1. Objectives and Requirements of the Experiment:
1. Learn how to install and configure Snort.
2. Understand how to define Snort rules.
3. Master the usage of Snort for analyzing network status.
4. Specific tasks:
1) Study the working principles of Snort.
2) Configure the Snort rules file.
3) Use Snort to detect network intrusion events.
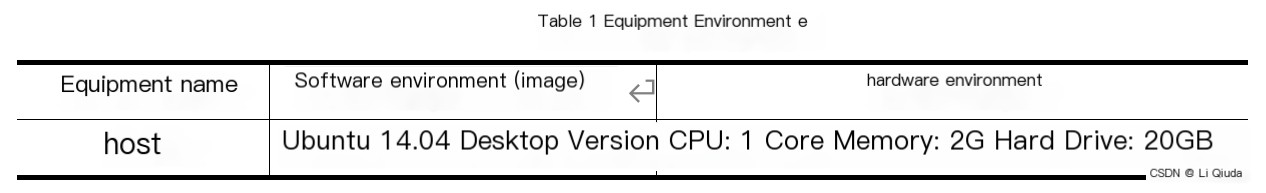
2. Experimental Equipment and Environment:
3. Principles of the Experiment:
1. Overview, Purpose, and Principles of an Intrusion Detection System (IDS)
Analyze and process malicious behaviors targeting computer and network resources. This is a technology based on detecting violations of security policies in computers, primarily focused on ensuring system security and detecting unauthorized or abnormal activities.
Intrusions can be categorized as external or internal. Based on the detection mechanism, it can be split into network-based intrusion detection and file system change-based intrusion detection.
The components of a network-based intrusion detection system include: data capturer, data processor, responder, and database.
The workflow is shown in Figure 1:

This experiment revolves around a network-based intrusion detection system.
2. Functions of the Snort Tool
Snort is an open-source, rule-based network intrusion detection software. Its primary functions include: packet sniffing (detection), packet logging (storage), and intrusion detection.
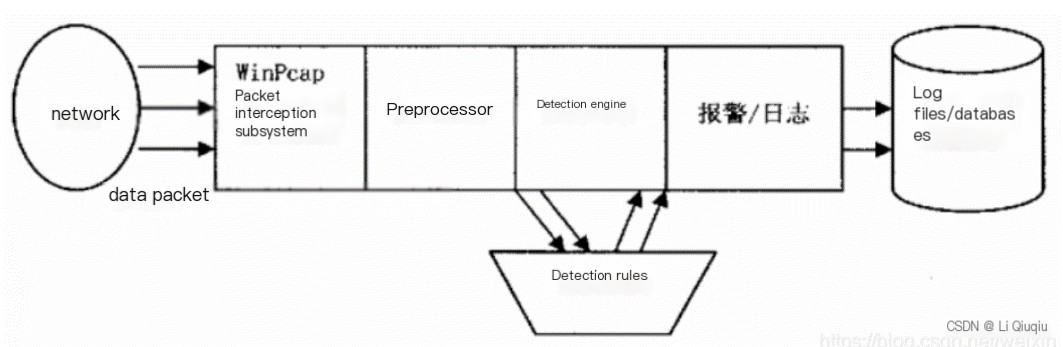
Operational workflow:
1) First, capture the packets on the network from the network interface card (NIC).
2) Decode the packets and fit them into the data structure of the link-layer protocol.
3) Preprocessors check the packets.
4) The detection engine processes the packets. See Figure 2 below.
The Snort command format is: Snort [-a|-e|s|e|t] [options]
3. Snort Rules
From a logical perspective, a Snort rule consists of a rule header and rule options.
Rule header: specifies the action, protocol type, address, port number, and direction operator.
Rule options: include properties like msg, flags, sid, rev, classtype, etc.


