Snort Modes
Snort includes three modes: sniffer, packet logger, and network intrusion detection system.
Snort as a Network Intrusion Detection System
1. Use Snort commands to start the intrusion detection system in Sniffer mode
sudo snort -d -h 192.168.202.134/24 -l ./log -c snort.conf -i en33
The explanation is as follows: (1) -d: Display application layer data (2) -h: Specify the value of HOME_NET in snort.conf, as shown below: 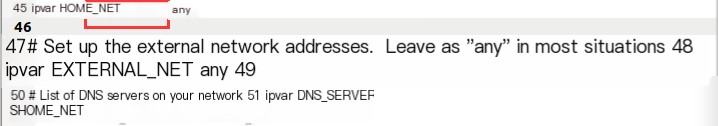 This command specifies
This command specifies HOME_NET=192.168.202.134/24 (this address needs to be replaced with the address of your virtual machine). (3) -l: Specify the log storage directory. It points to the log folder in the snort root directory. (4) -c: Specify the path of the snort configuration file. Therefore, this command needs to be run in the directory where snort.conf is located. (5) -i: Specify the network card as ens33 The result is as follows: 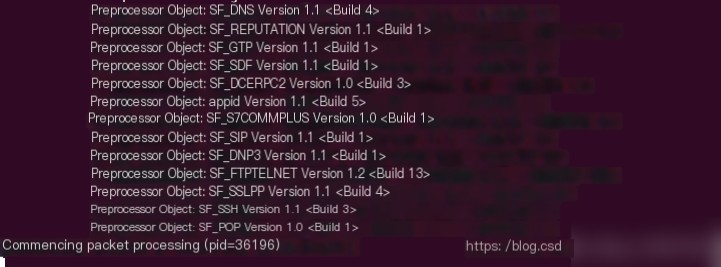 The appearance of
The appearance of Commencing packet processing proves that snort has successfully started.
2. Writing Snort Rules
Snort rules are divided into two parts: rule header and rule body. The rule header includes the action of the rule, the protocol used, the source and destination IP addresses, network source code, and port number. The rule body is enclosed in parentheses following the rule header, and they are generally not separated by lines. A simple rule is as follows:
alert tcp any any -> 192.168.202.134 any (msg:"test that snort is successful! ";sid:1000000900)
Alert for any TCP connection from any port to any port of 192.168.202.134 and print “test that snort is successful!“. Then use telnet to establish a TCP connection, and input the following on your physical machine (tested using Windows 10):
telnet 192.168.202.143 9999
The physical machine will display Connecting to 192.168.202.143... You can then close the connection on the physical machine and check the alert file in the log folder of the virtual machine as follows: 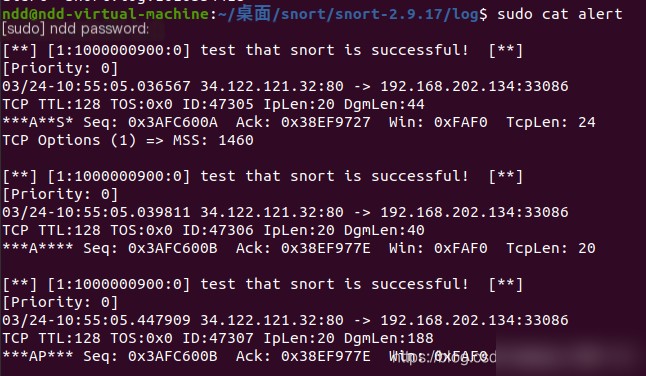
You can see that it prints the statement we just set: test that snort is successful!, and also indicates the source address and source port number. Additionally, it prints some application layer data (since we entered the -d option when starting snort, which stores application layer data in the file).
3. Advanced Snort Rule Writing
If a certain data is frequently used, you can define a variable and use $ to call the variable. For example:
var NET_IP 192.168.202.143
alert tcp any any -> $NET_IP any (msg:"test";sid=1000000901)


