Capturing HTTPS Packets with Wireshark Using Burp Suite
Burp Suite System Variable Configuration
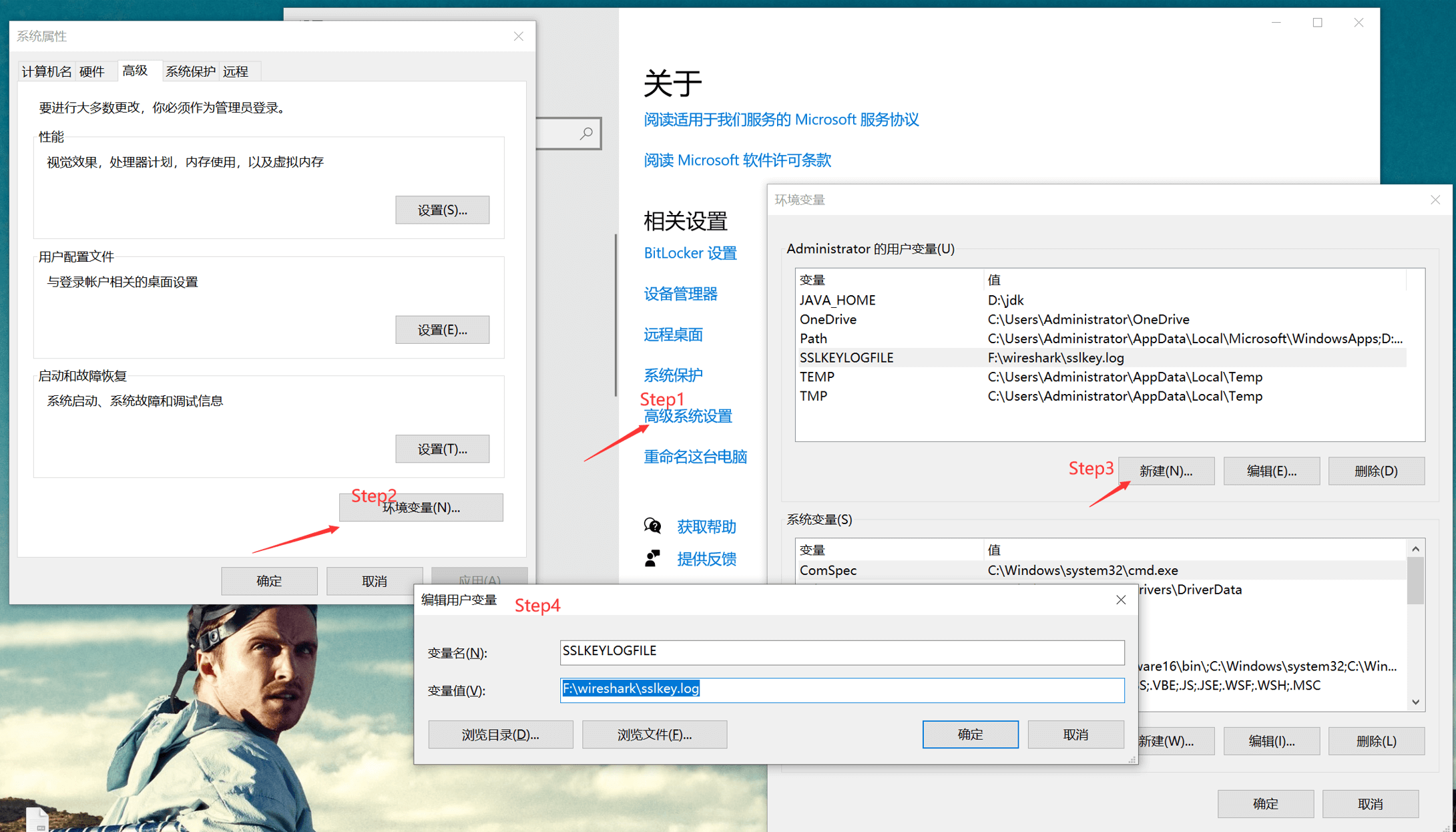
By setting system variables, you can enable Burp Suite to decrypt HTTPS. Once the TLS handshake is completed, the session keys will be stored in the designated keylog file. Wireshark can then use this keylog file to decrypt HTTPS traffic into plaintext.
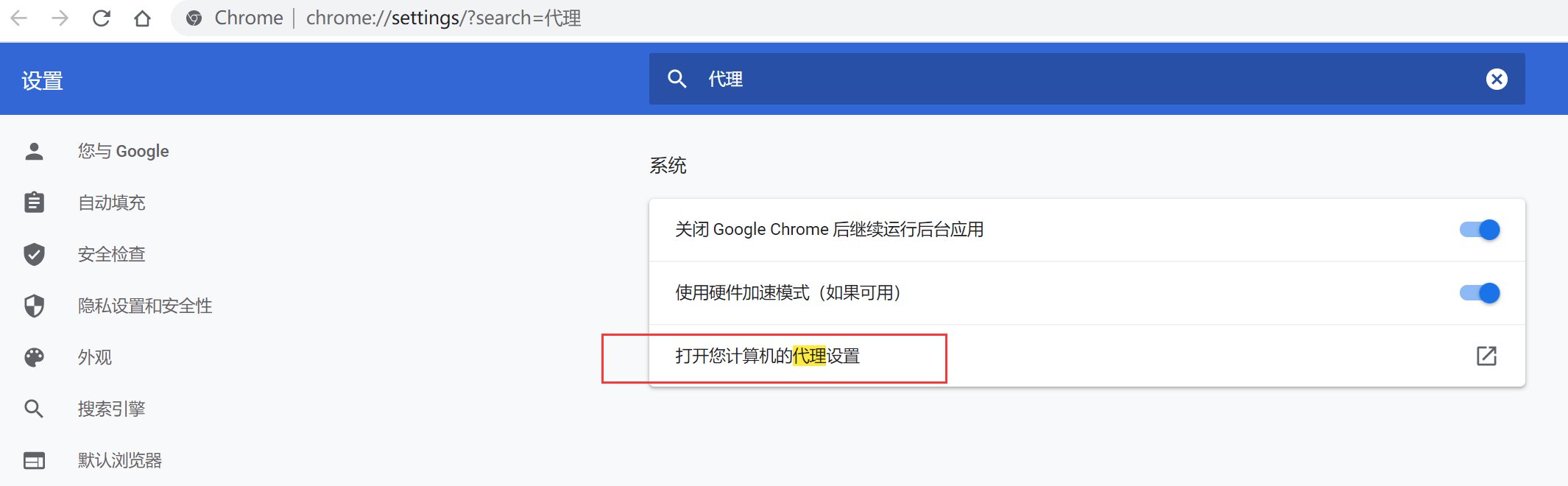
Open Computer Properties –> Advanced System Settings –> Environment Variables, set the file path:
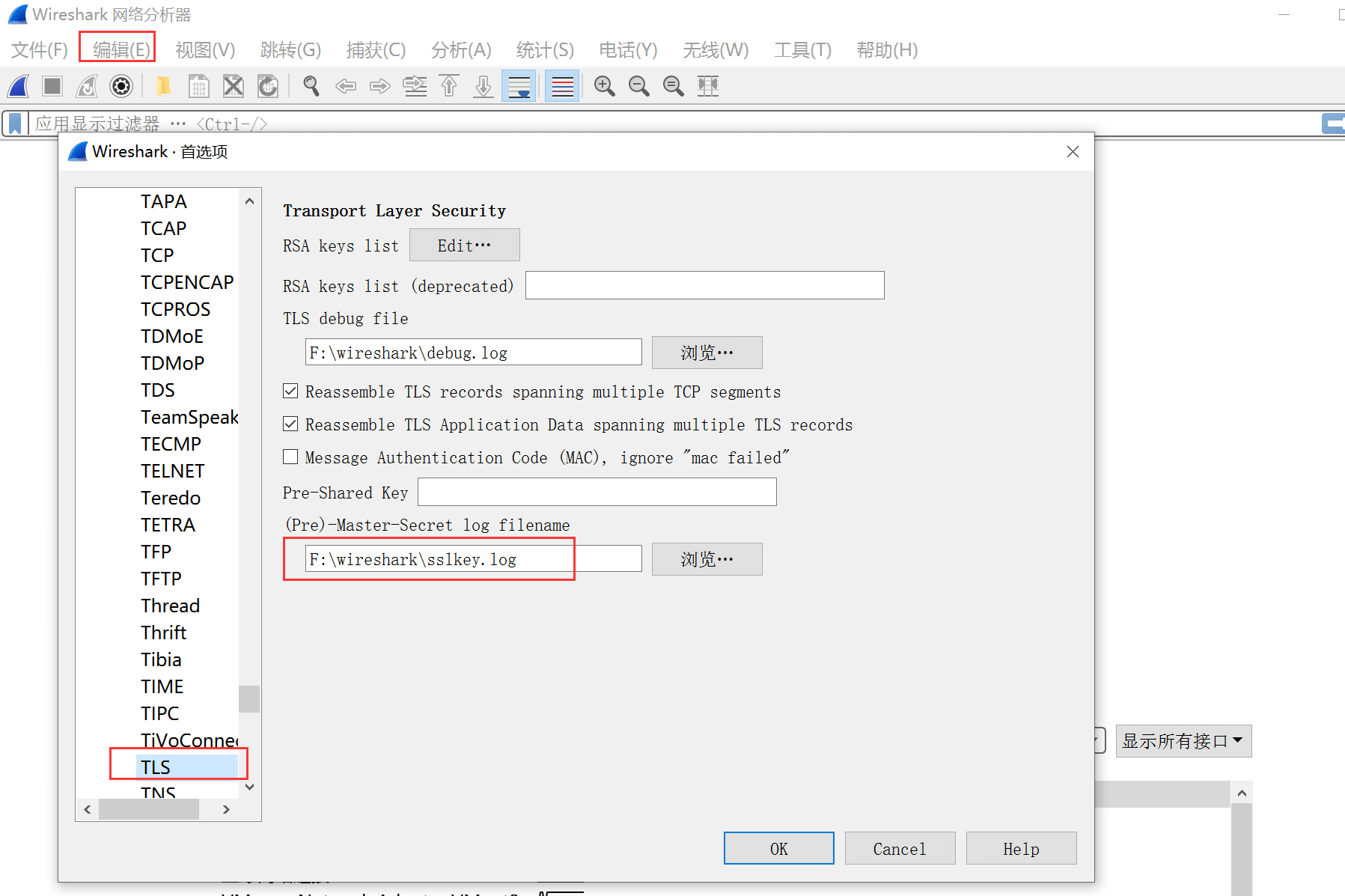
2. Configuring the Pre-Master-Secret in Burp Suite
In Wireshark preferences, select the TLS protocol and edit the Pre-Master-Secret file path:
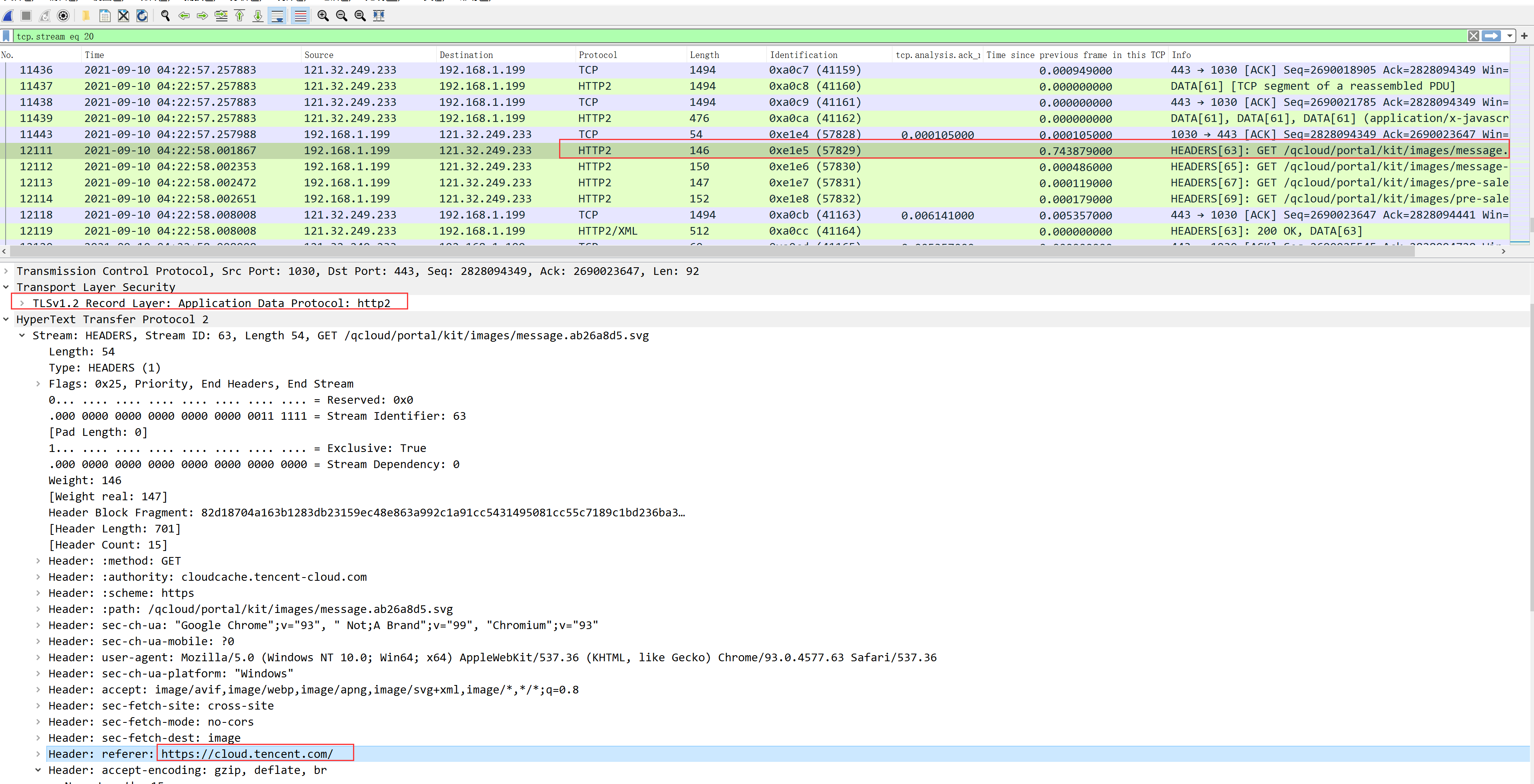
3. Packet Capture Practice
As shown below, we captured an HTTPS packet from the Tencent Cloud official website. After decryption, the HTTP header and request method (GET) can be clearly seen:
2. Capturing HTTPS Packets with Burp Suite
Burp Suite holds a place in the penetration field with powerful functions such as intercepting, modifying packets, and brute-forcing. It also has the ability to act as a man-in-the-middle to forward and decrypt for the client. Burp Suite can be downloaded, and the decompression password is Rokas.Yang. It requires a JDK environment to use.
1. Configure Proxy Listener
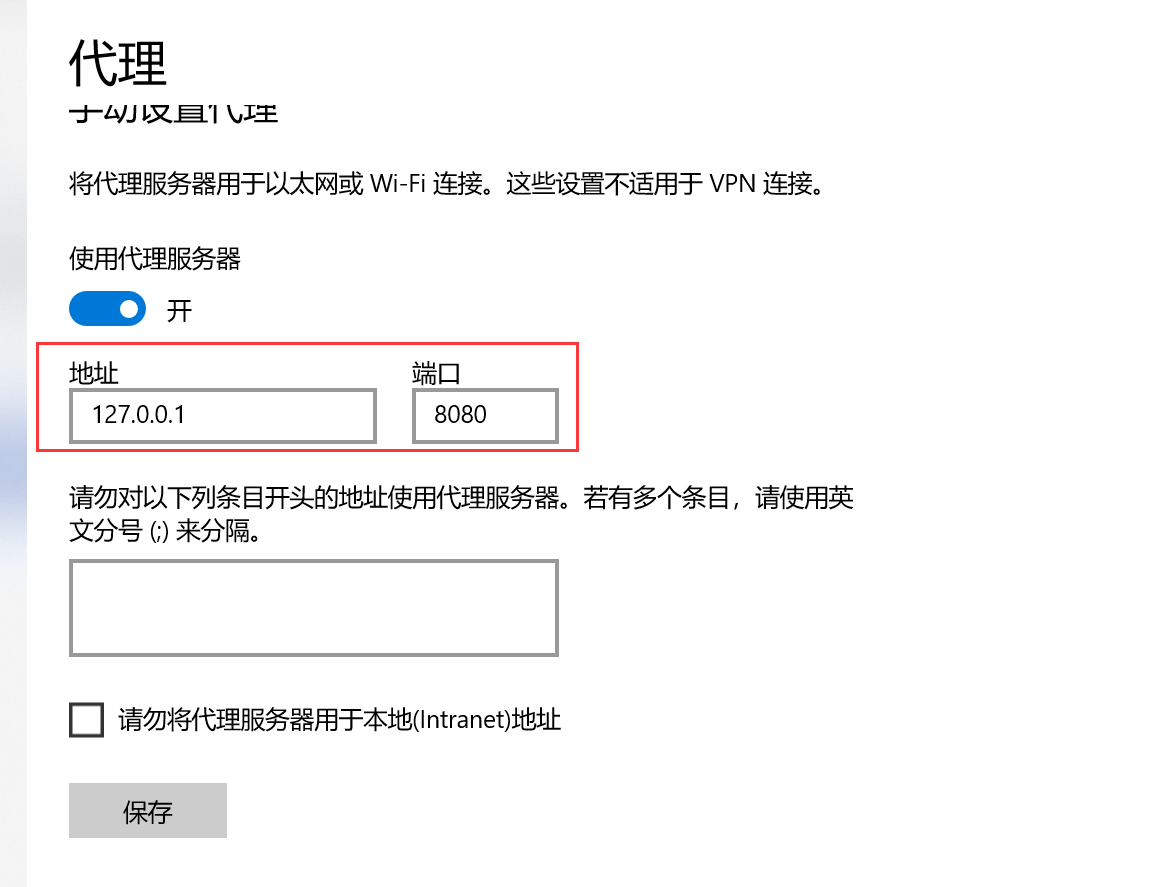
Proxy –> Options –> Proxy Listeners, set the local loopback address:
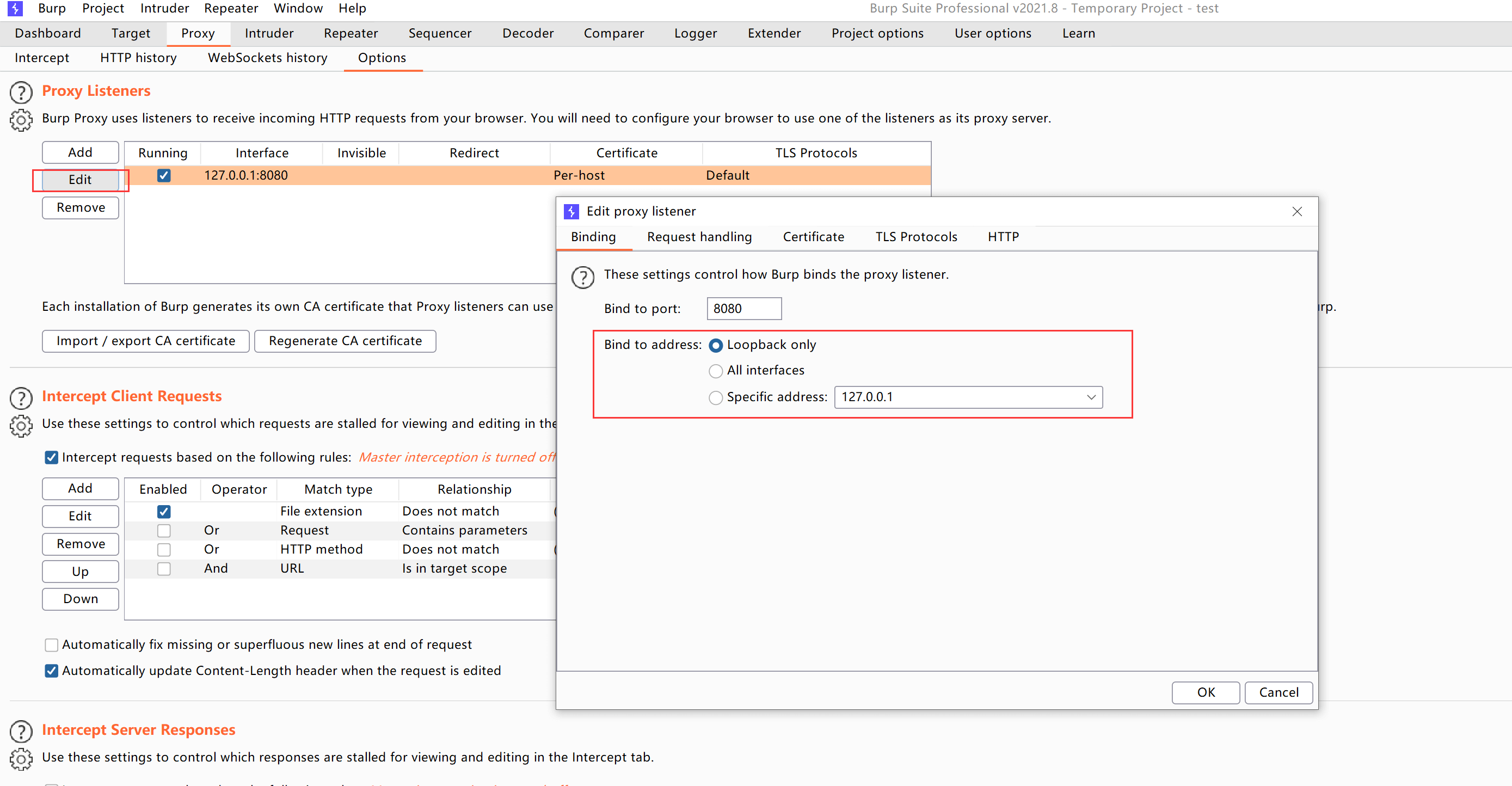
Set the browser proxy to the local 8080 port
Then all requests accessed through the browser will first pass through Burp Suite
2. Configure Intercept
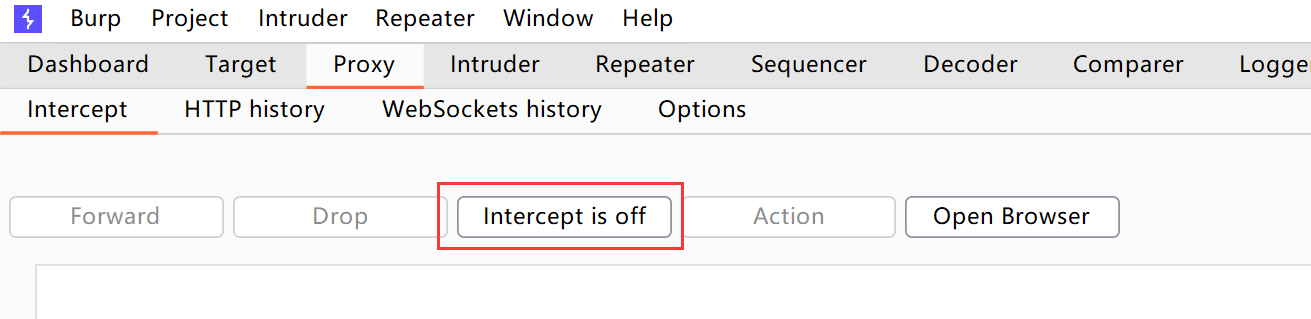
Intercept, as the name suggests, is used to intercept and modify packets. If you only want to decrypt HTTPS without modifying packets, set this option to off:
3. Install Burp Suite Issued CA Certificate
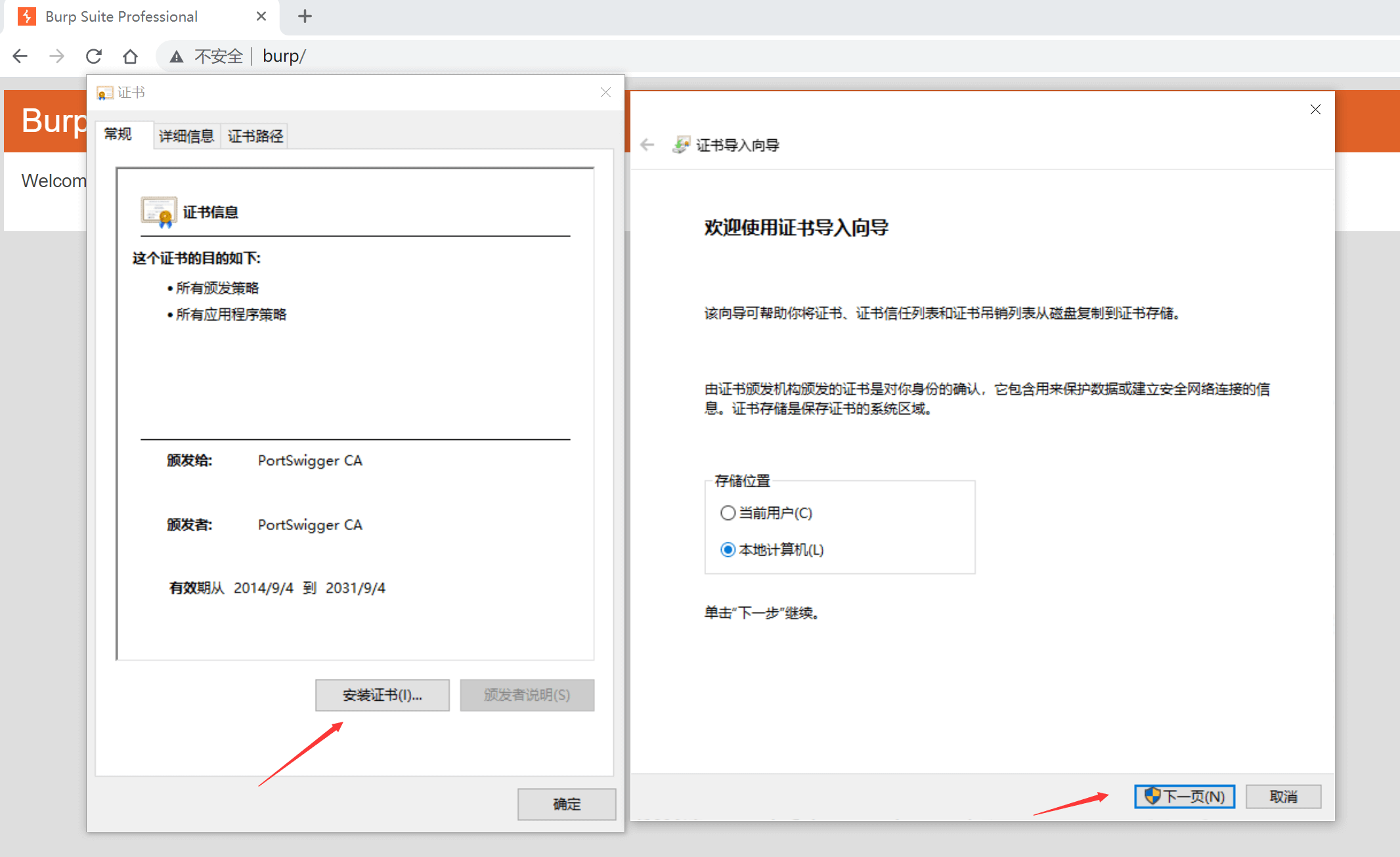
After setting the proxy, visit http://burp, and Burp Suite will hijack http://burp to provide a web page for certificate download. Download the built-in certificate to the local machine:

Import it into the trusted certificate list:
4. Start Packet Capture
Once everything is ready, start accessing with the browser, still using the Tencent Cloud official website as an example:
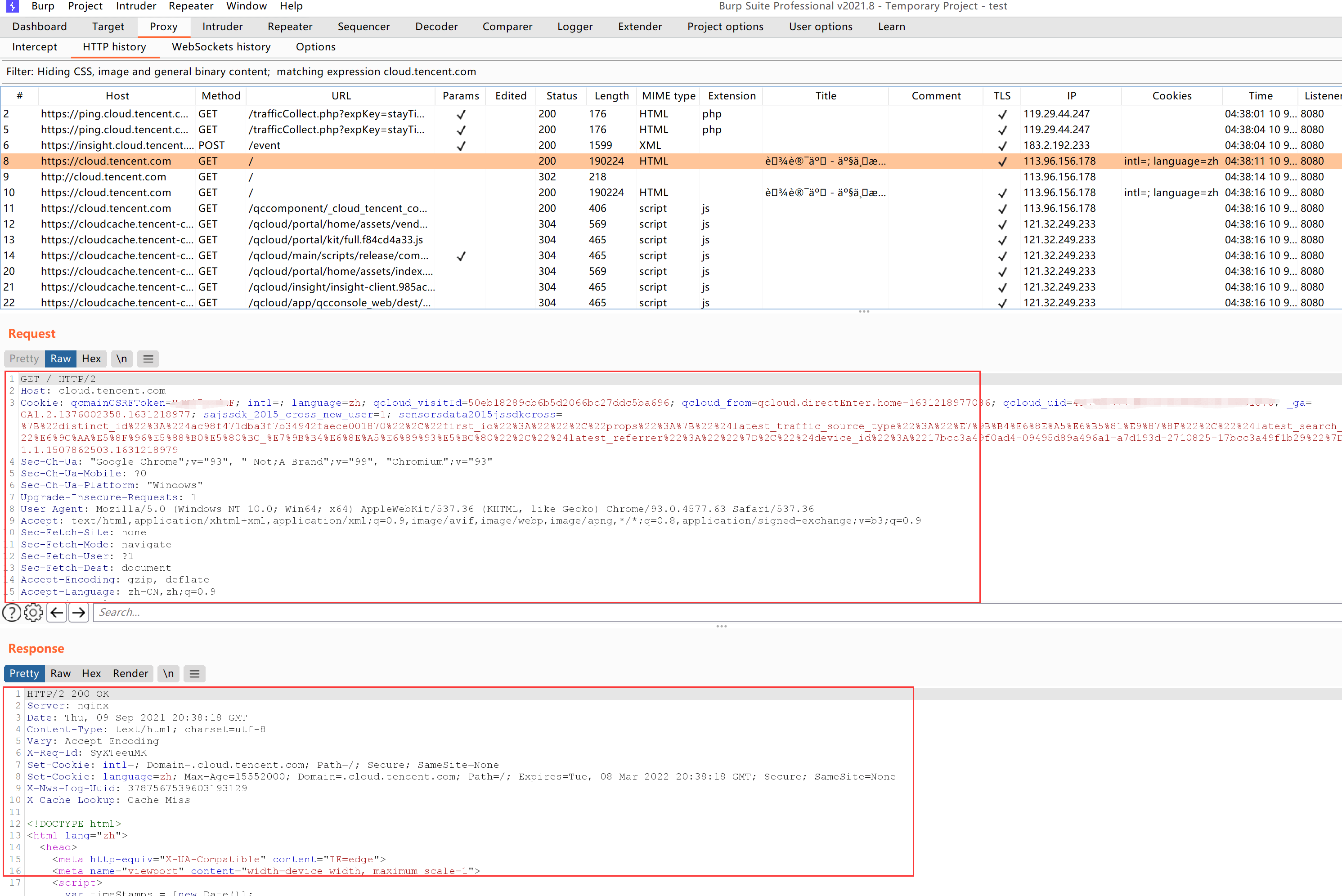
Enter the HTTP history page, where the packets just captured will be displayed in real-time. It can be clearly seen that the content in the decrypted HTTPS packet is an HTTP GET request sent by the client to the Tencent Cloud server, and a response was received.
You can also finely filter the requests you want, supporting regular expressions:
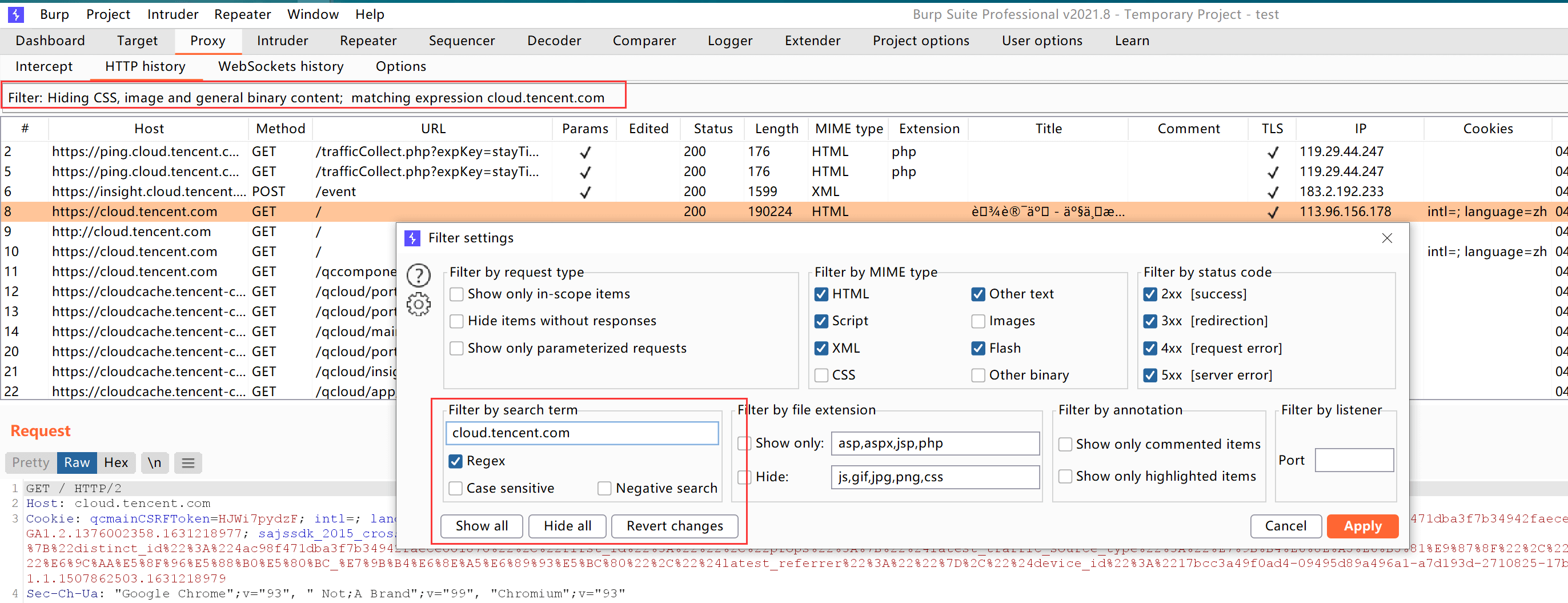
The Site map in the Target module is a well-organized site map:
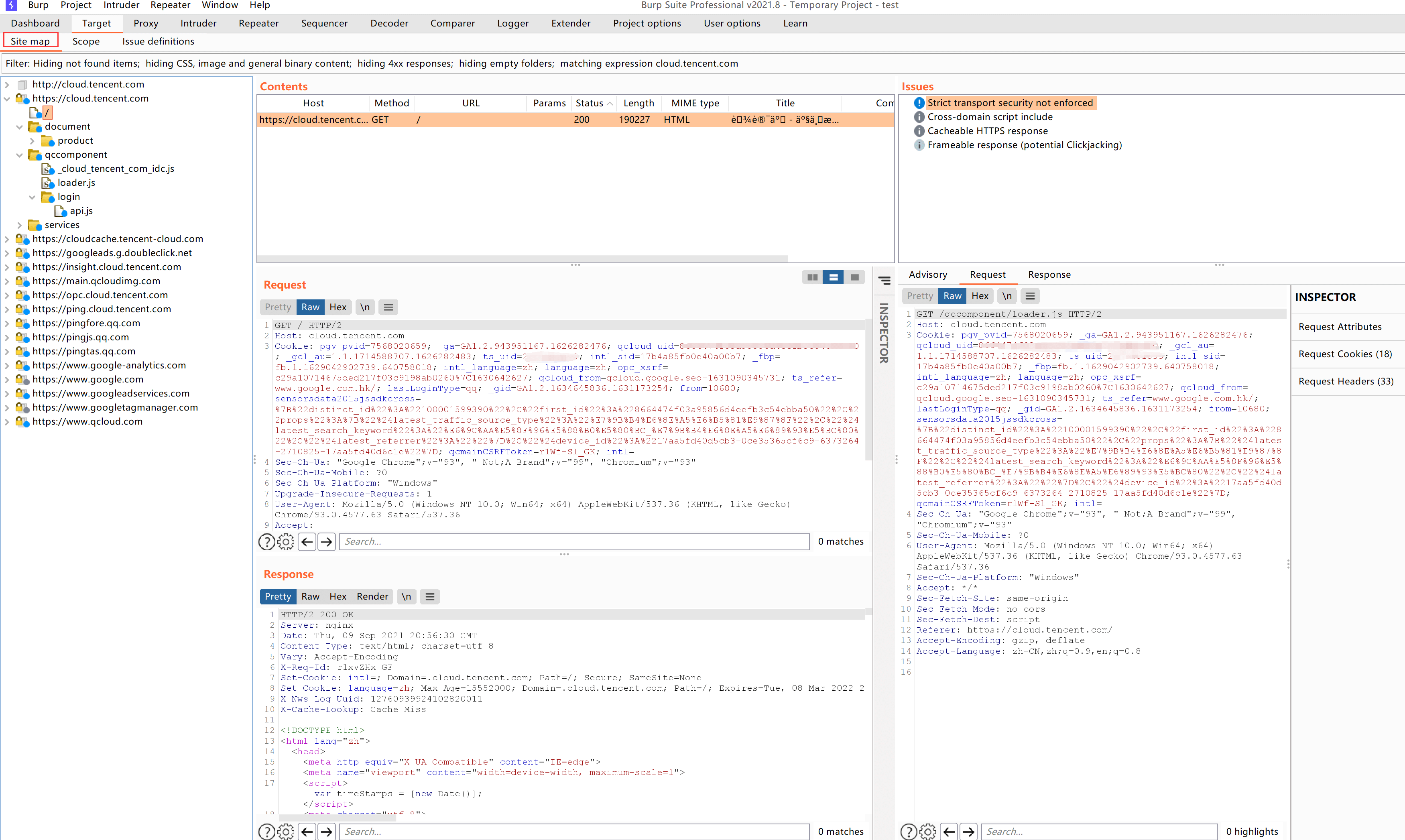
5. Capture Plaintext on Mobile Terminal via Burp Suite Proxy
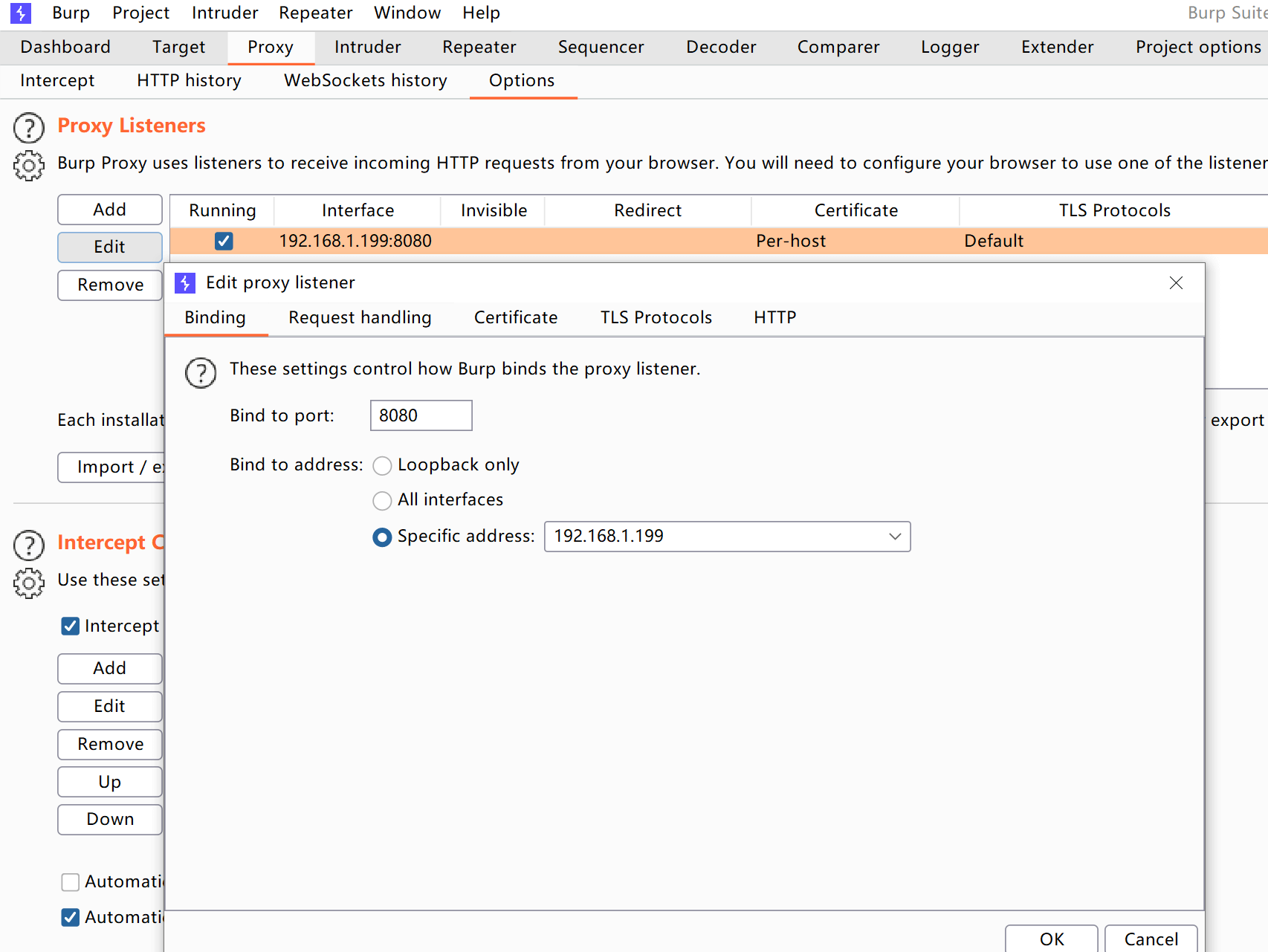
Set the listening address of the proxy module to the local intranet IP:
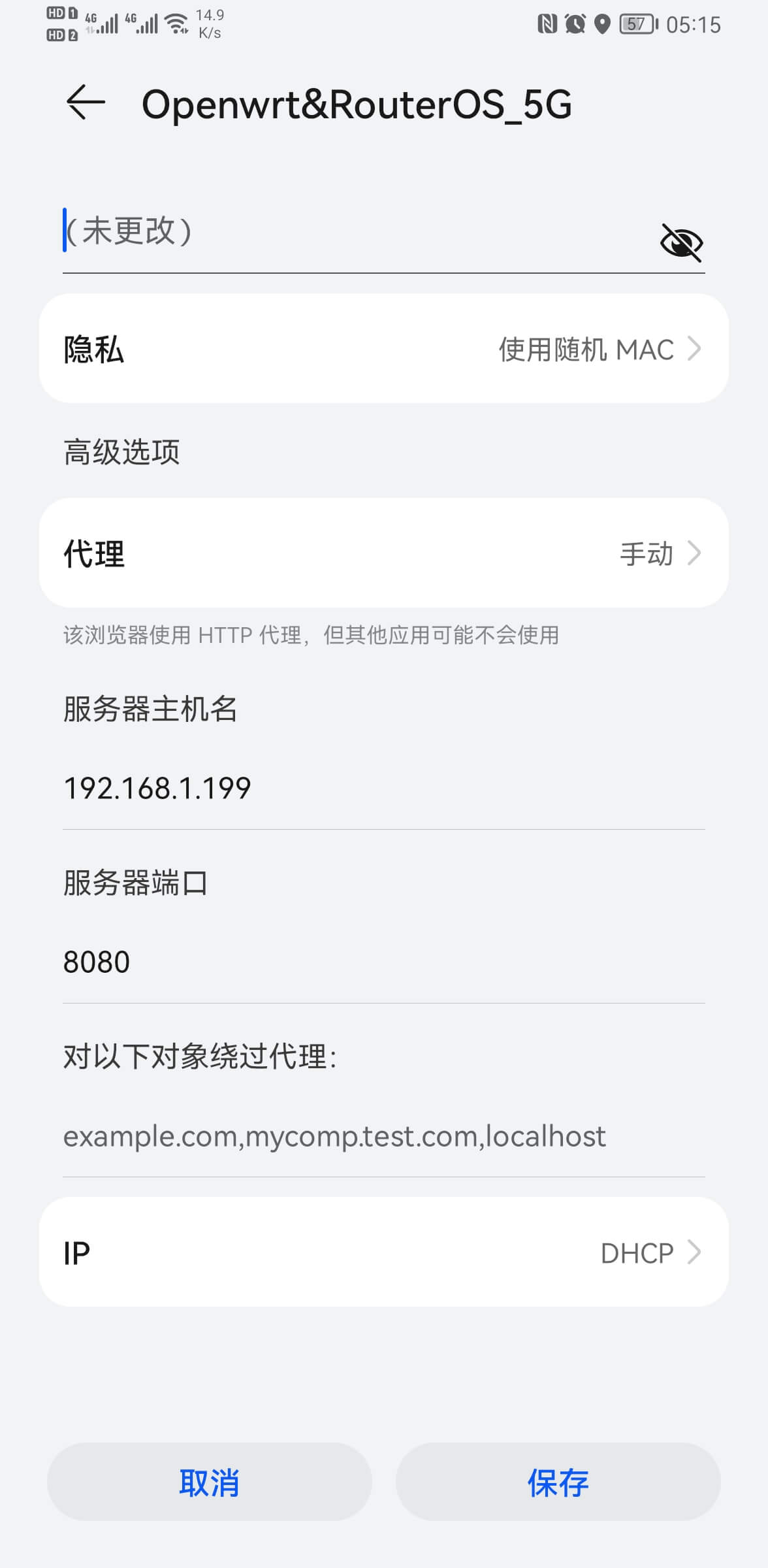
Set the mobile phone’s WIFI proxy to the local machine’s IP:PORT on the same local network
Similarly, the mobile terminal also needs to install the Burp CA certificate. The certificate downloaded by Burp is in .der format, which some phones cannot recognize. Therefore, I converted it to .cer format. Download link: Download and install the burp-cacert.cer file.
At this point, when the mobile phone accesses the external network, it will pass through the local computer’s Burp Suite and then go out to the router. All traffic will be intercepted and forwarded by Burp Suite, including mobile apps.
We take capturing data from the JD app as an example:
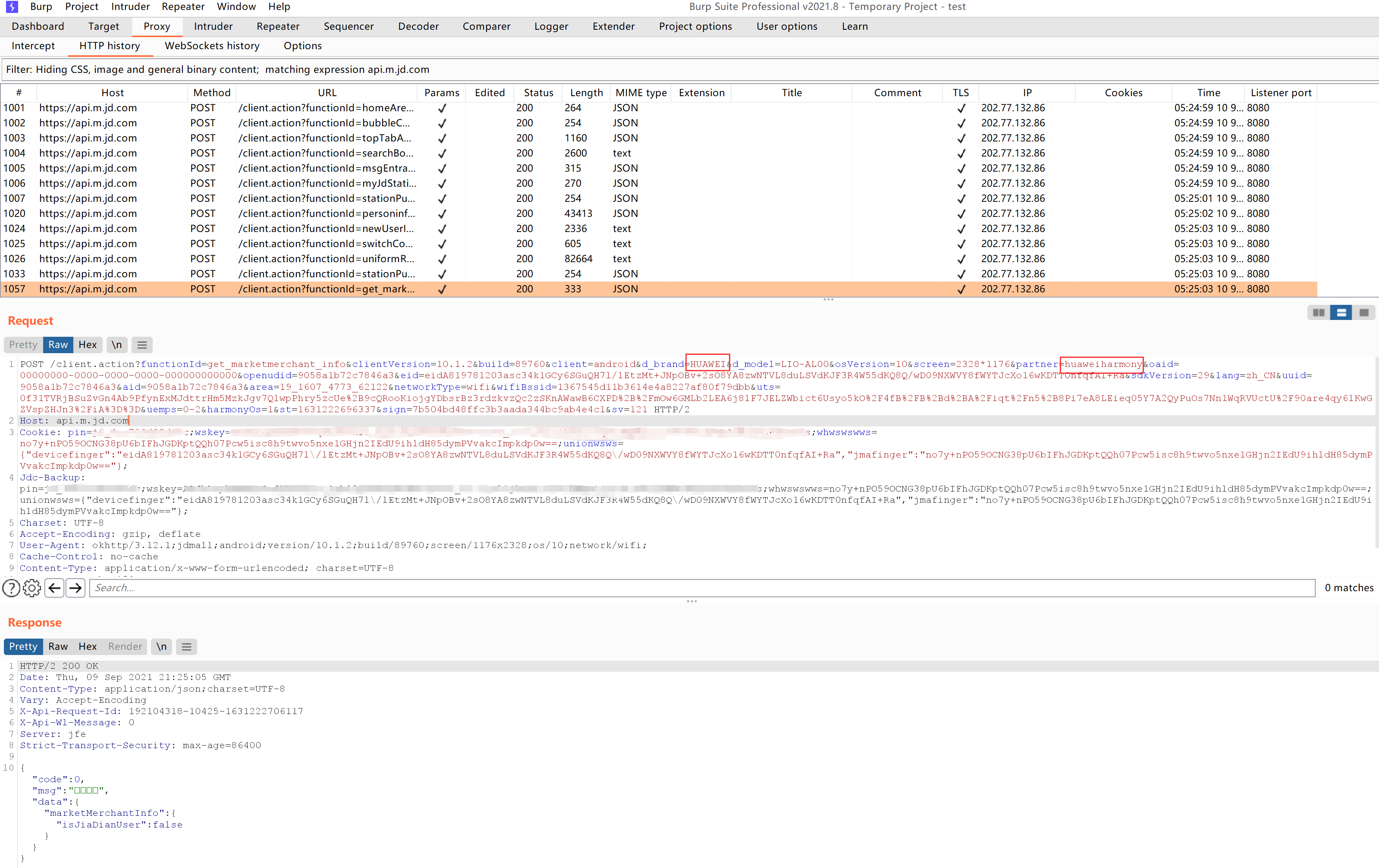
HTTPS has been successfully decrypted into plaintext.
3. Capturing HTTPS Packets with Charles
Charles is a small proxy packet capture tool that also has the function of issuing CA certificates and decrypting HTTPS. Official download link:
1. Proxy Configuration
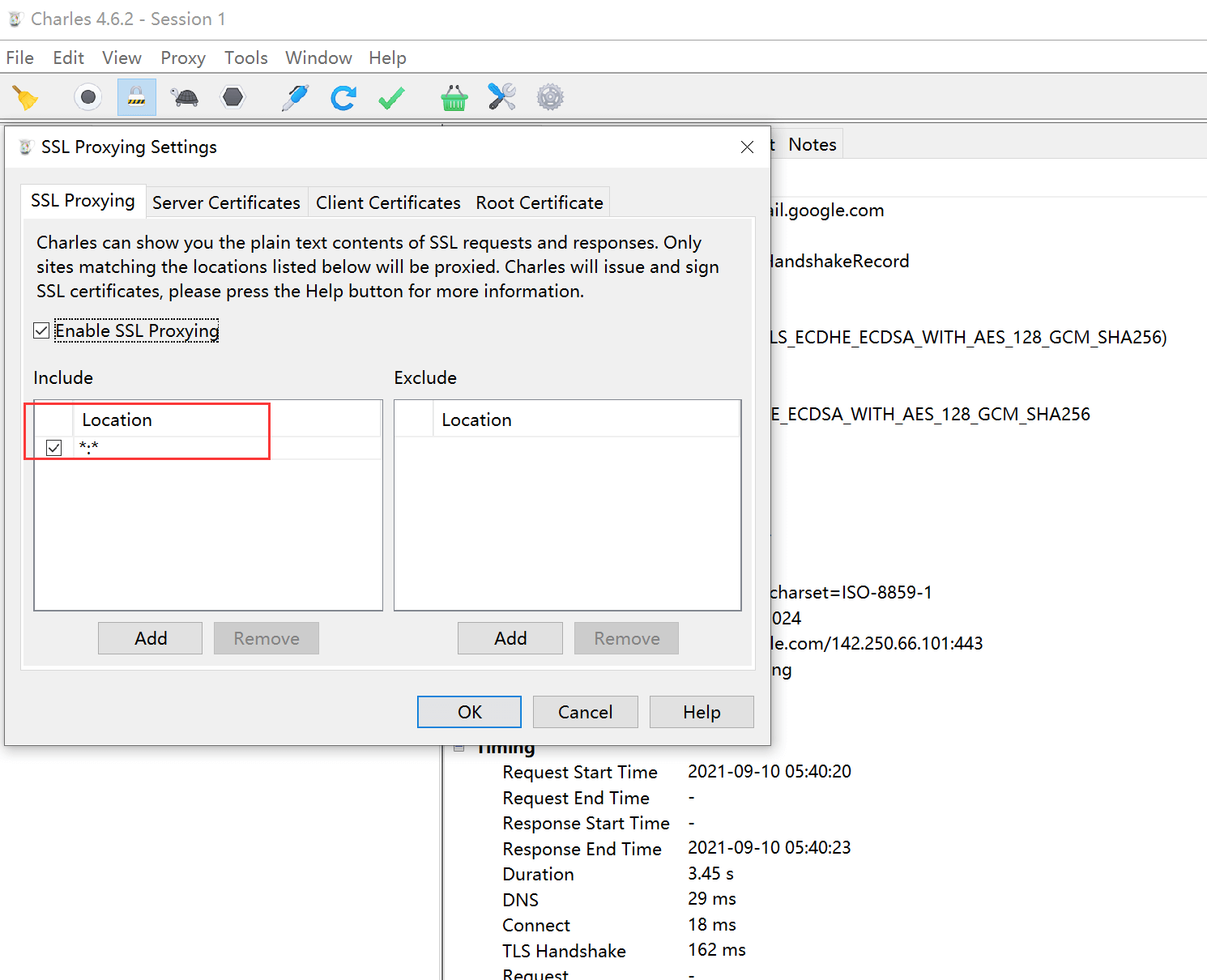
Proxy –> SSL Proxying Settings, as shown below, open SSL proxying and configure proxy content for all host ports
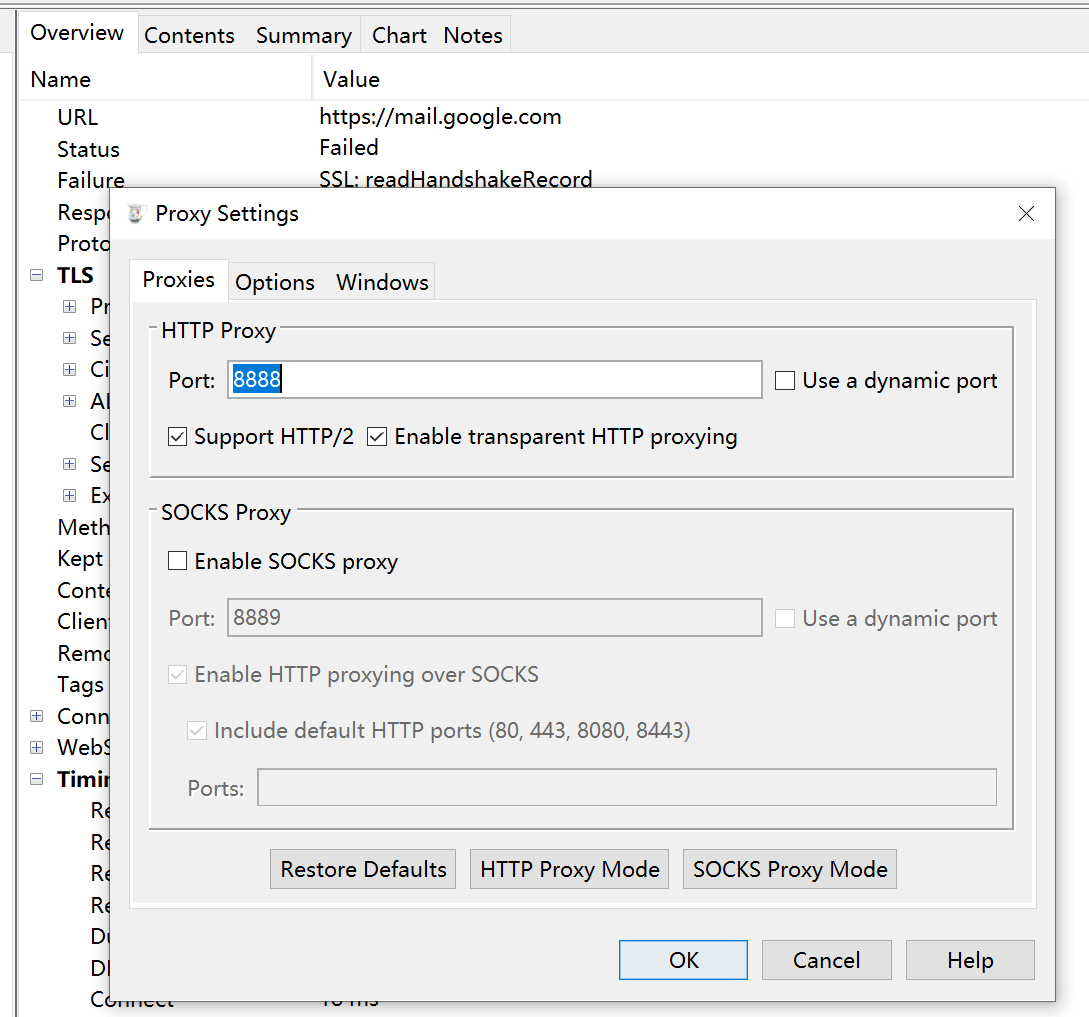
Proxy –> Proxy Settings to set the proxy port, default is 8888, and it will proxy the local machine by default
2. Install CA Certificate
After setting the browser proxy to the local 8888 port, visit to automatically download the certificate file in pem format. The computer may not recognize it, so I converted a .crt format, download and install it, and the import method is the same as installing the Burp Suite CA certificate, which will not be repeated here.
3. Packet Capture Practice
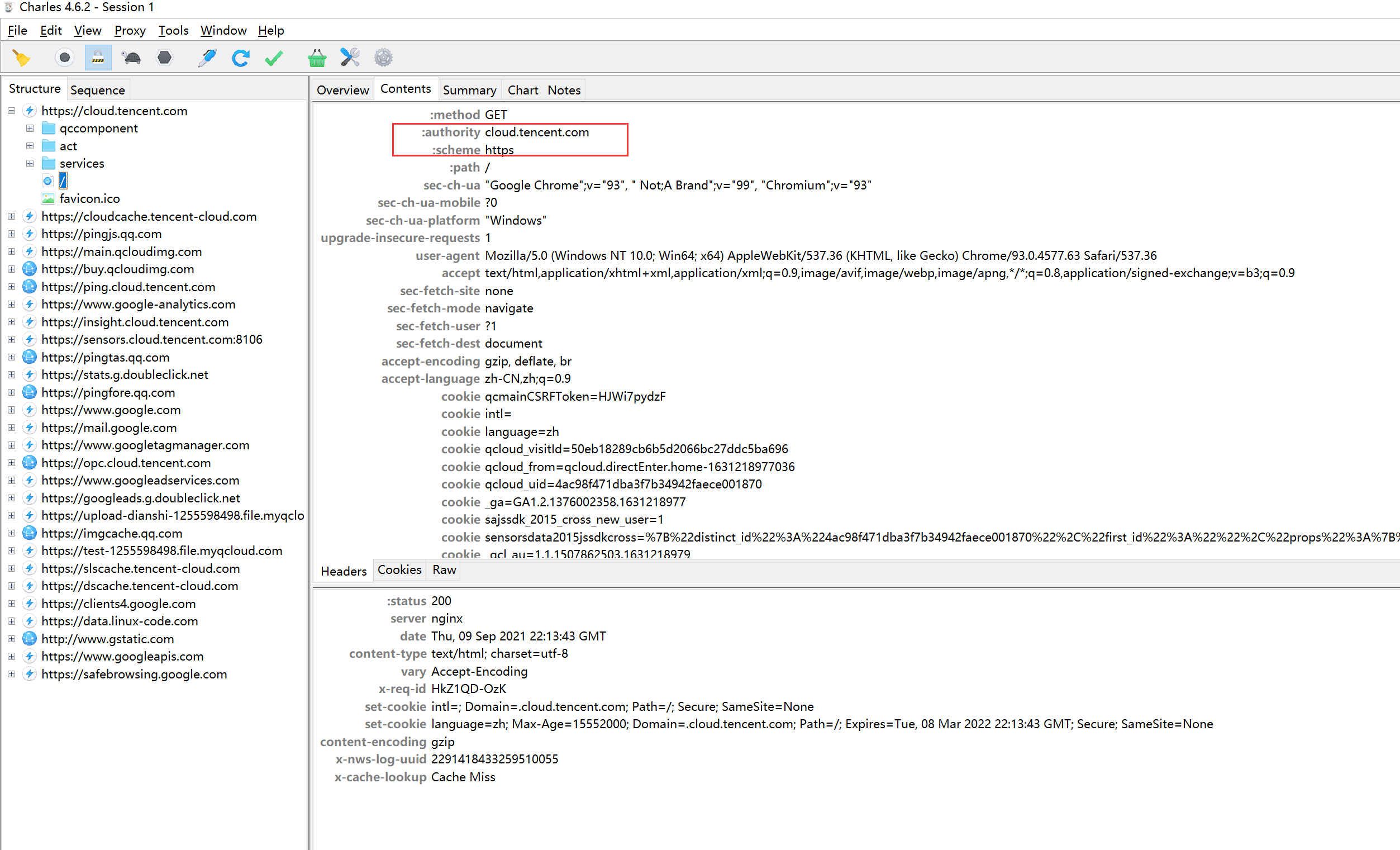
Next, try to capture HTTPS requests, still using the Tencent Cloud official website as an example:
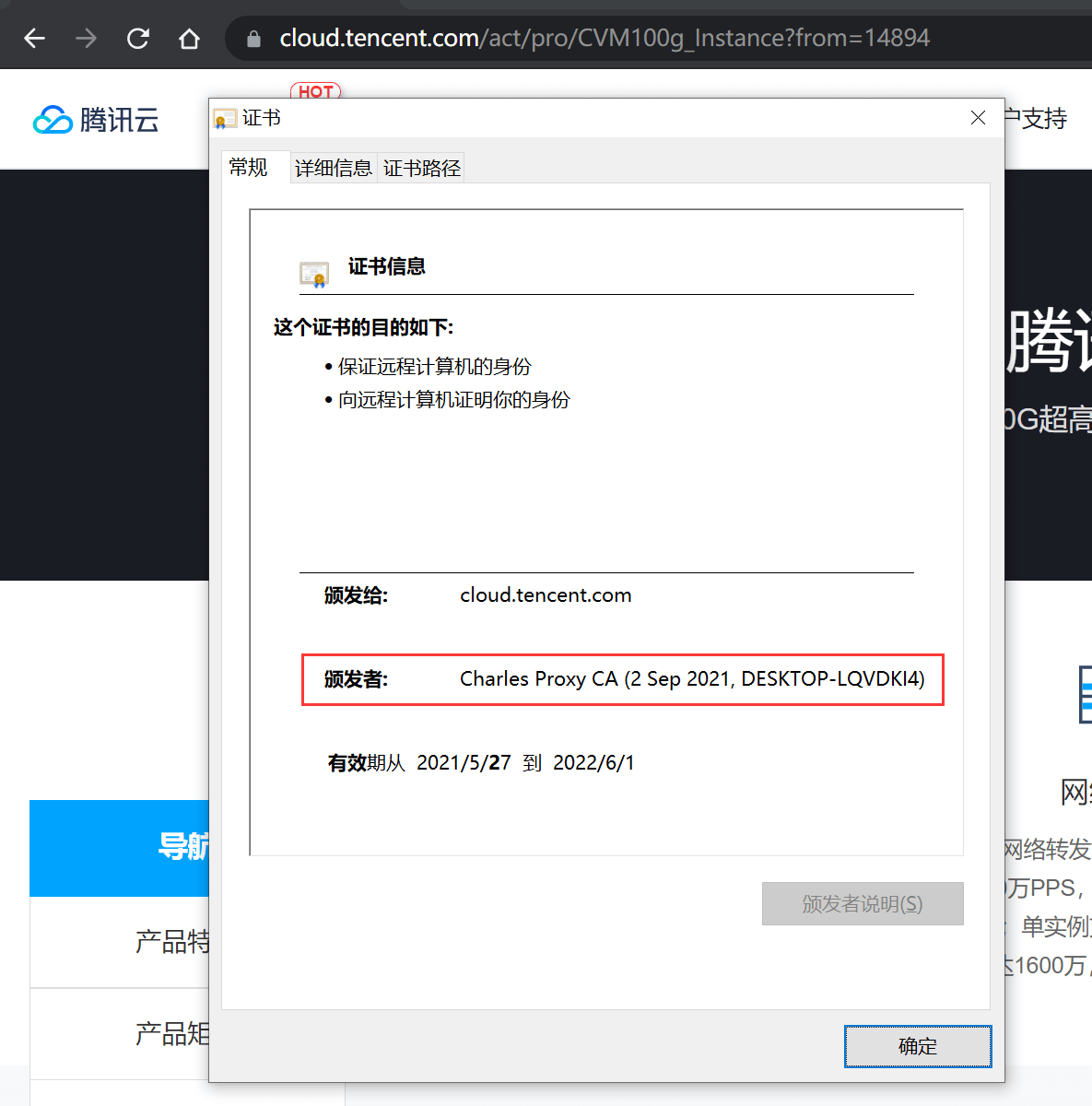
After opening the official website in the browser, you can see that the CA root certificate is the one we imported, and the HTTPS plaintext is captured:
Structure organizes the access structure of each site, similar to the sitemap function:
4. Capture Plaintext on Mobile Terminal via Charles Proxy
The configuration logic is the same as Burp Suite. Set the mobile WIFI proxy to the local computer’s Charles listening port (default 8888), and the certificate installation is the same, which will not be repeated.
Similarly, we capture the HTTPS request of the JD app:
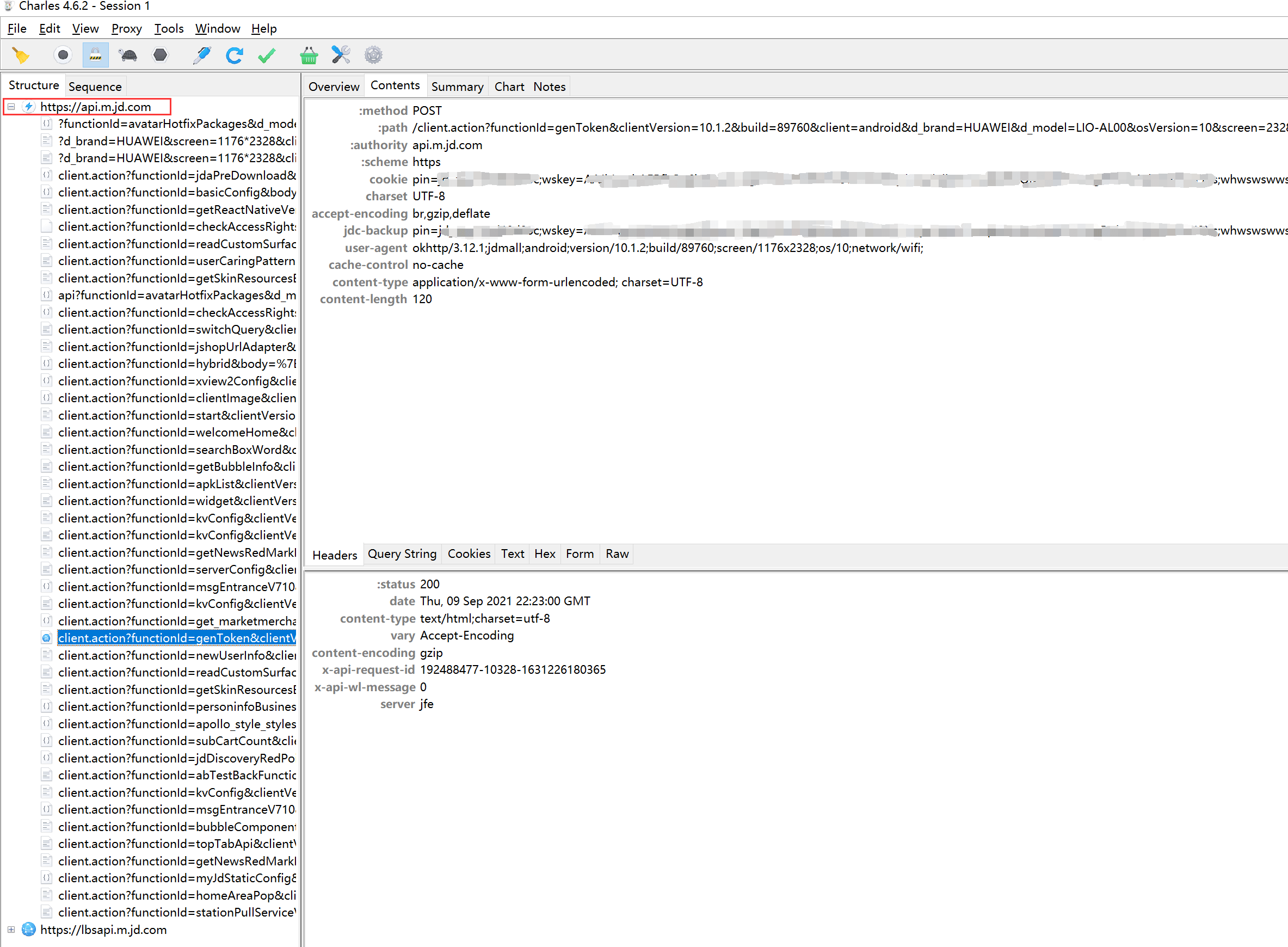
Successfully captured HTTP plaintext requests and response headers.
4. Summary
All three software have the ability to capture HTTPS plaintext, but the applicable scenarios are different:
Also uploaded a PDF version:



