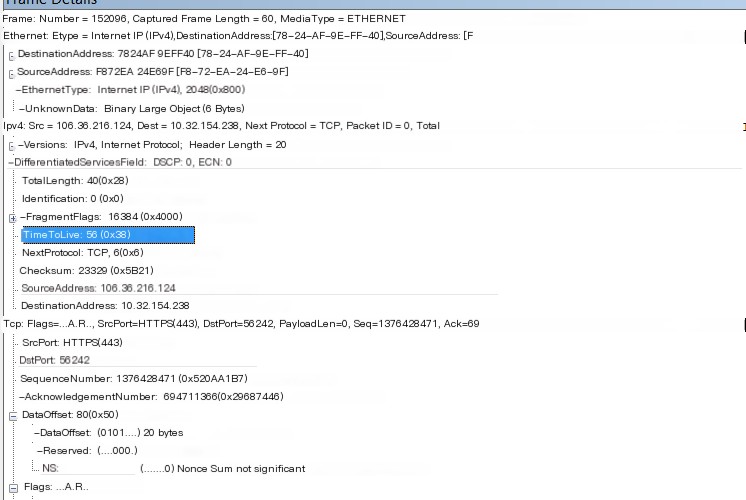
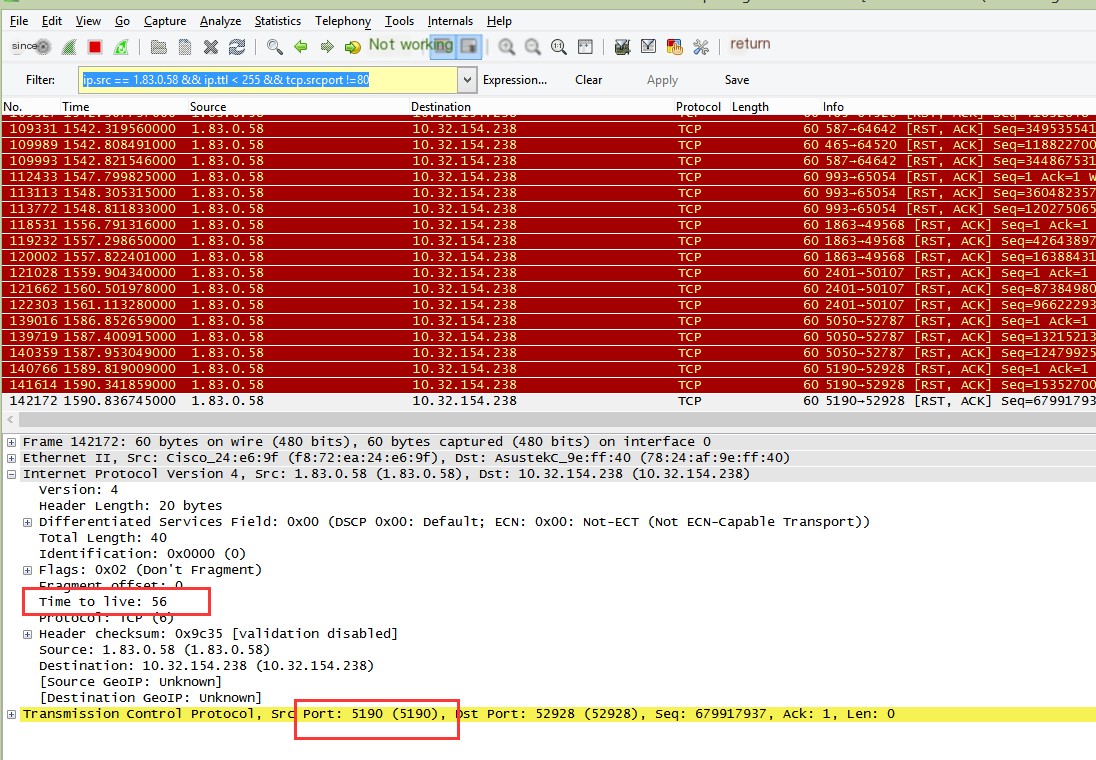
To use Wireshark for firewall packet detection, open the application and enter the filter “ip.src == [IP] && ip.ttl < 255”. This is because packets forged by the firewall typically have a TTL of 255, whereas genuine packets should have a TTL of 56. This filter helps in directly excluding the fake packets. Next, use a port scanner to scan all ports of the target IP. Finally, focus on identifying the ports that remain unfiltered after applying the scan.
21
80
4434655879931863240150505190
 />
/>