Recently, I discovered a very useful shell script obfuscation tool called Bashfuscator. Due to work requirements, I often write shell scripts, but the plain text content is easily “borrowed” by others.
Execute the following command to achieve one-click obfuscation, compilation, and encryption of shell scripts.
bashfuscator -s 1 -t 1 --layers 1 --no-file-write -f test.sh -o output.sh && shc shc -v -U -r -f output.sh && gzexe output.sh.x
 Shell Script Obfuscation, Compilation, and Encryption
Shell Script Obfuscation, Compilation, and Encryption
What is Bashfuscator?
Bashfuscator is a modular and extensible Bash obfuscation framework written in Python 3. It provides many different methods to make Bash one-liners or scripts harder to understand. It achieves this by generating complex, random Bash code that evaluates the original input and executes it at runtime. Bashfuscator makes it easy to generate highly obfuscated Bash commands and scripts, whether from the command line or as a Python library.
Project Address: Bashfuscator
https://github.com/Bashfuscator/Bashfuscator
https://bashfuscator.readthedocs.io
How to Install?
git clone https://github.com/Bashfuscator/Bashfuscator cd Bashfuscator python3 setup.py install --user
Tool Usage: Bashfuscator
Program Options for Bashfuscator
Program Options: -l, --list List all available obfuscators, compressors, and encoders -c COMMAND, --command COMMAND Obfuscate command -f FILE, --file FILE Name of the script to obfuscate --stdin Obfuscate standard input -o OUTPUT FILE, --outfile OUTPUT FILE File to write the payload to -q, --quiet Only print the payload --clip Copy the payload to the clipboard --test Test the payload after running, incompatible with -q
Obfuscation Options
Obfuscation Options:
-s {1,2,3}, --payload-size {1,2,3} Desired payload size. Default: 2
-t {1,2,3}, --execution-time {1,2,3} Desired speed of the payload. Default: 2
--layers LAYERS Number of obfuscation layers to apply, default: 2. Defaults to 1 when using --choose-mutators
--include-binaries BINARY [BINARY ...] Use payload in generated binaries
--exclude-binaries BINARY [BINARY ...] Do not use payload in generated binaries
--no-file-write Do not use obfuscators that require writing to files
--write-dir WRITE_DIR If Mutators need to write to a directory or create files
Obfuscate One-liner Command or Single File
Use the -c parameter to obfuscate a one-liner command.
$ bashfuscator -c "cat /etc/passwd"
[+] Mutators used: Token/ForCode -> Command/Reverse
[+] Payload:
${@/l+Jau/+<b=k } p''"r"i""n
Use the -f parameter to obfuscate a single shell script, -o generates the obfuscated shell script.
[root@zgao tmp]# bashfuscator -f test.sh -o outptu.sh
[+] Mutators used: String/Hex Hash
[+] Payload written to outptu.sh
[+] Payload:
${*//=q} ${*%Me}pr"${@##*^}"i${*,}n\tf %s "$( "${@~~}" pri"n"t"f" "\x$(""p${*#\`w}r${!
.....
#a)+2#1001)) )))" )" |"${@~~}"bas""
Personally Recommended Usage Parameters
Low Obfuscation Level
No additional file writing in the obfuscated script.
bashfuscator -s 1 -t 1 --layers 1 --no-file-write -f script.sh -o output.sh
Normal Obfuscation
No additional parameters.
bashfuscator -f test.sh -o output.sh
Obfuscation Script Execution Error?
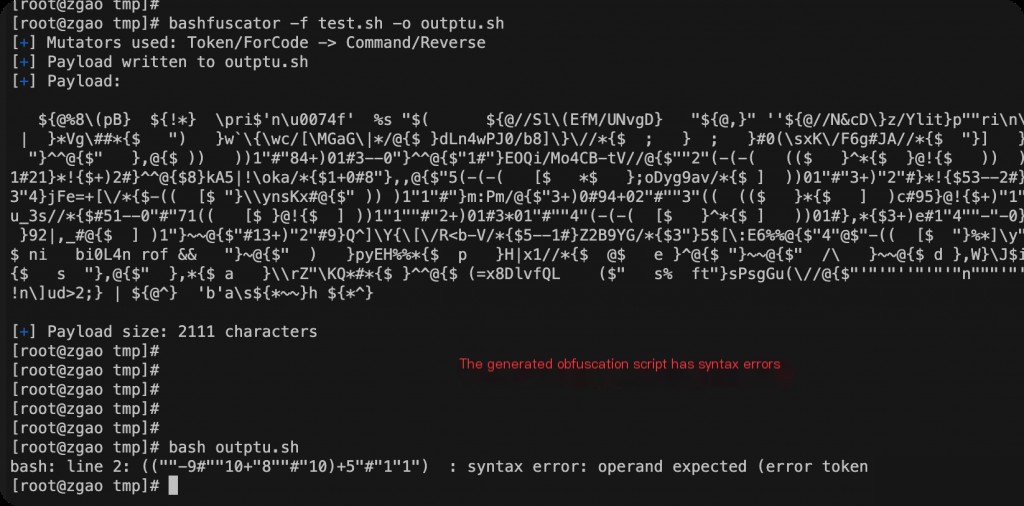
Randomly generated obfuscated scripts may have execution errors, you can test them first.
shc Package Binary Files
shc packages shell scripts into an executable binary file. If you’re still not assured with Bashfuscator, you can compile it again with shc.
The shc tool is not built-in and needs to be installed first.
yum install shc -y
Common shc Options
[root@zgao tmp]# shc -h shc version 4.0.3, Generic Shell Script Compiler shc GNU GPL Version 3 Md Jahidul Hamid <[email protected]> shc Usage: shc [-e date] [-m addr] [-i iopt] [-x cmnd] [-l lopt] [-o outfile] [-rvDSUHCABh] -f script -f %s Script filename to compile -i %s Inline options for the shell interpreter, i.e.: -e -x %s eXec command, as printf format, i.e.: exec('%s',@ARGV); -l %s Last shell option, i.e.: -- -o %s Output filename -r Relax security. Make a redistributable binary -v Verbose compilation -S Enable setuid for root callable programs [OFF] -D Enable debug exec calls [OFF] -U Make binary untraceable [No] -H Harden: Extra security protection [No]
Use the following parameters to compile the shell script into an exe
[root@zgao tmp]# shc -v -U -r -f outptu.sh shc shll=bash shc [-i]=-c shc [-x]=exec '%s' "$@" shc [-l]= shc opts= shc: cc outptu.sh.x.c -o outptu.sh.x shc: strip outptu.sh.x shc: chmod ug=rwx,o=rx outptu.sh.x
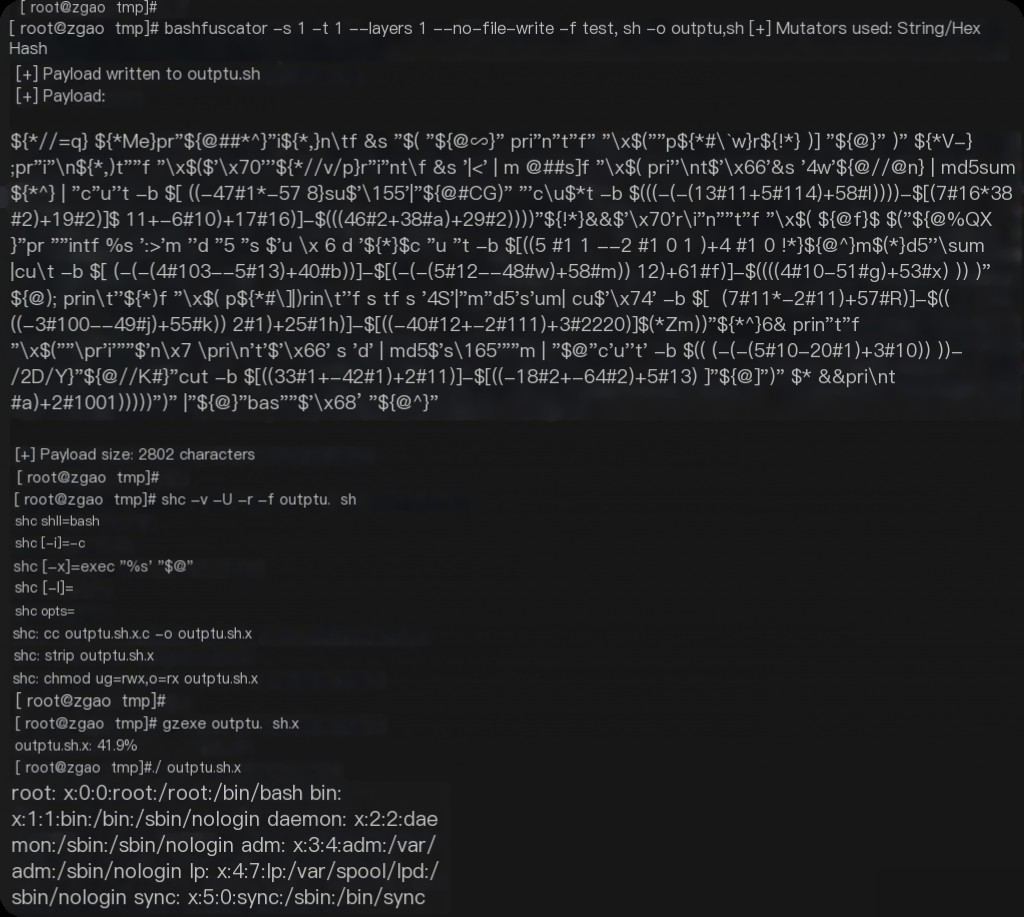
gzexe Compress shc Generated exe
The gzexe command, this command is built into the system. It is originally used to compress executable files, and the compressed file remains executable, automatically decompressing when executed. When you execute a compressed executable file, it automatically decompresses and continues to execute, just like using a regular executable file.
gzexe script.sh will back up the original unencrypted file as script.sh~, while script.sh becomes an encrypted file. gzexe -d script.sh will decrypt and restore the script, so it can only meet general encryption purposes.
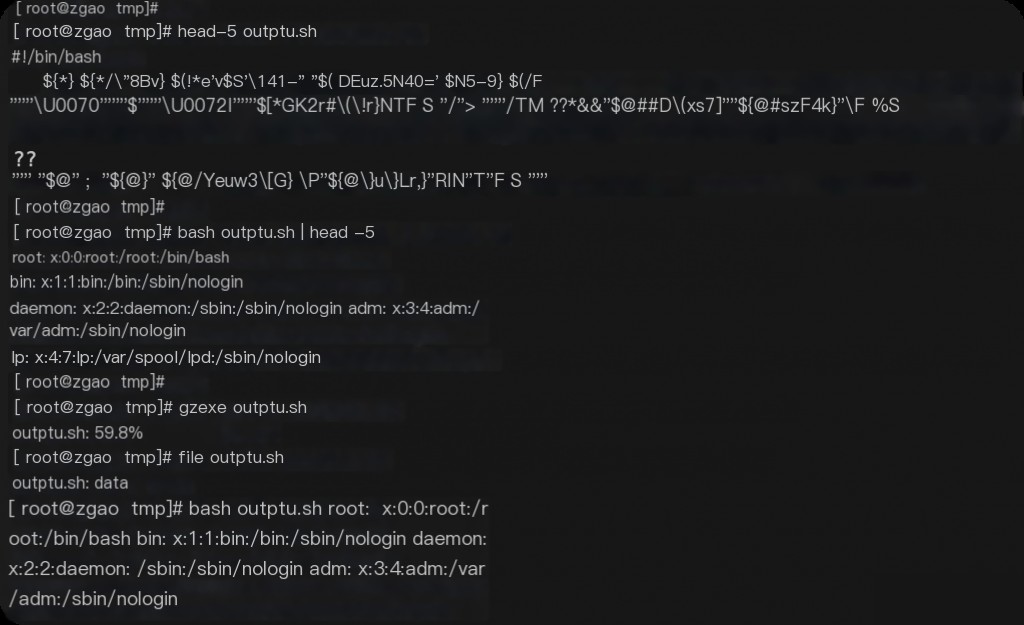
Here, gzexe is used to compress the exe file, further hiding the shell source code.


