I. Overview of Snort
Snort is a powerful network intrusion detection/prevention system (NIDS/NIPS) with features such as cross-platform compatibility, real-time traffic analysis, and network IP packet logging.
1. Operating Modes
Snort has three operating modes: sniffer, packet logger, and network intrusion detection system.
1. Sniffer: The sniffer mode simply reads packets from the network and displays them continuously on the terminal.
2. Packet Logger: The packet logger mode records packets to the hard drive.
3. Network Intrusion Detection: The network intrusion detection mode is the most complex and configurable. It allows Snort to analyze network traffic to match user-defined rules and take actions based on the detection results.
When using Snort, the network card will automatically be set to promiscuous mode.
II. Snort Installation and Download
For 32-bit systems, you must install WinpCap when using Snort.
Snort download link: https://www.snort.org/downloads#snort-downloads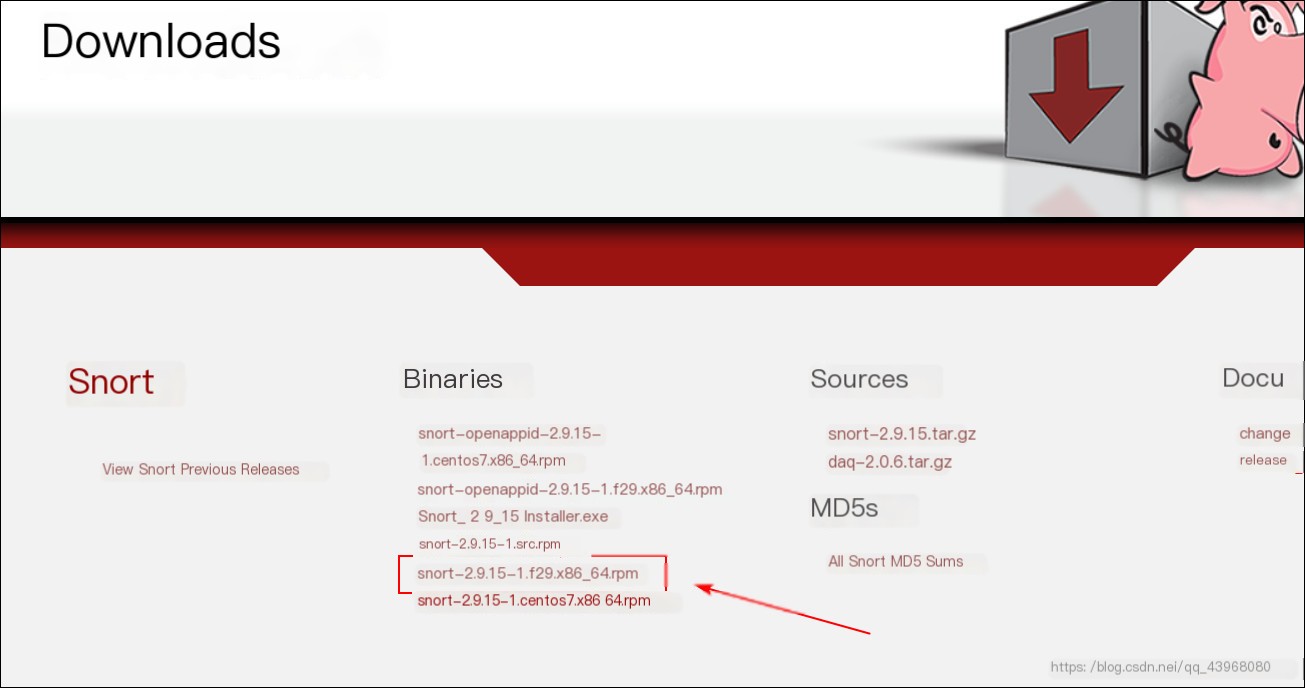
WinpCap download link: https://www.winpcap.org/install/default.htm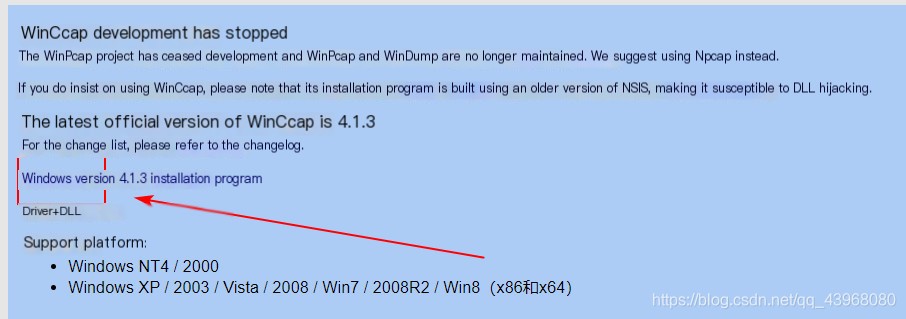
Simply install it (for convenience in future experiments, it is strongly recommended to install it in the root directory of the C drive).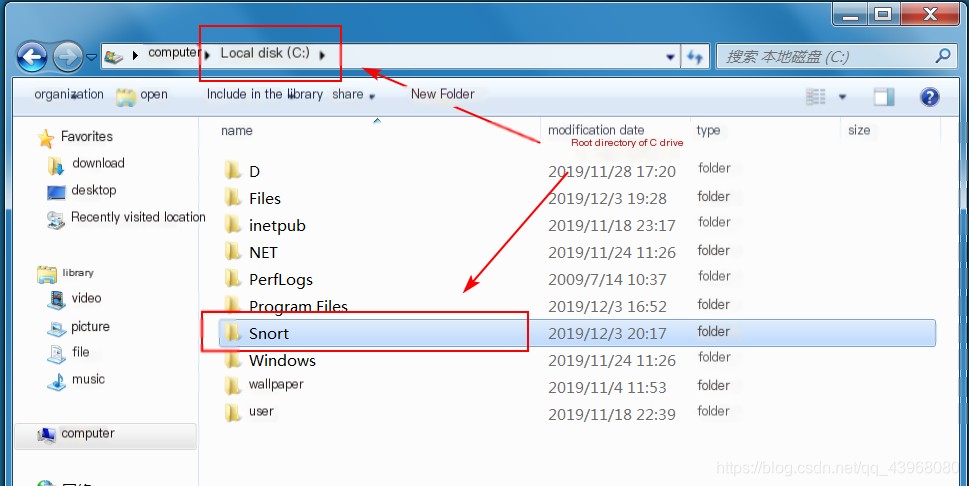
III. Sniffing and Data Logging
1. Sniffing
Open cmd in the bin directory of Snort.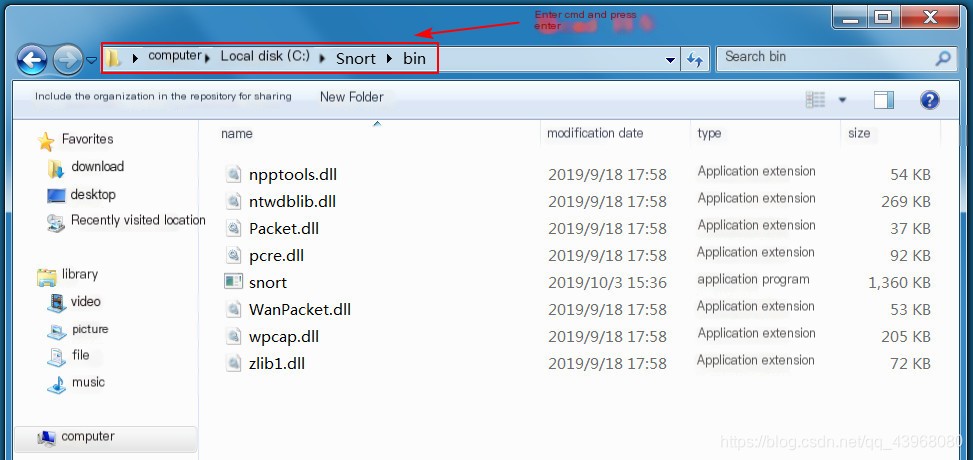
Enter snort -W to view the current network interfaces.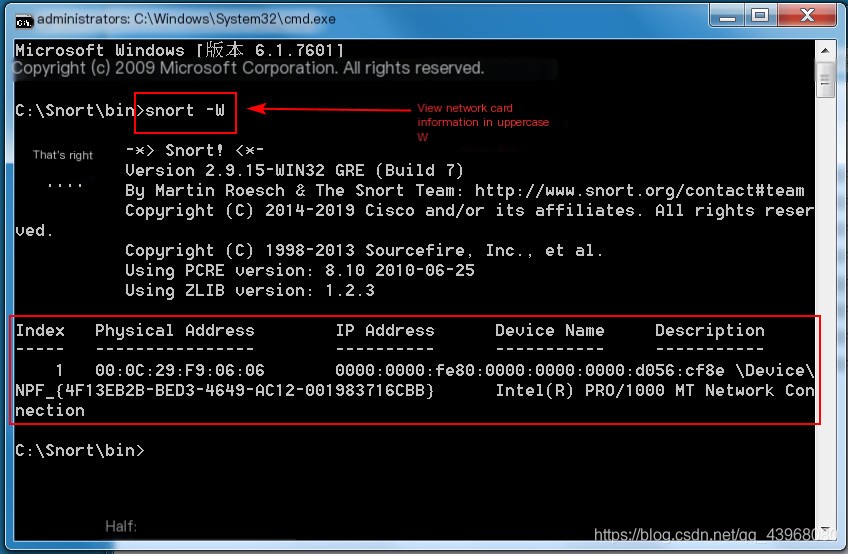
Sniff network interface 1: Snort -v -i1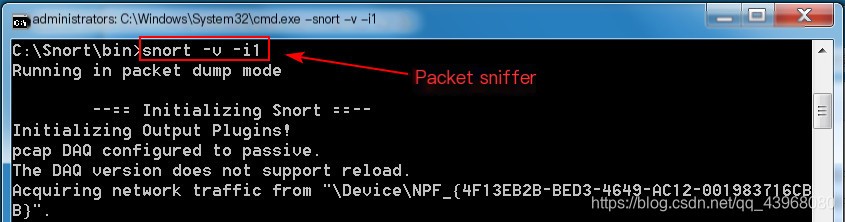
Use another host to ping this host.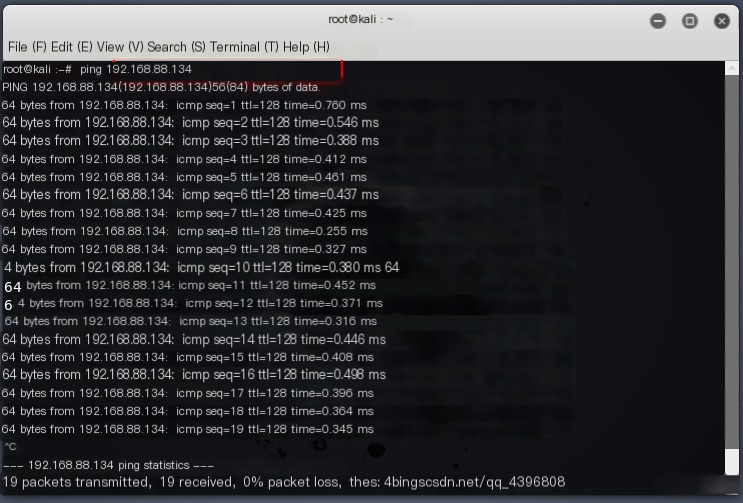
Packets are displayed.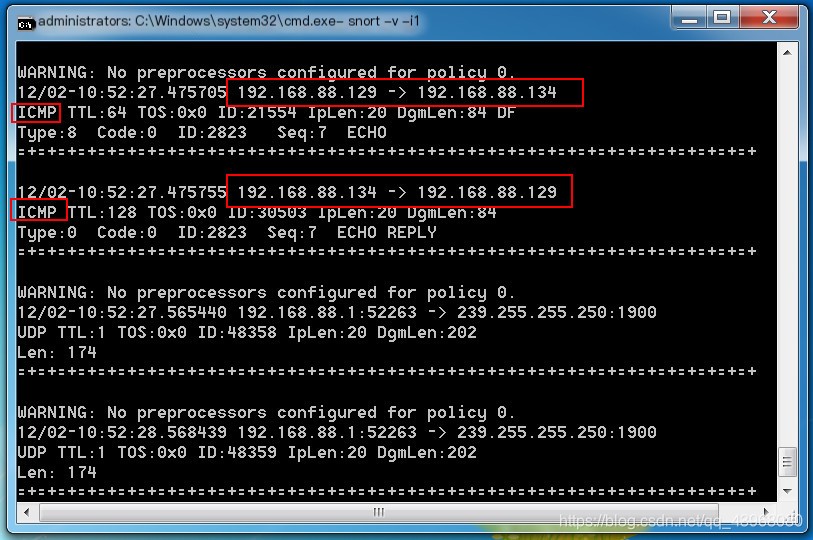
After pressing ctrl + c to terminate, you can view packet analysis.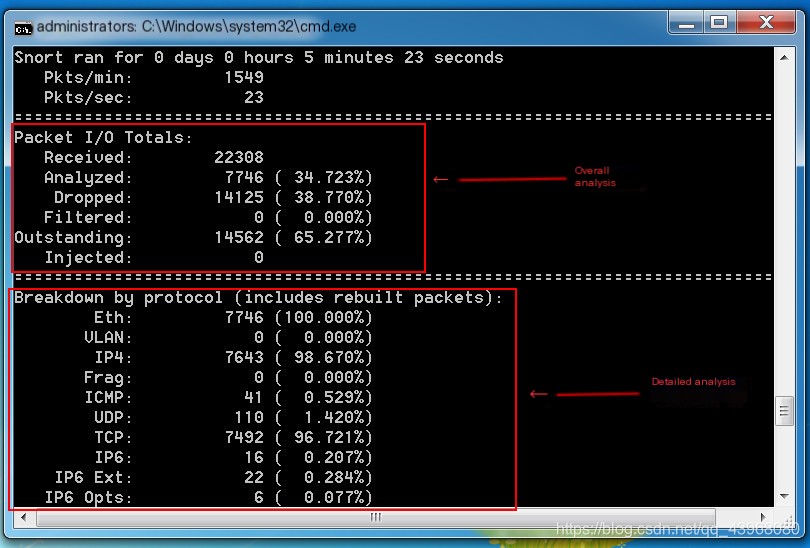
2. Packet Logging
By default, there is a log folder in the Snort directory where logs can be directly saved.
Use Snort -dve -i1 -h 192.168.88.0/24 -l c:\Snort\log -K ascii to log packets. The parameters are as follows:
-dve: Enables detailed sniffing mode.
-h: Specifies the monitored host segment. If not specified, it defaults to the local machine’s IP.
-l: Specifies the log directory where the content will be stored.
-K: Specifies the character set, storing data in ASCII format.
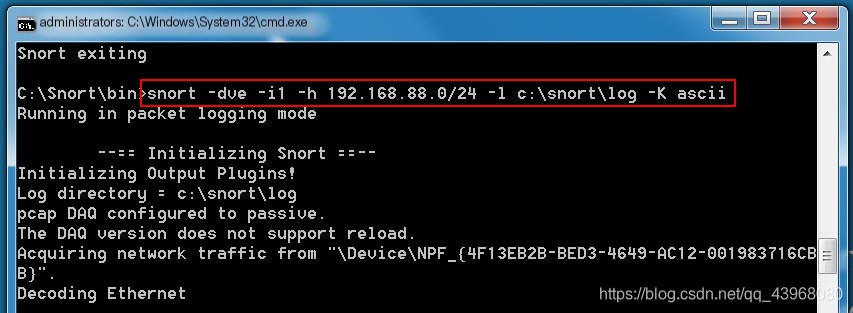
Access any webpage, and packet capture results will appear.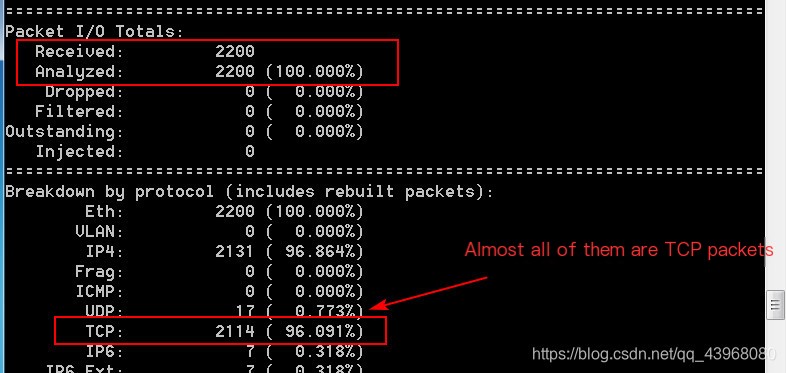
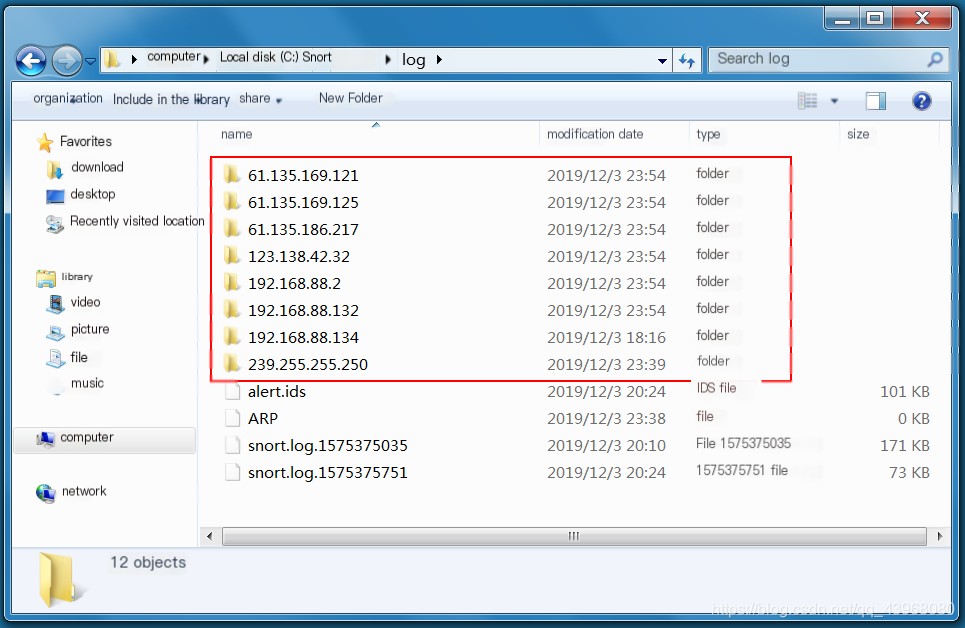
View the file content, which contains packet headers.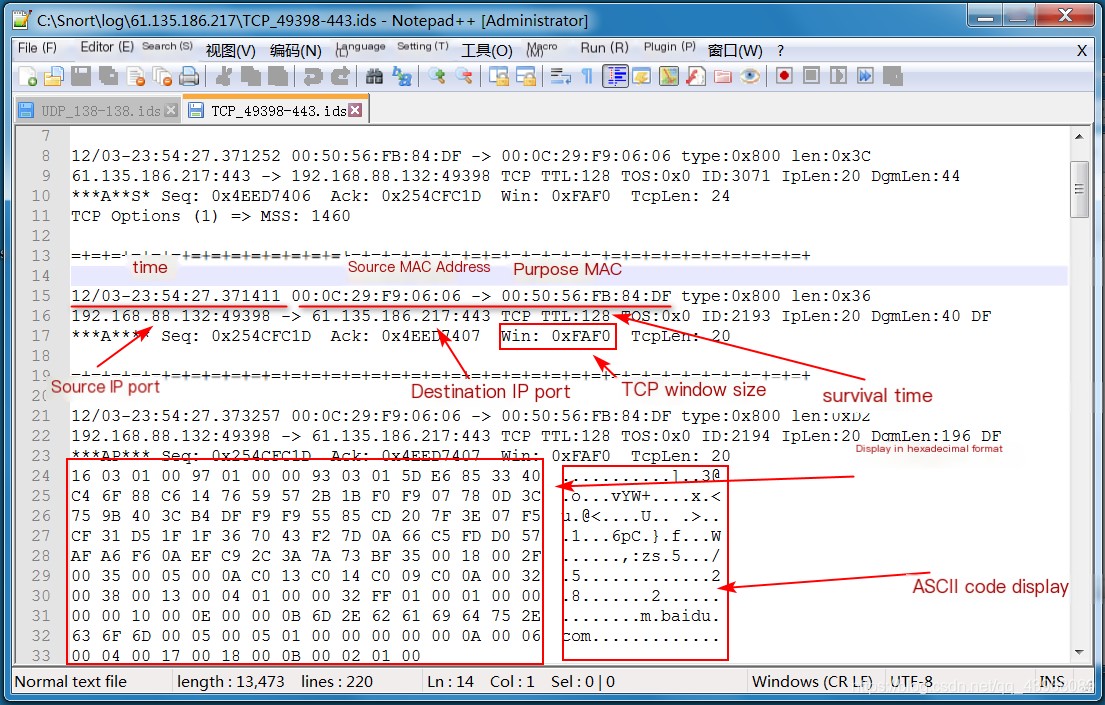 Link:Using Snort Part 2: Intrusion Detection
Link:Using Snort Part 2: Intrusion Detection


