KAPE (Kroll Artifact Parser and Extractor) is used to acquire and parse data sources necessary for Windows forensics. KAPE is a powerful, free software categorization program that customizes the acquisition of important forensic artifacts from devices or storage locations and parses them within minutes. Due to its speed, KAPE allows forensic investigators to prioritize finding the most critical systems for their cases. Additionally, during the data acquisition process, the data generated by KAPE can be reviewed for clues, timeline construction, and more.
KAPE Execution Process
KAPE has two main stages:
- Target Collection
- Module Execution and Data Parsing
KAPE focuses on quickly collecting and processing relevant data, grouping artifacts into categorized directories such as EvidenceOfExecution, BrowserHistory, and AccountUsage. The advantage of grouping by category is that forensic investigators no longer need to know how to handle prefetch, shimcache, amcache, userassist, etc., as they relate to the artifacts that need to be parsed.
KAPE Download
After filling out the information on the official website, they will send the download link to your corporate email.
KAPE Target Analysis
After downloading KAPE, unzip and open it to view the Targets directory, which contains the target information that KAPE will collect.
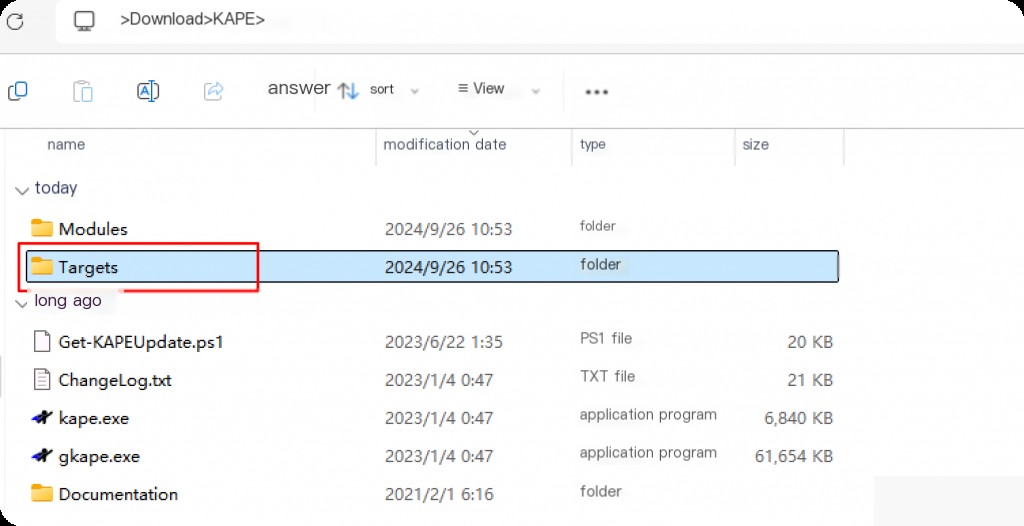
The collection targets are basic sets of files and directories. KAPE knows how to read these raw data sources and expand them to the files and directories present at the target location. Once KAPE processes all targets and establishes a file list, it processes the list and copies each file from the source to the target directory.
For files locked by the operating system and unable to be copied by conventional means, the file will be added to an auxiliary queue. This auxiliary queue contains all locked or in-use files. After processing the main queue, the auxiliary queue will be processed using different techniques (using raw disk reads) to bypass the locks. This will obtain a copy of the file from the source. Regardless of how the file is copied (regular copy or raw access), all original timestamps of directories and files themselves will be reapplied to the target files. Metadata will also be collected into log files.
You can see that these contents are further categorized by directory. Check the antivirus directory.
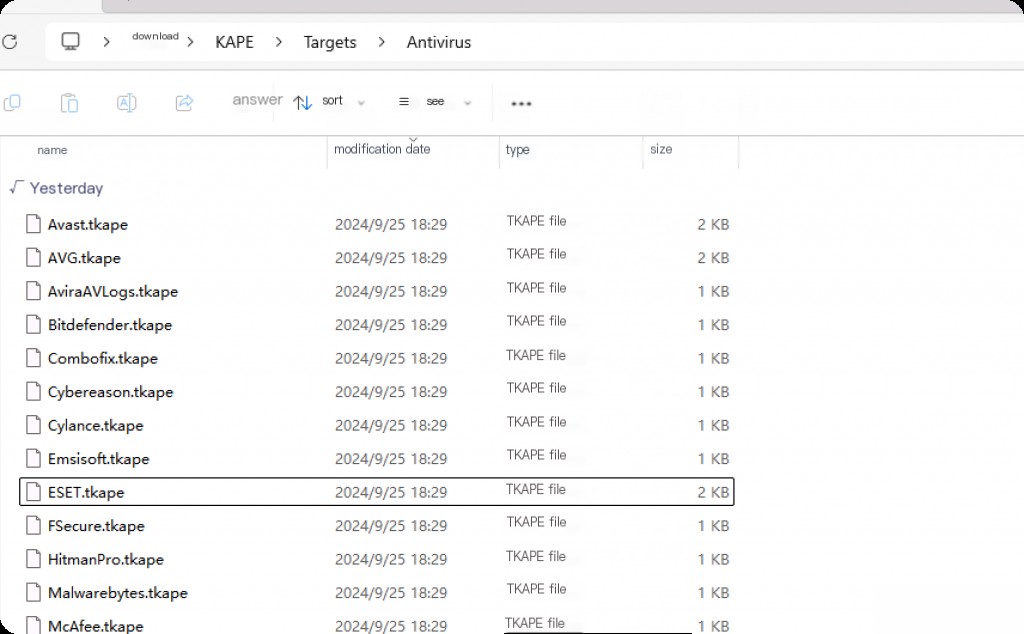
You can see target files for many different antivirus software vendors. This is very useful for forensics, for example, if we are acquiring data from a host running Avast antivirus software. During the collection phase, we will also select the Avast target as one of our targets to acquire relevant logs and files related to Avast antivirus software. Note that the file extension is TKAPE, representing Target KAPE.
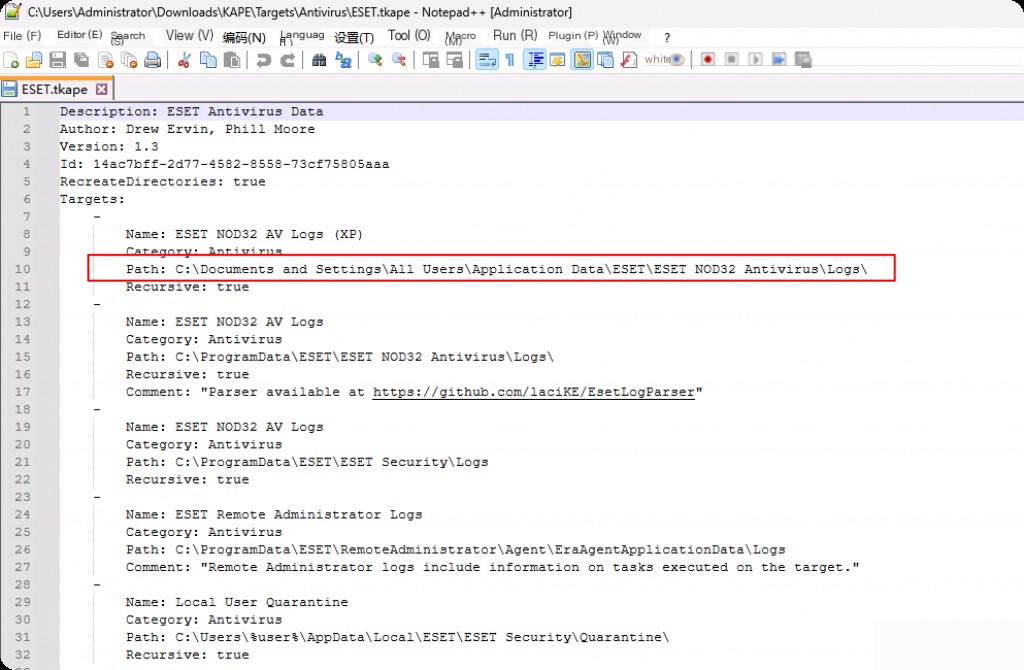
We can see that it specifies some common locations where Avast stores data. Therefore, when we run KAPE and designate Avast as one of the targets, KAPE will collect data through the above paths. Similarly, the browser category will contain targets for different browsers, and the log targets will contain paths for logs such as Apache, IIS, Nginx, etc.
The main target directories are Windows and Composite directories. Windows targets will contain many different targets for Windows forensic artifacts such as amcache, prefetch, etc.
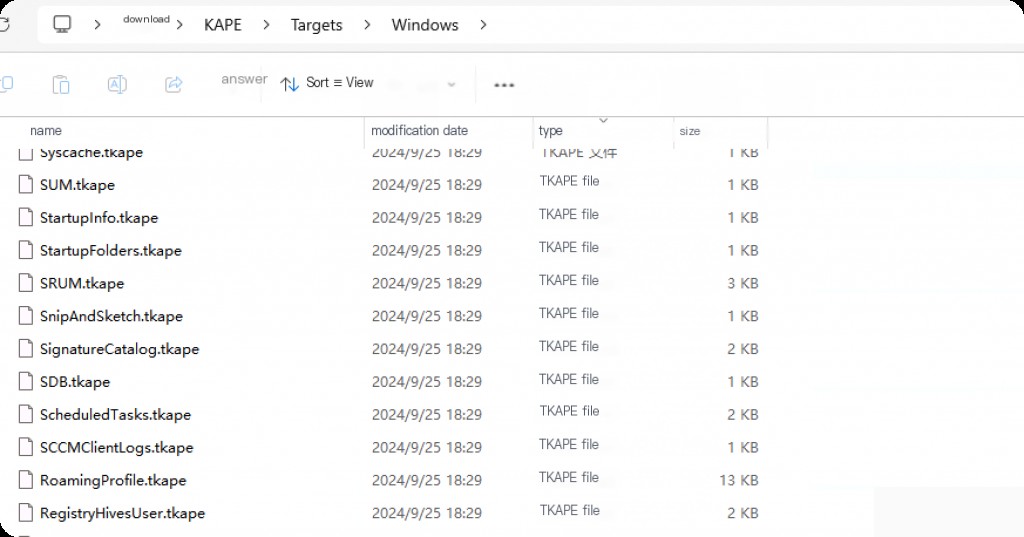
It is convenient when we want to acquire specific types of data, for example, if we only want event logs related to RDP, we will select the EventLogs-RDP target. Another important target category is called Composite. These targets are configured to collect most of the important forensic artifacts across the entire Windows system, not just specific artifacts. For example, SANS categorization and KAPE categorization are widely used because they collect almost all important types of artifacts needed for incident response.
KAPE Target File Structure
Understanding KAPE’s target structure by analyzing the SANS Target file.
Description: SANS Triage Collection
Author: Mark Hallman
Version: 1.4
Id: 1bfbd59d-6c58-4eeb-9da7-1d9612b79964
RecreateDirectories: true
Targets:
-
Name: Antivirus
Category: Antivirus
Path: Antivirus.tkape
-
Name: CloudStorage_Metadata
Category: Apps
Path: CloudStorage_Metadata.tkape
-
Name: CombinedLogs
Category: WindowsLogs
Path: CombinedLogs.tkape
-
Name: GroupPolicy
Category: GroupPolicy
Path: GroupPolicy.tkape
As seen in the composite target file, no data source paths or locations are specified, but other target files are specified, which contain the actual location paths of relevant artifacts. This means that composite targets consist of all other individual target files we briefly explored earlier. It is equivalent to customizing target rules or modifying existing rules as needed.
We can use any target and its parameters to collect the type of acquisition we want. For example, there is a target for acquiring “browser” related data, which will collect data related to browser analysis. The SANS Institute has created a target module that acquires SANS recommended artifacts and data.
Using KAPE for Target Acquisition
The structure of KAPE and how to collect data have been analyzed above. In the main KAPE directory, we see 2 .exe files, one named “kape.exe” and the other “gkape.exe”. Here we use gkape (GUI version).
Note: Run the tool as an administrator.
After opening, the main interface of KAPE is empty. Enable the “Use Targets” option to start acquiring data.
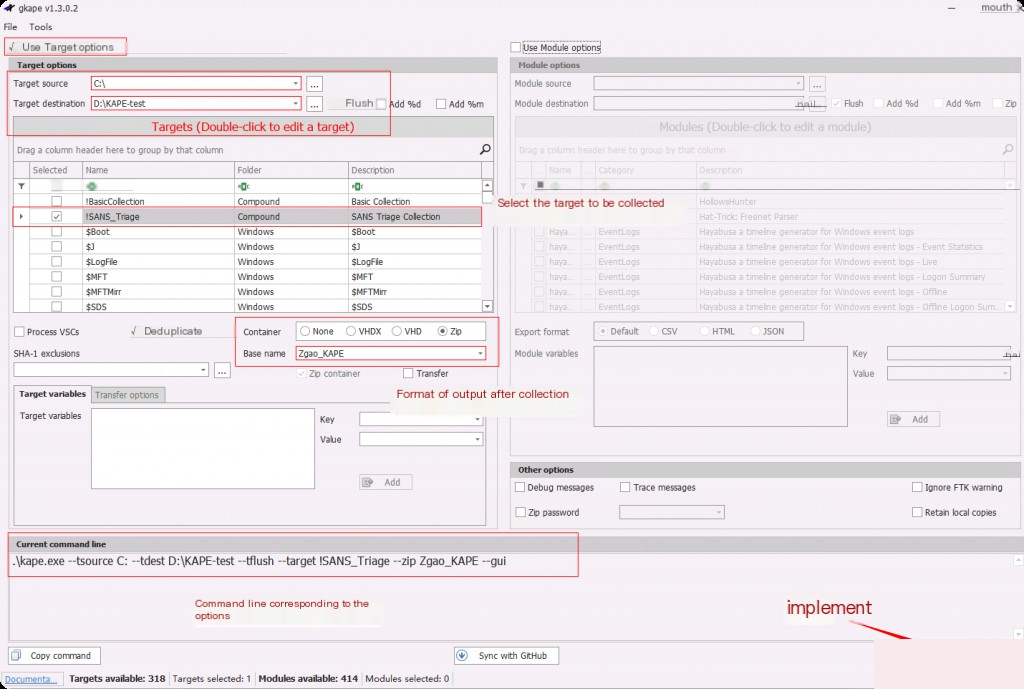
We will see a command prompt open and KAPE collecting data. The GUI KAPE only provides an easy-to-use interface, while the backend actually calls the CLI command line.
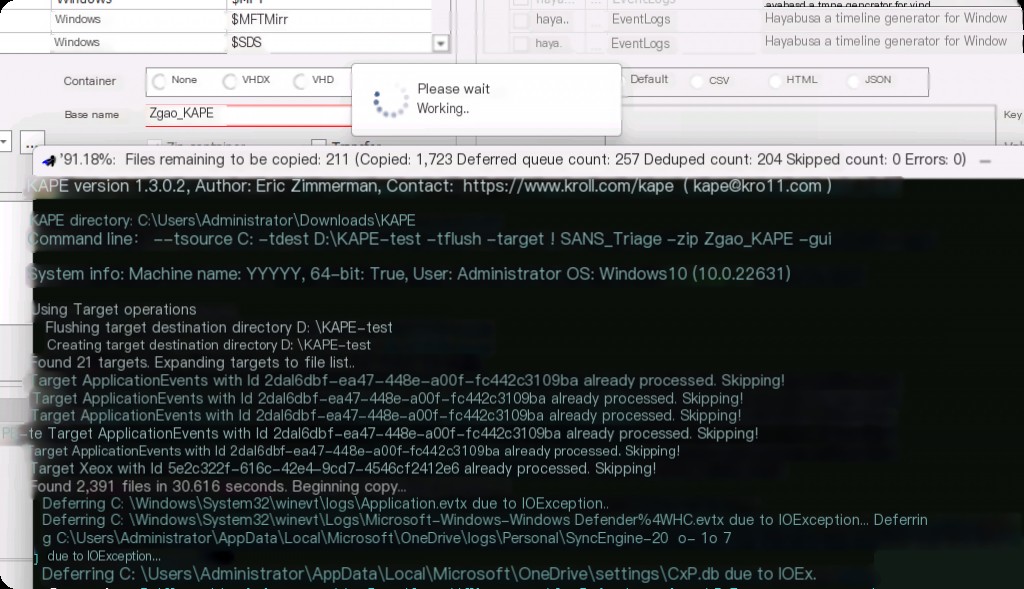
Forensic data source acquisition will take some time.
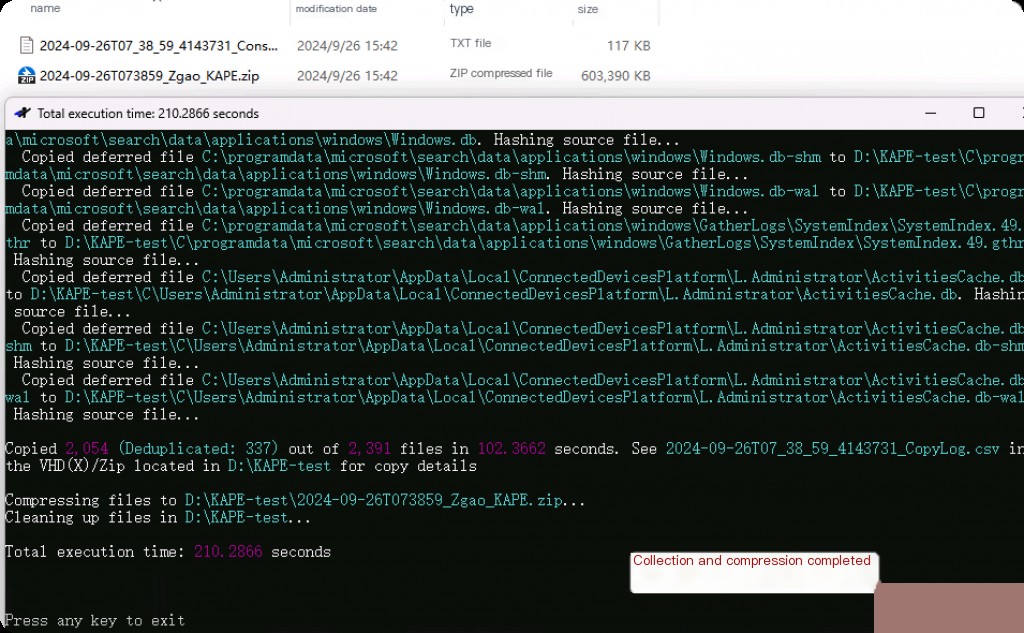
Preview the compressed package, and you can see that KAPE has collected almost all the data needed for forensics. The main data is located under the “C” directory.
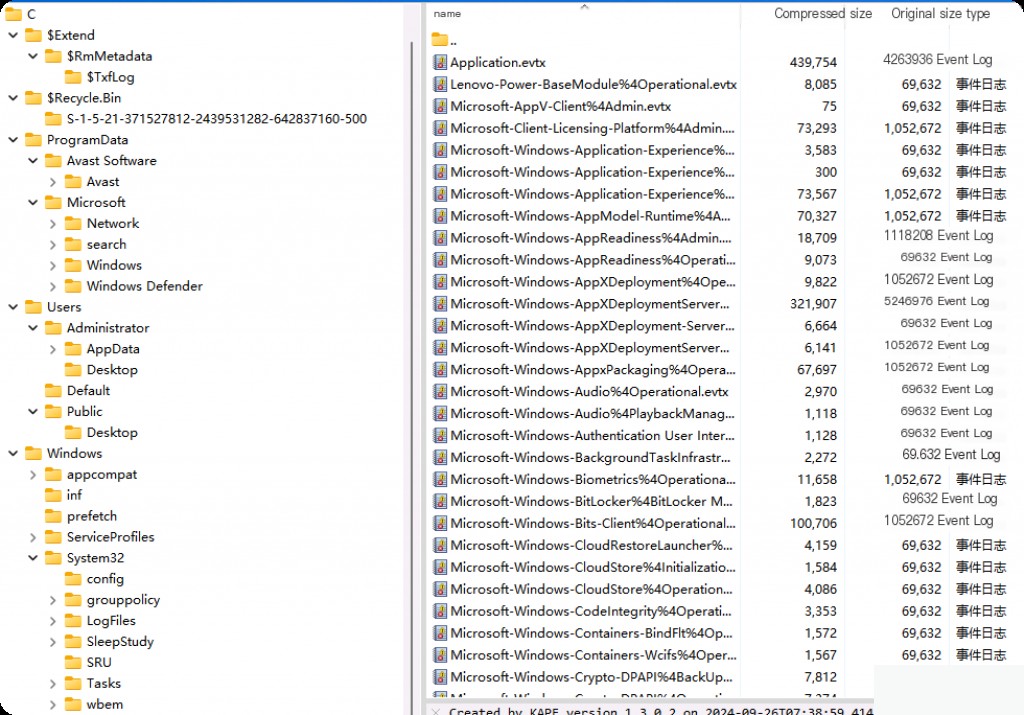
Although we can achieve similar things with FTK Imager, using KAPE to automatically collect hundreds of important data sources and artifacts based on our targets, rather than imaging the entire disk, significantly enhances our efficiency in emergency response. KAPE can complete the acquisition in less than 5 minutes and includes various files and artifacts needed for forensics.
KAPE Categorization and Analysis Modules
Like targets, modules are also defined using simple attributes and are used to run programs. These programs can target anything, including files collected through the target function, and what other programs are needed to further process the collected data during the real-time response process. It can be simply understood as the analysis and processing of source data.
For example, after collecting Jumplist, tools like JLECmd can be used to further parse the contents of the jump list and save it to CSV. If you want to collect the output of netstat or ipconfig, you can also do so. Each of these options will be included in its own module and then grouped together based on commonality between modules.
Using the
Windows_schtasks.mkapescheduled task module, it will query the scheduled tasks on the system and automatically save the results in a CSV file. This is accomplished by utilizing the "schtasks.exe" utility in Windows along with other necessary parameters. We don't need to manually run the command; once configured, KAPE will run it automatically.EZTools Directory
This directory contains mkape configuration files that instruct KAPE on how to use Eric Zimmerman tools to parse many Windows artifacts. EZTools or Eric Zimmerman tools are excellent forensic tools capable of parsing almost all Windows artifacts.
bin Directory
This directory contains all the Eric Zimmerman tools themselves, which are used by modules like EZTools or amcache.
These tools will parse most valuable artifacts, but we can also add our own applications to the bin directory and then create an mkape file for them.
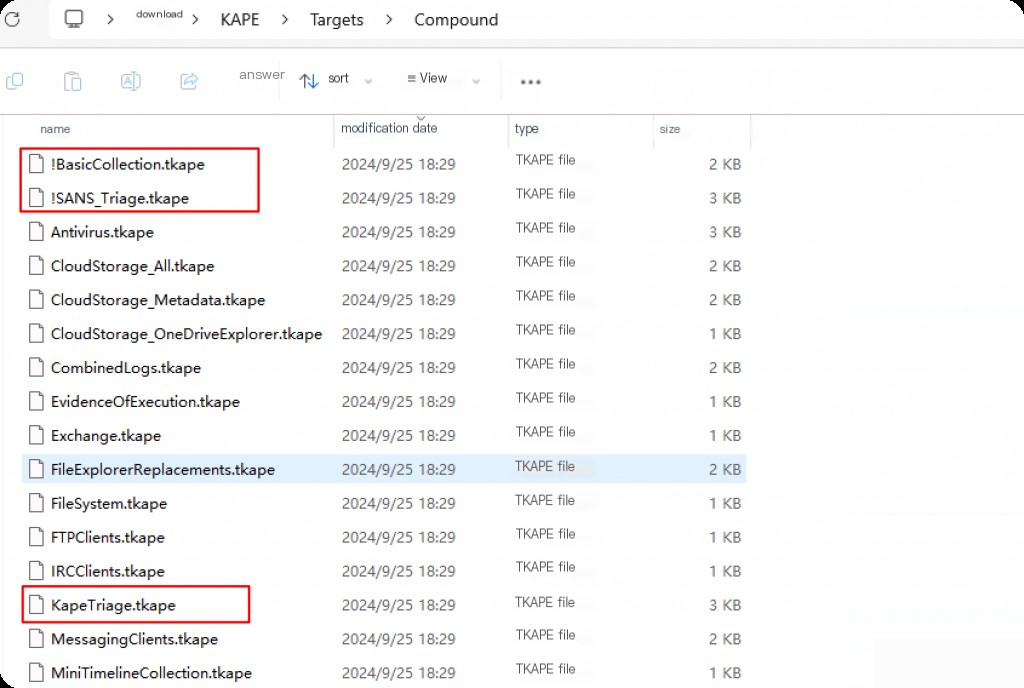
Compound Modules
Just like in targets, compound modules exist where we can leverage multiple other modules simultaneously. Access the "Compound" directory and read the mkape file of the "!EZParser" module, which utilizes all the mkape files from the EZTools directory mentioned above.
You can see it references mkape files named after EZtools, which can be found in the EZTools directory. Modules can be executed along with target acquisition, meaning that while collecting artifacts, they will also be categorized and parsed by the selected modules.
KAPE Automatically Collects and Parses Artifacts
Modules can be executed along with target acquisition, meaning that while collecting artifacts, they will also be categorized and parsed by the selected modules. The module target is where we want to store the categorized results.
The "module source" is the directory containing the files to be processed. If data has already been acquired, you can select a directory as the module source, and the selected modules will process the files in that path.
However, what we want to do is dynamically acquire and parse categorized data. Since we haven't acquired data yet, we will leave the module source empty. KAPE will automatically set the module source to the target destination, meaning that after acquisition, the data will be stored there, and KAPE will automatically process the files.
Click "OK" in the pop-up window. If you deselect the refresh option in the target or module target path, this prompt will not appear. Then, the process is the same as the one collected above.
Now we can directly view the results parsed by the forensic tools without manually parsing the artifacts. Emergency efficiency is increased by dozens of times.


