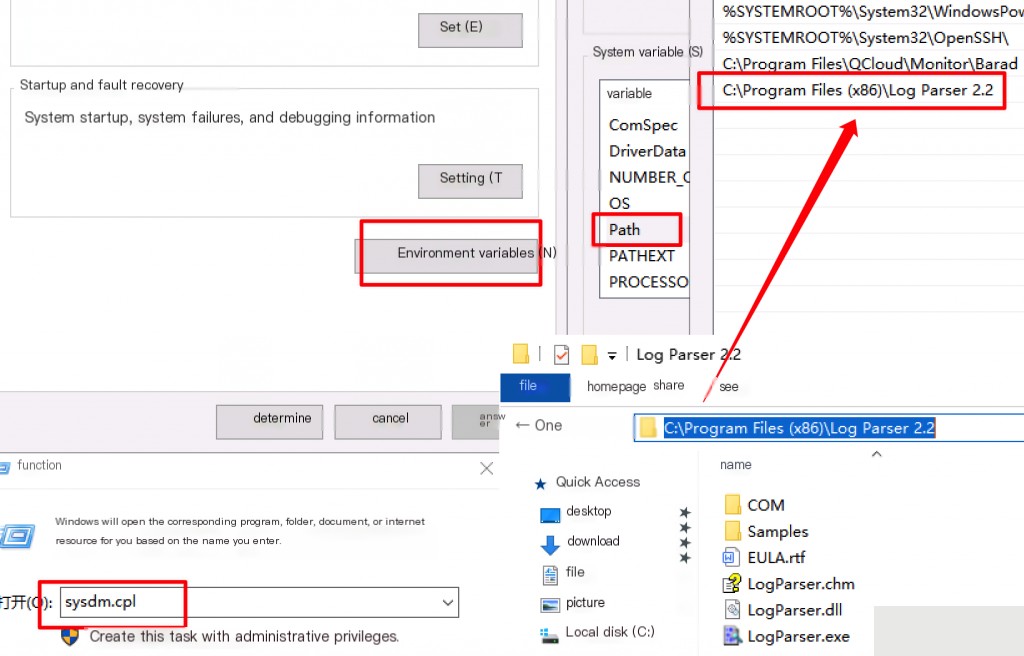
This article suggests adding LogParser to the environment variables before using it with PowerShell.
Adding LogParser to the Environment Variables
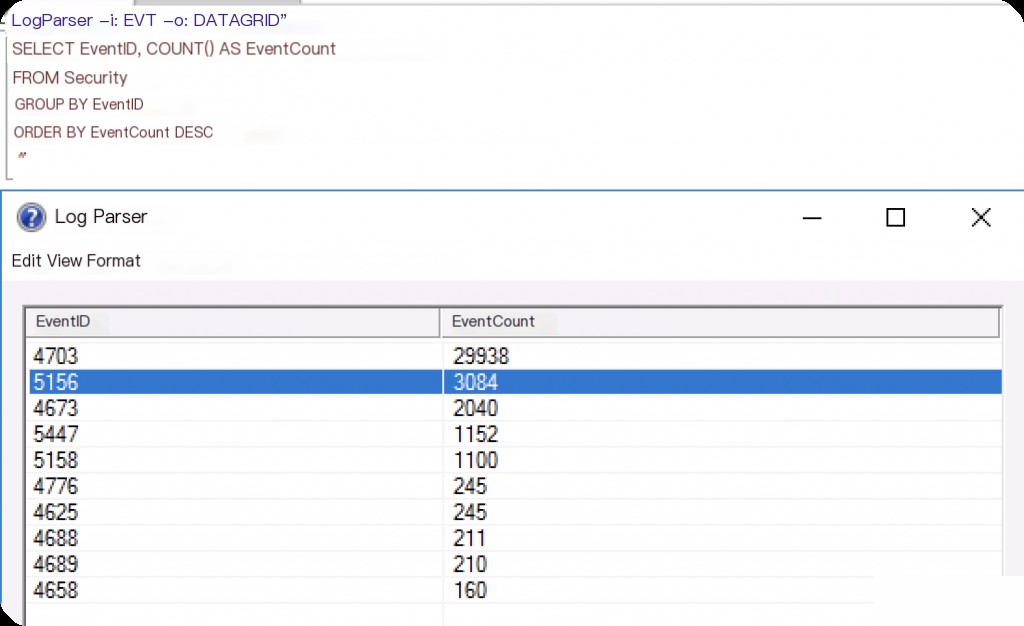
Counting and Sorting Event IDs Using LogParser
By counting and sorting, you can understand which Event IDs exist in the security logs.
LogParser -i:EVT -o:DATAGRID " SELECT EventID, COUNT(*) AS EventCount FROM Security GROUP BY EventID ORDER BY EventCount DESC "
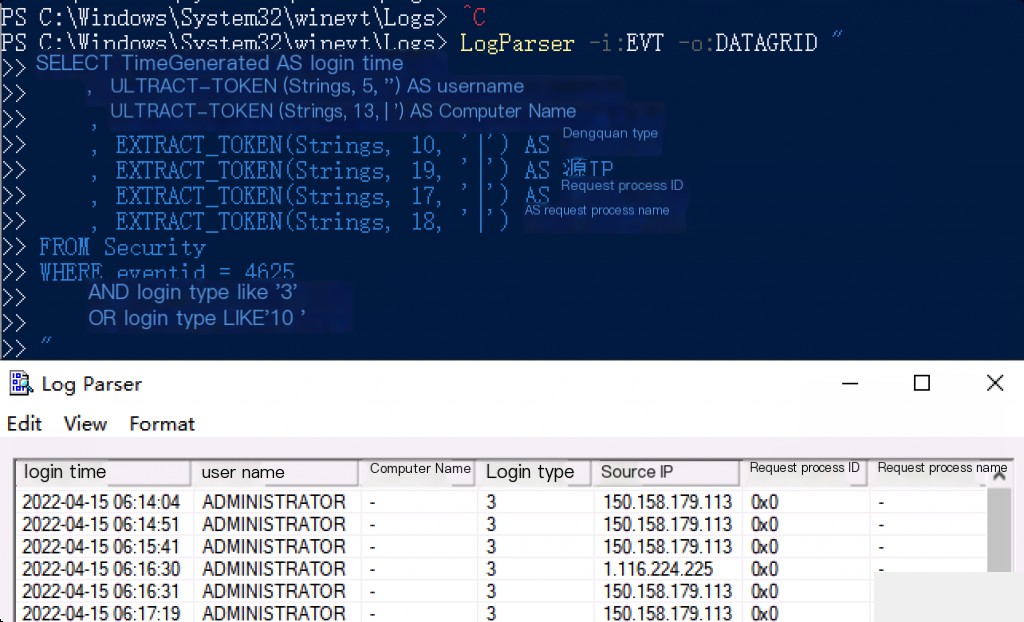
Remote Login Records using LogParser
Event ID: 4625 Login Failure – LogParser
In the Security log, Event ID 4625 represents authentication failure, and Type 3 indicates a network login. However, Logon Type 3 is not necessarily an RDP login failure log; it could be a network login for shared resources or printers, and some logs of this type may not capture the source IP.
LogParser -i:EVT -o:DATAGRID "
SELECT TimeGenerated AS Login Time
, EXTRACT_TOKEN(Strings, 5, '|') AS Username
, EXTRACT_TOKEN(Strings, 13, '|') AS Computer Name
, EXTRACT_TOKEN(Strings, 10, '|') AS Logon Type
, EXTRACT_TOKEN(Strings, 19, '|') AS Source IP
, EXTRACT_TOKEN(Strings, 17, '|') AS Request Process ID
, EXTRACT_TOKEN(Strings, 18, '|') AS Request Process Name
FROM Security
WHERE eventid = 4625
AND Logon Type LIKE '3'
OR Logon Type LIKE '10'
"
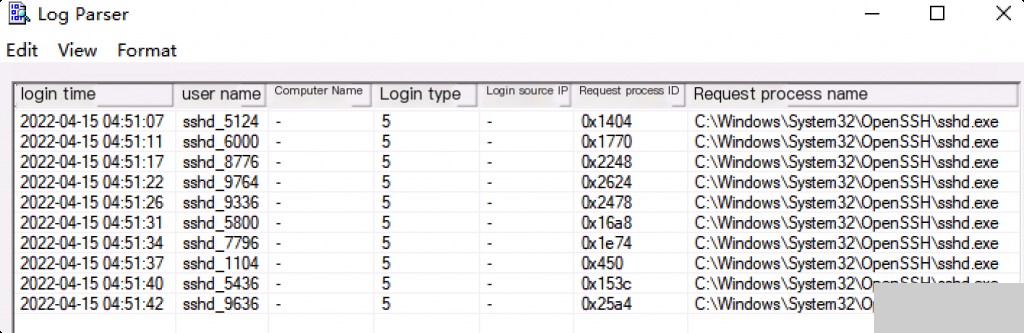
Event ID: 4624 LogParser Login Success
In the Security log, Event ID 4624, Type 10 or 7, where 7 represents session reconnection (re-login from a locked screen).
LogParser -i:EVT -o:DATAGRID "
SELECT TimeGenerated AS Login Time
, EXTRACT_TOKEN(Strings, 5, '|') AS Username
, EXTRACT_TOKEN(Strings, 11, '|') AS Computer Name
, EXTRACT_TOKEN(Strings, 8, '|') AS Logon Type
, EXTRACT_TOKEN(Strings, 18, '|') AS Source IP
, EXTRACT_TOKEN(Strings, 16, '|') AS Request Process ID
, EXTRACT_TOKEN(Strings, 17, '|') AS Request Process Name
FROM Security
WHERE eventid = 4624
AND Username NOT LIKE '%
Event ID: 21 LogParser Login Session
Log file name: Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
LogParser cannot directly read the Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx log file; it needs to be copied to another path and the file path specified.
logparser -i:evt -o:datagrid "
SELECT TimeGenerated AS Login Time, ComputerName AS Computer Name
, EXTRACT_TOKEN(Strings, 0, '|') AS Login Username
, EXTRACT_TOKEN(Strings, 2, '|') AS Login Source
FROM your.evtx
WHERE EventID = 21
"
LogParser: Event ID 22 – Shell Start
Log file name: Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
logparser -i:evt -o:datagrid "
SELECT TimeGenerated AS Login Time, ComputerName AS Computer Name
, EXTRACT_TOKEN(Strings, 0, '|') AS Login Username
, EXTRACT_TOKEN(Strings, 2, '|') AS Login Source
FROM your.evtx
WHERE EventID = 22
"
Event ID: 1149 Remote Login Records LogParser
Log file name: Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Operational.evtx
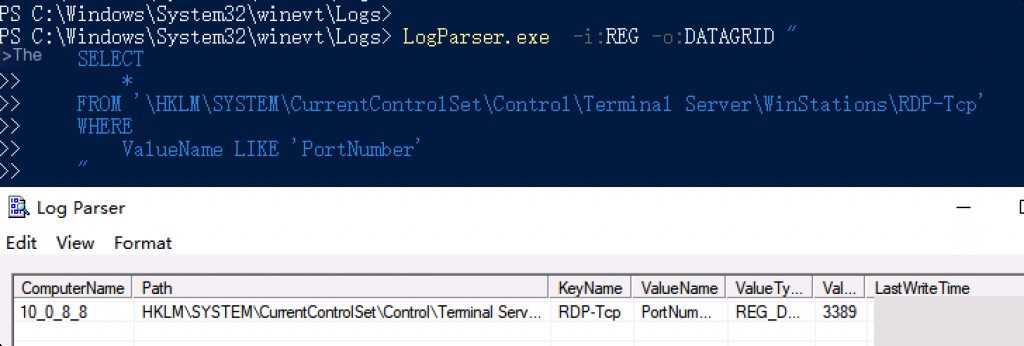
LogParser.exe -i:reg -o:datagrid " select LastWriteTime as Last Login Time ,KeyName as Remote IP ,Value as Username from \HKEY_CURRENT_USER\SOFTWARE\Microsoft where Path LIKE '%\Servers%' "
RDP Session Disconnect/Reconnect/Logout LogParser
Session disconnection (unexpected interruption) generates the following series of logs:
Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx- 24 RDP Session Disconnect
- 40 RDP Session Disconnect or Reconnect
Security- 4779 User Disconnected from RDP Session
- 4634 Account Logout
The disconnection log contains a Reason field, for more details refer to: ExtendedDisconnectReasonCode enumeration – Win32 apps | Microsoft Docs
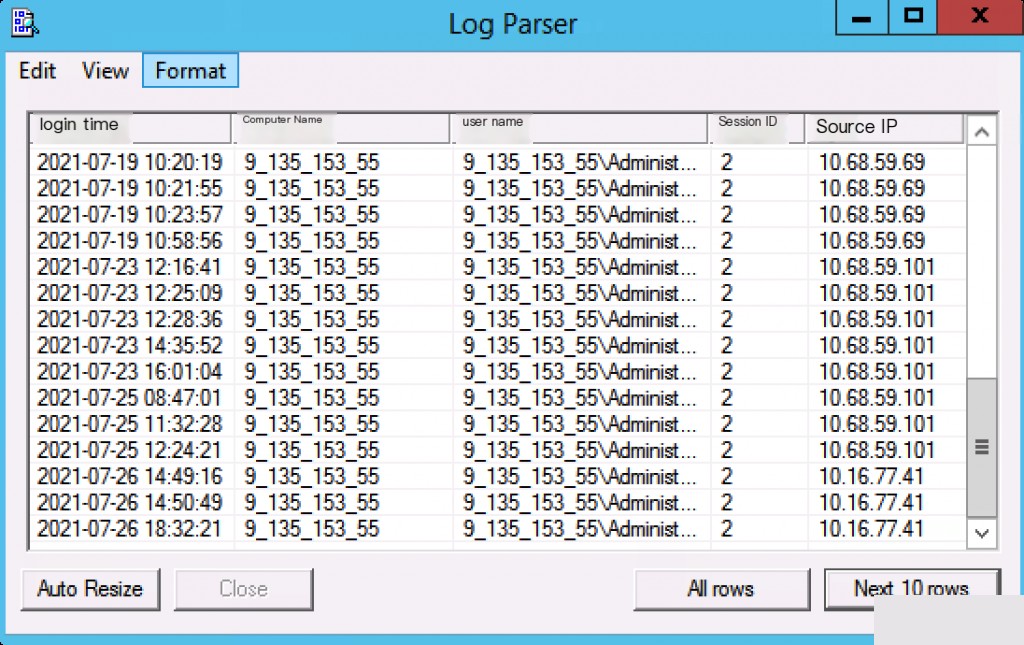
Event ID: 24 RDP Session Disconnect LogParser
LogParser.exe -i:EVT -o:DATAGRID "
SELECT
TimeGenerated AS Login Time,
ComputerName AS Computer Name,
EXTRACT_TOKEN(Strings, 0, '|') AS Username,
EXTRACT_TOKEN(Strings, 1, '|') AS Session ID,
EXTRACT_TOKEN(Strings, 2, '|') AS Source IP
FROM Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
WHERE
EventID = 24
"
Session disconnection (intentional disconnection) generates the following series of logs:
Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx- 24 RDP Session Disconnect
- 39 RDP Session Disconnect
- 40 RDP Session Disconnect or Reconnect
Security- 4779 User Disconnected from RDP Session
- 4634 Account Logout
Intentional disconnection refers to a purposeful disconnection by the user, not just closing the client to disconnect, usually done through the disconnect option in the start menu.
Event ID 24 or ID 4779 can confirm RDP session disconnection. To determine if the disconnection was intentional, correlate with ID 39 for analysis.
Event ID: 39 – RDP Session Disconnect (LogParser)
LogParser.exe -i:EVT -o:DATAGRID "
SELECT
TimeGenerated AS Login Time,
ComputerName AS Computer Name,
EXTRACT_TOKEN(Strings, 0, '|') AS Target Session,
EXTRACT_TOKEN(Strings, 1, '|') AS Source
FROM Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
WHERE
EventID = 39
"
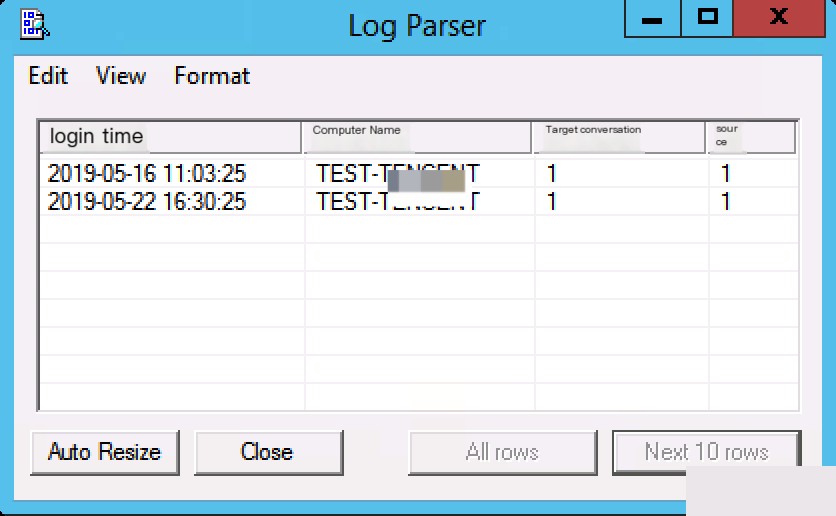
Session reconnection usually refers to re-logging in after a remote session timeout or manual lock. In full-screen remote login mode, you can lock the screen with Win+L or execute rundll32.exe user32.dll LockWorkStation to lock the screen.
LogParser Event ID: 25 RDP Session Reconnect
LogParser.exe -i:EVT -o:DATAGRID "
SELECT
TimeGenerated AS Login Time,
ComputerName AS Computer Name,
EXTRACT_TOKEN(Strings, 0, '|') AS Username,
EXTRACT_TOKEN(Strings, 1, '|') AS Session ID,
EXTRACT_TOKEN(Strings, 2, '|') AS Source IP
FROM Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
WHERE
EventID = 25
"
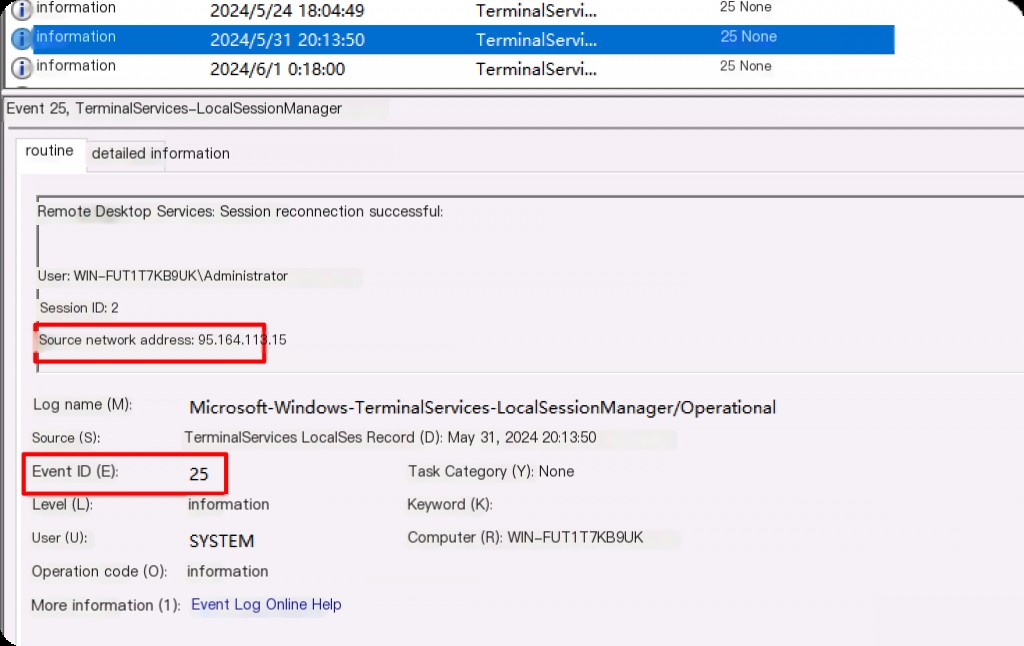
Successful Reconnection Record (ID 4624 Type 7)
LogParser -i:EVT -o:DATAGRID "
SELECT TimeGenerated AS LoginTime
, EXTRACT_TOKEN(Strings, 5, '|') AS UserName
, EXTRACT_TOKEN(Strings, 11, '|') AS ComputerName
, EXTRACT_TOKEN(Strings, 8, '|') AS LoginType
, EXTRACT_TOKEN(Strings, 18, '|') AS LoginSourceIP
, EXTRACT_TOKEN(Strings, 16, '|') AS RequestProcessID
, EXTRACT_TOKEN(Strings, 17, '|') AS RequestProcessName
FROM Security
WHERE eventid = 4624
AND LoginType LIKE '7'
"
Session Reconnect Failure Records (ID 4625 Type 7)
LogParser -i:EVT -o:DATAGRID "
SELECT TimeGenerated AS LoginTime
, EXTRACT_TOKEN(Strings, 5, '|') AS UserName
, EXTRACT_TOKEN(Strings, 13, '|') AS ComputerName
, EXTRACT_TOKEN(Strings, 10, '|') AS LoginType
, EXTRACT_TOKEN(Strings, 19, '|') AS SourceIP
, EXTRACT_TOKEN(Strings, 17, '|') AS RequestProcessID
, EXTRACT_TOKEN(Strings, 18, '|') AS RequestProcessName
FROM Security
WHERE eventid = 4625
AND LoginType LIKE '7'
"
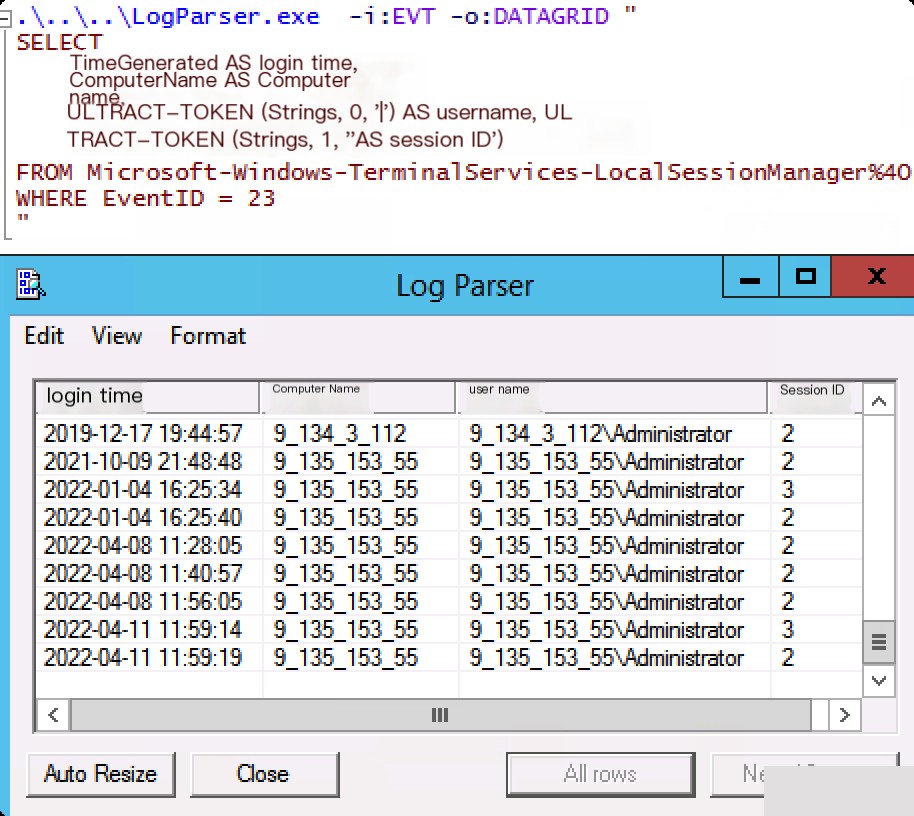
LogParser Event ID: 23 Session Logoff
Log File Name: Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
LogParser.exe -i:EVT -o:DATAGRID "
SELECT
TimeGenerated AS LoginTime,
ComputerName AS ComputerName,
EXTRACT_TOKEN(Strings, 0, '|') AS UserName,
EXTRACT_TOKEN(Strings, 1, '|') AS SessionID
FROM Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
WHERE EventID = 23
"
LogParser Service Records
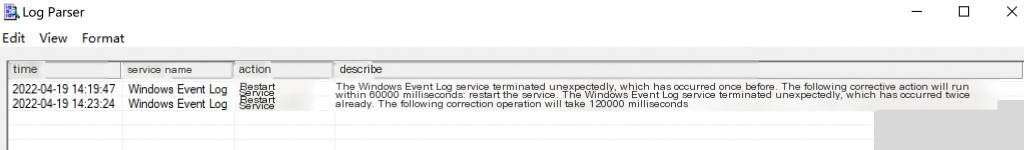
Event ID: 7031 LogParser Service Restart
LogParser.exe -i:evt -o:datagrid "
SELECT TimeGenerated AS Time, EXTRACT_TOKEN(Strings, 0, '|') AS ServiceName
, EXTRACT_TOKEN(Strings, 4, '|') AS Action
, Message AS Description
FROM System
WHERE eventid = 7031
AND ServiceName = 'Windows Event Log'
"
Event ID: 1102 – Security Log Clear Records (LogParser)
LogParser.exe -i:evt -o:datagrid " SELECT TimeGenerated AS Time, Message AS Description FROM Security WHERE eventid = 1102 "
Event ID: 104 – Other Log Clear Records using LogParser
LogParser.exe -i:evt -o:datagrid "
SELECT TimeGenerated AS Time
, EXTRACT_TOKEN(Strings, 0, '|') AS User
, Message AS Description
FROM system
WHERE eventid = 104
"
Scheduled Tasks (Cannot Query on 64-bit Systems)
Due to LogParser only having a compiled 32-bit version, querying registry information on 64-bit systems will be redirected, resulting in empty information.
LogParser.exe -i:reg -o:datagrid " SELECT * FROM 'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache' "
Scheduled Tasks (32-bit Systems)
Scheduled Tasks (64-bit Systems)
Therefore, it is not recommended to use LogParser to obtain registry information!
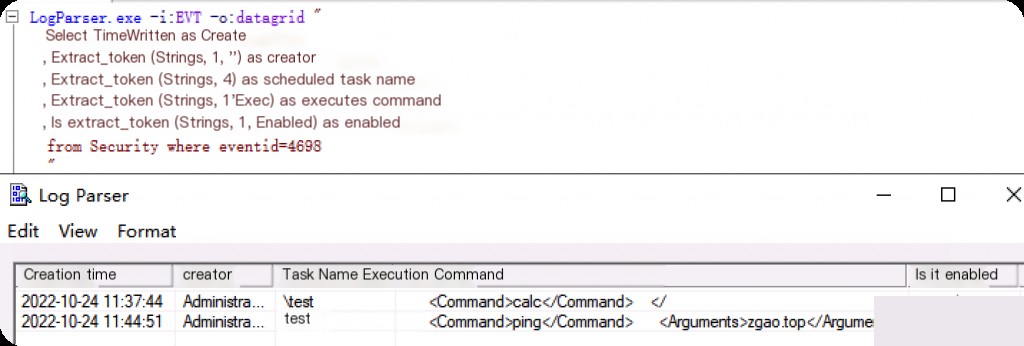
Event ID: 4698 – Scheduled Task Created using LogParser
LogParser.exe -i:EVT -o:datagrid " select TimeWritten as CreationTime ,extract_token(Strings,1,'|') as Creator ,extract_token(Strings,4,'|') as TaskName ,extract_token(Strings,1,'Exec> ') as ExecuteCommand ,extract_token(Strings,1,'Enabled> ') as IsEnabled from Security where eventid=4698 "
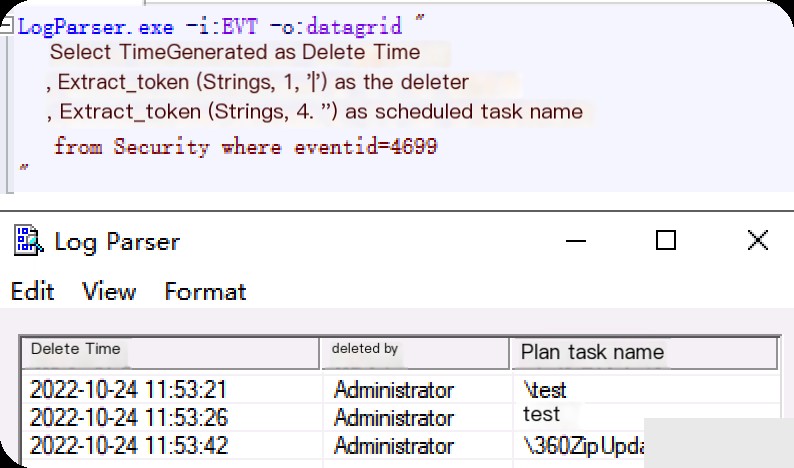
LogParser Event ID: 4699 Scheduled Task Deleted
LogParser.exe -i:EVT -o:datagrid " select TimeGenerated as DeletionTime ,extract_token(Strings,1,'|') as Deleter ,extract_token(Strings,4,'|') as TaskName from Security where eventid=4699 "
LogParser TaskScheduler Operation Logs
TaskScheduler has its own logs, but they need to be enabled in advance.
Log Location: Application and Services Logs > Microsoft > Windows > TaskScheduler > Operational
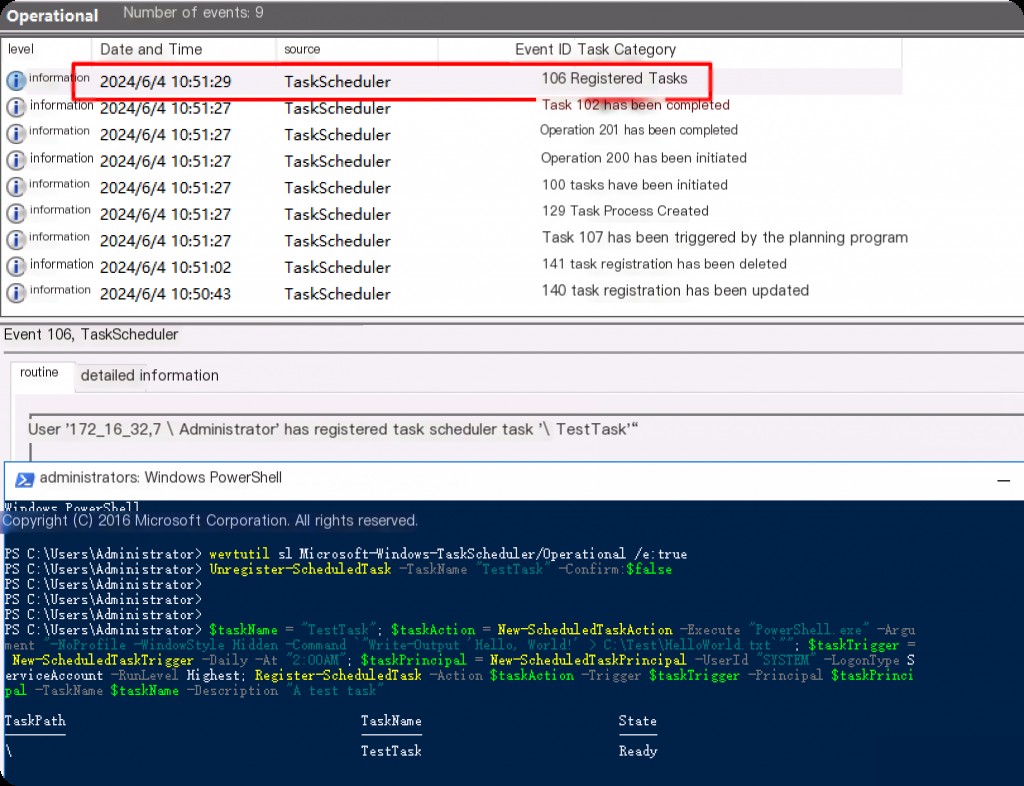
Open PowerShell and run as administrator.
wevtutil sl Microsoft-Windows-TaskScheduler/Operational /e:true
Create a scheduled task to test if the logs are successfully enabled.
$taskName = "TestTask"; $taskAction = New-ScheduledTaskAction -Execute "PowerShell.exe" -Argument "-NoProfile -WindowStyle Hidden -Command `"Write-Output 'Hello, World!' > C:\Test\HelloWorld.txt`""; $taskTrigger = New-ScheduledTaskTrigger -Daily -At "2:00AM"; $taskPrincipal = New-ScheduledTaskPrincipal -UserId "SYSTEM" -LogonType ServiceAccount -RunLevel Highest; Register-ScheduledTask -Action $taskAction -Trigger $taskTrigger -Principal $taskPrincipal -TaskName $taskName -Description "A test task"
Delete the created scheduled task.
Unregister-ScheduledTask -TaskName "TestTask" -Confirm:$false
Event ID: 106 LogParser Scheduled Task Registration
Very little information, only the task name of the scheduled task will be displayed.
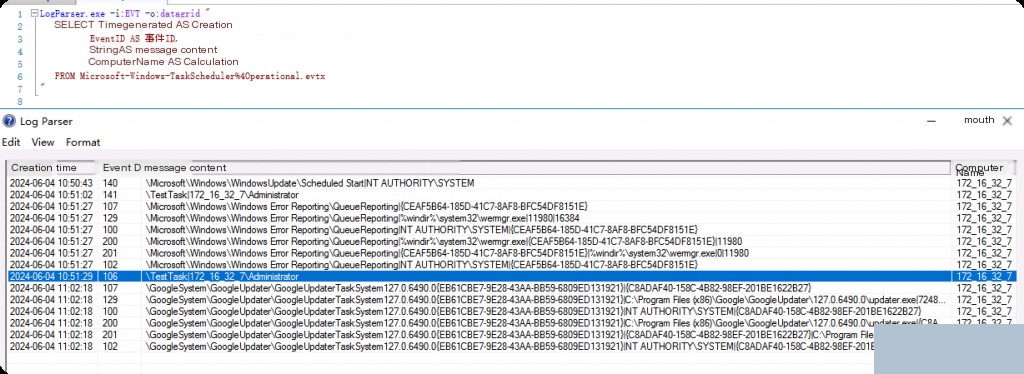
No filtering on event IDs for TaskScheduler.
LogParser.exe -i:EVT -o:datagrid "
SELECT TimeGenerated AS CreationTime,
EventID AS EventID,
Strings AS MessageContent,
ComputerName AS ComputerName
FROM Microsoft-Windows-TaskScheduler%4Operational.evtx
"
System User Change Records
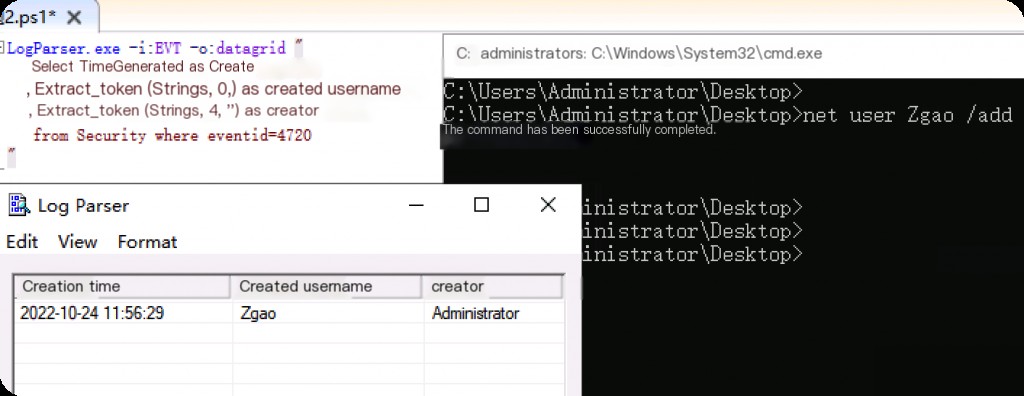
Event ID: 4720 User Created
LogParser.exe -i:EVT -o:datagrid " select TimeGenerated as CreationTime ,extract_token(Strings,0,'|') as CreatedUserName ,extract_token(Strings,4,'|') as Creator from Security where eventid=4720 "
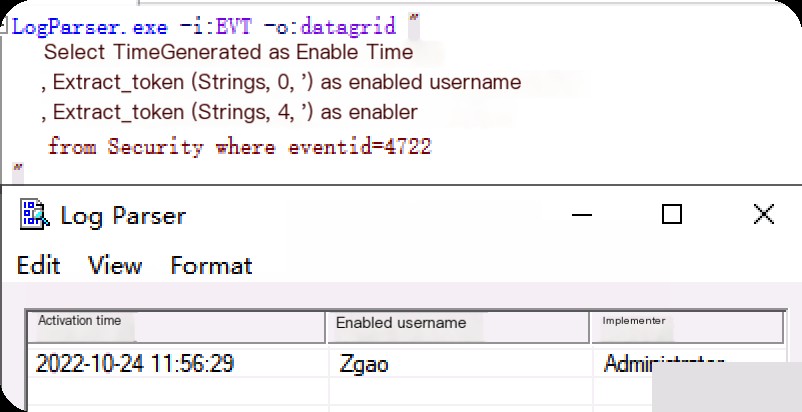
Event ID: 4722 User Enabled
LogParser.exe -i:EVT -o:datagrid " select TimeGenerated as EnableTime ,extract_token(Strings,0,'|') as EnabledUserName ,extract_token(Strings,4,'|') as Enabler from Security where eventid=4722 "
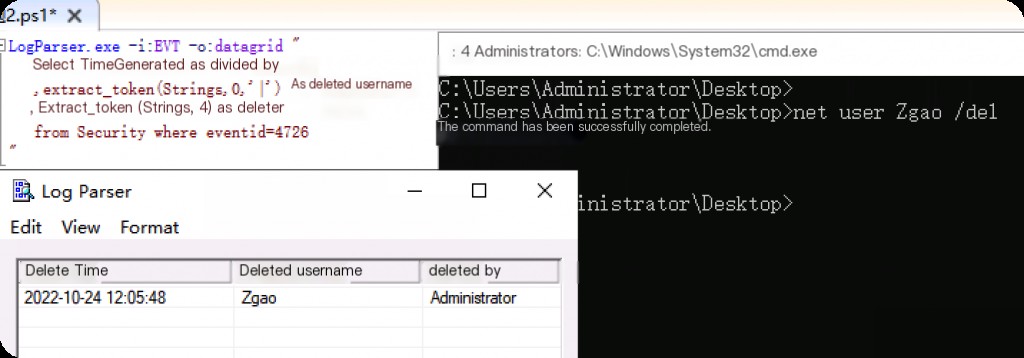
Event ID: 4726 User Deletion
LogParser.exe -i:EVT -o:datagrid " select TimeGenerated as DeletionTime ,extract_token(Strings,0,'|') as DeletedUsername ,extract_token(Strings,4,'|') as Deleter from Security where eventid=4726 "
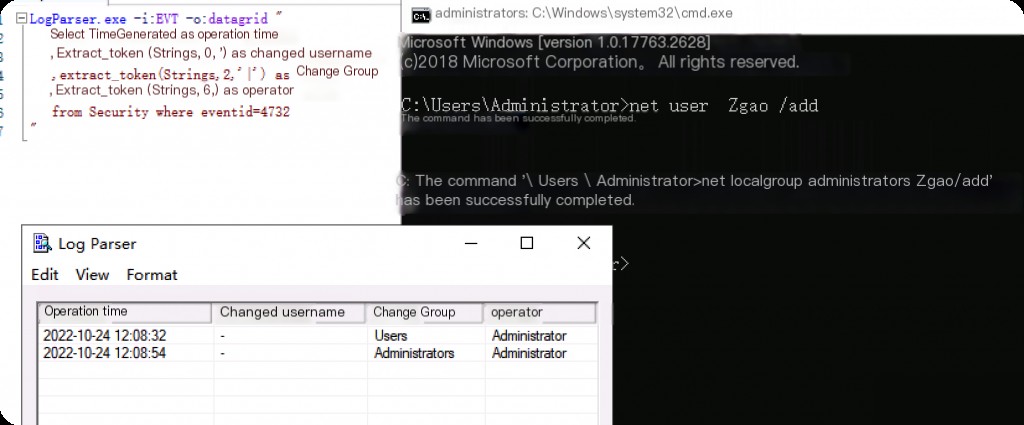
Event ID: 4732 User Group Change
LogParser.exe -i:EVT -o:datagrid " select TimeGenerated as OperationTime ,extract_token(Strings,0,'|') as ChangedUsername ,extract_token(Strings,2,'|') as ChangedGroup ,extract_token(Strings,6,'|') as Operator from Security where eventid=4732 "
Event ID: 4740 User Account Locked
Windows generates two types of events related to account lockouts. Each time an account is locked, Event ID 4740 is generated on domain controllers, Windows servers, and workstations. Each time an account is unlocked, Event ID 4767 is generated.
Windows allows you to set an Account Lockout Threshold to define the number of invalid login attempts before an account is locked. You can also use the Account Lockout Duration setting to define how long an account remains locked. These account lockout policies help protect the network from password guessing attempts and potential brute force attacks.
LogParser -i:EVT -o:DATAGRID "
SELECT TimeGenerated AS EventTime
, EXTRACT_TOKEN(Strings, 0, '|') AS LockedUsername
, EXTRACT_TOKEN(Strings, 1, '|') AS CallerComputerName
, EXTRACT_TOKEN(Strings, 4, '|') AS AccountName
, EXTRACT_TOKEN(Strings, 5, '|') AS AccountDomain
FROM Security
WHERE eventid = 4740
"
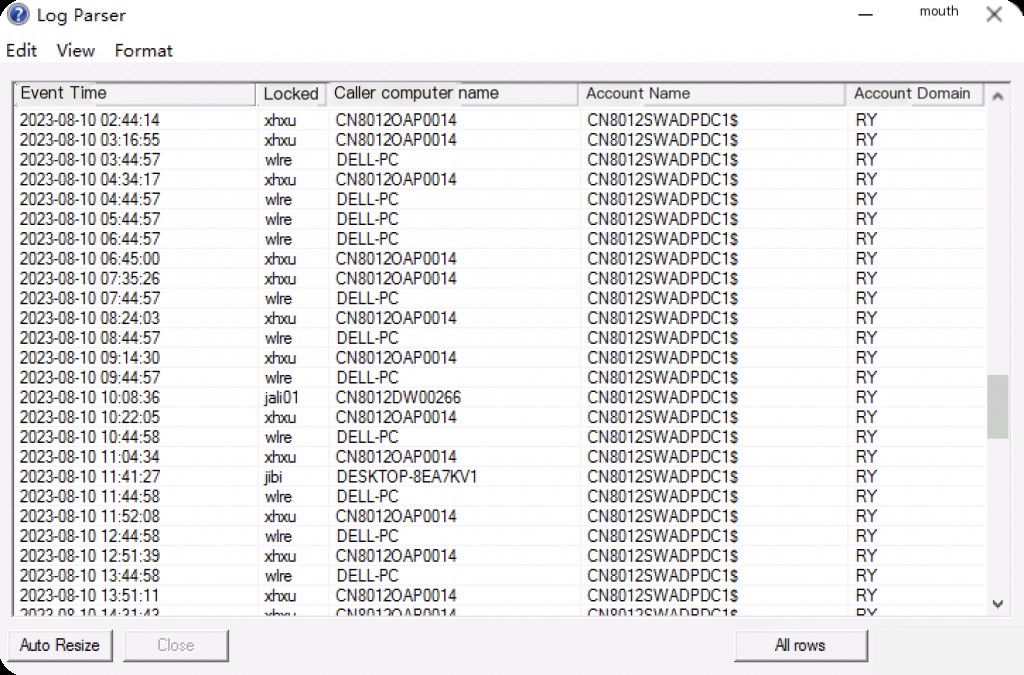
RDP Open Ports
LogParser.exe -i:reg -o:datagrid "
select LastWriteTime as LastWriteTime
,Value as RemotePort
from 'HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp' where ValueName like 'PortNumber'
"
RDP Remote Login to Other Hosts Records
Remote login records need to be obtained by querying the registry.
LogParser.exe -i:reg -o:datagrid "
select LastWriteTime as LastLoginTime
,KeyName as RemoteIP
,Value as Username
from 'HKEY_CURRENT_USER\SOFTWARE\Microsoft\Terminal Server Client\Servers'
"
PowerShell Execution Records
In PowerShell logs, executing a PowerShell command generates 6 logs, including 2 engine lifecycle logs (EventID: 400 Start; EventID: 403 Stop) and 6 program lifecycle logs (EventID: 600) (Registry, Alias, Environment, FileSystem, Function, Variable start).
PowerShell mainly focuses on the value of hostApplication.
Event ID: 400 Start
Log File Name: Windows PowerShell.evtx
logparser.exe -i:evt -o:datagrid "
SELECT TimeGenerated AS Time
, EXTRACT_TOKEN(EXTRACT_TOKEN(Strings, 1, 'Host Application = '), 0, 'Engine Version') AS Data
FROM your.evtx
WHERE eventid = 4103
"
Note: Logparser has a length limit when outputting in table format, which may not display completely.
Event ID: 4103 Executing Pipeline
Log File Name: Microsoft-Windows-PowerShell%4Operational.evtx
logparser.exe -i:evt "
SELECT TimeGenerated AS Time, ComputerName AS ComputerName, Sid
, EXTRACT_TOKEN(EXTRACT_TOKEN(Strings, 1, 'Host Application = '), 0, 'Engine Version') AS Data
FROM your.evtx
WHERE eventid = 4103
"
Event ID: xxxx PowerShell File Download Record
Log File Name: Microsoft-Windows-PowerShell-DesiredStateConfiguration-FileDownloadManager%4Operational.evtx
To be supplemented
CMD Command Execution Records
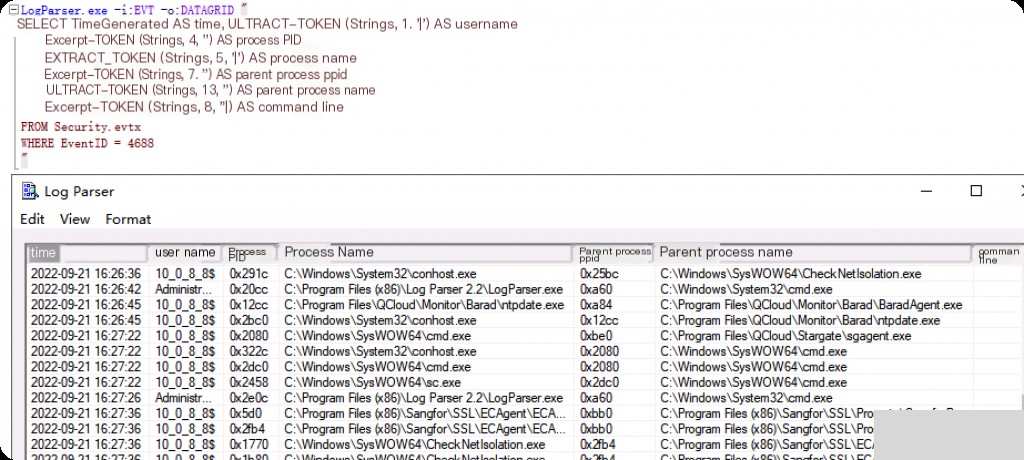
Event ID: 4688 Create New Process
Event ID 4688 is not enabled by default in Windows and needs to be manually enabled in advance.
LogParser.exe -i:EVT -o:DATAGRID "
SELECT TimeGenerated AS Time, EXTRACT_TOKEN(Strings, 1, '|') AS Username
, EXTRACT_TOKEN(Strings, 4, '|') AS ProcessPID
, EXTRACT_TOKEN(Strings, 5, '|') AS ProcessName
, EXTRACT_TOKEN(Strings, 7, '|') AS ParentProcessPPID
, EXTRACT_TOKEN(Strings, 13, '|') AS ParentProcessName
, EXTRACT_TOKEN(Strings, 8, '|') AS CommandLine
FROM Security.evtx
WHERE EventID = 4688
"
Event ID: 4689 End Process
LogParser.exe -i:EVT -o:DATAGRID "
SELECT TimeGenerated AS Time, EXTRACT_TOKEN(Strings, 1, '|') AS Username
, EXTRACT_TOKEN(Strings, 4, '|') AS StatusCode
, EXTRACT_TOKEN(Strings, 5, '|') AS ProcessPID
, EXTRACT_TOKEN(Strings, 6, '|') AS ProcessName
FROM Security.evtx
WHERE EventID = 4689
"
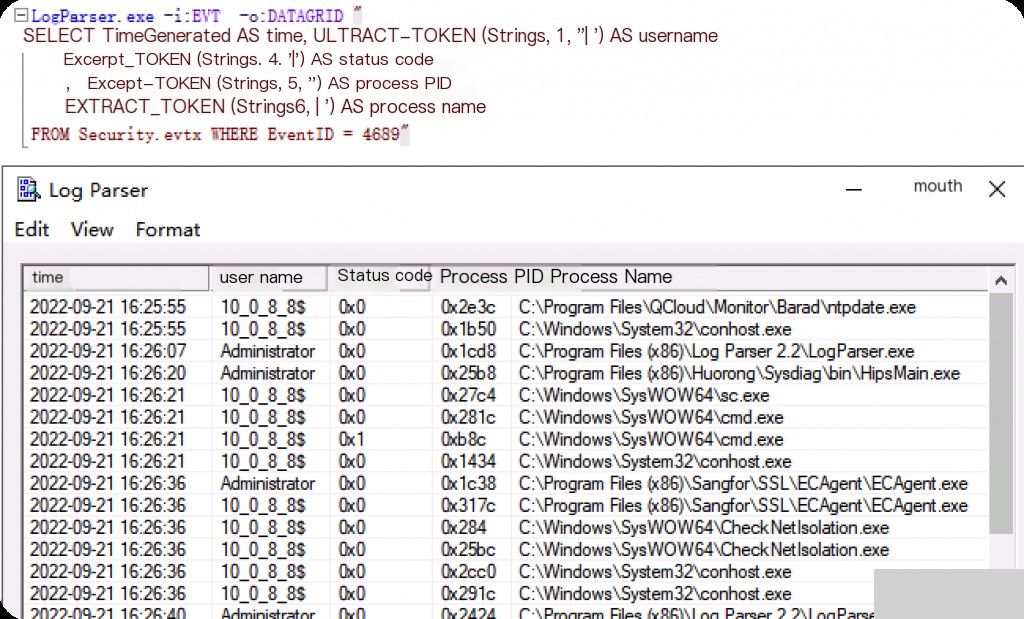
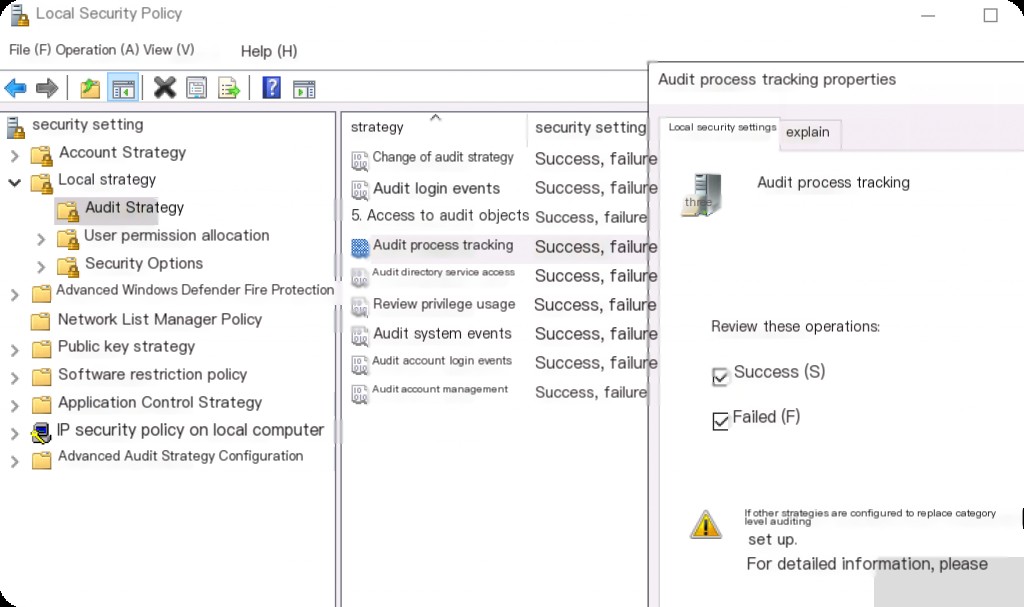
How to Enable CMD Command Audit Policy?
Running secpol.msc opens the Local Security Policy. Navigate to Local Policies -> Audit Policy. By default, Windows does not enable audit policies. If the policy is not enabled, Windows will not record certain events, such as process creation events. You need to manually modify the properties of each audit policy and select both success and failure audit operations.
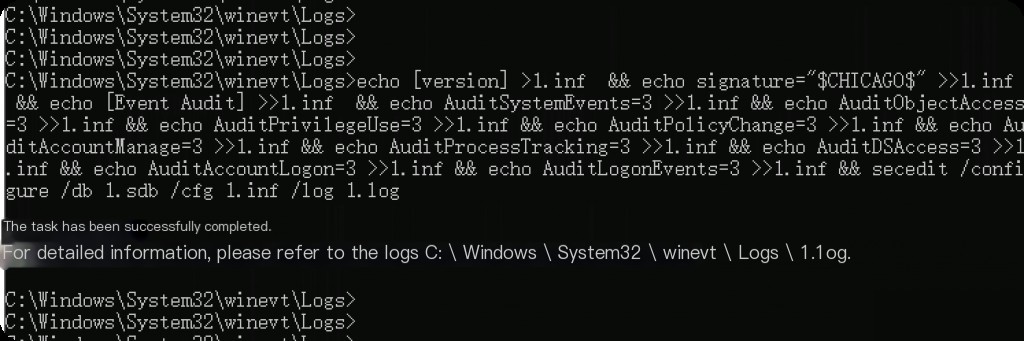
Alternatively, you can enable it with a single command using an administrator CMD.
echo [version] > 1.inf && echo signature="$CHICAGO$" >> 1.inf && echo [Event Audit] >> 1.inf && echo AuditSystemEvents=3 >> 1.inf && echo AuditObjectAccess=3 >> 1.inf && echo AuditPrivilegeUse=3 >> 1.inf && echo AuditPolicyChange=3 >> 1.inf && echo AuditAccountManage=3 >> 1.inf && echo AuditProcessTracking=3 >> 1.inf && echo AuditDSAccess=3 >> 1.inf && echo AuditAccountLogon=3 >> 1.inf && echo AuditLogonEvents=3 >> 1.inf && secedit /configure /db 1.sdb /cfg 1.inf /log 1.log
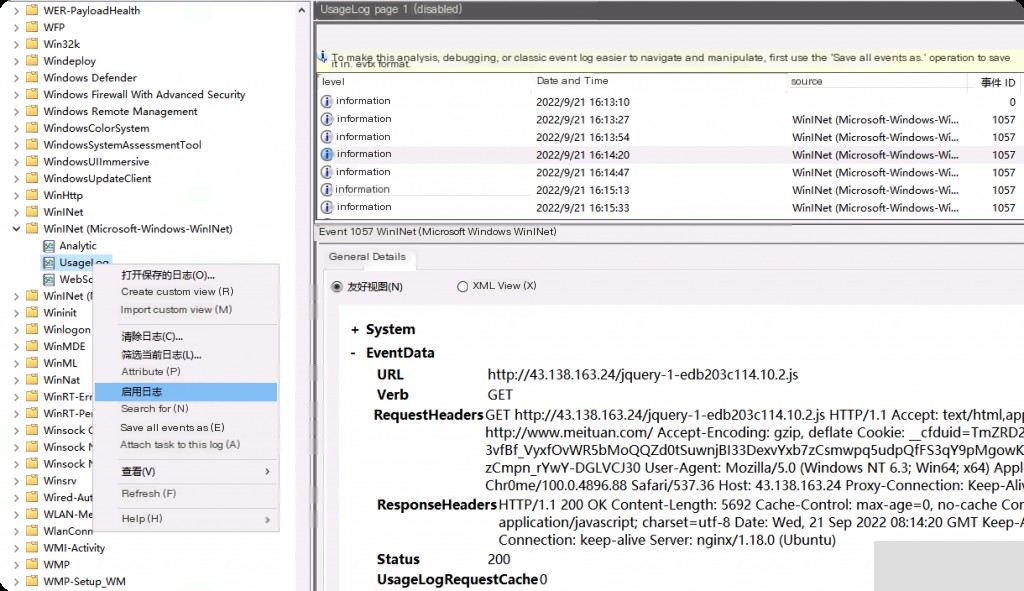
Network Request Records
Event ID: 1057 WinINet Network Request Records
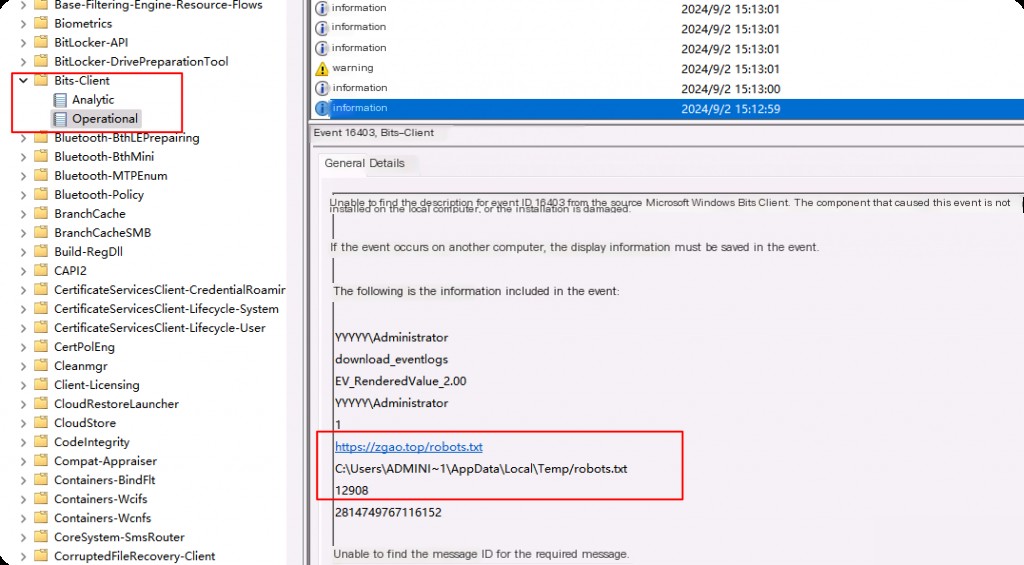
This log is disabled by default and needs to be enabled in advance. It is very useful for capturing C2 traffic, those who know, know.
Application and Services Logs -> Microsoft -> Windows -> WinINet (Microsoft-Windows-WinINet), right-click to start Microsoft-Windows-WinINet/UsageLog log.
 cs beacon callback to C2 request record
cs beacon callback to C2 request record
It can also be enabled via command line.
wevtutil gl "Microsoft-Windows-WinINet/UsageLog" wevtutil sl /e /q "Microsoft-Windows-WinINet/UsageLog"
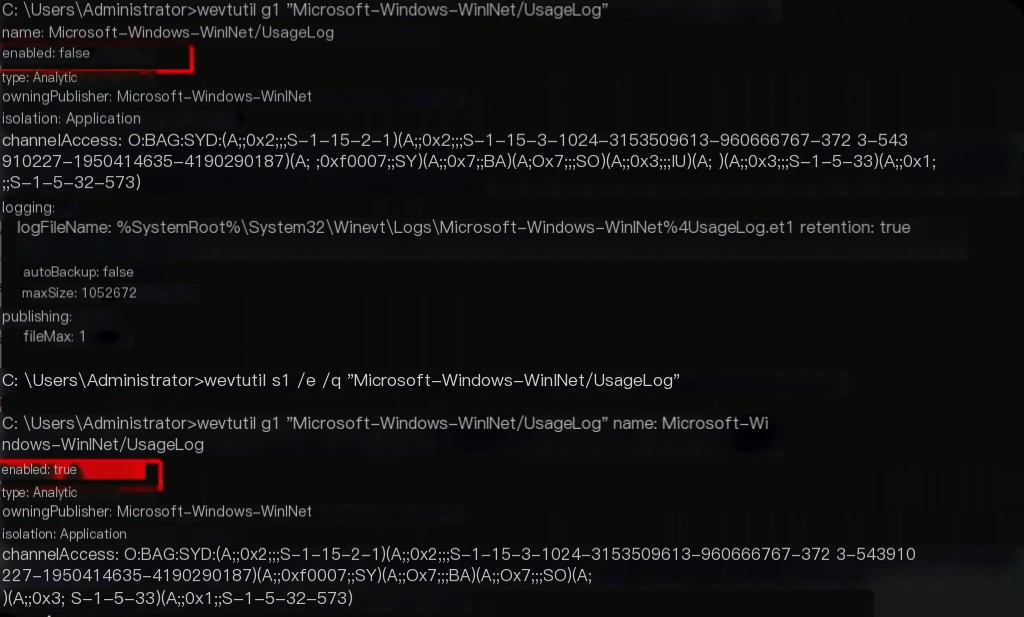
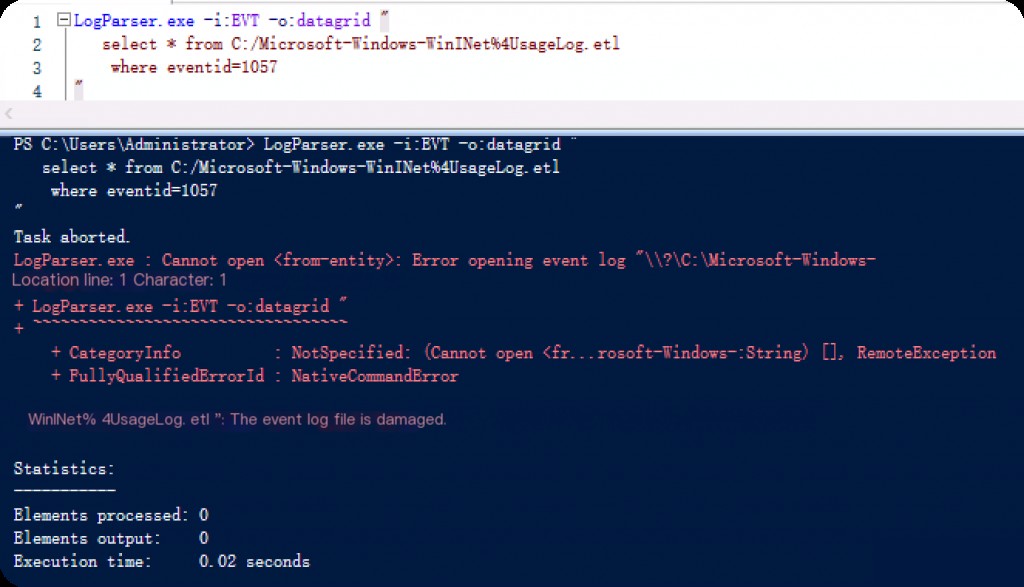
Since the log is in etl format, logparser cannot parse it.
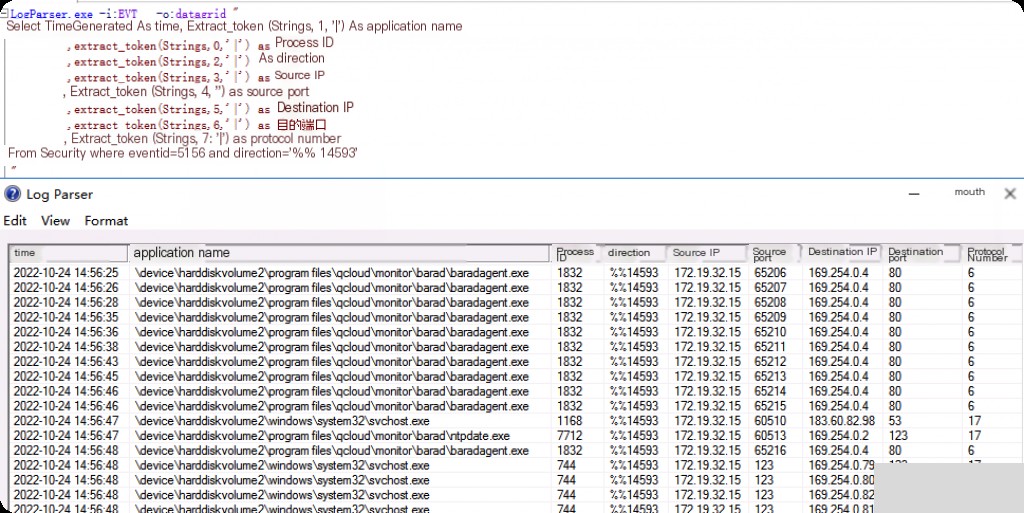
Event ID: 5156 External to Internal Network Connection
The 5156 event also needs to be enabled in advance, in the same way as 4688.
LogParser.exe -i:EVT -o:datagrid "
select TimeGenerated As Time, extract_token(Strings,1,'|') As ApplicationName
,extract_token(Strings,0,'|') as ProcessID
,extract_token(Strings,2,'|') as Direction
,extract_token(Strings,3,'|') as SourceIP
,extract_token(Strings,4,'|') as SourcePort
,extract_token(Strings,5,'|') as DestinationIP
,extract_token(Strings,6,'|') as DestinationPort
,extract_token(Strings,7,'|') as ProtocolNumber
from Security where eventid=5156 and Direction='%%14593'
"
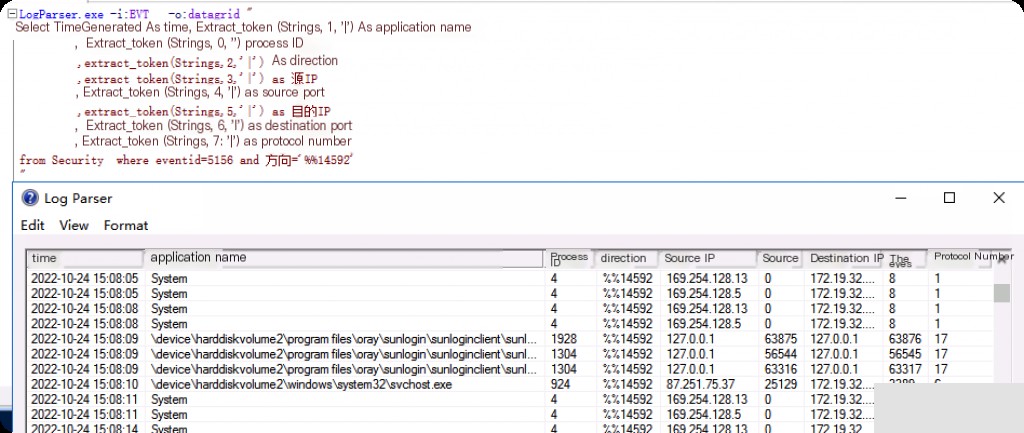
Event ID: 5156 Internal to External Network Connection
LogParser.exe -i:EVT -o:datagrid "
select TimeGenerated As Time, extract_token(Strings,1,'|') As ApplicationName
,extract_token(Strings,0,'|') as ProcessID
,extract_token(Strings,2,'|') as Direction
,extract_token(Strings,3,'|') as SourceIP
,extract_token(Strings,4,'|') as SourcePort
,extract_token(Strings,5,'|') as DestinationIP
,extract_token(Strings,6,'|') as DestinationPort
,extract_token(Strings,7,'|') as ProtocolNumber
from Security where eventid=5156 and Direction='%%14592'
"
Privileged Calls
This type of event ID only occurs on domain hosts.
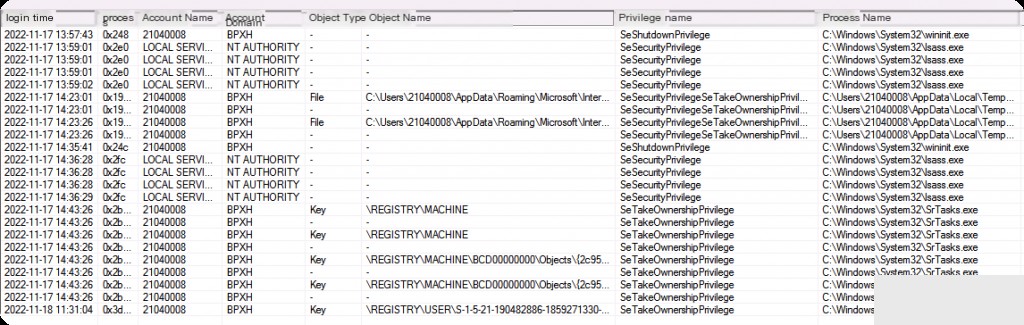
Event ID: 4673 Privileged Service Called
LogParser.exe -i:evt -o:datagrid " SELECT TimeGenerated AS LoginTime, EXTRACT_TOKEN(Strings, -2, '|') AS ProcessPID, EXTRACT_TOKEN(Strings, 1, '|') AS AccountName, EXTRACT_TOKEN(Strings, 2, '|') AS AccountDomain, EXTRACT_TOKEN(Strings, -3, '|') AS PrivilegeName, EXTRACT_TOKEN(Strings, -1, '|') AS ProcessName FROM Security.evtx WHERE EventID = 4673 "
For more information on the privilege name, refer to: https://learn.microsoft.com/zh-cn/windows/security/threat-protection/auditing/event-4673
Event ID: 4674 Attempt to Perform Operation on a Privileged Object
LogParser.exe -i:evt -o:datagrid " SELECT TimeGenerated AS LoginTime, EXTRACT_TOKEN(Strings, -2, '|') AS ProcessPID, EXTRACT_TOKEN(Strings, 1, '|') AS AccountName, EXTRACT_TOKEN(Strings, 2, '|') AS AccountDomain, EXTRACT_TOKEN(Strings, 5, '|') AS ObjectType, EXTRACT_TOKEN(Strings, 6, '|') AS ObjectName, EXTRACT_TOKEN(Strings, -3, '|') AS PrivilegeName, EXTRACT_TOKEN(Strings, -1, '|') AS ProcessName FROM Security.evtx WHERE EventID = 4674 "
Application Remote Login
Log file name: Application.evtx
MSSQL Remote Login
Event ID: 18456 Login Failed
logparser.exe -i:evt -o:datagrid "
SELECT TimeGenerated AS Time, SourceName AS Source, ComputerName AS ComputerName
, EXTRACT_TOKEN(Strings, 0, '|') AS LoginName
, EXTRACT_TOKEN(Strings, 1, '|') AS Reason
, EXTRACT_TOKEN(Strings, 2, '|') AS SourceIP
FROM Application.evtx
WHERE EventID = 18456
"
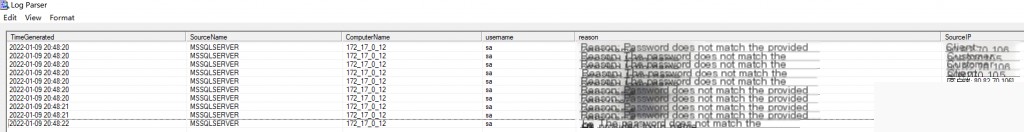
Event ID: 18454 Login Successful
logparser.exe -i:evt -o:datagrid " select TimeGenerated as Time ,SourceName as Source ,ComputerName as ComputerName ,EXTRACT_TOKEN(Strings,0,'|') as username as LoginName ,EXTRACT_TOKEN(Strings,1,'|') as Reason ,EXTRACT_TOKEN(Strings,2,'|') as SourceIP from Application.evtx where EventID=18454 "
Event ID: 15457 xp_cmdshell Enable Information
logparser.exe -i:evt -o:datagrid "
SELECT TimeGenerated AS Time, SourceName AS Source, ComputerName AS ComputerName
, EXTRACT_TOKEN(Strings, 0, '|') AS Method
, EXTRACT_TOKEN(Strings, 1, '|') AS Status1
, EXTRACT_TOKEN(Strings, 2, '|') AS Status2
FROM Application.evtx
WHERE EventID = 15457
AND Method = 'xp_cmdshell'
"
System Service Records
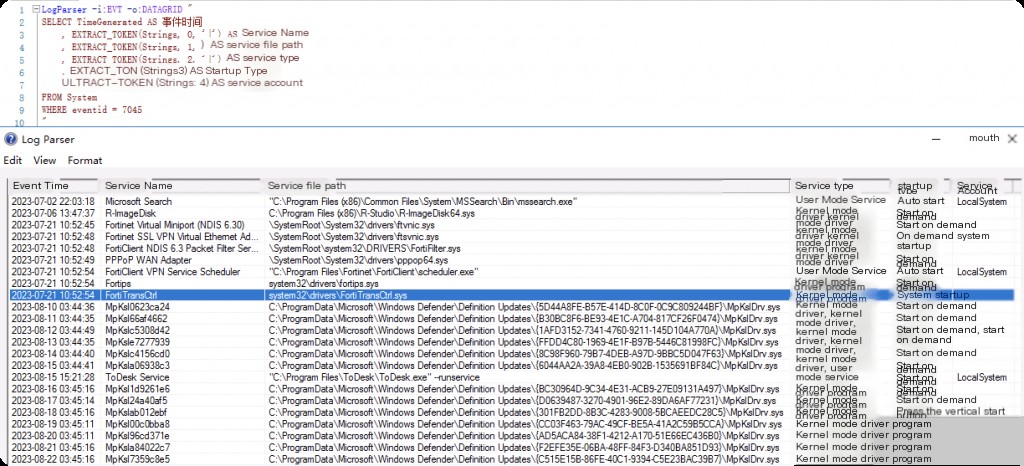
Event ID: 7045 Service Created Successfully
In cs, jump psexec_psh is often used to create and start temporary services to execute commands. The 7045 event log contains the name, path, and startup parameters of the new service, which can be used for further analysis and confirmation of malicious activity.
Note that this event is located in the system log, not the security log.
LogParser -i:EVT -o:DATAGRID "
SELECT TimeGenerated AS EventTime
, EXTRACT_TOKEN(Strings, 0, '|') AS ServiceName
, EXTRACT_TOKEN(Strings, 1, '|') AS ServiceFilePath
, EXTRACT_TOKEN(Strings, 2, '|') AS ServiceType
, EXTRACT_TOKEN(Strings, 3, '|') AS StartupType
, EXTRACT_TOKEN(Strings, 4, '|') AS ServiceAccount
FROM System
WHERE eventid = 7045
"
Kerberos Authentication Records
Event ID: 4768 Credential Ticket Request (TGT Request)
Event ID 4768 indicates a Kerberos Ticket Granting Ticket (TGT) request event issued by the Kerberos authentication service. This event is recorded when a user logs in, showing the details of the user’s request for a Kerberos TGT.
Note: This event is generated each time the Key Distribution Center issues a Kerberos Ticket Granting Ticket (TGT). This event is only generated on domain controllers.
LogParser -i:EVT -o:DATAGRID "
SELECT TimeGenerated AS EventTime
, EXTRACT_TOKEN(Strings, 0, '|') AS Username
, EXTRACT_TOKEN(Strings, 1, '|') AS TargetDomainName
, EXTRACT_TOKEN(Strings, 3, '|') AS ServiceName
, EXTRACT_TOKEN(Strings, 6, '|') AS Status
, EXTRACT_TOKEN(Strings, 7, '|') AS EncryptionType
, EXTRACT_TOKEN(Strings, 8, '|') AS PreAuthenticationType
, EXTRACT_TOKEN(Strings, 9, '|') AS IPAddress
, EXTRACT_TOKEN(Strings, 10, '|') AS IPPort
FROM Security
WHERE eventid = 4768
"
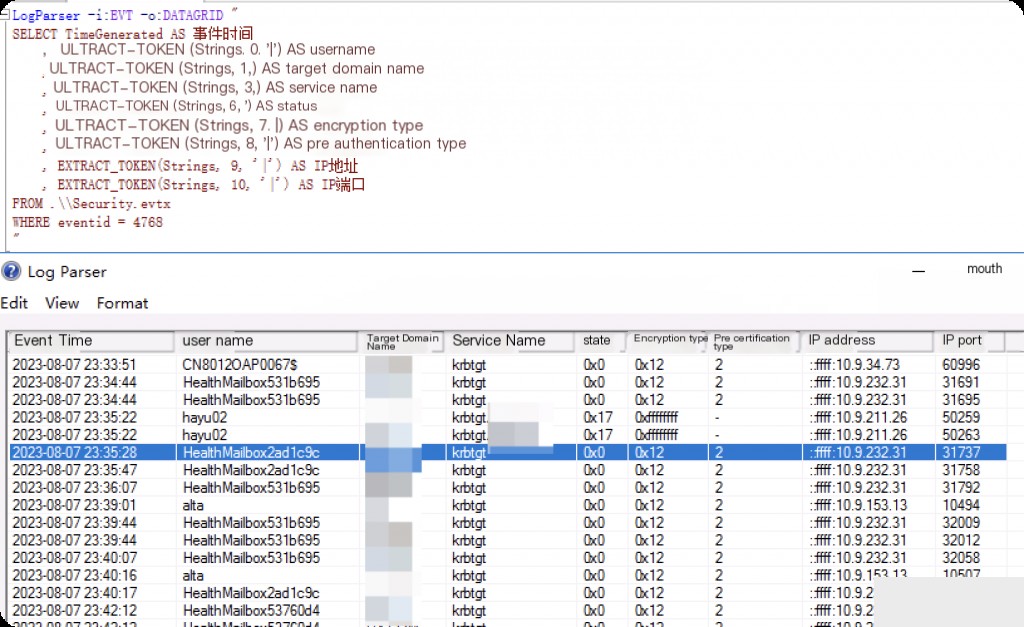
If TGT authentication fails, a Failure event will be seen with a status code other than “0x0”. Event ID 4798 will not generate status codes 0x10 and 0x18, but will generate the event “4771: Kerberos Pre-Authentication Failed”.
Event ID: 4771 Pre-Authentication Failed
This event is generated each time a TGT request fails (e.g., due to incorrect or expired password). It is recorded only on domain controllers and only for failure events.
LogParser -i:EVT -o:DATAGRID "
SELECT TimeGenerated AS Event Time
, EXTRACT_TOKEN(Strings, 0, '|') AS Target Username
, EXTRACT_TOKEN(Strings, 2, '|') AS Service Name
, EXTRACT_TOKEN(Strings, 4, '|') AS Status
, EXTRACT_TOKEN(Strings, 5, '|') AS Pre-Authentication Type
, EXTRACT_TOKEN(Strings, 6, '|') AS IP Address
, EXTRACT_TOKEN(Strings, 7, '|') AS IP Port
FROM Security
WHERE eventid = 4771
"
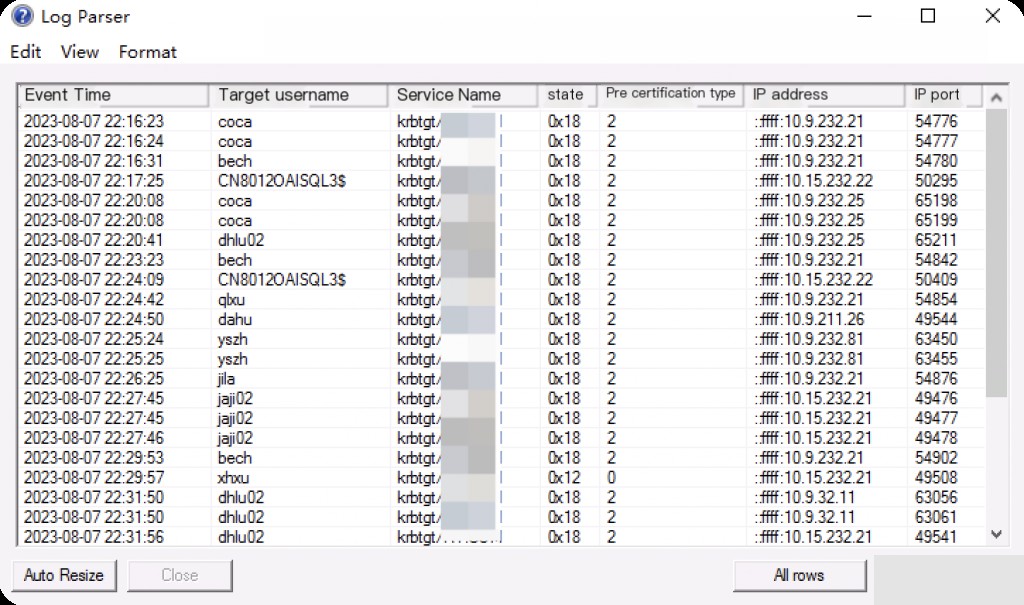
Event ID: 4770 Service Ticket Renewed
Event ID 4770 records the renewal of a Kerberos service ticket. This means that a user has requested to renew their Kerberos service ticket to continue accessing a specific service.
LogParser -i:EVT -o:DATAGRID "
SELECT TimeGenerated AS Event Time
, EXTRACT_TOKEN(Strings, 0, '|') AS Target Username
, EXTRACT_TOKEN(Strings, 1, '|') AS Target Domain
, EXTRACT_TOKEN(Strings, 2, '|') AS Service Name
, EXTRACT_TOKEN(Strings, 4, '|') AS Ticket Options
, EXTRACT_TOKEN(Strings, 5, '|') AS Encryption Type
, EXTRACT_TOKEN(Strings, 6, '|') AS IP Address
, EXTRACT_TOKEN(Strings, 7, '|') AS IP Port
FROM Security
WHERE eventid = 4770
"
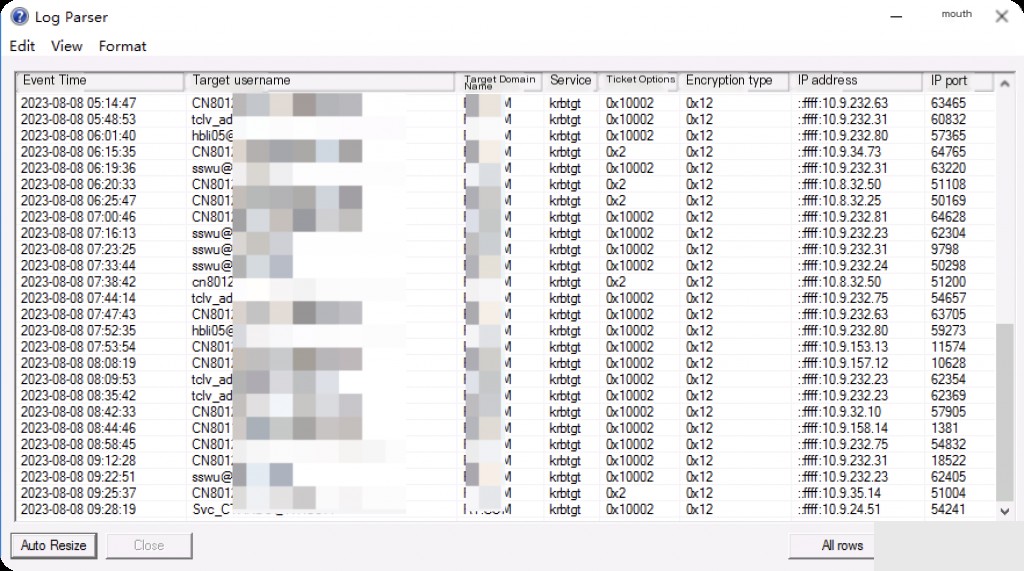
Event ID: 4769 Ticket Granted (TGT)
This event is generated each time a user requests access to network resources, leading the Key Distribution Center (KDC) to obtain a Kerberos Ticket Granting Service (TGS) ticket request for authentication. It is only recorded on domain controllers.
Difference between 4768 and 4769:
- Event 4768: The user requests a TGT from the Kerberos authentication service. A successful request (status 0x0) means the user has successfully obtained a TGT, but this does not necessarily mean a 4769 event will follow.
- Event 4769: After successfully obtaining a TGT, when the user attempts to access a specific service, the Kerberos authentication service generates a service ticket and records event 4769.
Therefore, after a successful 4768, a user may generate a 4769 event, depending on whether the user continues to request a ticket for a specific service.
LogParser -i:EVT -o:DATAGRID "
SELECT TimeGenerated AS Event Time
, EXTRACT_TOKEN(Strings, 0, '|') AS Target Username
, EXTRACT_TOKEN(Strings, 1, '|') AS Target Domain
, EXTRACT_TOKEN(Strings, 2, '|') AS Service Name
, EXTRACT_TOKEN(Strings, 5, '|') AS Encryption Type
, EXTRACT_TOKEN(Strings, 6, '|') AS IP Address
, EXTRACT_TOKEN(Strings, 7, '|') AS Port
, EXTRACT_TOKEN(Strings, 8, '|') AS Status
FROM Security
WHERE eventid = 4769
"
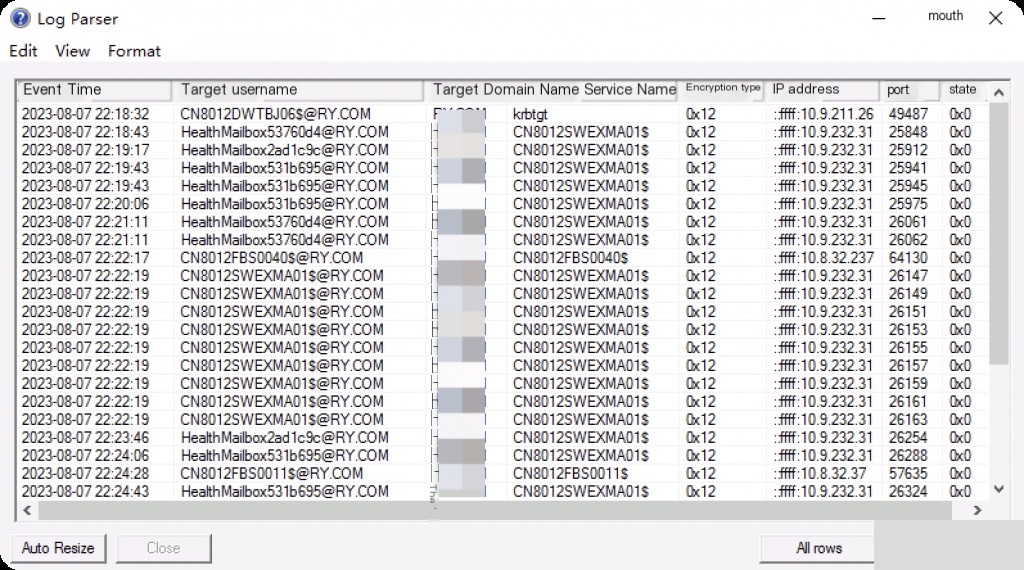
Token Privilege Changes
Event ID: 4703 Token Privileges Adjusted
Event ID 4703 is used to record changes to user privileges. It logs which privileges a process has enabled or disabled, such as the ability to back up files, shut down the system, load and unload device drivers, etc.
LogParser -i:EVT -o:DATAGRID "
SELECT TimeGenerated AS Event Time
, EXTRACT_TOKEN(Strings, 1, '|') AS Username
, EXTRACT_TOKEN(Strings, 2, '|') AS User Domain
, EXTRACT_TOKEN(Strings, 5, '|') AS Target Username
, EXTRACT_TOKEN(Strings, 6, '|') AS Target Domain
, EXTRACT_TOKEN(Strings, 8, '|') AS Process Name
, EXTRACT_TOKEN(Strings, 9, '|') AS Process ID
, EXTRACT_TOKEN(Strings, 10, '|') AS Enabled Privileges List
, EXTRACT_TOKEN(Strings, 11, '|') AS Disabled Privileges List
FROM Security
WHERE eventid = 4703
"
Object Access
Event ID: 4658 Object Handle Closed
Event 4658 is logged when an object handle is closed. This object can be of any type — file system, kernel, registry object, or file system object stored on a removable device. This event is only logged if “Success” auditing is enabled in the “Audit Handle Manipulation” subcategory.
LogParser -i:EVT -o:DATAGRID "
SELECT TimeGenerated AS Event Time
, EXTRACT_TOKEN(Strings, 1, '|') AS Username
, EXTRACT_TOKEN(Strings, 2, '|') AS User Domain
, EXTRACT_TOKEN(Strings, 4, '|') AS Object Server
, EXTRACT_TOKEN(Strings, 5, '|') AS Handle ID
, EXTRACT_TOKEN(Strings, 6, '|') AS Process ID
, EXTRACT_TOKEN(Strings, 7, '|') AS Process Name
FROM Security
WHERE eventid = 4658
"
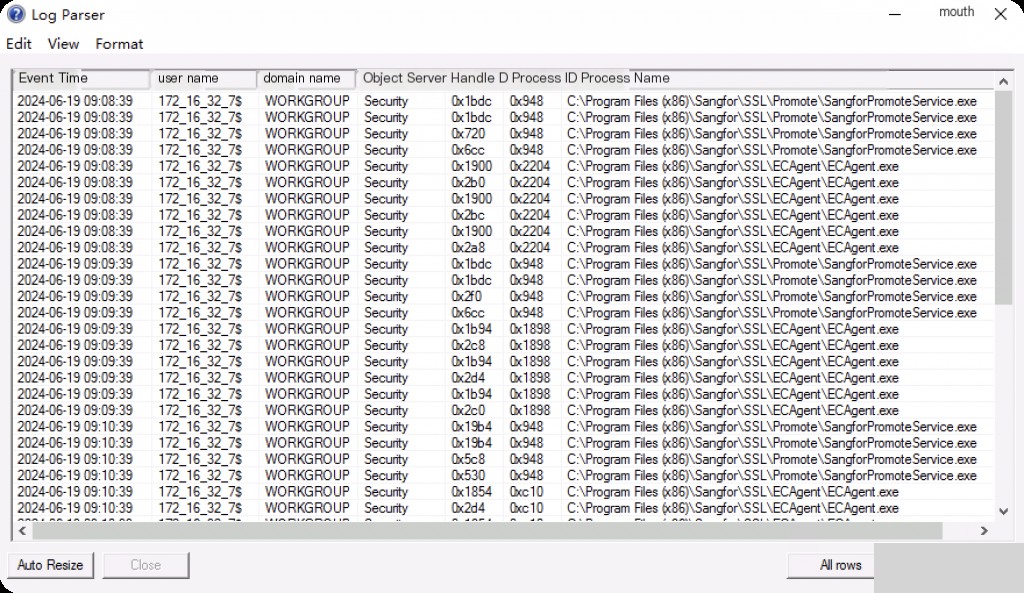
Event ID: 4656 Request Object Handle
Event ID 4656 is logged when a request is made to access a specific object. The requested object can be of any type — file system, kernel, registry object, or file system object stored on a removable device.
If access is denied, it is logged as a failure audit. This event shows the result of the access request (recorded by 4663).
LogParser -i:EVT -o:DATAGRID "
SELECT TimeGenerated AS Event Time
, EXTRACT_TOKEN(Strings, 1, '|') AS Username
, EXTRACT_TOKEN(Strings, 2, '|') AS User Domain
, EXTRACT_TOKEN(Strings, 4, '|') AS Object Server
, EXTRACT_TOKEN(Strings, 5, '|') AS Object Type
, EXTRACT_TOKEN(Strings, 6, '|') AS Object Name
, EXTRACT_TOKEN(Strings, 7, '|') AS Handle ID
, EXTRACT_TOKEN(Strings, 9, '|') AS Access List
, EXTRACT_TOKEN(Strings, 14, '|') AS Process ID
, EXTRACT_TOKEN(Strings, 15, '|') AS Process Name
FROM Security
WHERE eventid = 4656
"
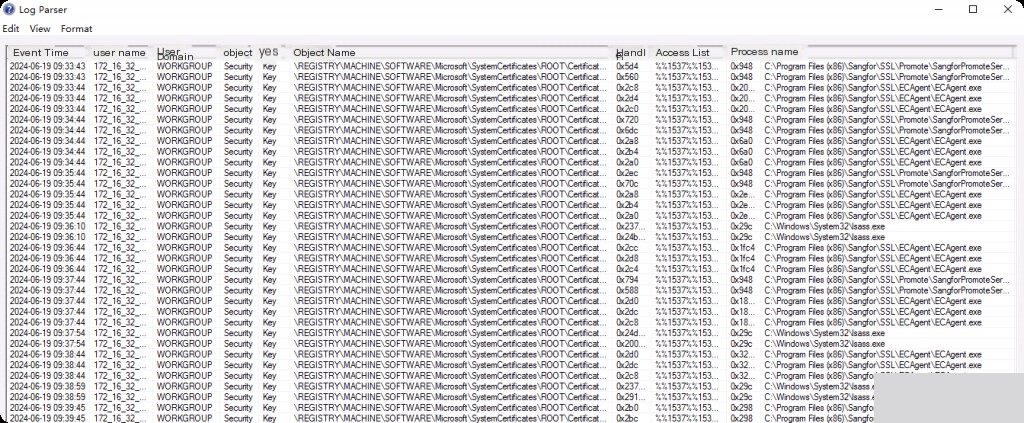
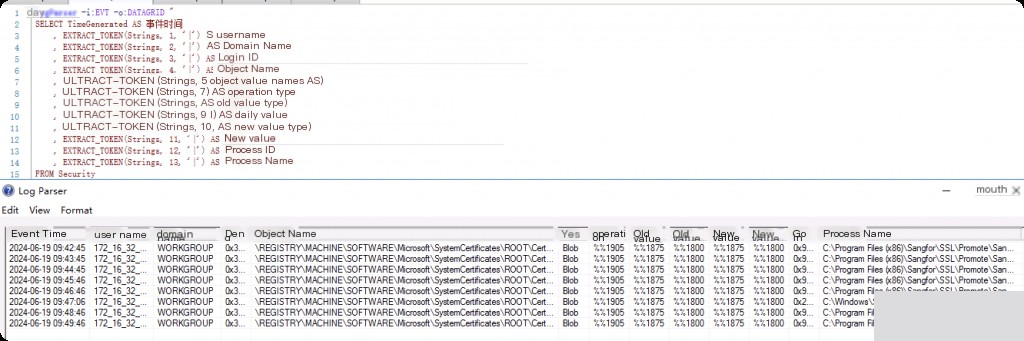
Event ID: 4657 Registry Value Modified
Event ID 4657 is logged if a registry key value is modified. Note that this event is only triggered when a key value (not the key itself) is modified. Additionally, this event is only logged if auditing is enabled in the SACL of the registry key.
LogParser -i:EVT -o:DATAGRID "
SELECT TimeGenerated AS Event Time
, EXTRACT_TOKEN(Strings, 1, '|') AS Username
, EXTRACT_TOKEN(Strings, 2, '|') AS User Domain
, EXTRACT_TOKEN(Strings, 3, '|') AS Logon ID
, EXTRACT_TOKEN(Strings, 4, '|') AS Object Name
, EXTRACT_TOKEN(Strings, 5, '|') AS Object Value Name
, EXTRACT_TOKEN(Strings, 7, '|') AS Operation Type
, EXTRACT_TOKEN(Strings, 8, '|') AS Old Value Type
, EXTRACT_TOKEN(Strings, 9, '|') AS Old Value
, EXTRACT_TOKEN(Strings, 10, '|') AS New Value Type
, EXTRACT_TOKEN(Strings, 11, '|') AS New Value
, EXTRACT_TOKEN(Strings, 12, '|') AS Process ID
, EXTRACT_TOKEN(Strings, 13, '|') AS Process Name
FROM Security
WHERE eventid = 4657
"
 Post Views: 3,301 Appreciation
Post Views: 3,301 Appreciation


