Similar to ASA firewalls, iptables rule the same role: ensuring network security, system security, and server security. Similar to ASA, it also requires setting up a policy, using the input chain.
The following case provides a basic understanding of iptables rule operations.
Experimental Environment:
The website server’s IP address is 192.168.1.5, the gateway server’s internal address is eth0:192.168.1.254, and the external address is eth1:172.16.16.254. The internet test machine is 172.16.16.172. The goal is to enable these three systems to ping each other successfully.
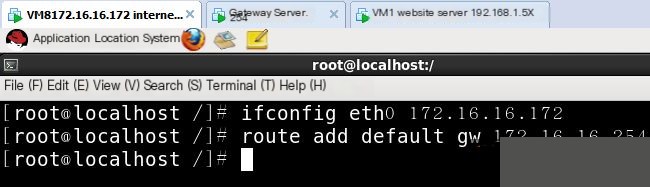
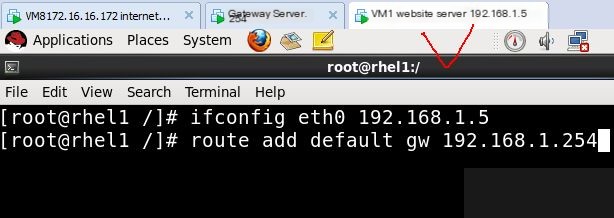
Network management server needs to enable routing forwarding function
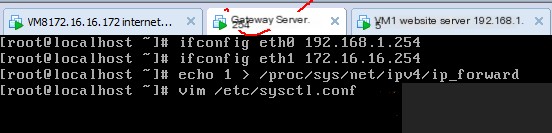
You can also enter vim /etc/sysctl.conf to modify it to 1, to permanently enable the routing forwarding function
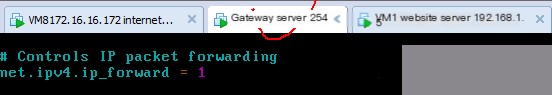
Finally, testing for successful mutual ping is needed
Below is an introduction to the application of various iptables rule
1. Writing Iptables Rules
1. For example, insert a iptables rule in the INPUT chain of the filter table on the website server to reject packets using the ICMP protocol sent to the local machine.
Execute: Iptables -t filter -I INPUT -p icmp -j REJECT
View rules: iptables -L INPUT –line-numbers
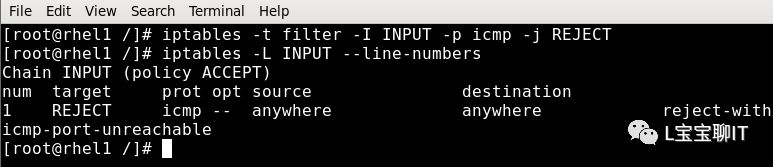
Then, use 172.16.16.172 to ping 192.168.1.5 again; the destination port appears unreachable, unable to ping through.
2. Add new iptables rule
For example:
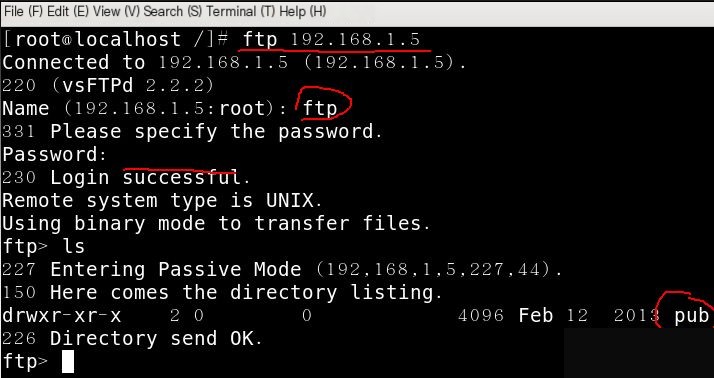
1) Add a iptables rule at the end of the INPUT chain in the filter table to accept the TCP protocol (set up an FTP service on the website server before the experiment, so the internet test machine can access the FTP server).
Access on the internet test machine
By default, the firewall on the website server is active, so it is inaccessible, then execute:
iptables -t filter -A INPUT -p tcp -j ACCEPT
Discover it remains inaccessible, because -A adds a new iptables rule at the end
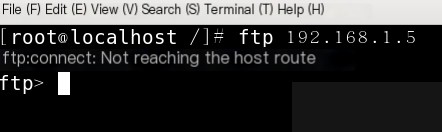
Therefore execute: Iptables -I INPUT -p tcp -j ACCEPT (-I by default adds as the first rule)
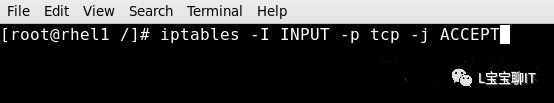
Access FTP again
View iptables rule on the website server
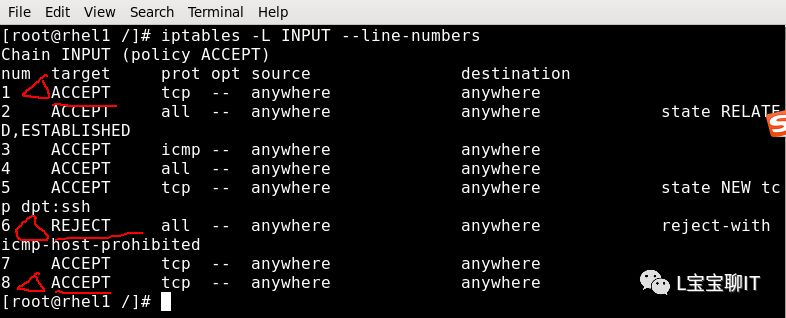
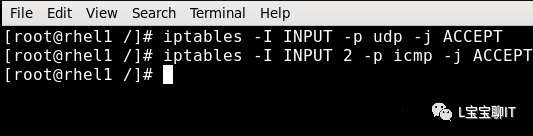
Example: 2) Add rules to allow UDP packets to pass, default located at the first of the filter
Iptables -I INPUT -p udp -j ACCEPT
Example: 3) Specify the order number, add rules allowing ICMP packets to pass, located at the second
Iptables -I INPUT 2 -p icmp -j ACCEPT
View the rule list:
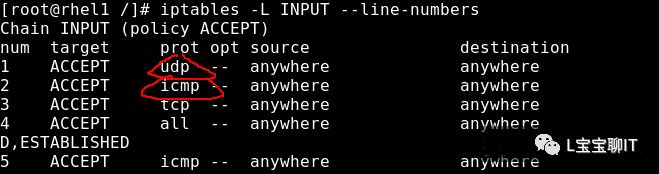
3. Display the iptables rule list in numerical form to speed up execution
Iptables -n -L INPUT (-n -L can be abbreviated as -nL)
4. Delete and clear rules
1) To delete the third iptables rule in the INPUT chain of the filter table, execute:
Iptables -D INPUT 3
2) Use -F to clear all iptables rule from a specified chain or table
Iptables -F INPUT
3) Clear the filter table, nat table, mangle table
Iptables -F
Iptables -t nat -F
Iptables -t mangle -F
5. Set default policies: if no iptables rule can match a packet, execute the default policy
For example, 1) Set the default policy of the FORWARD chain in the filter table to drop, and the OUTPUT chain’s default policy to allow (default policies do not take part in the order arrangement of rules, so their placement doesn’t matter).
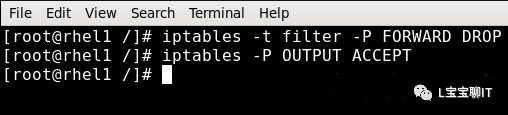
2. Iptables Rule Matching Conditions
Multiple matching conditions can be specified for the same iptables rule, and the conditions must all be met for the rule to take effect.
1. Generic Matching: Comprising three types: protocol matching, address matching, network interface matching.
1) Protocol Matching
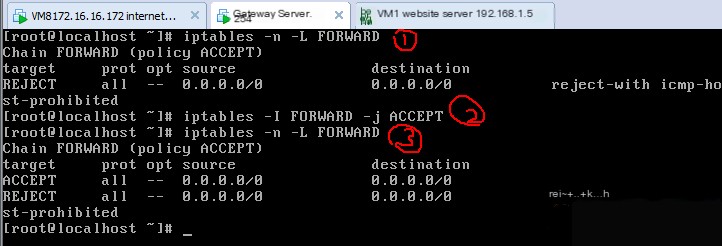
If the firewall is enabled on the gateway server, then the internet test machine cannot access the website server.
View the FORWARD chain of the gateway server, finding only one rule denying all.
If routing forwarding is to be allowed, execute the following command:
iptables -I FORWARD -j ACCEPT, then on the internet test machine, the website server can be accessed.
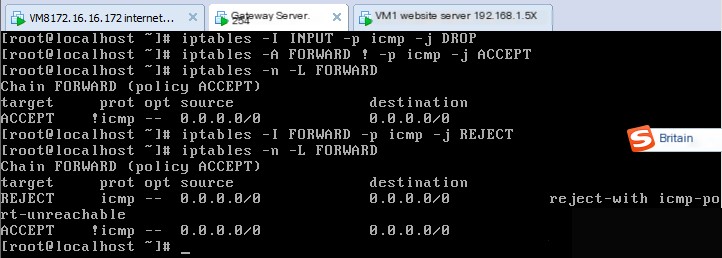
If dropping packets accessing the firewall itself via the ICMP protocol, but allowing forwarding of packets other than those using the ICMP protocol through the firewall is desired, execute:
Iptables -I INPUT -p icmp -j DROP
Iptables -A FORWARD ! -p icmp -j ACCEPT
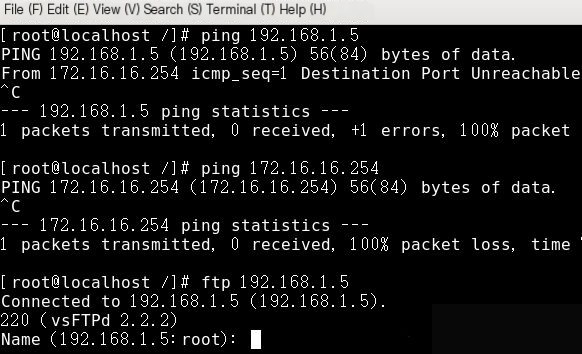
Before executing, ping 172.16.16.254 and 192.168.1.5 from the internet test machine, and both succeed before execution; after executing, they fail. However, accessing the FTP server of the website still succeeds.
First, ping from the internet test machine, able to succeed
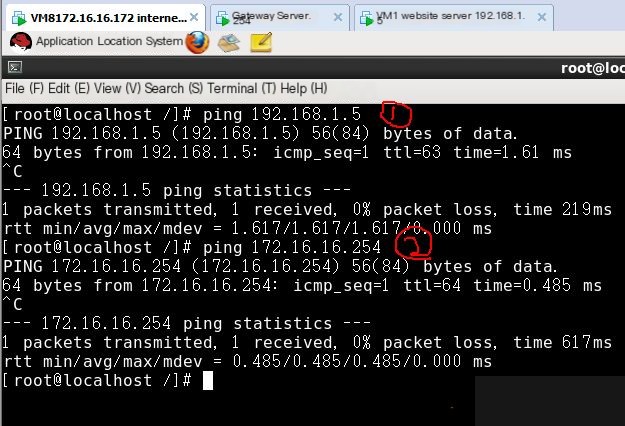
Then execute the following command on the gateway server
Now, ping 192.168.1.5 and 172.16.16.254 from the internet test machine are inaccessible, but FTP can still be accessed.
2) Address Matching
Example 1) Reject forwarding of data from source address 172.16.16.172, but allow forwarding for packets from source address 192.168.1.0
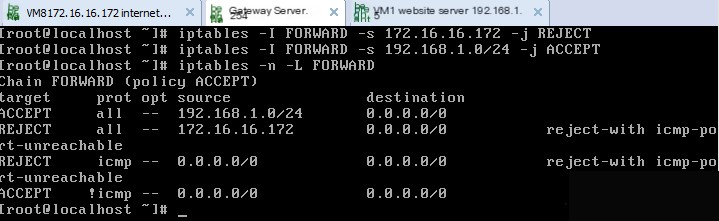
Since 172.16.16.172 is the internet test machine, it cannot ping 192.168.1.5, nor access FTP.
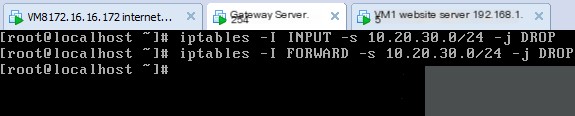
Example 2) If high scan frequency or suspicious login attempts are detected from a certain network segment, firewall rules can immediately block access.
Iptables -I INPUT -s 10.20.30.0/24 -j DROP
Iptables -I FORWARD -s 10.20.30.0/24 -j DROP
3) Network Interface Matching
For example, to discard packets from accessing the firewall itself from the external network interface with a private address as the source, execute as follows:
First: Ping 172.16.16.254 from 172.16.16.172, successful
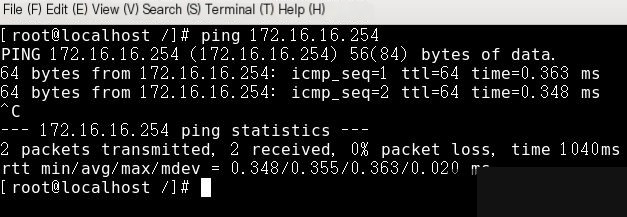
Then execute the following command:
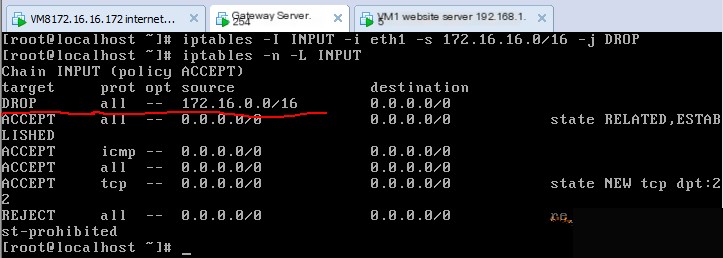
Now ping 172.16.16.254 from 172.16.16.172 again, unsuccessful because the external network interface is eth1
2. Implicit Matching: Specifies the protocol matching as a prerequisite condition, equivalent to a sub-condition.
1) Port Matching
For example, allow segment 192.168.1.0/24 DNS query packets.
First, enable DNS service on the website server
vim /var/named/chroot/var/named/google.com.zone
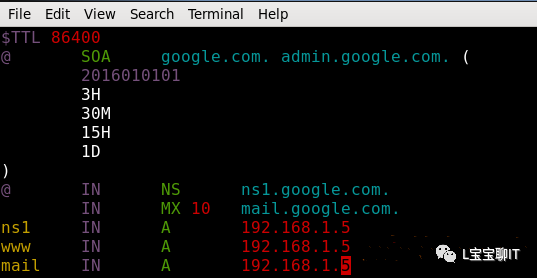
For experimental purposes, first execute the following command on the gateway server, prevent forwarding
Iptables -I FORWARD -j REJECT
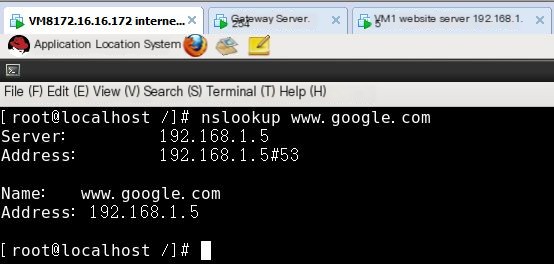
Then execute nslookup on the internet test machine, cannot resolve
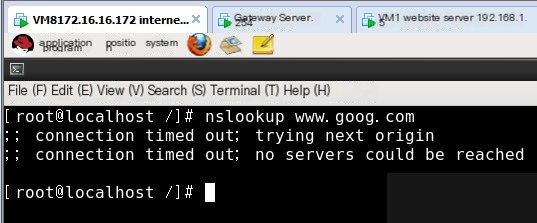
Next, execute implicit matching on the gateway server, allowing DNS query packet forwarding for 172.16.16.0 segment
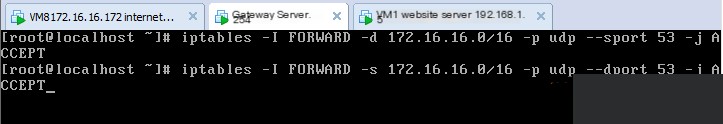
Test resolution again on the internet test machine
2) ICMP Type Matching
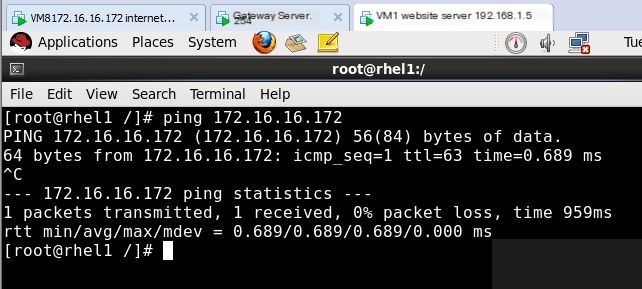
To prohibit other hosts from pinging the local machine while allowing the local machine to ping other hosts, the following actions can be performed:
Firstly for experimental convenience, execute on the gateway server: (before execution, delete other rules and close the firewall, upon writing rules it will automatically turn on)
The internet test machine and the website server can ping each other, then execute:
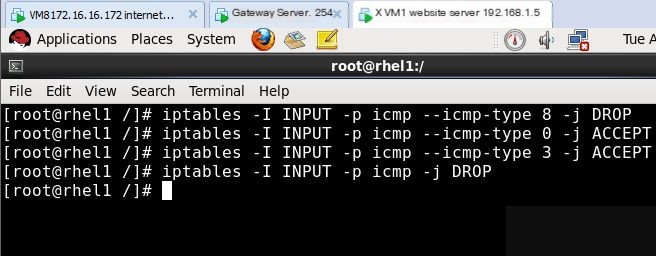
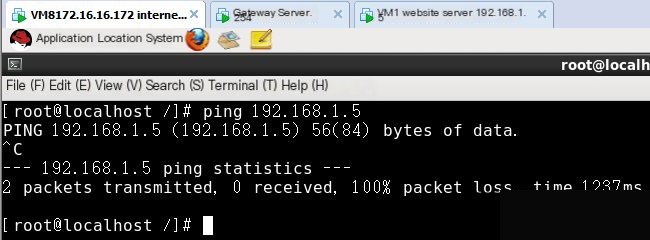
If experimentation fails, change the last rule above to iptables -A INPUT -p icmp-j DROP
Then test:
3. Explicit Matching
The corresponding module must be called before the matching condition is set
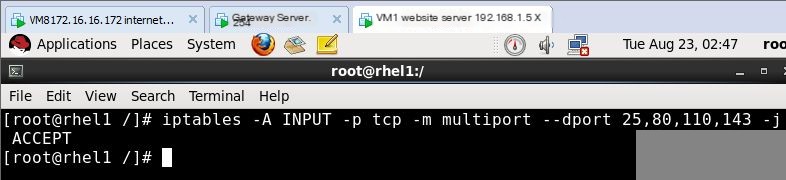
1) Multi-port Matching
For example, allow the website server itself to open ports 25, 80, 110, and 143
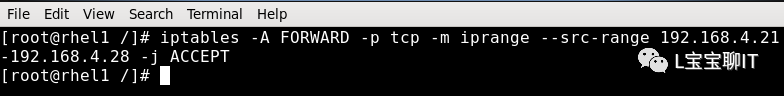
2) IP Range Matching
For example, prohibit forwarding of TCP packets whose source address is between 192.168.4.21 and 192.168.4.28.
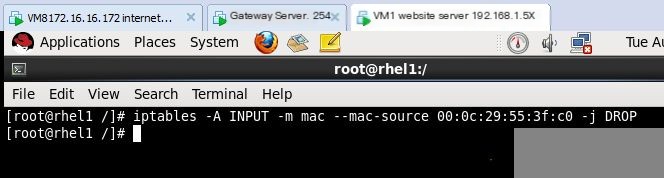
3) MAC Address Matching
For example, prohibit hosts with the following MAC addresses from accessing any application on the website server.
4) State Matching
For example, prohibit forwarding of non-syn request packets unrelated to a normal TCP connection (such as spoofed network attack packets).
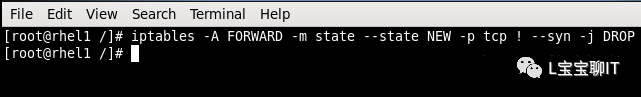
Equally, allow the local machine’s web service on port 80, yet permit passage of TCP response packets to the local machine while discarding all other inbound packets, set inbound rules as follows:
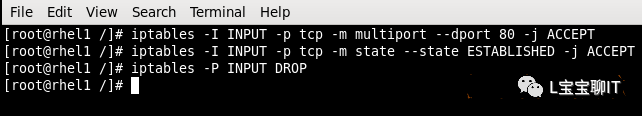
Above are the basic applications of iptables firewall rules; below is the hands-on experimental section:
3. Hands-on Experiment
1. Experimental Environment is the same as above
The website server’s IP address is 192.168.1.5, the gateway server’s internal address is eth0:192.168.1.254, the external address is eth1:172.16.16.254, and the internet test machine is 172.16.16.172. Achieve mutual ping among the three systems.
2. Write inbound rules for the website server
(1) All rules in this example are added within the INPUT chain of the filter table with the default policy set to DROP.
(2) Use “-p icmp ! –icmp-type 8” to match conditions for non-ICMP request packets.
(3) Use “-p tcp –dport 80” to match conditions for TCP port 80 access.
(4) Use “-p tcp -m state –state ESTABLISHED,RELATED” to match TCP response packets.
[root@localhost ~]# iptables -P INPUT DROP
[root@localhost ~]# iptables -A INPUT -p icmp !–icmp-type 8 -j ACCEPT
[root@localhost ~]# iptables -A INPUT -p tcp–dport 80 -j ACCEPT
[root@localhost ~]# iptables -A INPUT -p tcp -mstate –state ESTABLISHED,RELATED -j ACCEPT
(5) Test inbound control effect: From other hosts, access to local web services is possible, but not to other services (such as FTP, DNS); the local machine can ping other hosts, but other hosts cannot ping the local machine.
[root@localhost ~]# iptables -nL INPUT
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT icmp — 0.0.0.0/0 0.0.0.0/0 icmp !type 8
ACCEPT tcp — 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
ACCEPT tcp — 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
…… //Other test processes are omitted
3. Write forwarding rules for the gateway server
(1) All rules in this example are added within the FORWARD chain of the filter table with the default policy set to DROP.
(2) For TCP protocol ports 80, 20, 21, 25, 110, 143, and UDP protocol port 53, respectively write forwarding rules for accessing the Internet from the LAN and from the Internet responding to requests from the LAN.
[root@localhost ~]# iptables -P FORWARD DROP
[root@localhost ~]# iptables -A FORWARD -s192.168.1.0/24 -p tcp -m multiport –dport 20,21,
80,25,110,143 -o eth1 -j ACCEPT
[root@localhost ~]# iptables -A FORWARD -i eth1-m state –state ESTABLISHED,RELATED -j ACCEPT
[root@localhost ~]# iptables -A FORWARD -s192.168.1.0/24 -p udp –dport 53 -oeth1 -j ACCEPT
[root@localhost ~]# iptables -A FORWARD -p udp–sport 53 -i eth1-j ACCEPT
(3) Perform DNS query to determine IP addresses for web.qq.com, w.qq.com, and im.qq.com, including: 112.90.141.88, 112.90.141.163, 112.90.141.164, 58.251.149.159, 58.251.60.202, 123.138.238.100, 123.138.238.101. Then sequentially write forwarding rules for these IP addresses to prohibit access to TCP protocol ports 80, 443.
[root@localhost ~]# vi /opt/black_ip.txt //Compile a list of banned addresses
112.90.141.88
112.90.141.163
112.90.141.164
58.251.149.159
58.251.60.202
123.138.238.100
123.138.238.101
[root@localhost ~]# for i in `cat/opt/black_ip.txt`; do iptables -I FORWARD -d$i -p tcp -m multiport –dport 80,443 -j DROP ; done //Read IP addresses to insert rules
(4) Test forwarding control effect: Access from hosts in the LAN to web.qq.com etc. blocked sites on the Internet fails, but access to other web sites, DNS, and FTP network services succeeds.
[root@localhost ~]# iptables -nL FORWARD
Chain FORWARD (policy DROP)
target prot opt source destination
DROP tcp — 0.0.0.0/0 123.138.238.101 multiport dports 80,443
DROP tcp — 0.0.0.0/0 123.138.238.100 multiport dports 80,443
DROP tcp — 0.0.0.0/0 58.251.60.202 multiport dports 80,443
DROP tcp — 0.0.0.0/0 58.251.149.159 multiport dports 80,443
DROP tcp — 0.0.0.0/0 112.90.141.164 multiport dports 80,443
DROP tcp — 0.0.0.0/0 112.90.141.163 multiport dports 80,443
DROP tcp — 0.0.0.0/0 112.90.141.88 multiport dports


