First, collect the MAC addresses of each device for analysis purposes:
| Server A: 00-0c-29-bb-bb-7f Server B: 00-0C-29-8C-BF-6D Default Gateway: 00-50-56-fe-c8-98 |
|---|
Start Wireshark on Server B, then execute the ping command to communicate with A. Wireshark will capture the communication process. After the ping command ends, stop the capturing, and let’s get familiar with Wireshark’s main interface.
The interface of Wireshark is very intuitive, divided into three windows from top to bottom.
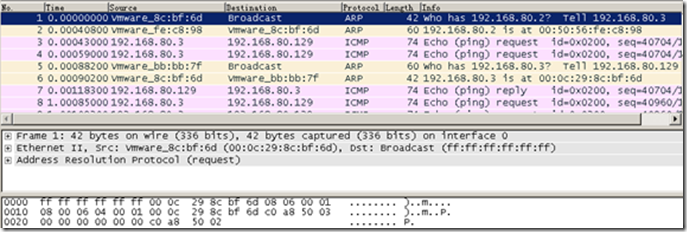
The top window lists all captured packets, with key information such as: packet number, the relative time when the packet was captured, the source address of the packet, the destination address of the packet, the protocol of the packet, the size of the packet, and a summary of the packet information.
After selecting a packet, the middle window displays detailed information of the packet in a hierarchical manner, and you can expand or collapse to view all the content captured in this packet.
The bottom window shows the raw form of the packet, as it appears when transmitted over the link, which is not used much generally.
For example, we select packet 1. In the top window, it shows that this is an ARP broadcast packet sent by Server B, with the purpose of querying the MAC address of the gateway 192.168.80.2. In the bottom window, the first line shows the basic information of the packet, Frame1 indicates this is packet 1. The second line shows the encapsulation information of the data frame, while the third line shows the encapsulation information of the ARP protocol.
When Server B pings Server A, B will first resolve the address of the gateway, which is consistent with our previous analysis.
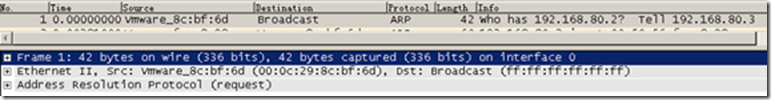
Packet 2 is the response from the default gateway, informing Server B of its MAC address. Note that the beginning of these MAC addresses has been replaced with VMware, as the first 3 bytes of a MAC address represent the manufacturer.
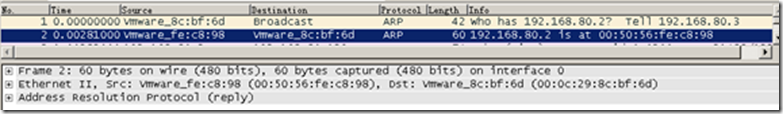
Packet 3 is the ping packet sent by Server B, with the specified destination IP as A (192.168.80.129), but the destination MAC is the default gateway’s 00-50-56-fe-c8-98. This indicates that B expects the gateway to forward the packet to A.
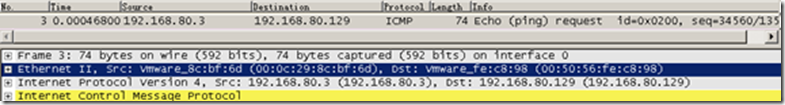
Packet 5 is the ARP broadcast sent by A, inquiring about B’s MAC address. This is because A believes that B is on the same network, hence there’s no need to rely on the gateway.
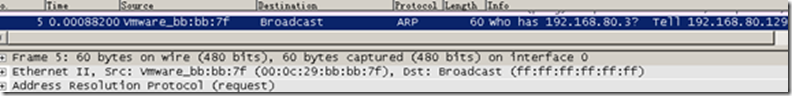
The next packet, number 6, is B directly responding to A’s ARP request, providing its MAC address to A. This demonstrates that B, when replying to an ARP request, does not consider the fact that the request came from another network and simply responds.
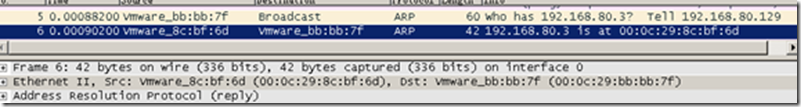
Subsequently, there are some repeated ping requests and ping replies.
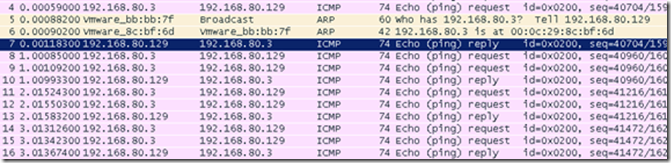
Therefore, capturing packets with Wireshark corroborates our prior theoretical analysis.



