Windows endpoints were recently compromised. Thanks to our advanced EDR/IDS solution, we noticed this immediately. The alert has been escalated to Level 2 (Incident Responder) for further investigation. As our forensic analyst, you have obtained a memory dump of the infected host. You should continue the investigation.
Challenge Link
https://app.letsdefend.io/challenge/memory-analysis
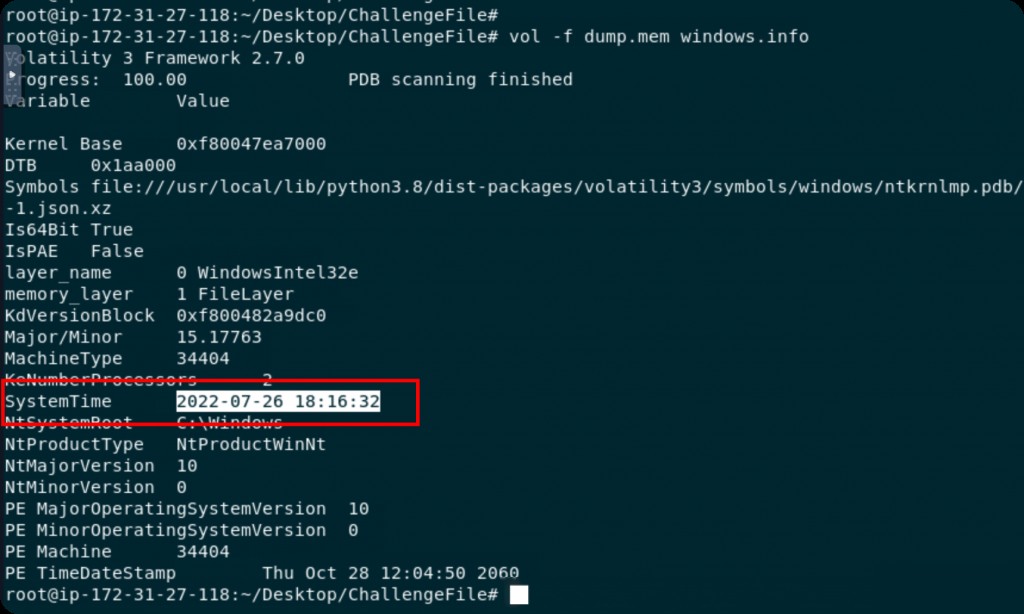
Date and Time of Memory Acquisition from the Infected Endpoint
This is the time when the memory dump was acquired.
vol -f dump.mem windows.info
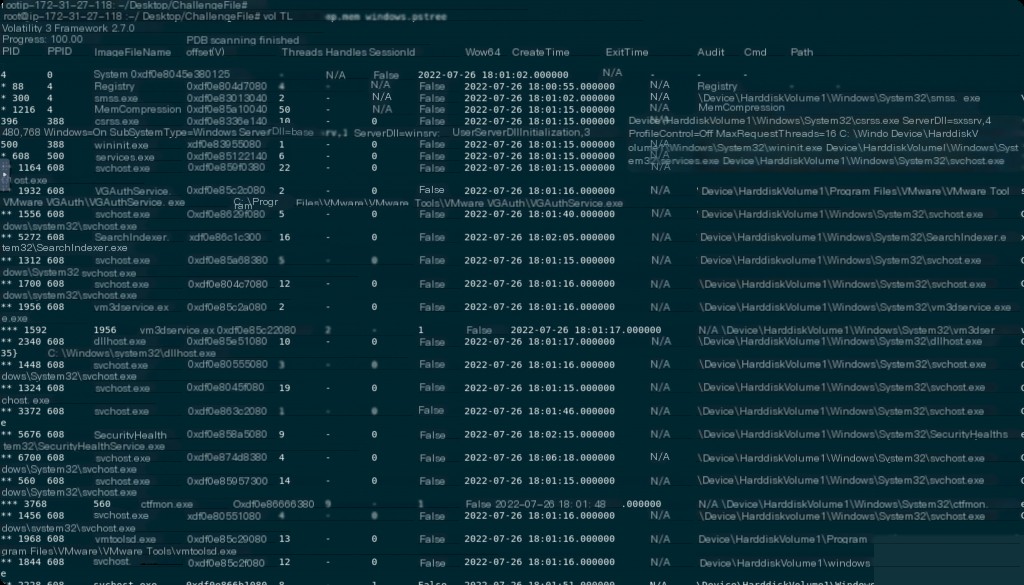
What are the suspicious processes running on the system?
In Windows, attackers can disguise malware executables by renaming them to legitimate Windows binary names (such as services.exe, svchosts.exe, lsass.exe, etc.).
Therefore, it is crucial to verify if a process has a legitimate parent process. For example, svchost.exe should always have services.exe as its parent process, and lsass.exe should have wininit.exe as its parent process.
vol -f dump.mem windows.pstree
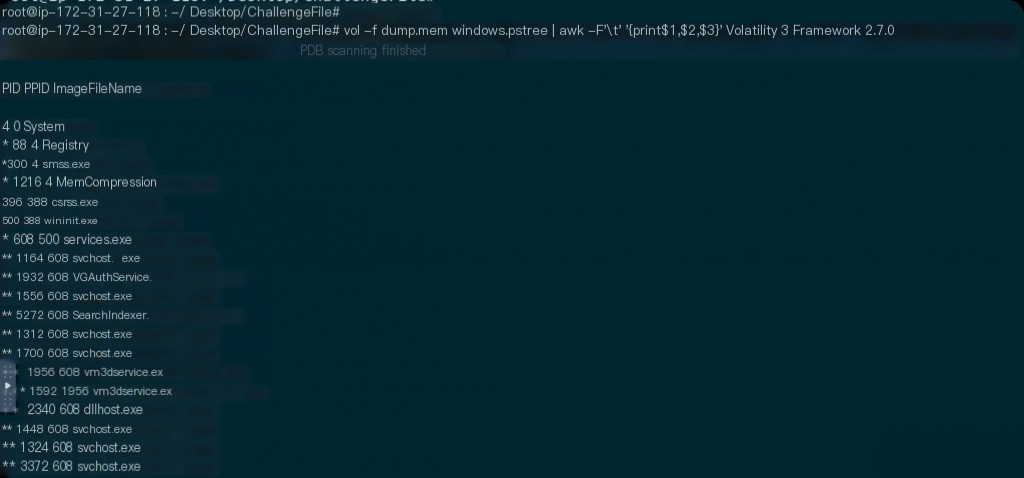
The displayed content is too much and inconvenient to view, and I am only concerned with the parent process information. We can use awk to filter it.
This looks much better, but it is not as intuitive as the pstree command in Linux systems. Let’s use sed to replace it.
vol -f dump.mem windows.pstree | awk -F'\t' '{print$1,$2,$3}' | sed 's/*/L---/g'
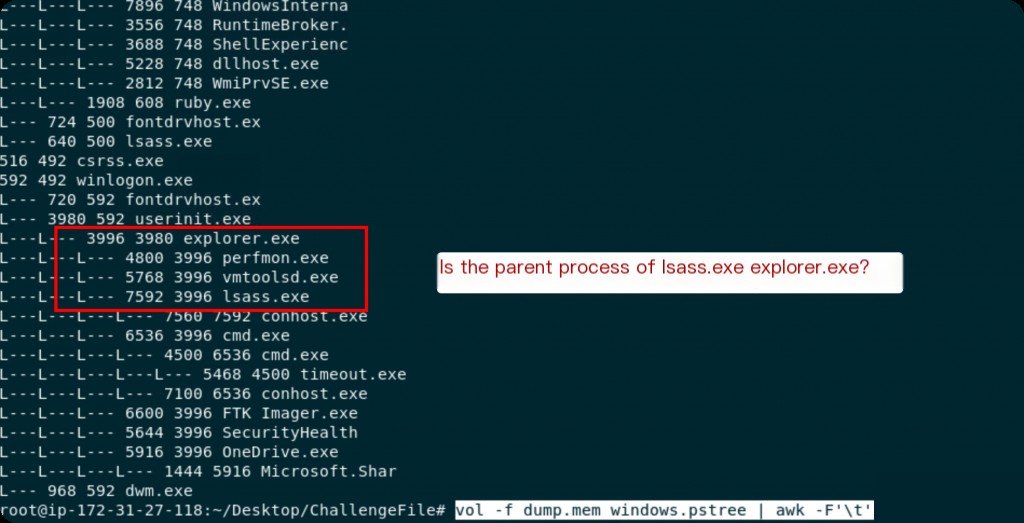
Now it looks much better. The pstree shows two running lsass.exe processes, one of which has wininit.exe as its parent process, which is normal, but the second lsass.exe having explorer.exe as its parent process is very suspicious.
What malicious tool did the attacker run on the system?
We already know that the lsass.exe process with pid 7592 is suspicious. Let’s dump it from memory.
vol -f dump.mem windows.pslist --pid 7592 --dump md5sum 7592.lsass.exe.0x2238edc0000.dmp
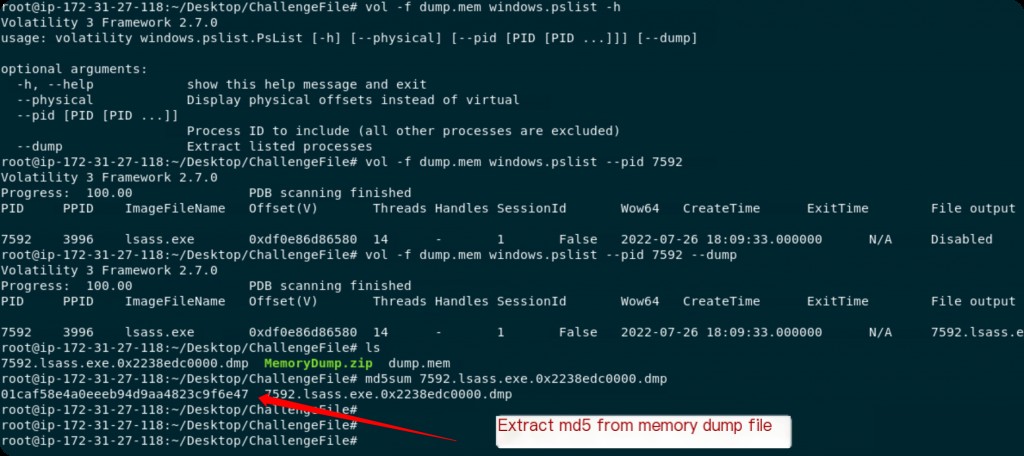
Extract the MD5 and search it on VT.
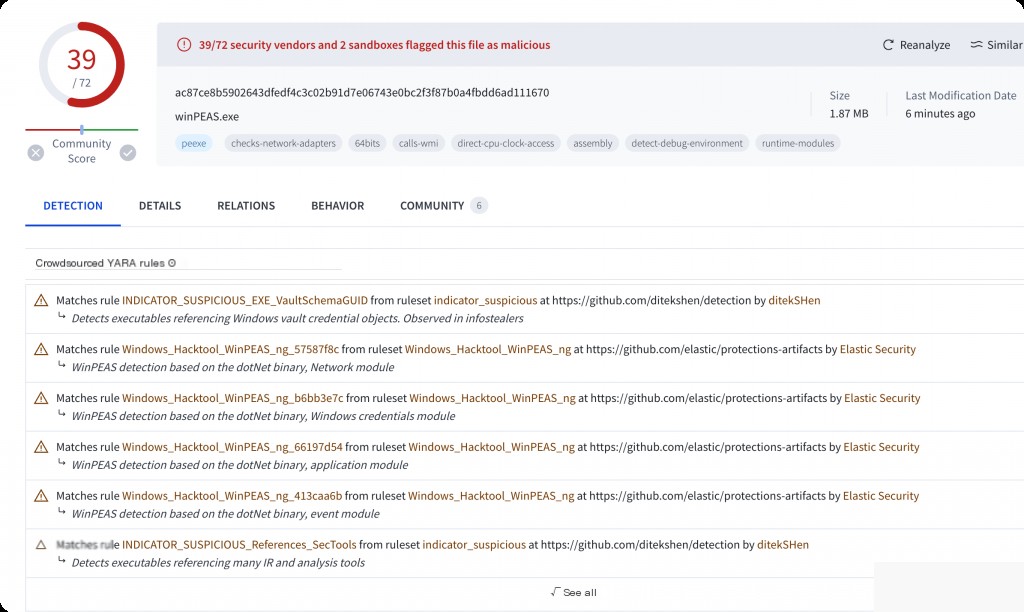
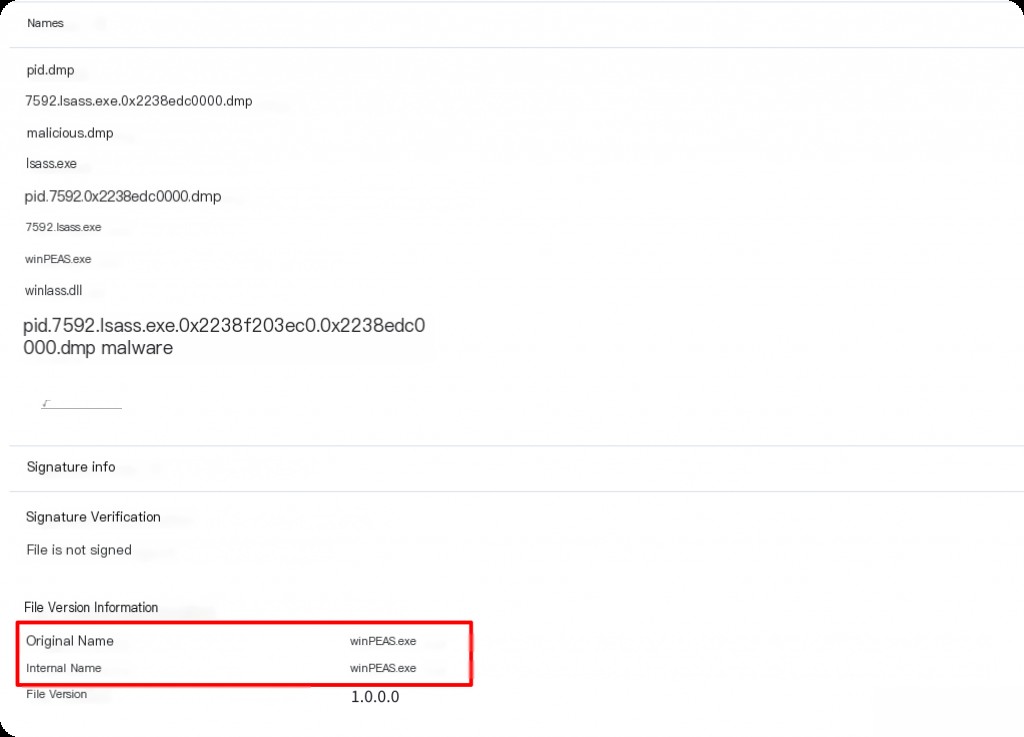
Which user account was compromised?
To view usernames and domains, you can use the windows.session plugin, which will display usernames and their associated processes.
vol -f dump.mem windows.sessions
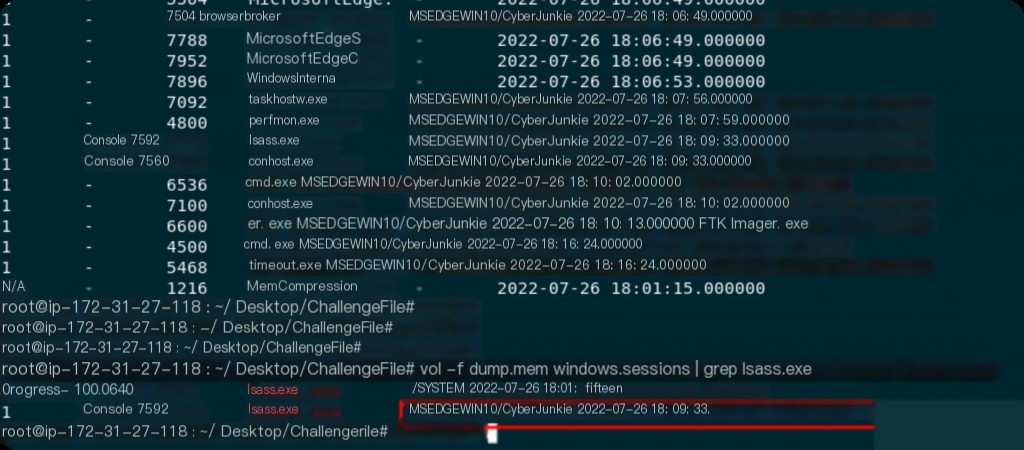
It is clear that the malicious lsass.exe is running under the MSEDGEWIN10/CyberJunkie user account.
What is the compromised user’s password?
Volatility has a hashdump plugin that works similarly to mimikatz. We can use it to dump hashes and then crack them with hashcat.
Copy the ntlm hash of the CyberJunkie user and crack it using hashcat on Kali.
hashcat -m 1000 cyberjunkie.hash /usr/share/wordlists/rockyou.txt --force
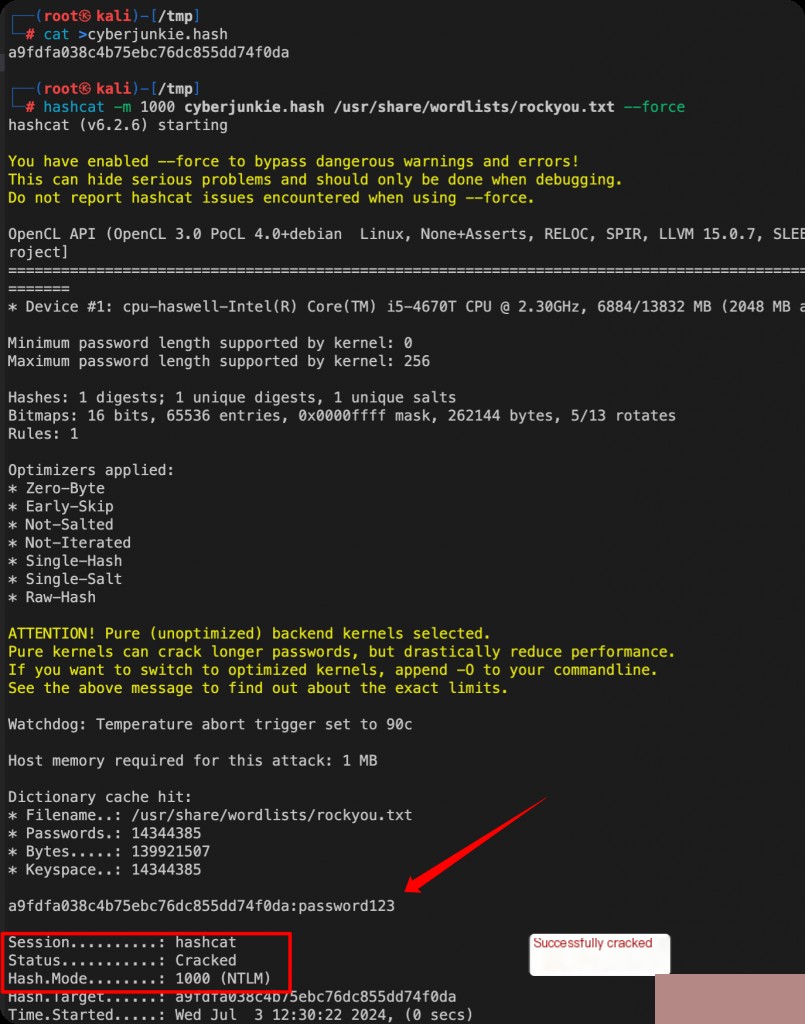
The password for the CyberJunkie user is password123.
Of course, you don’t necessarily have to use hashcat; you can also use online ntlm hash lookup services to crack it.


