Last year, during an offline event, I received a registration invitation code for the Attack and Defense World CTF platform from a cybersecurity professional at SaiNing. Now, the platform is open for everyone to register. However, I hadn’t attempted any CTF challenges on it until today. Since I planned to explore CTF this summer and had some free time, I spent about half an hour solving the beginner-level web challenges. These challenges were quite straightforward, each focusing on a single concept. Despite their simplicity, I decided to document my thought process while solving them.
1. view_source
Simply press F12 or Ctrl+U to view the source code and retrieve the flag. No further explanation needed.
2. get_post
This challenge involves sending simple POST and GET requests. Just use HackBar to send the requests, and you’re done. Using Burp Suite here would be overkill.
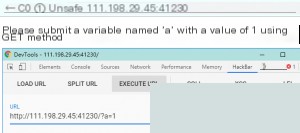
Then,
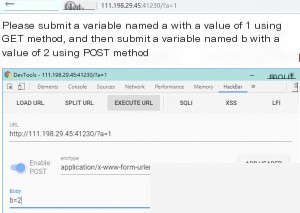
you’ll get the flag. Some users in the comments mentioned that modifying the request method in Burp Suite to POST didn’t work. Why?
This user is likely a beginner. Let me explain briefly: when modifying the request method in Burp Suite, it’s not as simple as just changing
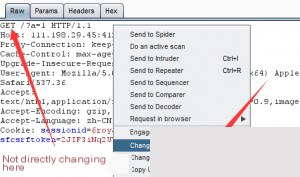
Pay attention to the details:
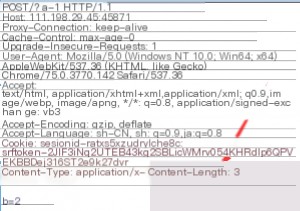
If you modify the request in Burp Suite by changing `GET /?a=1 HTTP/1.1` to `POST /?a=1 HTTP/1.1` and add `b=2` in the body, it won’t work. You also need to add the header `Content-Type: application/x-www-form-urlencoded` so the server can recognize the POST data. Burp Suite automatically adds this header when changing the request method.
3. robots
This challenge tests knowledge of the robots.txt protocol. It’s very simple. Here’s a brief explanation from Baidu:
The `robots.txt` file is a plain text file that can be created and edited using any common text editor, such as Notepad on Windows. It’s a protocol, not a command. When search engines visit a website, they first check the `robots.txt` file to determine which files on the server are accessible.
Since `robots.txt` is located in the root directory of the website, you can access it directly by appending `/robots.txt` to the URL.
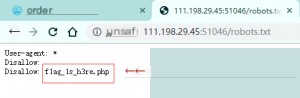
Visiting this page reveals the flag.
4. backup
This is more of a common-sense challenge. Simply append `.bak` to `index.php` in the URL, like this: `xxx:port/index.php.bak`. Download the file and open it with a text editor to find the flag. No difficulty here.
I always follow one principle: if a problem can be solved using the browser’s developer tools, I won’t use any other tools. Chrome is amazing!
For this challenge, check the response headers in the Network tab of the developer tools.
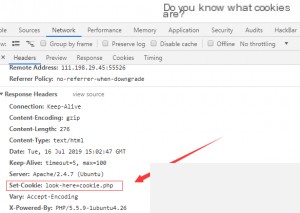
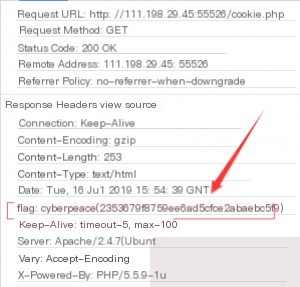
It clearly indicates that we need to open the `cookie.php` page. The flag is hidden in the response header.
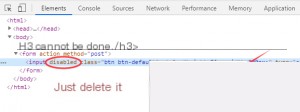
This challenge is extremely simple. Just remove the `disabled` attribute from the input element, and you’ll get the flag.
7. simple_js
8. xff_referer
This challenge tests the ability to forge X-Forwarded-For (XFF) and Referer headers. Use HackBar to add these headers.

HackBar is awesome.
9. weak_auth
This challenge was amusing. I initially planned to brute-force the password using Burp Suite, but I casually tried `123456` and got the flag. Well…
10. webshell
No difficulty here. Just use a webshell tool like China Chopper to connect.
11. command_execution
This is a simple command execution challenge.
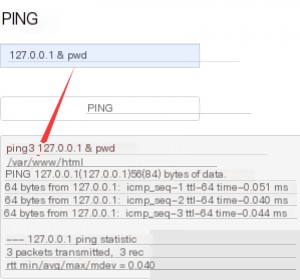
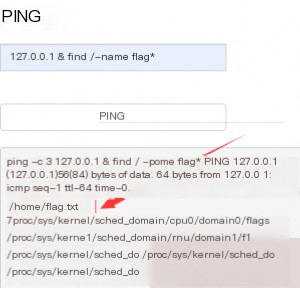
After executing the `pwd` command, I obtained the current directory path. The next step is to locate the flag and read it. Use the `find` command from the root directory to search for the flag, as it’s usually named `flag.txt`. However, it might not have an extension, so use a wildcard (`*`) to account for this. Once you find the path, use `cat` to read the flag.
Here’s a quick summary of some Linux operators:
& and &&, | and || differences:
`&`: Runs the task in the background. For example, to run `redis-server` in the background, use `redis-server &`.
`&&`: Executes the next command only if the previous one succeeds. For example, `echo ‘hello’ && echo ‘nihao’`.
`|`: A pipe operator that passes the output of one command as input to the next. For example, `echo ‘hello’ | wc -l`.
`||`: Executes the next command only if the previous one fails. For example, `cat nofile || echo “failed”`.
12. simple_php
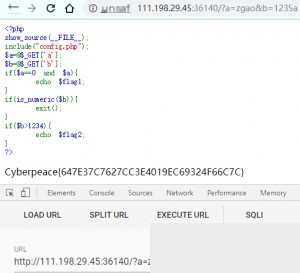
This challenge tests PHP’s weak type comparison.
PHP has two comparison operators:
==: Converts the data types before comparing.
===: Does not convert data types; compares them as-is.
When comparing strings and numbers using ==, PHP converts the string to a number before comparing:
php
var_dump('a' == 0); // true, because 'a' is converted to 0
var_dump('123a' == 123); // true, because '123a' is converted to 123
In the conditional statement, `a == 0` and `a != 0` are required. Since PHP uses weak comparison with `==`, you can set `a` to a string. During the `==` check, the string is converted to `0`, satisfying the condition. For `b`, the `is_numeric` function requires `b` to not be a number, and `b > 1234`. You can set `b = 2345a`, which is not considered a number but is greater than `1234`, satisfying the condition.