Our organization has been targeted by a phishing campaign, and so far, three systems in our network have opened the phishing emails. We have collected quick triage images from one of the infected systems and provided them to you to identify the TTPs (Tactics, Techniques, and Procedures) used by the attacker. Identify the techniques and strategies used by the attacker so that our incident response team can respond and mitigate any further harm to the network.
Challenge Link
https://app.letsdefend.io/challenge/windows-forensics
Forensic Tools
ShellBags Explorer
ShellBags Explorer is a tool used to analyze ShellBags data structure information in Windows operating systems. ShellBags are items in the Windows Registry that record folder view settings and access history. ShellBags Explorer can provide the following information:
- Paths to folders accessed by the user.
- Timestamps of when these folders were accessed.
- Folder view settings (e.g., icon size, sorting order, etc.).
- Other metadata of the folders (e.g., creation time, modification time, etc.).
This tool is very useful in digital forensic analysis because even if files or folders are deleted, the information recorded in ShellBags may still be retained in the Registry, providing valuable historical access records.
ShellBags Explorer primarily analyzes the following two Registry Hive files:
- NTUSER.DAT:
- Location:
C:\Users\\NTUSER.DAT - Description: Each user account has an NTUSER.DAT file that contains the user’s profile information and Registry data. ShellBags data is stored in the NTUSER.DAT file to record the user’s folder view settings and access history.
- Location:
- USRCLASS.DAT:
- Windows 7/8/10:
C:\Users\\AppData\Local\Microsoft\Windows\UsrClass.dat - Windows XP:
C:\Documents and Settings\\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat - Description: The USRCLASS.DAT file also contains Registry data related to the user profile, particularly those involving user interface and folder settings. Part of the ShellBags data is also stored in this file.
- Windows 7/8/10:
AccessData FTK Imager
FTK supports multiple ways to read the content of image files.
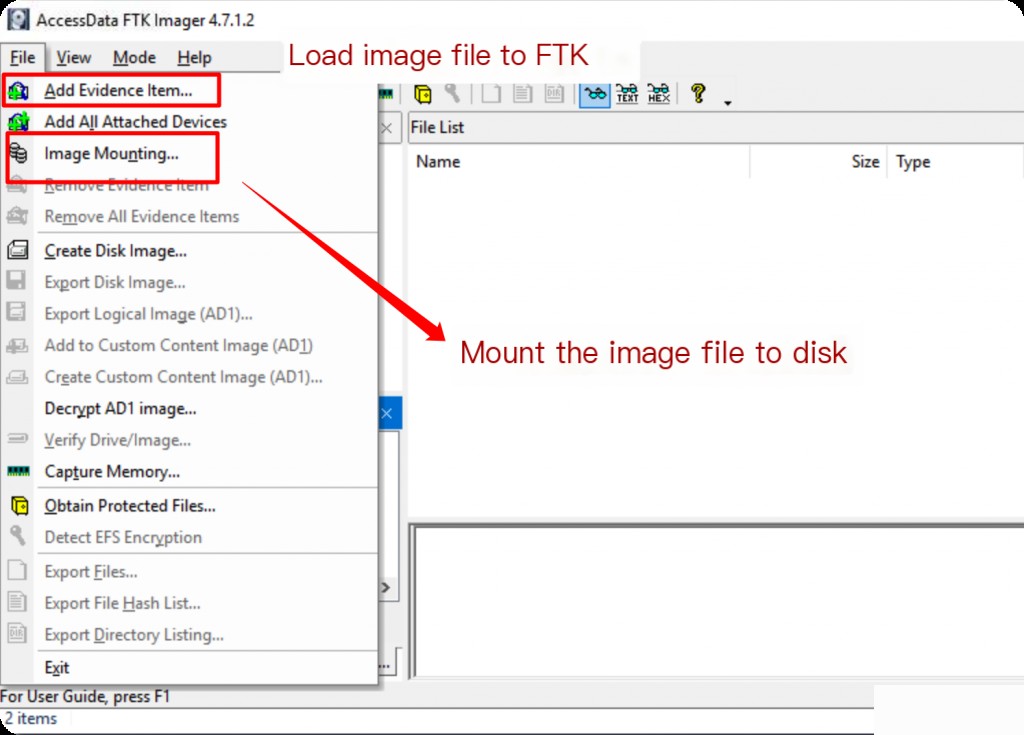
Select Add Evidence Item —> Image File to specify the local image file.
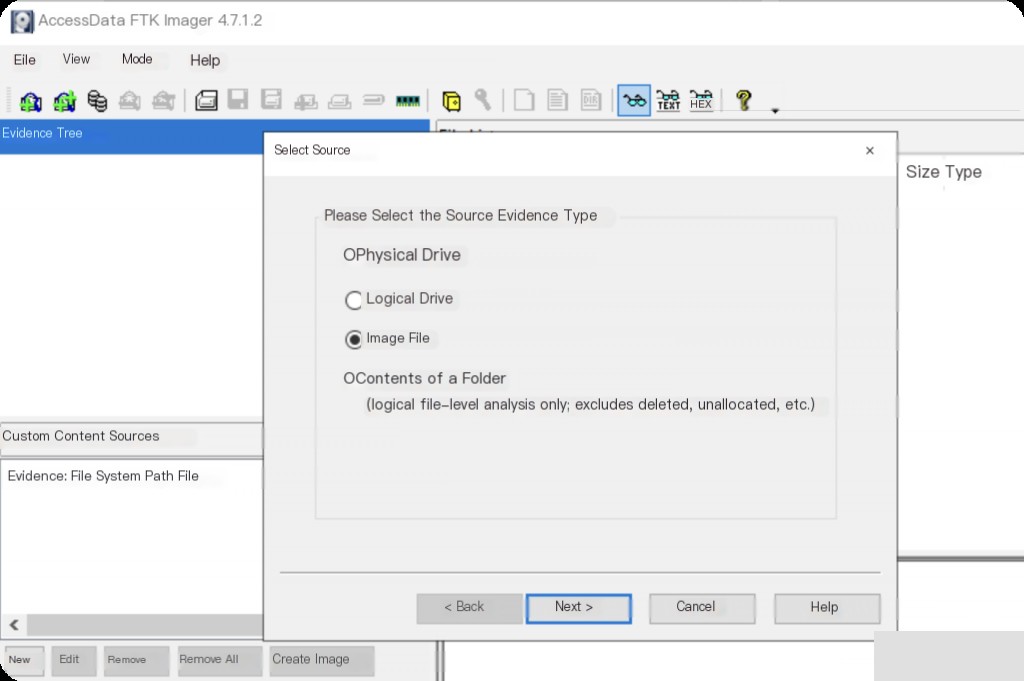
The second method is to mount the image to the disk using FTK. ( This article is based on this method for image analysis )
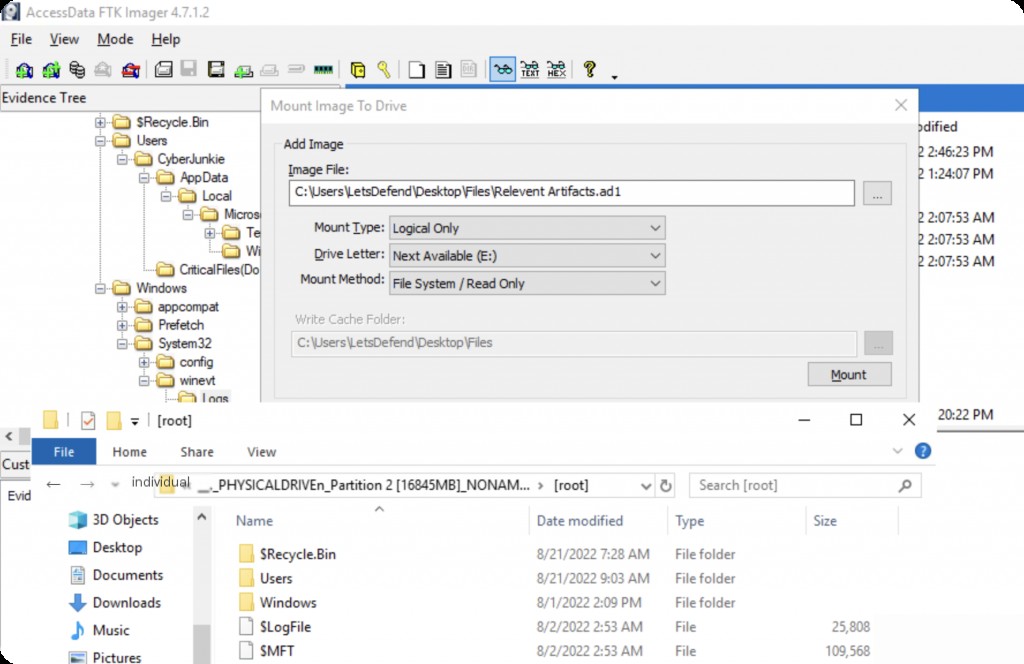
What is the full path of the downloaded document?
Initial access was achieved through a malicious document sent via email. Use FTK to mount the image to the local disk and analyze the dat files using ShellBags Explorer.
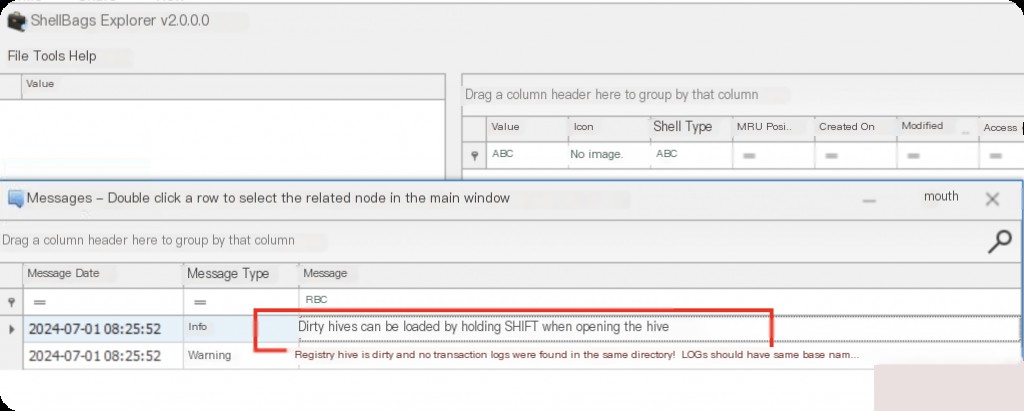
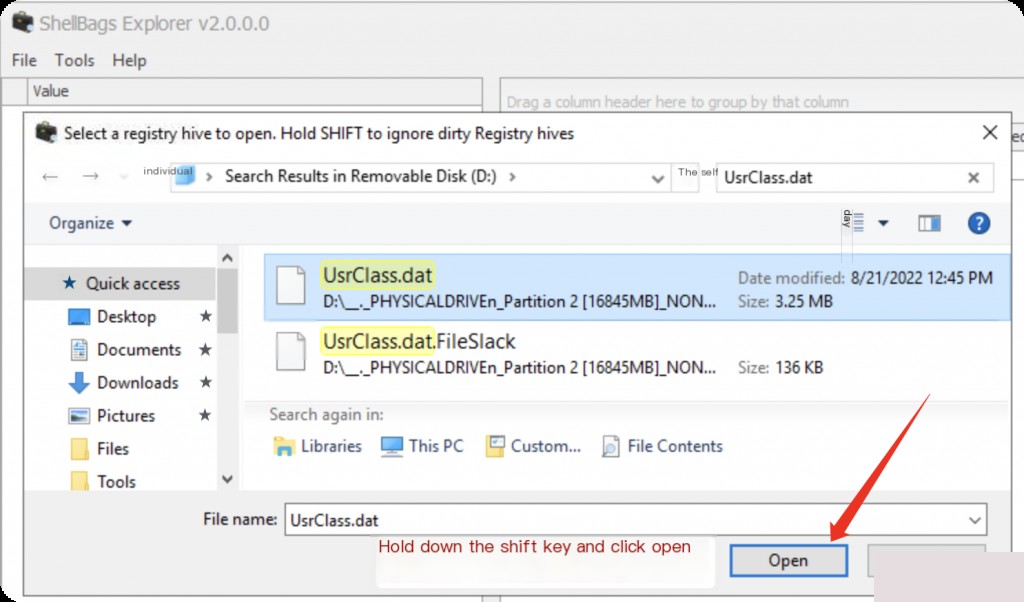
Directly opening it will result in an error Registry hive is dirty, so hold down the SHIFT key to ignore the error when opening.
Since the document was downloaded from a malicious email, the download path is likely the Downloads folder, so maildownloads is probably the path of the malicious document required by the challenge.
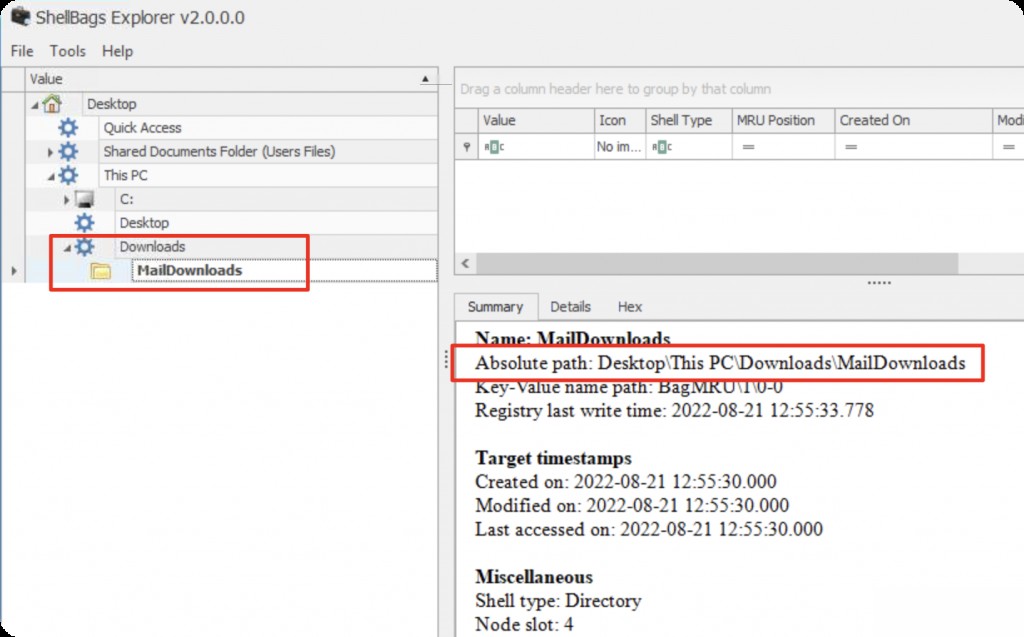
Combine the absolute path of the image: c:\users\cyberjunkie\downloads\maildownloads
What is the name of the document delivered via phishing?
After opening the document according to the prompt, a stager was downloaded, which securely deleted the document, making it unrecoverable. Analyze the artifacts to find evidence of GUI application execution or deletion evidence.
Therefore, you can start by analyzing the Windows Recycle Bin. $Recycle.Bin is a folder in the root directory of the Windows operating system that contains deleted files and folders. When a file or folder is deleted from the Windows system, it is moved to the Recycle Bin instead of being permanently deleted. The Recycle Bin path in the challenge is:
D:\__._PHYSICALDRIVEn_Partition 2 [16845MB]_NONAME [NTFS]\[root]\$Recycle.Bin\S-1-5-21-1187034906-4050784041-186213912-1001
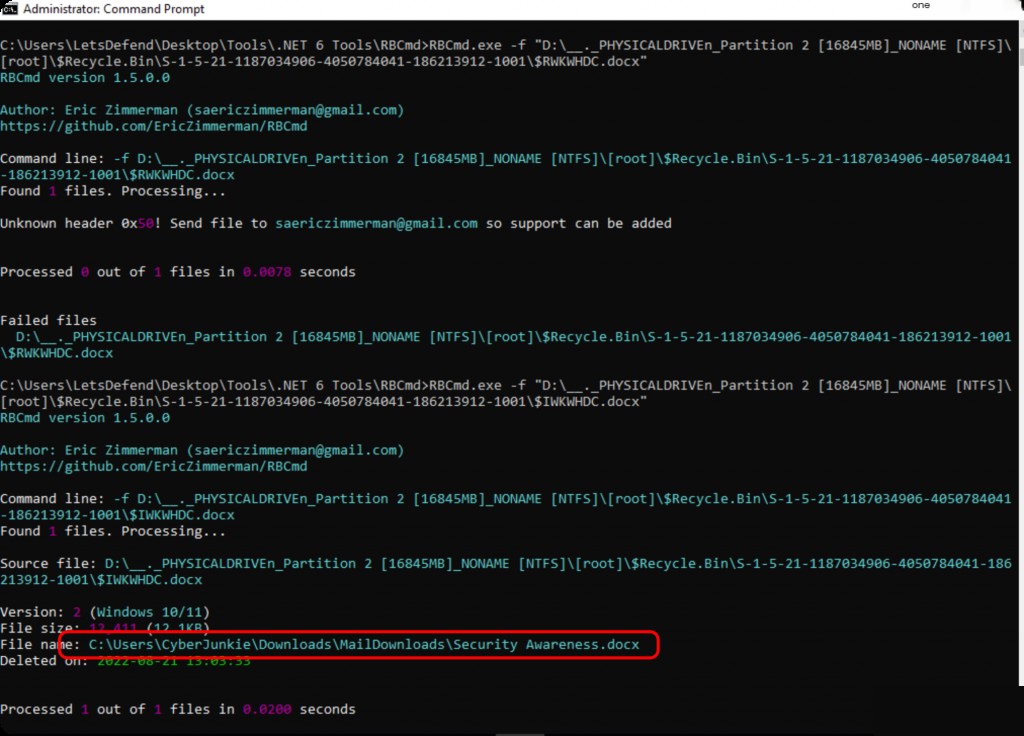
Use RBCmd to extract file information from the Recycle Bin.
RBCmd.exe -f "D:\__._PHYSICALDRIVEn_Partition 2 [16845MB]_NONAME [NTFS]\[root]\$Recycle.Bin\S-1-5-21-1187034906-4050784041-186213912-1001\$IWKWHDC.docx"
The document name obtained is “ Security awareness.docx”. Besides using RBCmd, you can also directly view the properties of the deleted file using FTK.
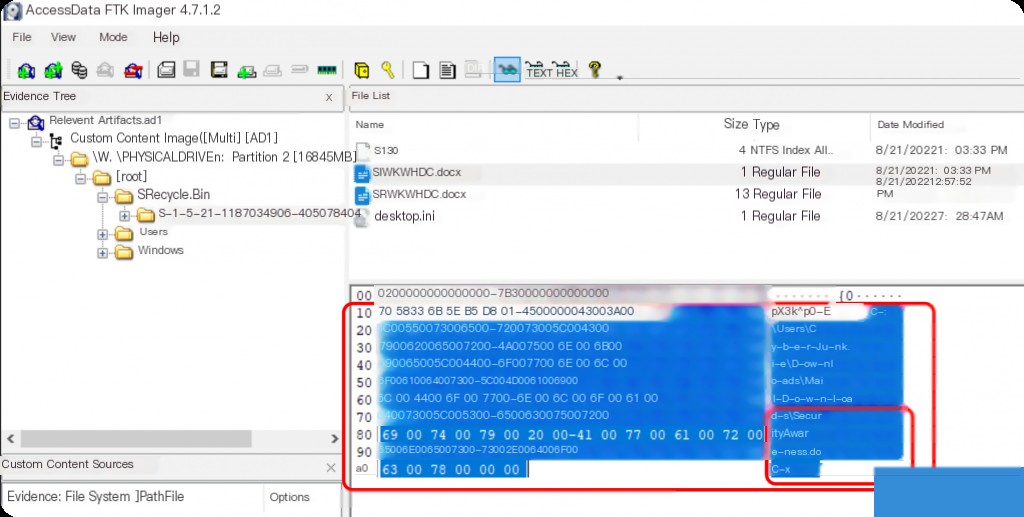
What is the name of the stager that connected to the attacker’s C2 server?
The initial investigation approach was to extract suspicious exe files by analyzing event ID 4688 in security.evtx.
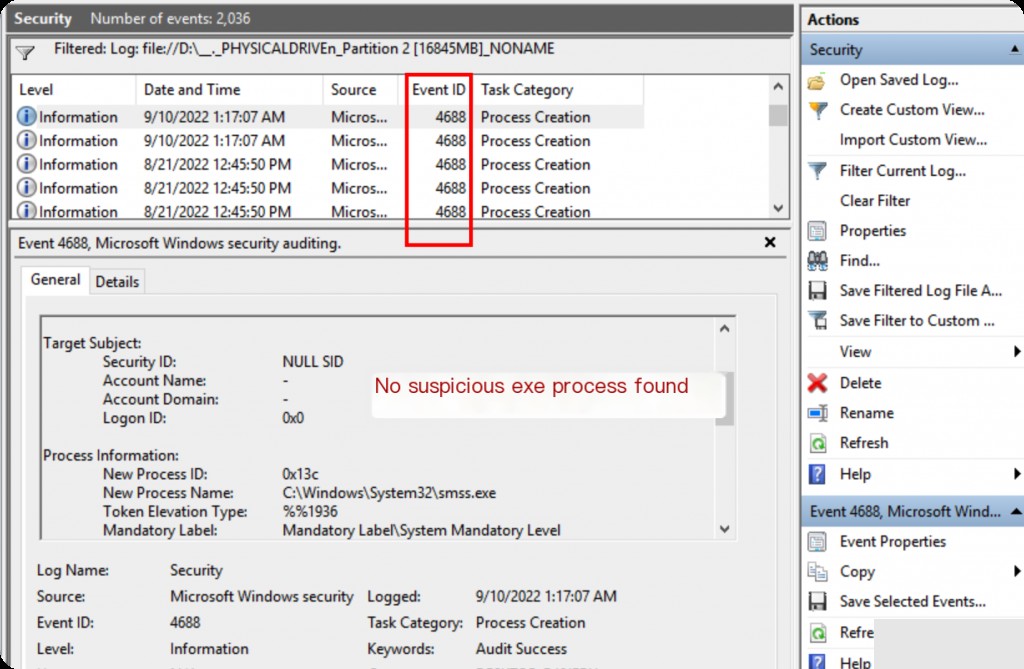
Therefore, a different approach was taken, starting from the Registry.
Amcache.hve is a Windows Registry Hive file primarily used to record information related to application execution. It was introduced starting from Windows 8 to help the operating system improve startup performance and application load speed. The Amcache.hve file contains a wealth of useful forensic information that can be used to analyze applications that have been run on the system and installed executables.
Default file path: C:\Windows\AppCompat\Programs\Amcache.hve
You can use the tool provided in the challenge, AmcacheParser.exe, to extract and analyze it.
AmcacheParser.exe -f "D:\__._PHYSICALDRIVEn_Partition 2 [16845MB]_NONAME [NTFS]\[root]\Windows\appcompat\Programs\Amcache.hve" --csv ./
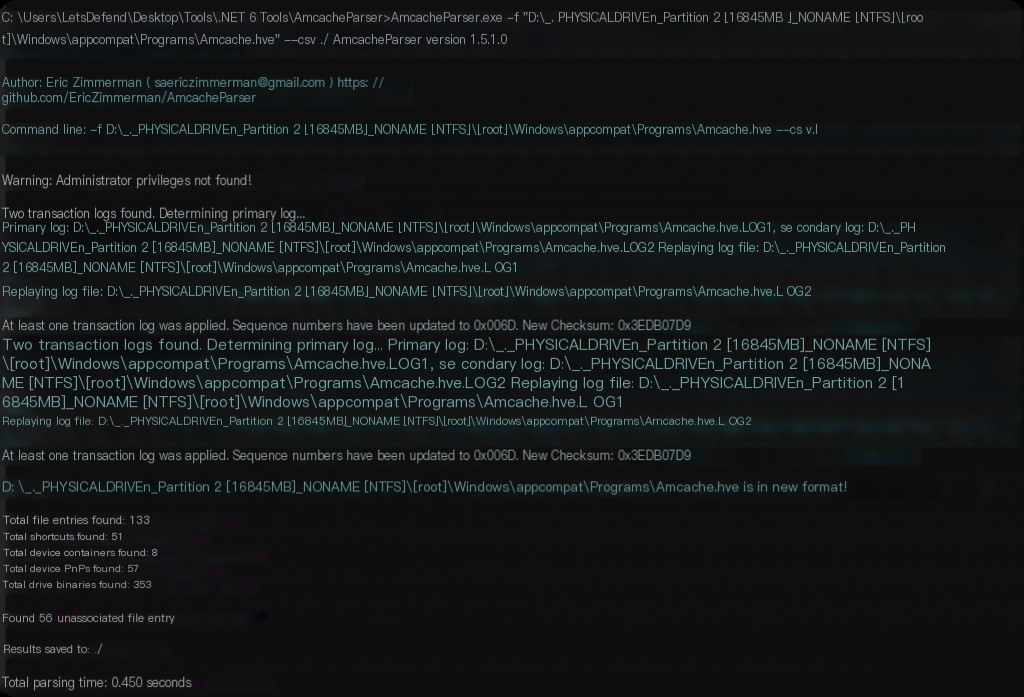
Multiple CSV files will be generated, with a focus on FileEntries.
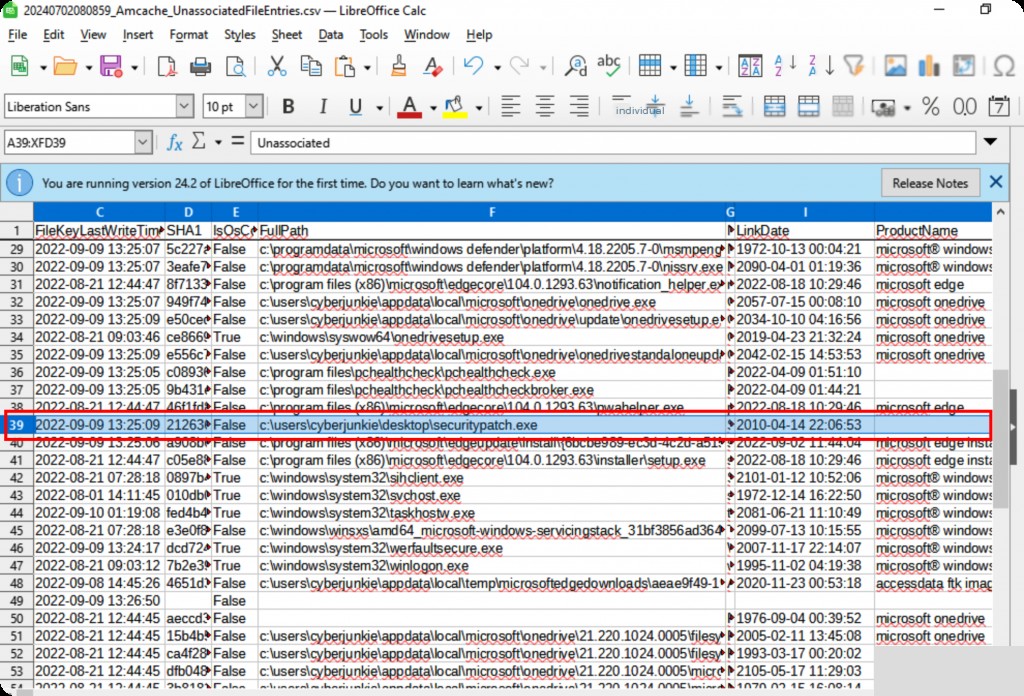
Analysis revealed that a suspicious exe file was run under the cyberjunkie user.
Analyze the stager and verify the original and tampered timestamps
The attacker manipulated the MACB timestamps of the stager executable file to confuse analysts. This is a method used by attackers to hide their tools on the victim’s file system, known as Timestomping .
Timestomping is an anti-forensic technique where an attacker modifies the timestamps (such as creation time, modification time, access time, etc.) of files or directories to obfuscate or hide their activity traces. This technique can make files appear as if they were created, modified, or accessed at different times, thereby confusing forensic analysts and making it difficult to reconstruct the true timeline of events.
$MFT is the Master File Table in the NTFS file system, which is one of the core components of the NTFS file system. The $MFT file contains metadata about all files and directories in the file system. Each file and directory has a record in the $MFT, which includes information such as file name, size, timestamps, permissions, and the location of file content on the disk.
In this challenge, the $MFT file is located at:
D:\__._PHYSICALDRIVEn_Partition 2 [16845MB]_NONAME [NTFS]\[root]\$MFT
Parsing the timestamps will take some time. Once completed, find the file path from the previous question.
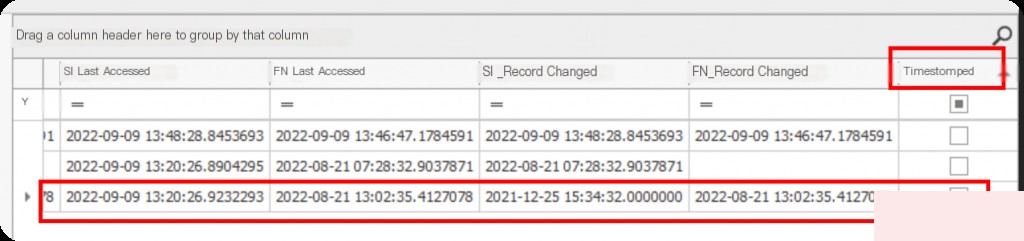
And it shows that the file’s timestamp has been modified.
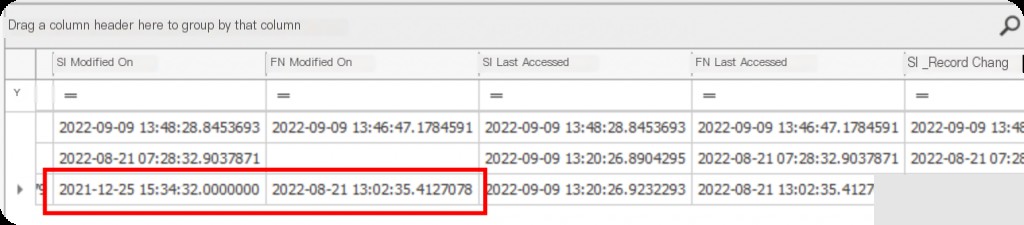
The hint for the question is: $STANDARD_INFORMATION and $FILE_NAME
$Standard_Information (SI) is the modified timestamp (user-level), and $FILE_Name (FN) is the original timestamp.
So the answer is: 2022-08-21 13:02:23.66 : 2021-12-25 15:34:32
What is the name of the process that executes the attacker’s persistent executable file upon exiting?
The attacker establishes persistence by manipulating registry keys. The GlobalFlags image file technique is used to establish persistence.
What is GlobalFlag persistence?
The GlobalFlag registry key used for attack persistence is an advanced attack technique. Attackers can use this registry key to set specific flags, thereby automatically loading malware or executing malicious operations when the system starts. This technique leverages system debugging and diagnostic features to hide or enhance the persistence of malware.
This key is located in the SOFTWARE registry hive, with the registry path as follows:
D:__._PHYSICALDRIVEn_Partition 2 [16845MB]_NONAME [NTFS][root]\Windows\System32\config\SOFTWARE
GlobalFlag is located in the following two locations:
- HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options
- HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SilentProcessExit
You can use the AccessData Registry Viewer tool to quickly search for this key.
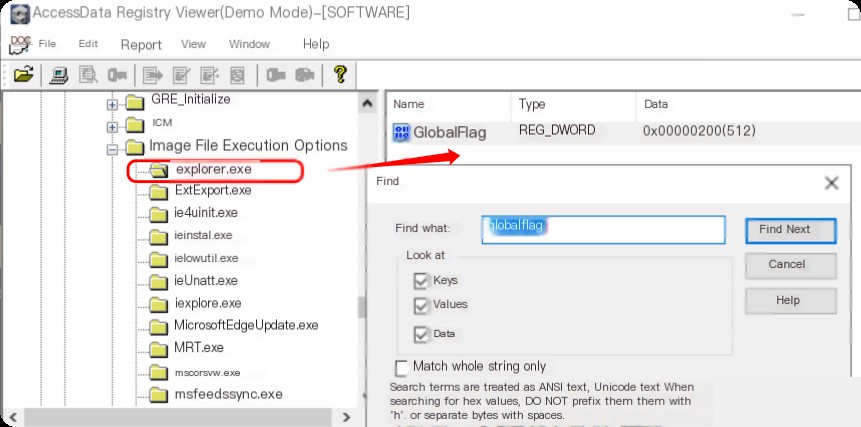
Only explorer.exe has the GlobalFlag set.
What is the full path name of the executable file set for persistence?
Similarly, searching SilentProcessExit will reveal the corresponding file path.
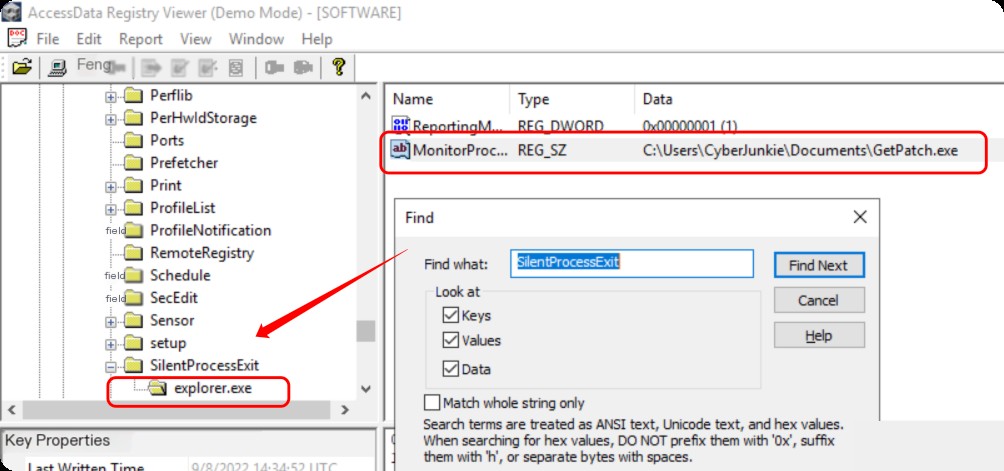
When explorer.exe terminates, GetPatch.exe begins execution.
What command did the attacker run on cmd after logging into another Windows system via RDP?
I initially had no clue about this question, but later I looked it up online.
During an RDP session, small bitmap images are cached on the client computer. These images can be extracted from the cache files in the Windows Terminal Services directory to reveal the contents of the remote session.
The RDP cache path corresponding to the question is:
D:__._PHYSICALDRIVEn_Partition 2 [16845MB]_NONAME [NTFS]\[root]\Users\CyberJunkie\AppData\Local\Microsoft\Terminal Server Client\Cache\
Use bmc-tools to analyze the bitmaps:
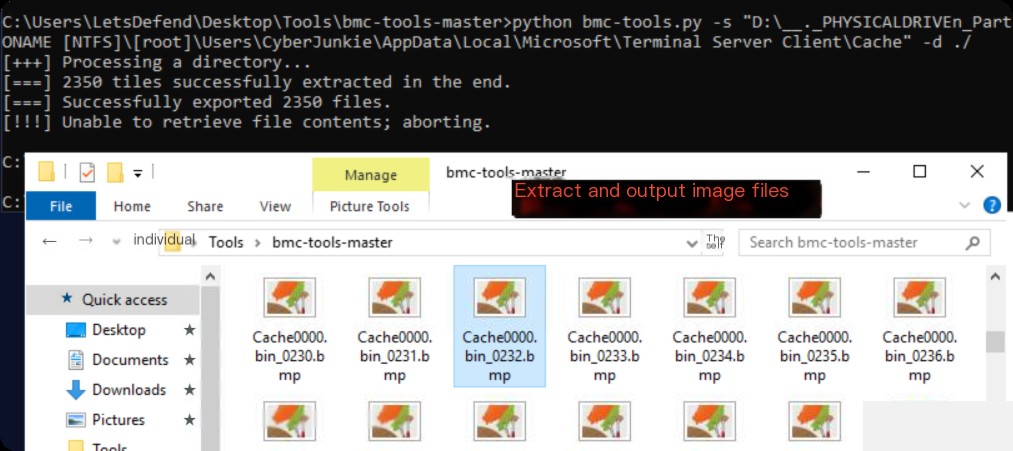
Stitching the bitmaps together reveals the cmd command content.
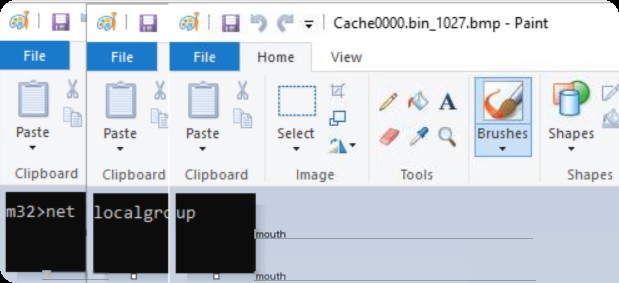
The bitmap image numbers are 1024, 1025, 1027.
What command was executed that led to privilege escalation?
In Cobalt Strike (CS) or Metasploit Framework (MSF), the command jump psexec_psh is typically used to create and start a temporary service to execute commands. Event log 7045 contains the name, path, and startup parameters of the new service, which can be used for further analysis and confirmation of malicious activity.
D:__._PHYSICALDRIVEn_Partition 2 [16845MB]_NONAME [NTFS]\[root]\Windows\System32\winevt\Logs
Here, the system.evtx file is copied to the DeepBlue directory.
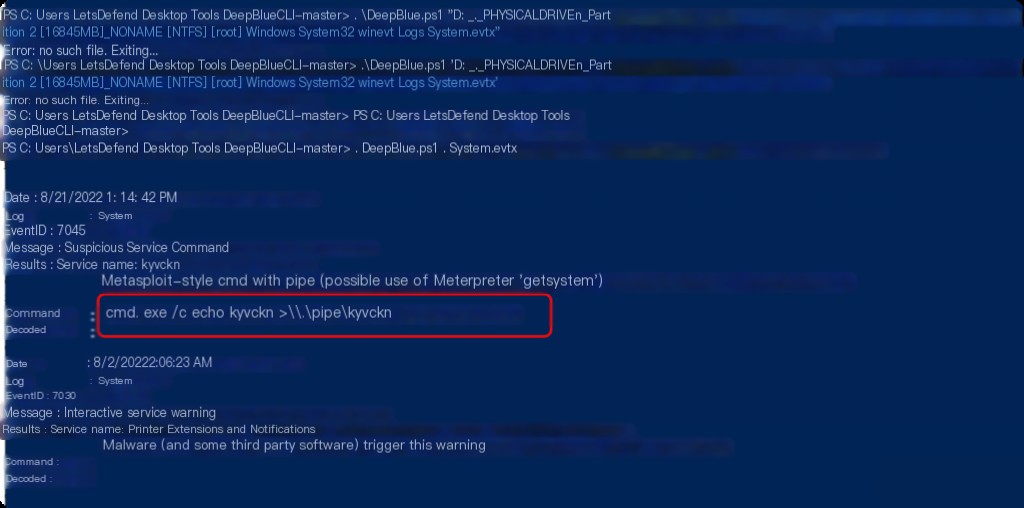
Since the target environment does not provide logparser, DeepBlue.ps1 is used for analysis.
What framework did the attacker use?
Based on the output of DeepBlue.ps1, the use of Meterpreter indicates that the Metasploit framework was used.


