You are a skilled digital forensics investigator faced with a challenging task. An intriguing Docker image analysis awaits you, with multiple layers hiding critical information and clues. Your goal is to uncover these hidden layers, examine their contents, and piece together the puzzle to solve the mystery. Test your skills, as each layer contains new surprises and valuable insights. Can you uncover the secrets hidden beneath the surface of this mysterious Docker image?
Image name: mmox/what-is-0xl4ugh
Challenge Link
https://app.letsdefend.io/challenge/docker-forensics
How many layers does this Docker image have?
You need to use the dive command to count the layers of the container.
dive mmox/what-is-0xl4ugh
dive is a container image analysis tool that visually shows which files have changed in each layer and the disk space occupied by each layer. This way, you can see the historical build process of the image. It also shows the disk space usage of the image, allowing you to analyze if there is room for optimization, especially for large image files.
In dive’s TUI interface, use the tab key to switch left and right, and the arrow keys (↔) to switch up and down.
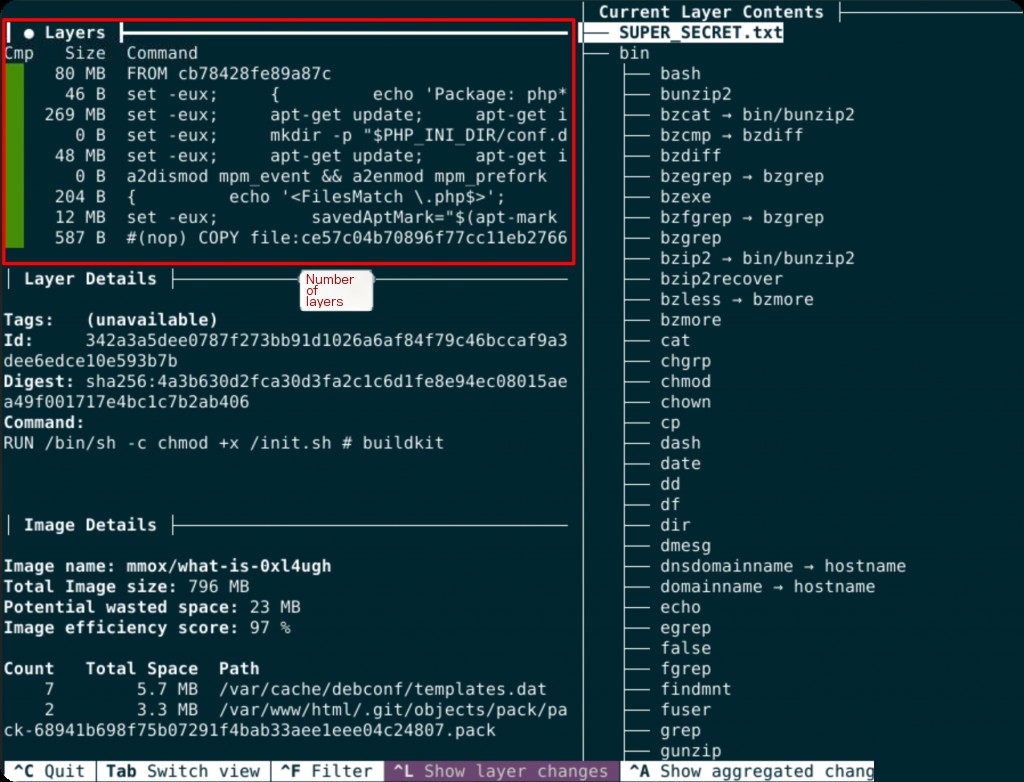
However, dive itself does not have a dedicated parameter to directly count the number of Docker image layers, so you need to manually count the layers. There are 23 layers here.
What web server is used by the image?
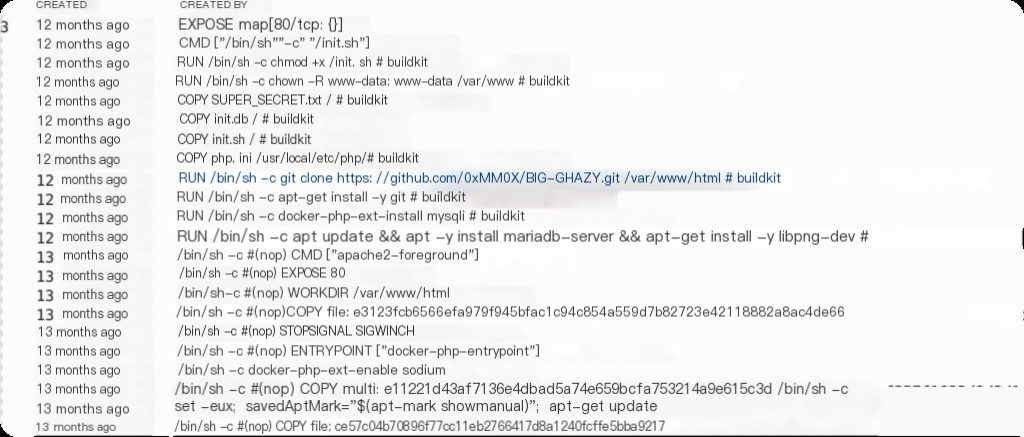
docker history --no-trunc mmox/what-is-0xl4ugh > history.txt
Using dive is not convenient for this, and docker history does not display completely. You need to add the –no-trunc parameter to view the full build container history commands.
What are the database username and password?
This task requires viewing the contents of files within the image. There are two ways to do this:
- Run the container and view the files inside.
- Create the container (without running it) and copy the files to the host machine to view them.
- Export the image as a tar file and view the files directly within the image.
Using docker run and docker exec
This method is common: first, run the container and then enter it to view the contents. However, it is not recommended as many containers require specific parameters or environments to run correctly. This is the most common way to use docker, so it will not be demonstrated here.
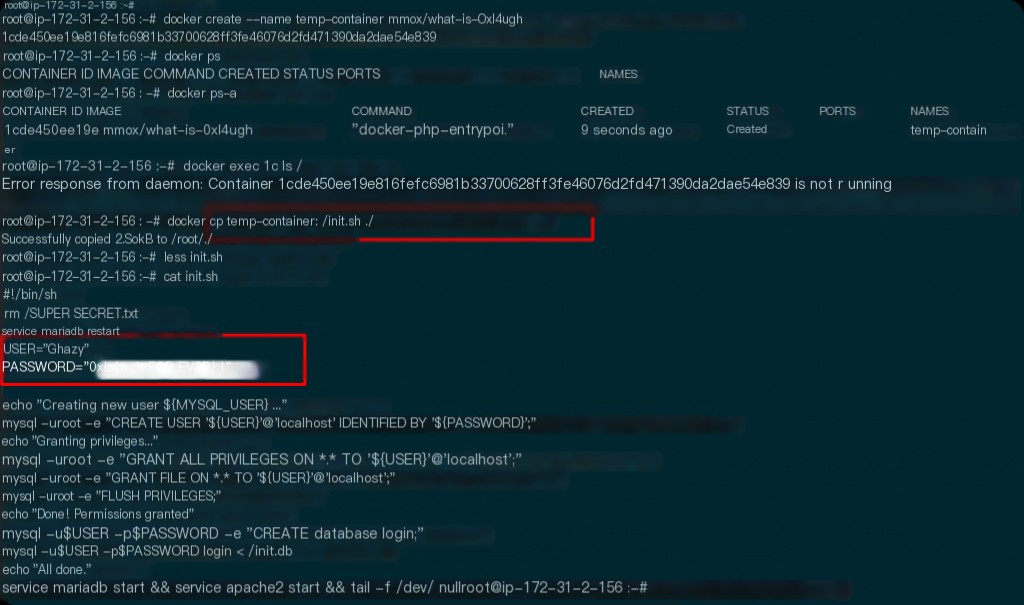
Using docker create and docker cp
docker create --name temp_container mmox/what-is-0xl4ugh docker cp temp_container:/init.sh ./
Using docker save and tar commands
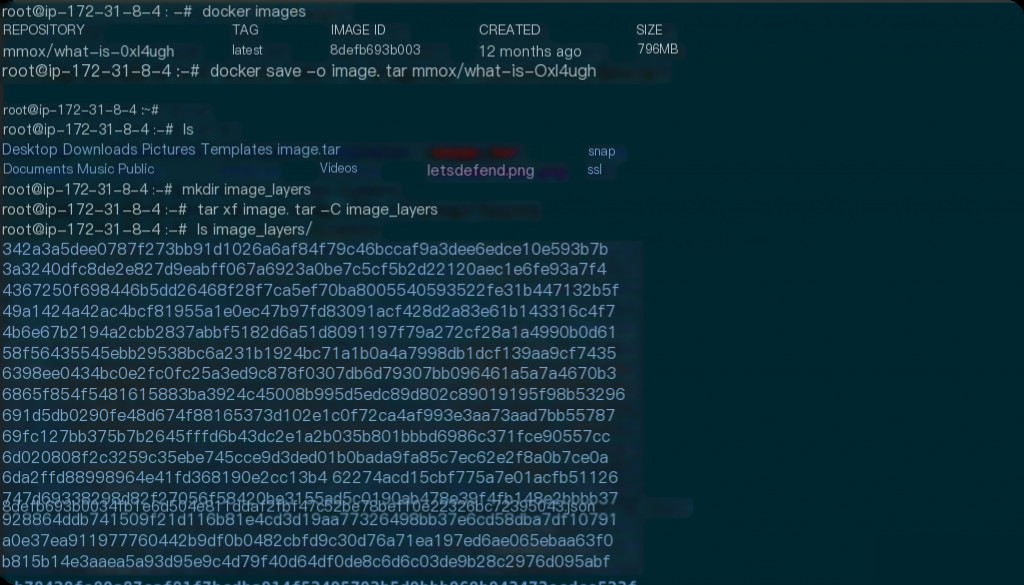
Use the docker save command to save the image as a tar file and then extract the saved tar file.
docker save -o image.tar mmox/what-is-0xl4ugh mkdir image_layers tar -xvf image.tar -C image_layers
After extraction, you will see a directory containing all the image layers. Each layer is a tar file.
find ./image_layers/ -name "*.tar" -exec tar -O -xf {} init.sh 2> /dev/null \;
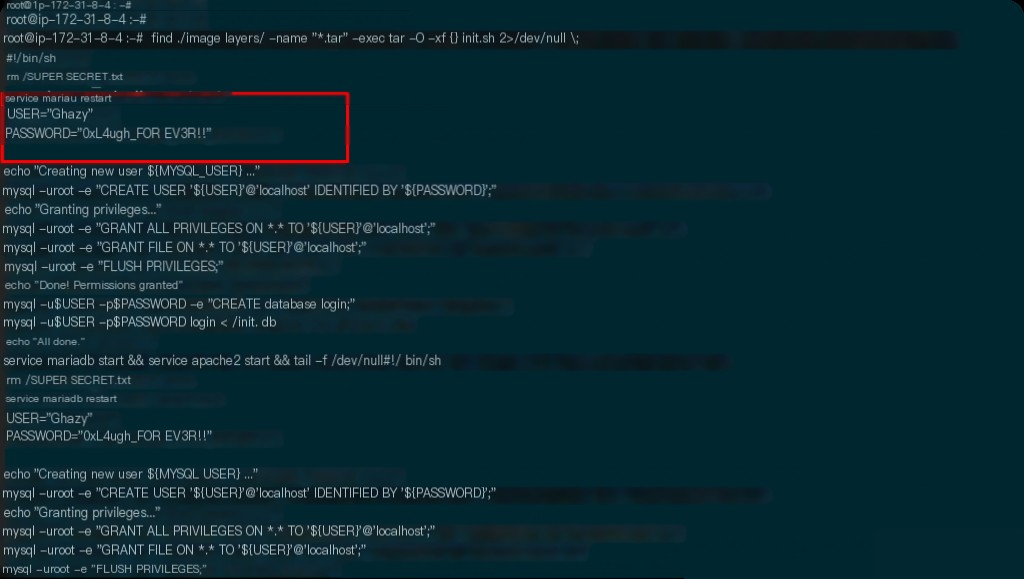
This method allows you to view the internal files of the image without creating a container.
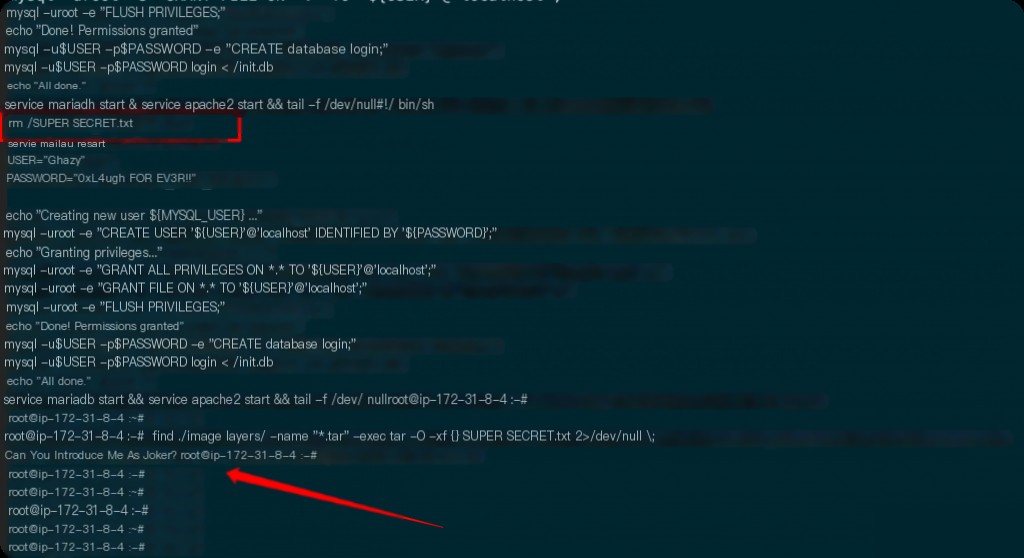
What is the deleted SECRET?
This is related to the previous question. In init.sh, there is a command rm /SUPER_SECRET.txt. If you start the container and then check, the file will already be deleted, and you need to reach the layer before the file is deleted.
Use the same command as above to view the file contents.
find ./image_layers/ -name "*.tar" -exec tar -O -xf {} SUPER_SECRET.txt 2> /dev/null \;
Post Views:74Support


