Linux System Memory Dump
LiME is a tool specifically designed for the Linux operating system to create a secure copy of the system RAM. It works as a kernel module and can export the memory contents to disk files in various formats, such as raw and lime formats.
LiME Memory Dump
LiME is used for analysis and security investigations, collecting data from system memory. This includes valuable information about running system processes, network connections, user sessions, and even potential malware. LiME allows for retrospective analysis of events that occurred during system shutdown or activity by creating a complete and unaltered data copy.
https://github.com/504ensicsLabs/LiME
root@VM-24-5-ubuntu:~/tools# git clone https://github.com/504ensicsLabs/LiME.git Cloning into 'LiME'... remote: Enumerating objects: 386, done. remote: Counting objects: 100% (37/37), done. remote: Compressing objects: 100% (23/23), done. remote: Total 386 (delta 18), reused 28 (delta 14), pack-reused 349 Receiving objects: 100% (386/386), 1.62 MiB | 7.33 MiB/s, done. Resolving deltas: 100% (207/207), done. root@VM-24-5-ubuntu:~/tools# cd LiME/src/ root@VM-24-5-ubuntu:~/tools/LiME/src# ls deflate.c disk.c hash.c lime.h main.c Makefile Makefile.sample tcp.c root@VM-24-5-ubuntu:~/tools/LiME/src# make make -C /lib/modules/5.15.0-107-generic/build M="/root/tools/LiME-master/src" modules make[1]: Entering directory '/usr/src/linux-headers-5.15.0-107-generic' CC [M] /root/tools/LiME-master/src/tcp.o CC [M] /root/tools/LiME-master/src/disk.o CC [M] /root/tools/LiME-master/src/main.o CC [M] /root/tools/LiME-master/src/hash.o CC [M] /root/tools/LiME-master/src/deflate.o LD [M] /root/tools/LiME-master/src/lime.o MODPOST /root/tools/LiME-master/src/Module.symvers CC [M] /root/tools/LiME-master/src/lime.mod.o LD [M] /root/tools/LiME-master/src/lime.ko BTF [M] /root/tools/LiME-master/src/lime.ko Skipping BTF generation for /root/tools/LiME-master/src/lime.ko due to unavailability of vmlinux make[1]: Leaving directory '/usr/src/linux-headers-5.15.0-107-generic' strip --strip-unneeded lime.ko mv lime.ko lime-5.15.0-107-generic.ko
The ko module with the kernel version number is generated, indicating that LiME has been compiled and installed.
insmod lime-5.15.0-107-generic.ko "path=/tmp/ubuntu.mem format=lime"
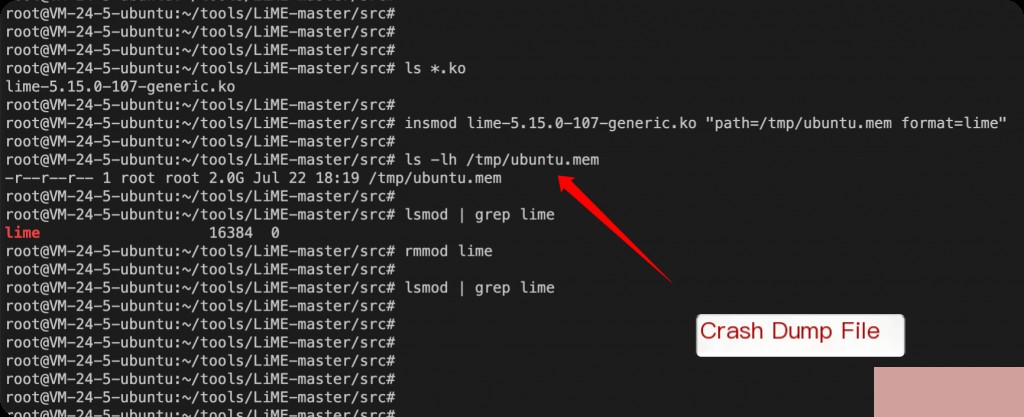
Load the ko kernel module to perform the memory dump operation. Remember to remove the ko module with rmmod after each dump; otherwise, you will encounter errors during subsequent executions.
AVML Memory Dump (Recommended)
AVML is a portable volatile memory acquisition tool for Linux, written in Rust, and designed to be deployed as a static binary. AVML can be used to acquire memory without prior knowledge of the target operating system distribution or kernel. No compilation or fingerprinting is required on the target. Its memory sources include:
- /dev/crash
- /proc/kcore
- /dev/mem
If no memory source is specified on the command line, AVML will traverse the memory sources to find an available source.
This tool is very convenient as it is provided as a single binary file. Compared to LiME, its advantage is that it does not rely on or create kernel objects. We only need to run the binary and specify the output path to acquire the memory image.
https://github.com/microsoft/avml

[root@VM-4-7-centos tmp]# ./avml -h
A portable volatile memory acquisition tool
Usage: avml [options]
Parameters:
The filename to write on the local system
Options:
--compress
Compress using Snappy
--source
Specify input source [possible values: /dev/crash, /dev/mem, /proc/kcore]
--max-disk-usage
Specify the maximum estimated disk usage (in MB)
--max-disk-usage-percentage
Specify the maximum estimated disk usage percentage to stay below
--url
Upload via HTTP PUT after acquisition
--delete
Delete after successful upload
--sas-url
Upload via Azure Blob Storage after acquisition
--sas-block-size
Specify the maximum block size in MiB
--sas-block-concurrency
Specify the Blob upload concurrency [default: 10]
-h, --help
Print help information (use '--help' for more details)
-V, --version
Print version information
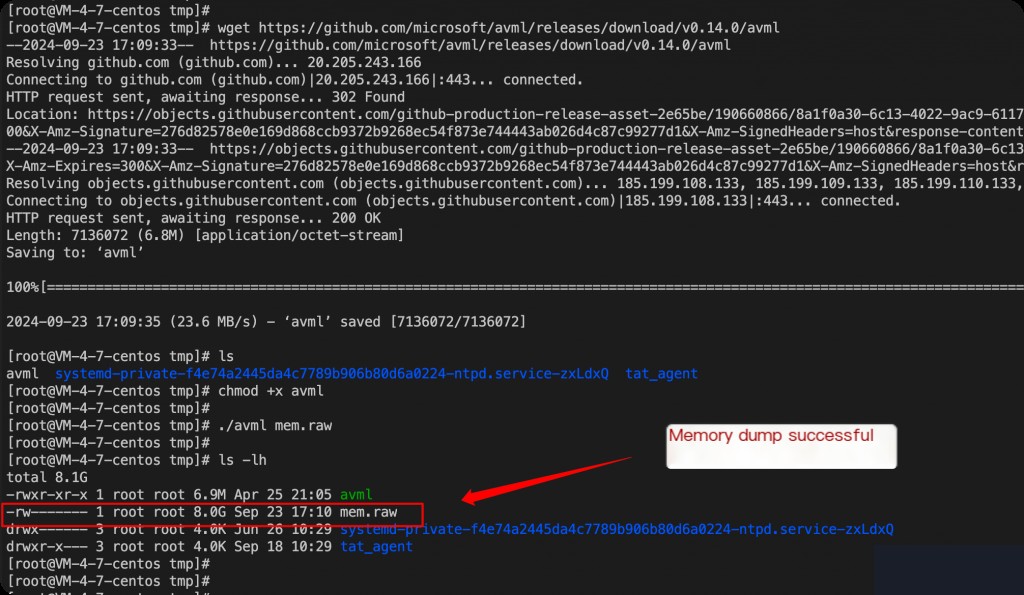
Compressed Transfer of Memory Dumps
The raw memory dump file is the same size as the current system memory. The file size is too large and needs to be compressed for transfer.
root@VM-24-5-ubuntu:/tmp# tar czvf ubuntu.mem.tgz ubuntu.mem ubuntu.mem root@VM-24-5-ubuntu:/tmp# ls -lh ubuntu.mem* -r--r--r-- 1 root root 2.0G Jul 22 18:19 ubuntu.mem -rw-r--r-- 1 root root 550M Jul 22 18:35 ubuntu.mem.tgz
Linux Process Memory Dump
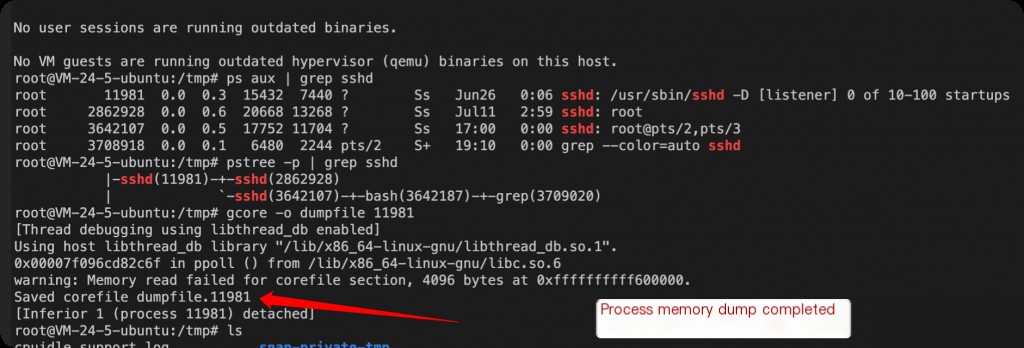
gcore Dump Specified Process Memory
gcore is a tool for generating core files of processes, and it is part of GDB. Using this command, you can create a memory dump file of a specified process, which can then be analyzed with GDB or other tools.
Install gdb
apt install gdb -y
Usage
gcore -o
Windows Memory Dump using LiME tool
Windows memory forensics involves a detailed examination of the system’s physical memory (RAM), which is crucial for understanding the current state of the computer or actions performed in the past. In cases of system crashes, malware attacks, or other security breaches, the data stored in RAM may contain important information.
Dumplt Memory Dump
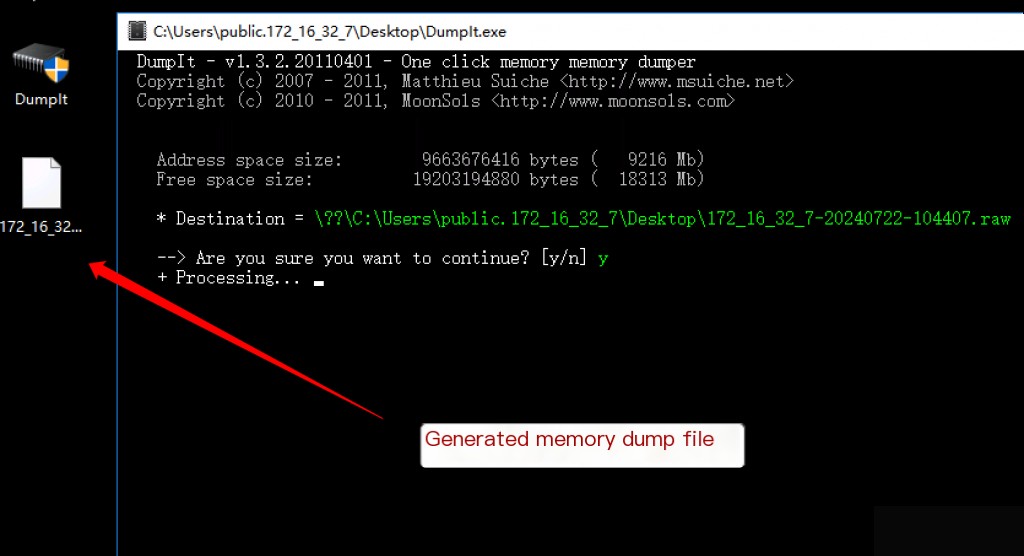
Memory dumping on Windows is very simple. Running Dumplt as an administrator allows you to directly dump the memory of Windows.
FTK Memory Dump
AccessData FTK Imager is an industry-standard software product that provides a powerful set of tools for digital forensic professionals. It allows users to create, examine, and analyze data images from various media and file systems, including hard drives, USBs, CDs/DVDs, SANs, RAIDs, Jaz/Zip disks, and even RAM. Images created with FTK Imager allow for detailed examination of digital evidence while preserving its integrity.
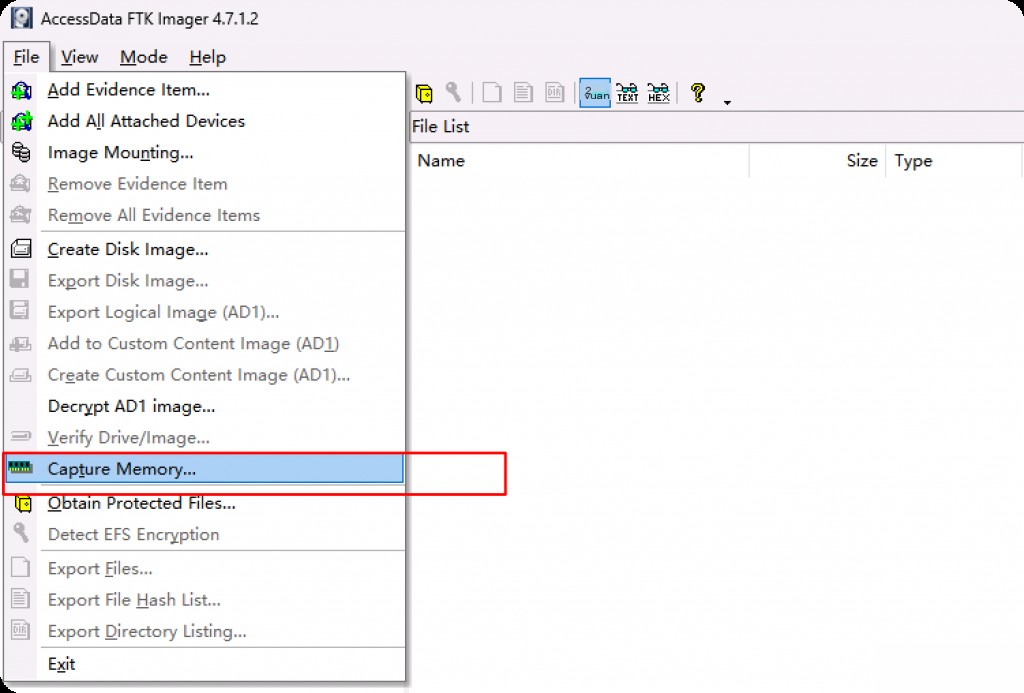
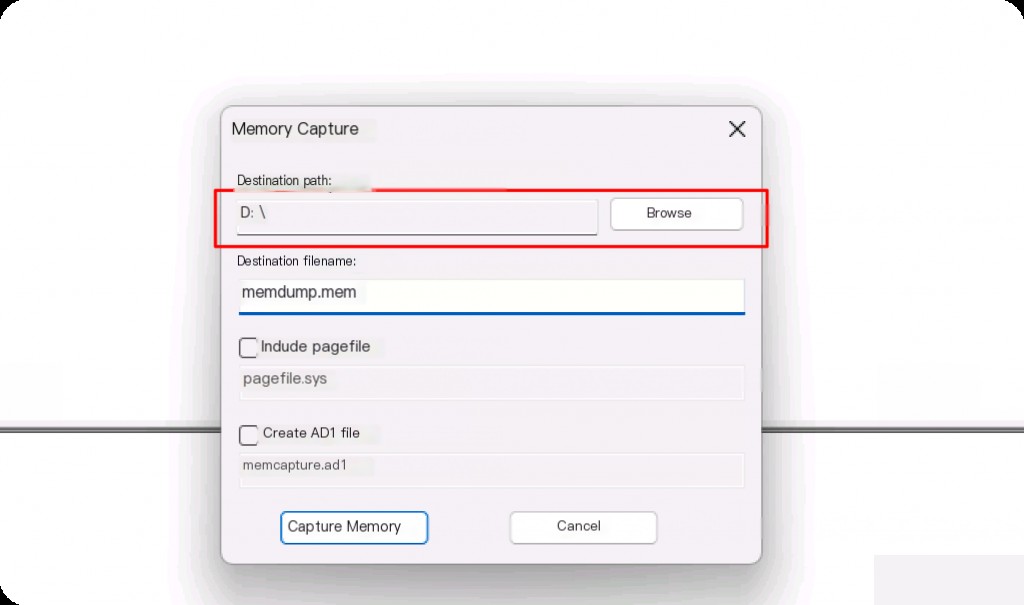
Then select the save path in the pop-up window.
Windows Process Memory Dump
Task Manager Dump Process Memory
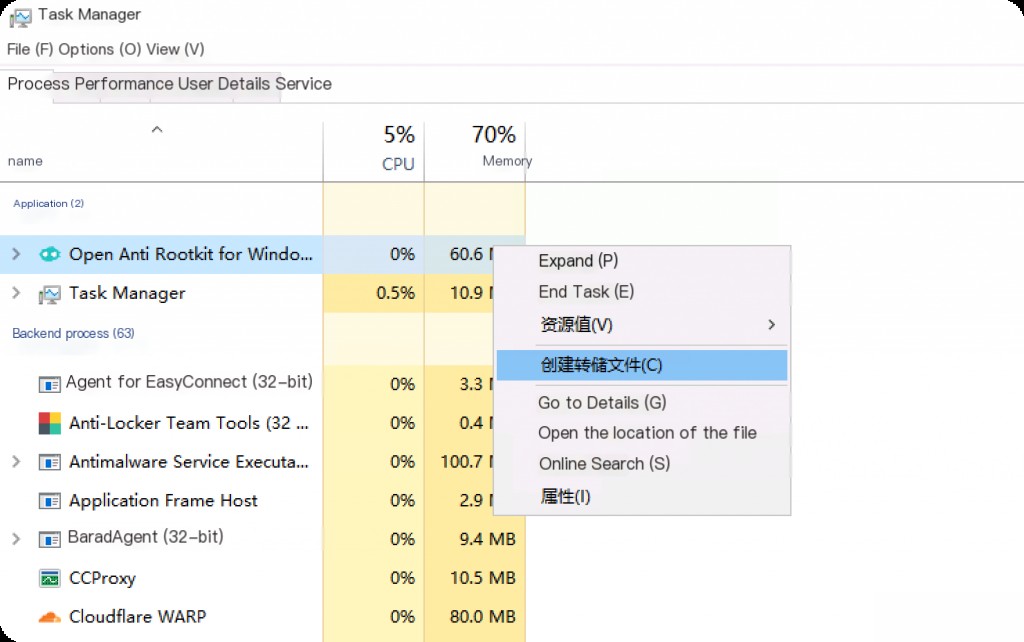
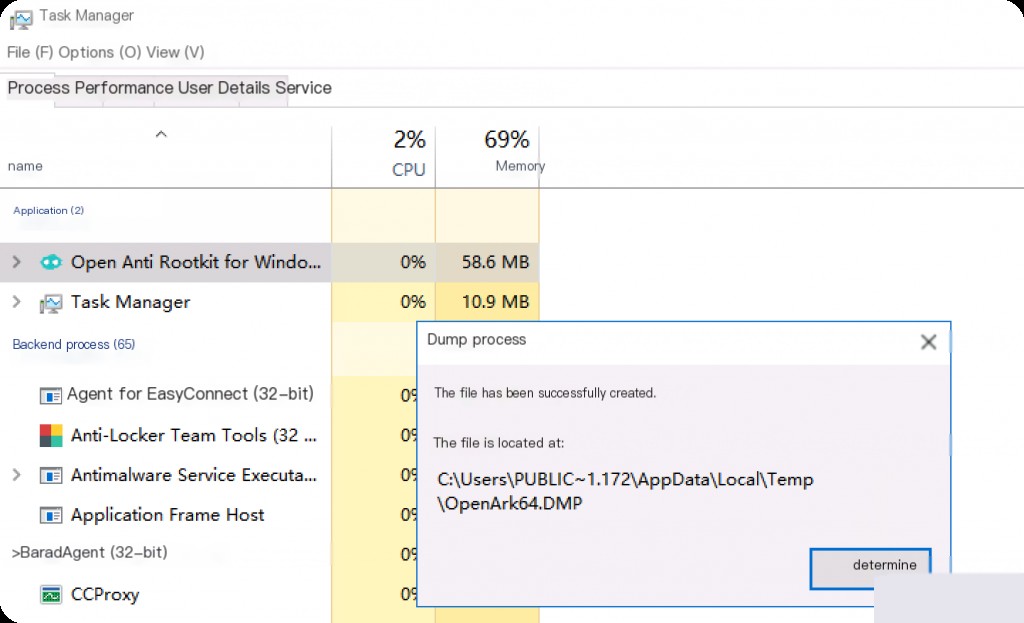
Dumping process memory is relatively simple and can be done directly using Task Manager to dump the memory of a specified process.
procdump Dump Process Memory
ProcDump is a lightweight command-line utility provided by Microsoft Sysinternals that offers various memory dump options, primarily designed for memory dumps of individual processes.
procdump -ma [Process ID or Name] [Output File Path]
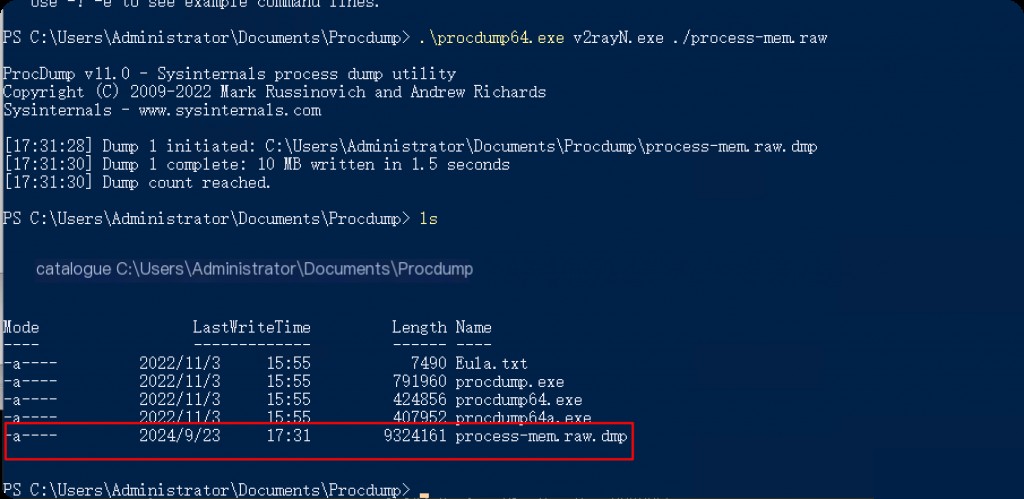
-ma parameter indicates creating a full dump file that includes all memory information.


