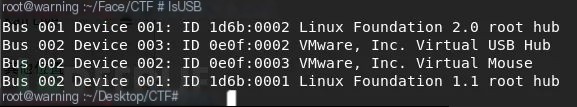
Here, we mainly demonstrate USB mouse traffic and keyboard traffic. There has been considerable analysis under Linux; the following environment is conducted under Windows.
The rules for USB mouse traffic are shown below:
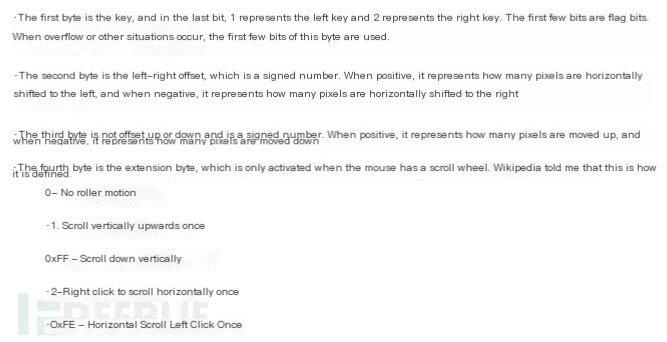
To capture using Wireshark, you need to select the usbpcap tool option during installation. This way, your Wireshark will have a USB interface option, and you can start capturing by clicking on it.

The following image shows the traffic when I click the left mouse button to draw circles on the screen:
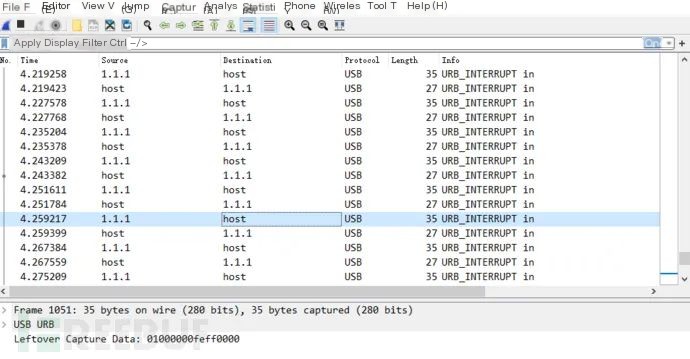
Some mice might not adhere to the standard protocol precisely, leading to analysis issues.
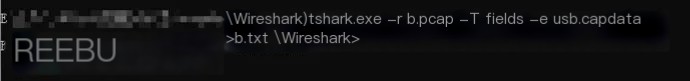
The USB traffic captured in Wireshark is concentrated in the Leftover Capture Data module, and we can use the tshark tool to extract it. Enter the following in the directory where tshark.exe is installed in Windows:
tshark.exe -r b.pcap -T fields -e usb.capdata >b.txt // Here, b.pcap represents the captured packet file name, and b.txt is where the extracted data is stored.
When viewing the contents of b.txt, you may find many empty lines due to useless packets. We need to remove the empty lines before proceeding to the next step.

After removing the empty lines, plot the pixel coordinates according to the mouse traffic rules. Finally, use a plotting tool (like Matlab or Python’s Matplotlib) to create the image.
Understanding the principles allows you to easily use Wang Yihang’s tool for extraction, by entering:
python UsbMiceDataHacker.py b.pcap LEFT // where b.pcap is the name of the captured packet file.
After running, you should see the display:
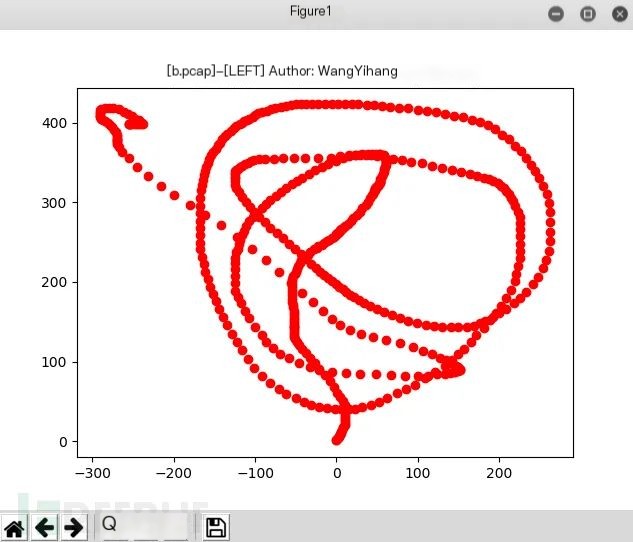
It’s important to note that this tool must work under Python 2, with Matplotlib and NumPy installed.
The length of keyboard data packets is 8 bytes, with keystroke information concentrated in the third byte. Every keystroke generates a packet. Hence, if you observe information in packets with 8 bytes and only the third byte is not 0000, it is most likely keyboard traffic.
Search for keyboard in the USB protocol documentation to find a table for keystroke information and the corresponding hexadecimal data in the packet:
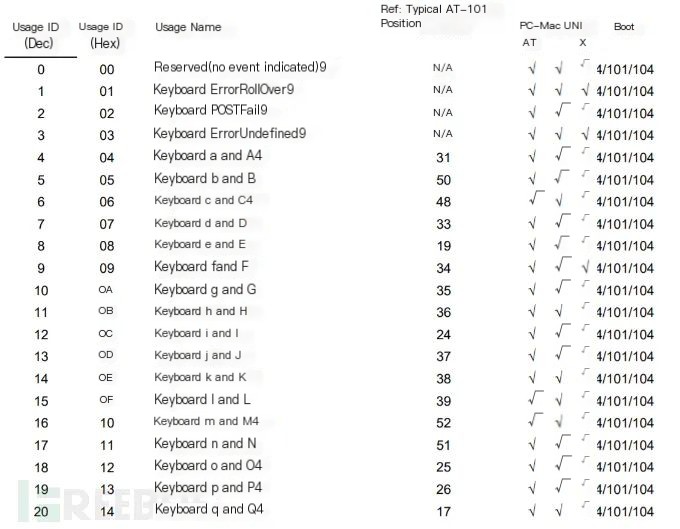
The capture steps are similar to the above. Below, an example problem from the XCTF Intercollegiate Competition (ez_mem&usb) is explained.
In the final step, we obtained a compressed file, which we decompressed with a password to get a text file of keyboard traffic:
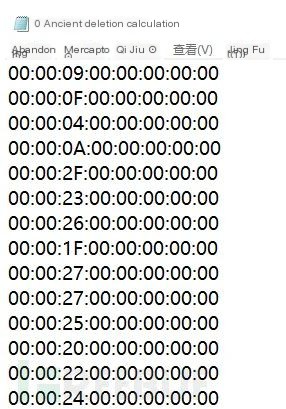
Based on the characteristics of keyboard traffic, it can be determined very easily.
Use code to extract according to the decoding table. Here is the code:
Of course, you can also directly use Wang Yihang’s code to extract files from the pcap packet, which bypasses many intermediate steps, and the code is very versatile.



