In penetration testing, it is common to encounter apps with SSL certificate verification, which makes it impossible to capture packets. To bypass this, we need to hook the SSL pinning functions on iOS. This article demonstrates how to perform an SSL pinning bypass on a specific app using Frida and Objection.
Difficulty
★☆☆☆☆
Tools
- Jailbroken iOS 14.4
- AppsDump
- Frida
- Objection
- IDA 7.7
- HTTP Catcher
Analysis Approach
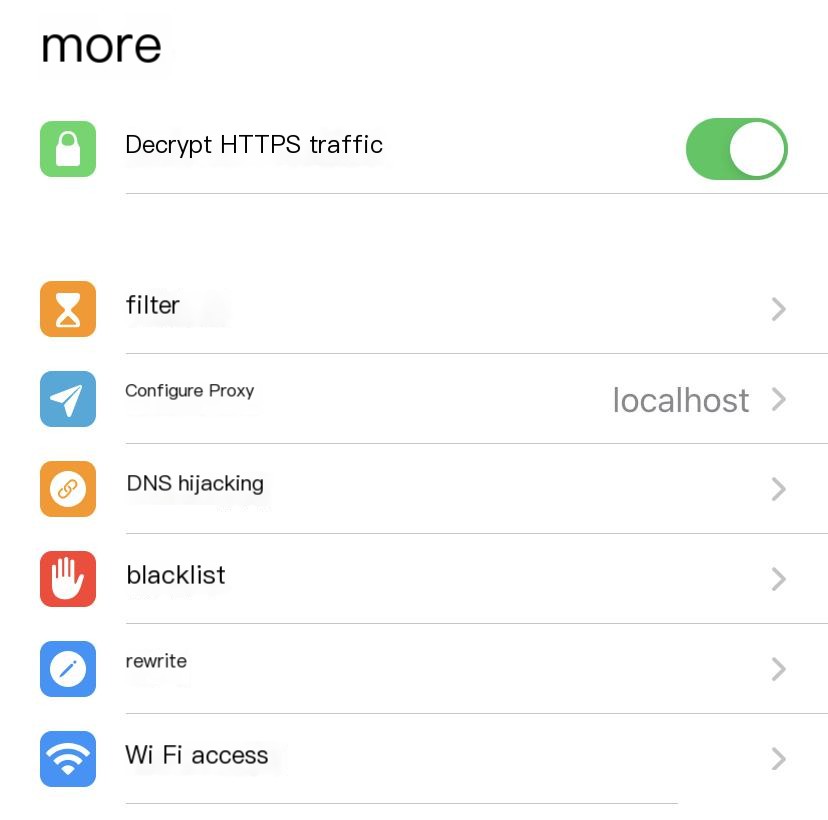
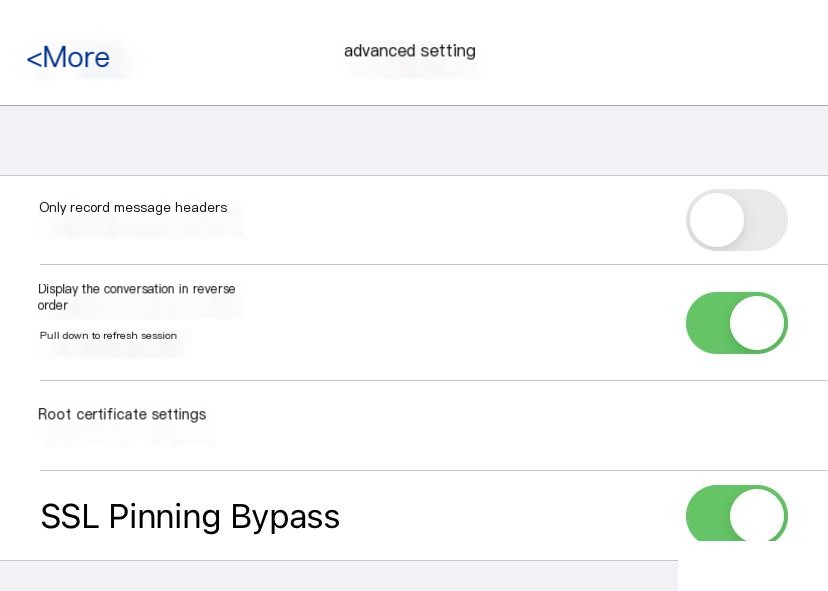
We use HTTP Catcher on iOS to capture packets. When SSL Pinning Bypass is enabled (proxy set to localhost), packets can be captured normally. However, for testing purposes, we need to capture traffic on Burp Suite on a Mac, where SSL Pinning Bypass does not work.
Knowing that it is a certificate verification issue, we can directly use an SSL Unpinning script to hook, but we will use IDA for a simple analysis to understand the principle.
Appsdump Shelling
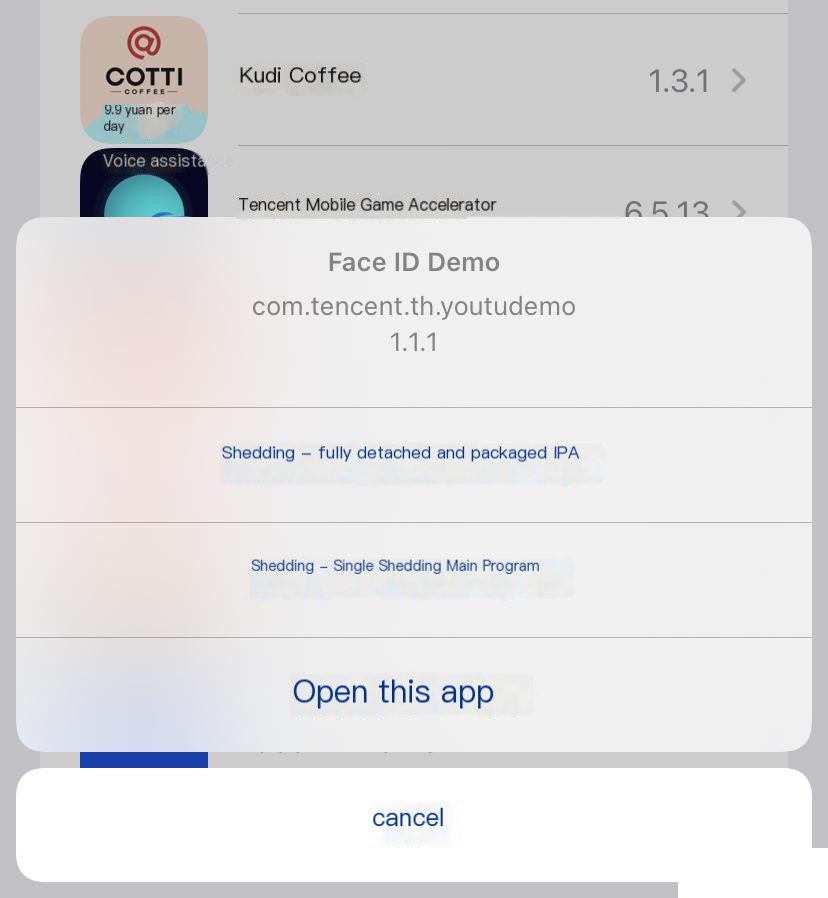
Recently, I discovered a very convenient app for shelling on iOS, Appsdump. It supports iOS 15 and is based on TrollStore for shelling. The key is that it can shell in a non-jailbroken state .
It supports single main program extraction, which can then be sent to a Mac via AirDrop, making it extremely convenient!
IDA Analysis Process
Since it is a certificate issue, after throwing the maco into IDA for analysis, we directly search for certificate-related keywords to locate the key functions.
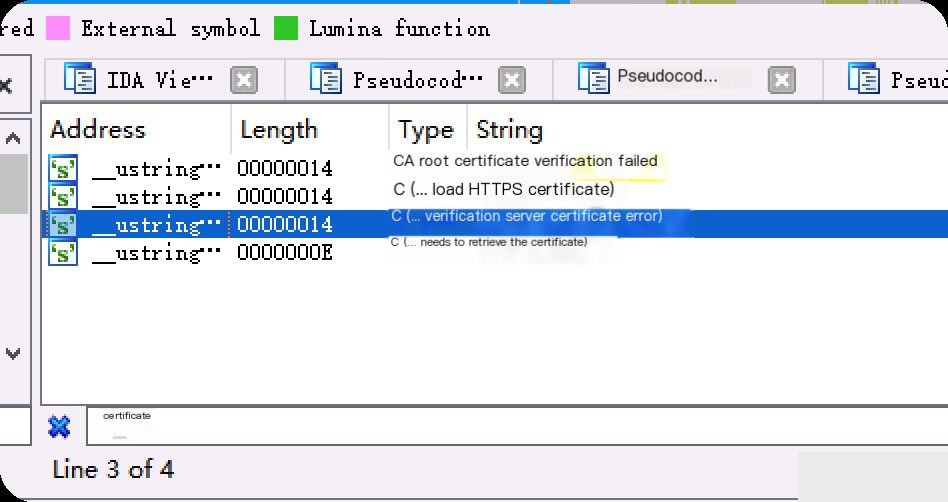
Double-click the string’s location.
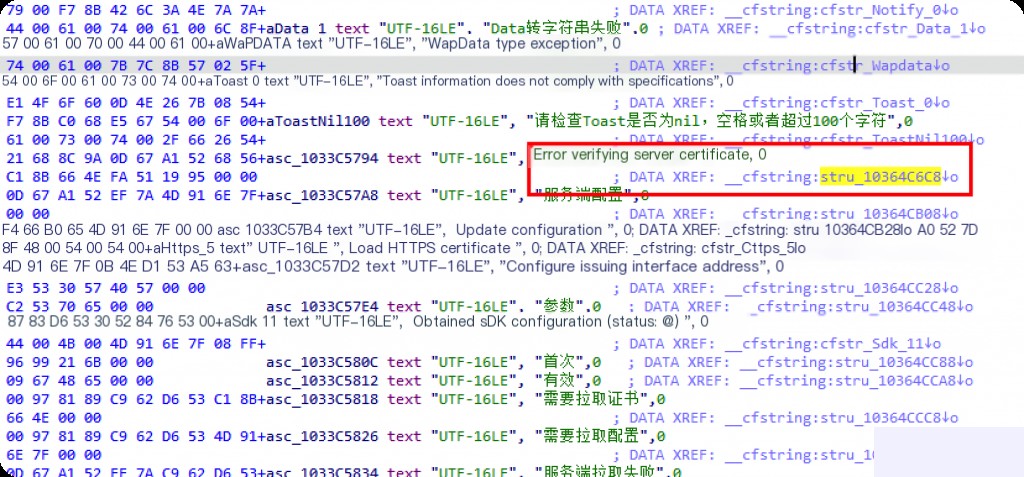
View the methods that reference this string.
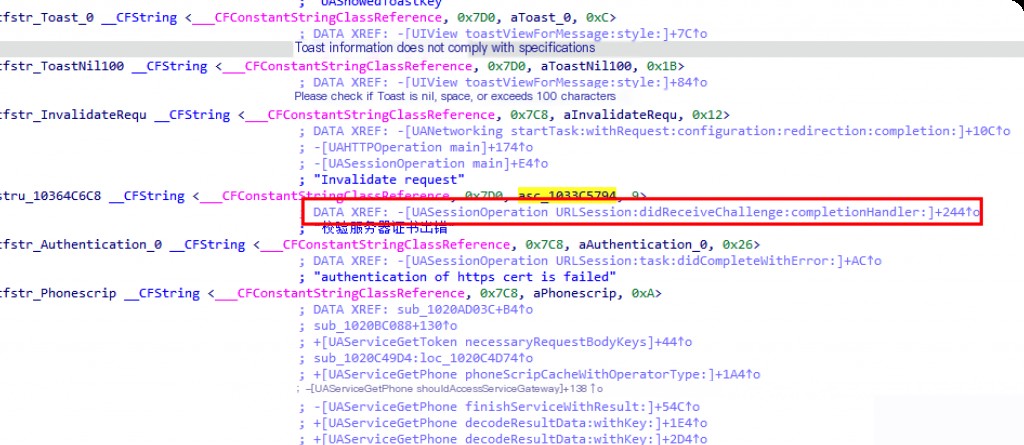
Navigate to the -[UASessionOperation URLSession:didReceiveChallenge:completionHandler:] method, and press F5.
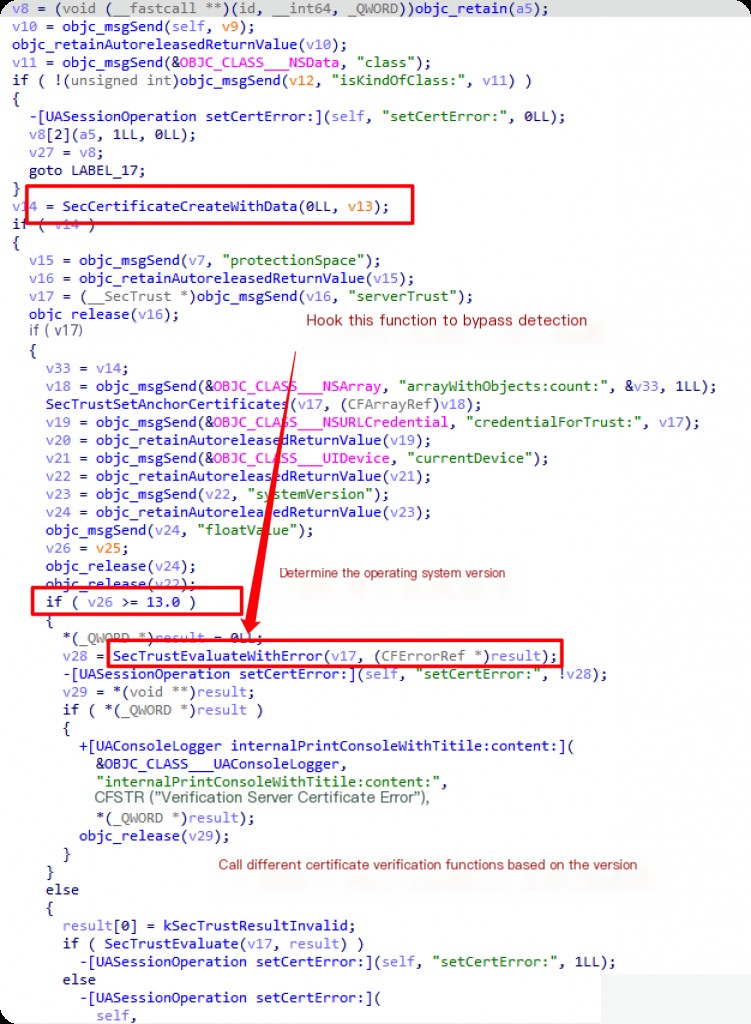
SecTrustEvaluateWithError is a system function on the iOS platform. This function comes from the Security.framework and is used to evaluate whether a SecTrust object can be trusted by the system.
This function returns a Boolean value. If true, the certificate can be trusted; if false, the certificate cannot be trusted. If the evaluation fails, a CFErrorRef object containing error details will be returned through the second parameter. This function is available on iOS 13.0 and later versions, so you can see a version check in the code that selects whether to use SecTrustEvaluateWithError or the older SecTrustEvaluate function based on the device’s system version.
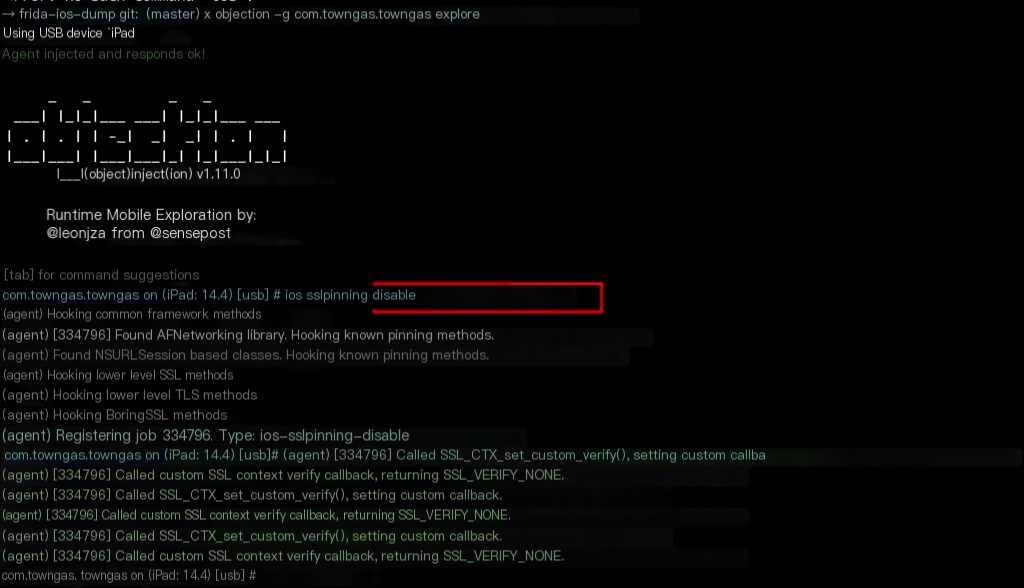
Objection iOS SSL Pinning Disable
Objection is a command-line hook tool based on Frida. It is very convenient to use without writing code.
objection -g explore ios sslpinning disable
Frida Bypass Script
There are many ready-made SSL Pinning bypass scripts available online, so there is no need to write one yourself. They generally hook the key system functions for SSL certificate verification, consistent with our analysis.
Save the above script as ssl-pinning-bypass.js file.
frida -UF -l ssl-pinning-bypass.js
The execution result is as follows:
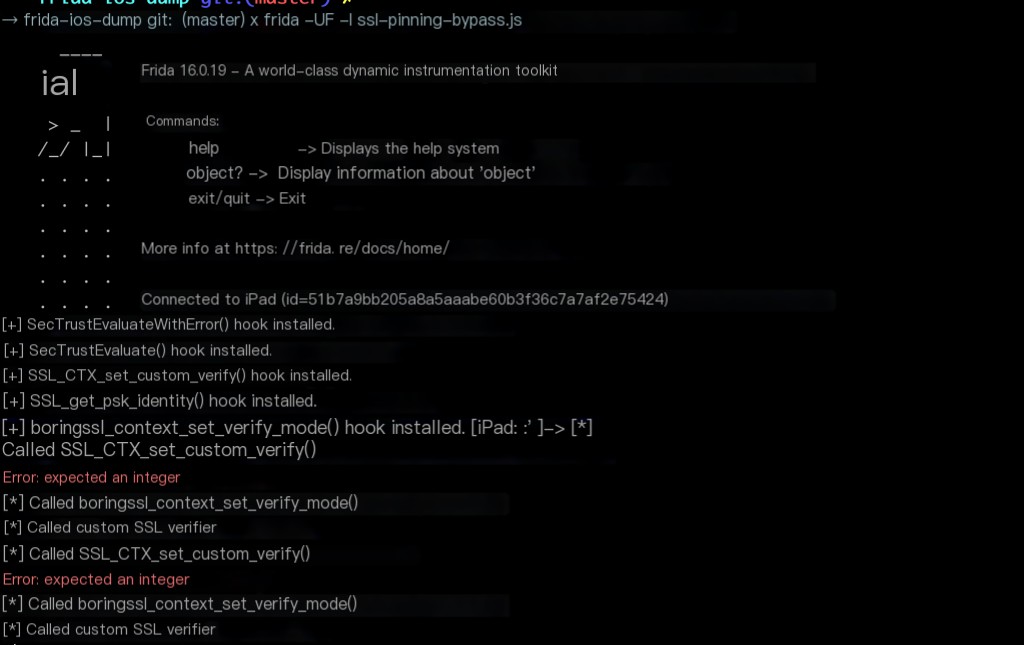
Then you can capture packets normally.


