Our friend became a victim of a suspicious cracking tool. But it seems that it did not go as planned, so investigate it to find any evidence.
Challenge Link
https://app.letsdefend.io/challenge/windows-memory-dump
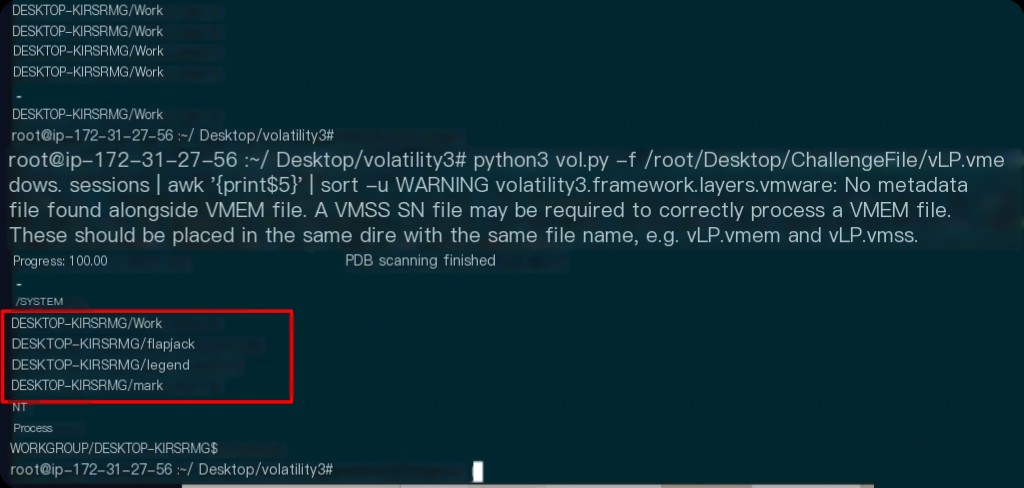
How many users are on this machine?
python3 vol.py -f /root/Desktop/ChallengeFile/vLP.vmem windows.hashdump
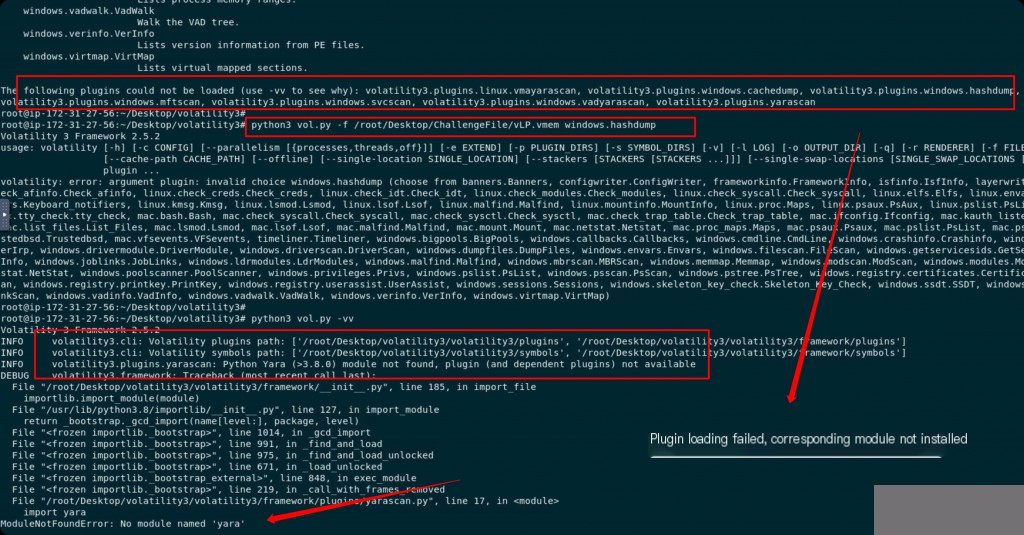
Initially tried to get the number of users on the machine through hashdump, but found that the plugin failed to load, so had to use other plugins.
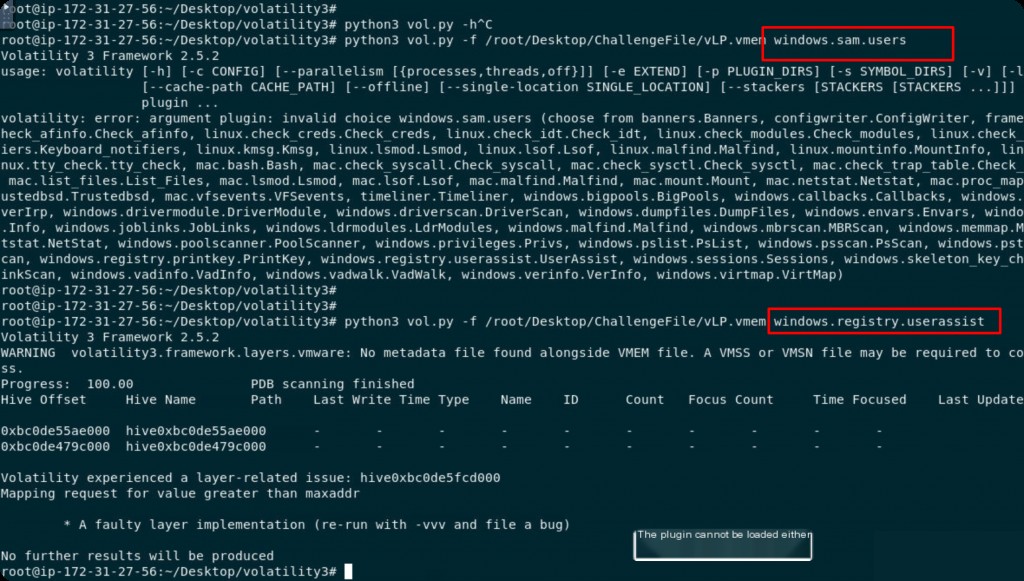
python3 vol.py -f /root/Desktop/ChallengeFile/vLP.vmem windows.sam.users python3 vol.py -f /root/Desktop/ChallengeFile/vLP.vmem windows.registry.userassist
python3 vol.py -f /root/Desktop/ChallengeFile/vLP.vmem windows.sessions | awk '{print$5}' | sort -u
Which user is infected?
According to the prompt, the victim is a suspicious cracking tool user, suspected of downloading malicious software. Match the files in the Downloads directory.
python3 vol.py -f /root/Desktop/ChallengeFile/vLP.vmem windows.filescan | grep Downloads
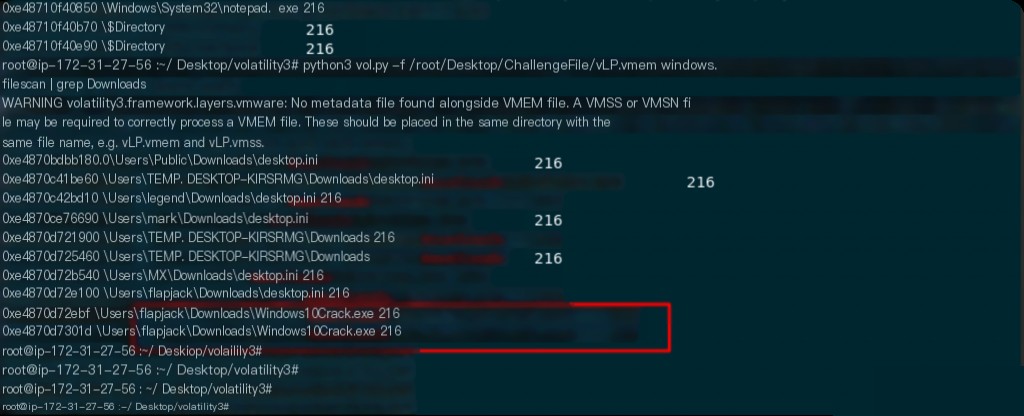
Which file implanted ransomware?
Windows10Crack.exe
What is the URL for downloading the ransomware?
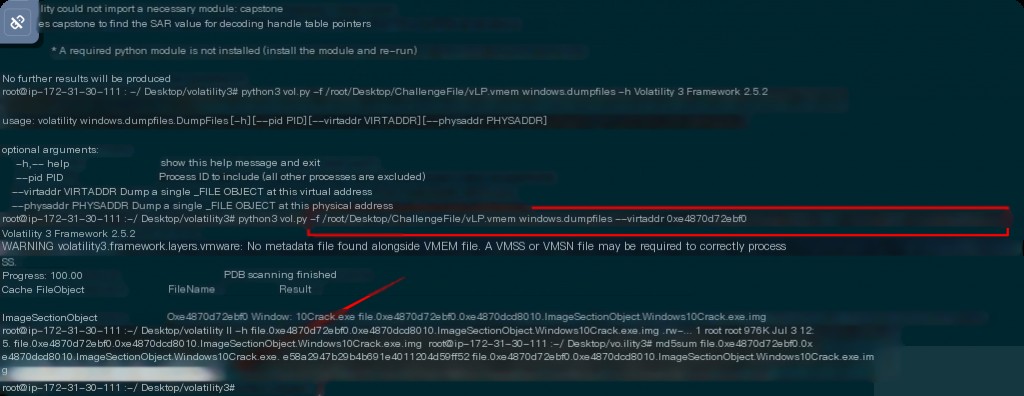
The hint requires reverse analysis of the exe, so first dump the scanned file from the previous filescan.
python3 vol.py -f /root/Desktop/ChallengeFile/vLP.vmem windows.dumpfiles --virtaddr 0xe4870d72ebf0 md5sum file.0xe4870d72ebf0.0xe4870dcd8010.ImageSectionObject.Windows10Crack.exe.img
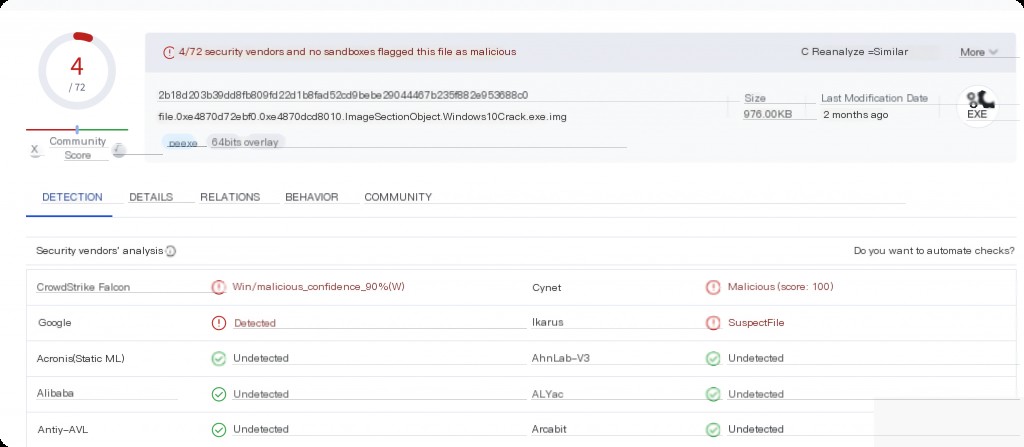
Match the MD5 on VT.
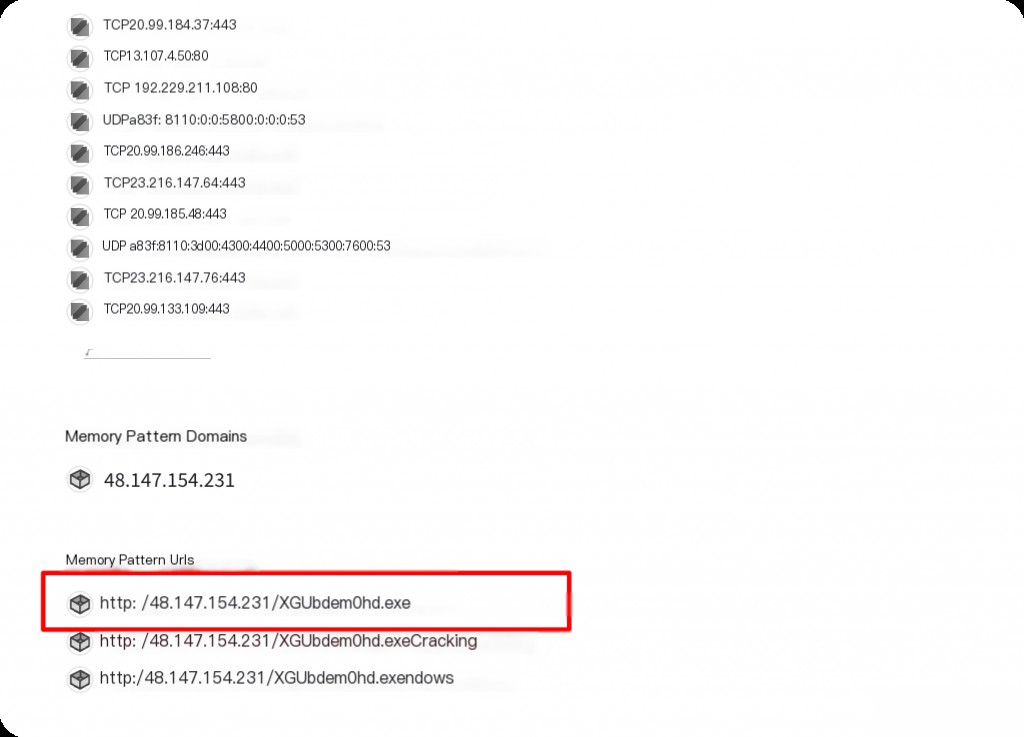
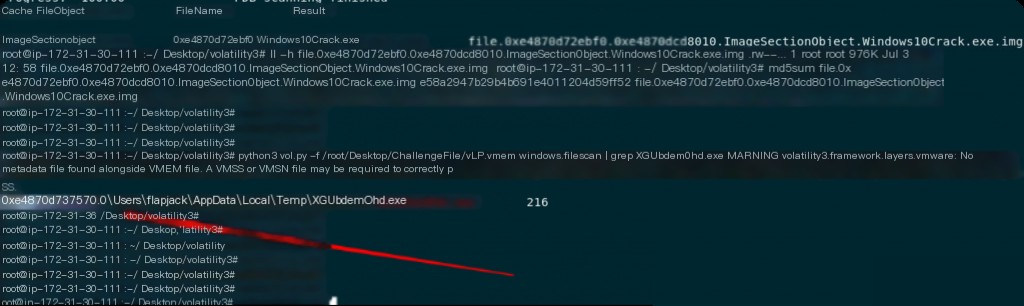
What is the virtual offset of the ransomware?
python3 vol.py -f /root/Desktop/ChallengeFile/vLP.vmem windows.filescan | grep XGUbdem0hd.exe
What is the main registry key modified by the ransomware?
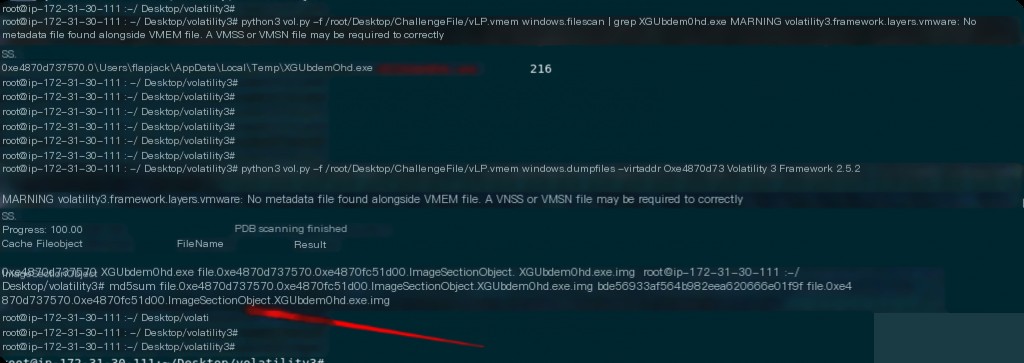
Dump XGUbdem0hd.exe again to get the MD5.
python3 vol.py -f /root/Desktop/ChallengeFile/vLP.vmem windows.dumpfiles --virtaddr 0xe4870d737570 md5sum file.0xe4870d737570.0xe4870fc51d00.ImageSectionObject.XGUbdem0hd.exe.img
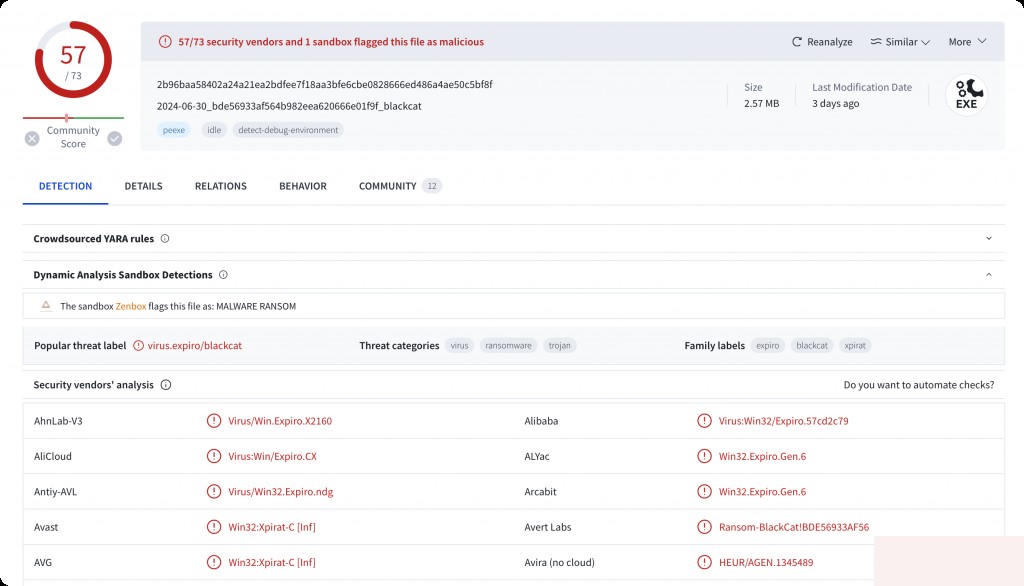
The previous file was a loader, so the VT detection rate was low. This one is the actual ransomware program, and the VT detection rate is much higher. It is identified as a ransomware program from the Blackcat family.
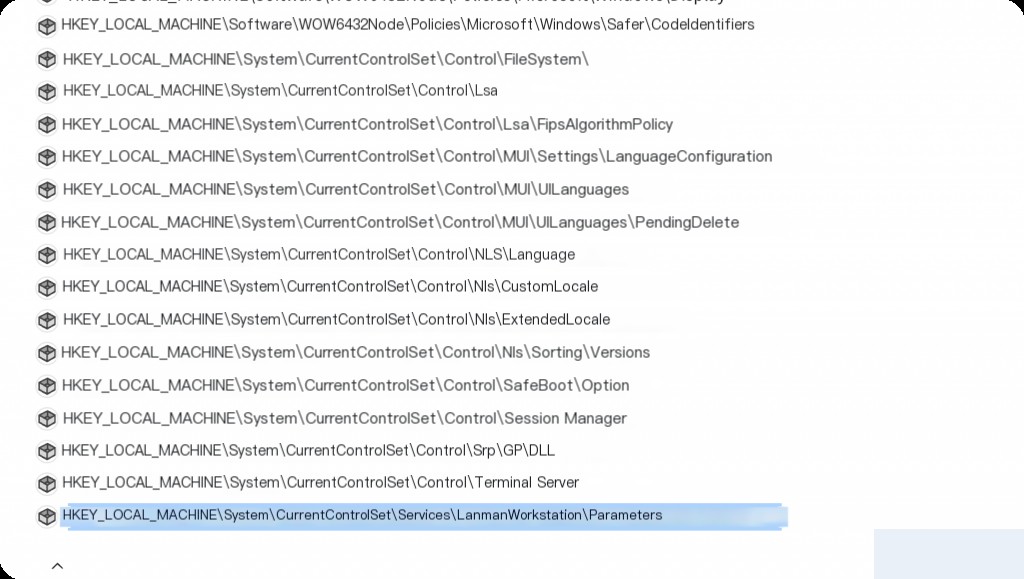
What are the credentials for AdminRecovery?
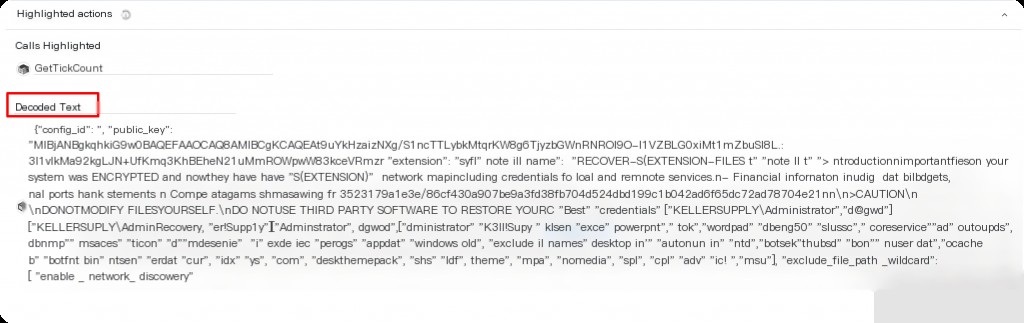
K3ller!$Supp1y


