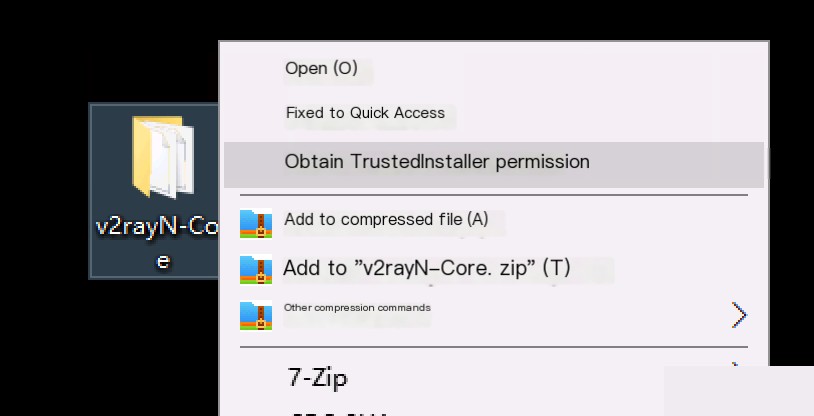
TrustedInstaller permissions are established in Windows Vista and later systems for system security purposes, providing the highest system permissions. (Permissions higher than SYSTEM and Administrator) My personal understanding: similar to Linux’s chattr permissions on files, even root cannot directly modify the files.
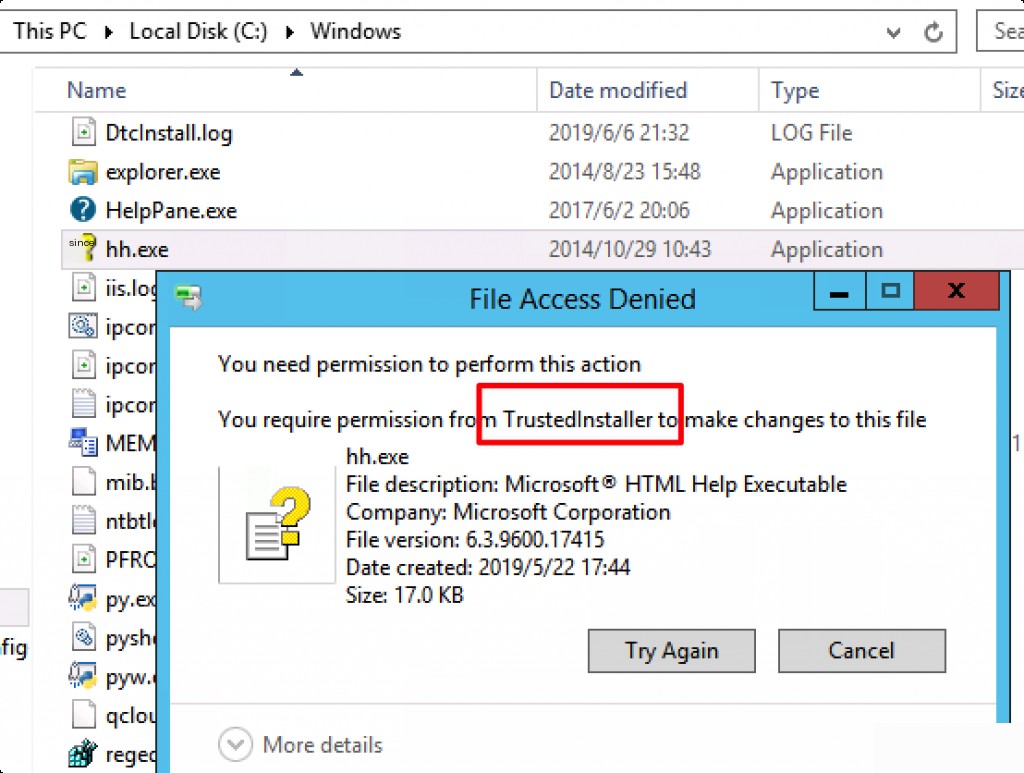
Manually Obtain Permissions
Right-click to get the properties of the file.
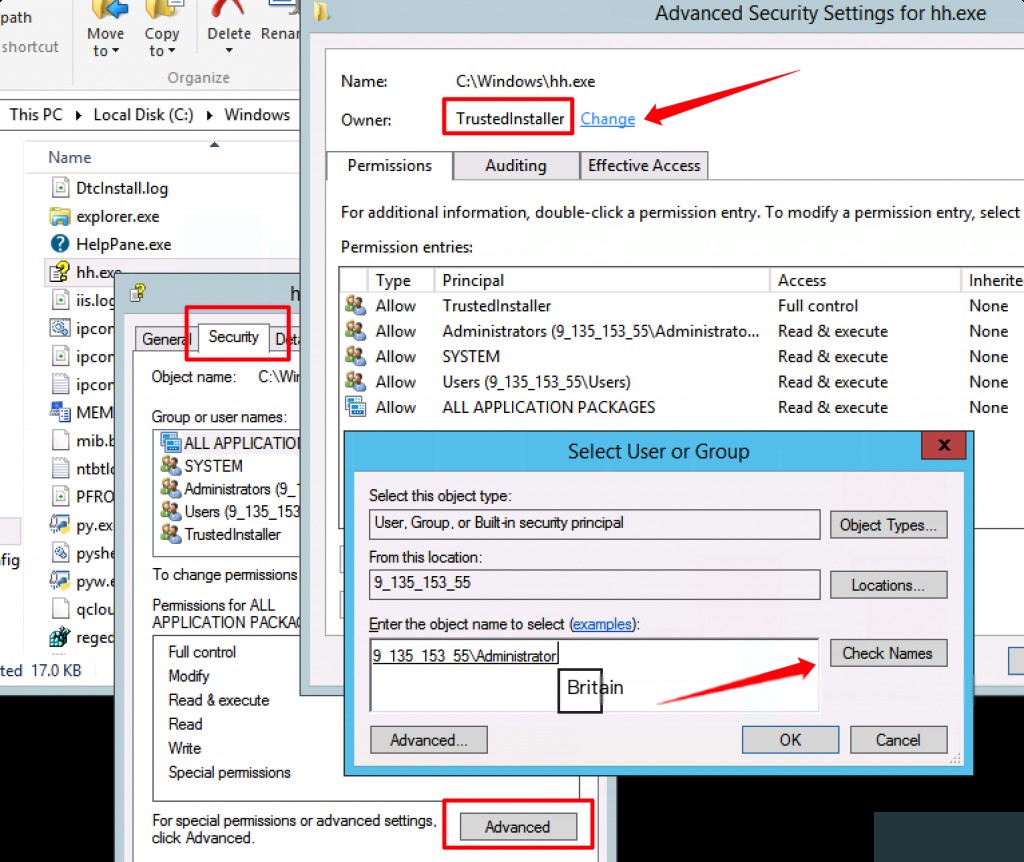
Enter the username here, in my case, it is Administrator. After entering, click Check Names to auto-complete.
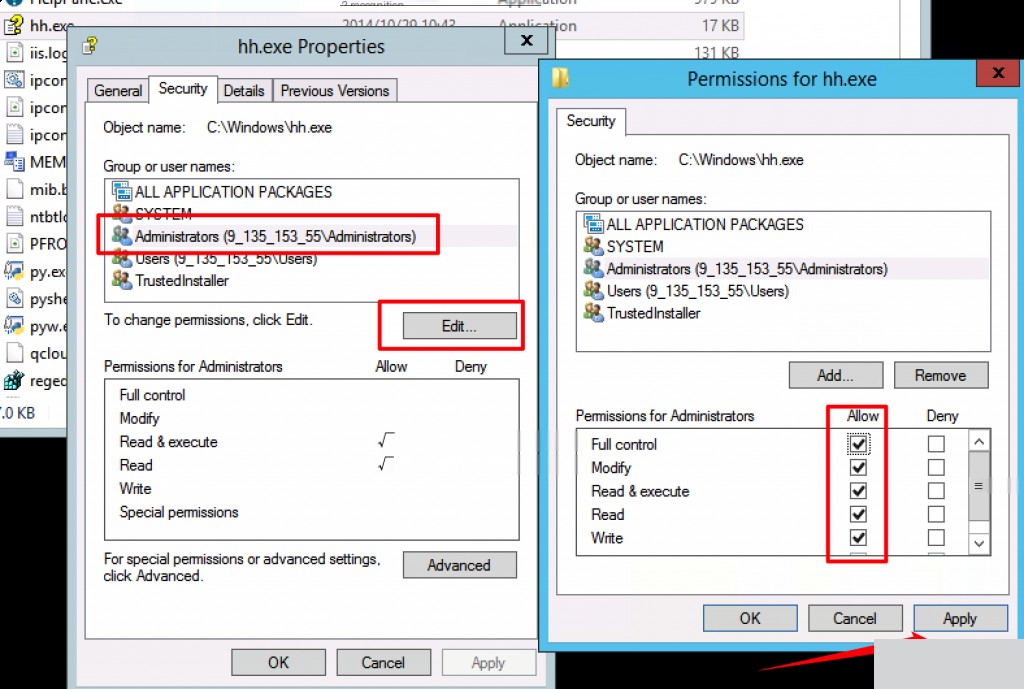
Note: On some systems, you may also need to check the “Replace owner on subcontainers and objects” option.
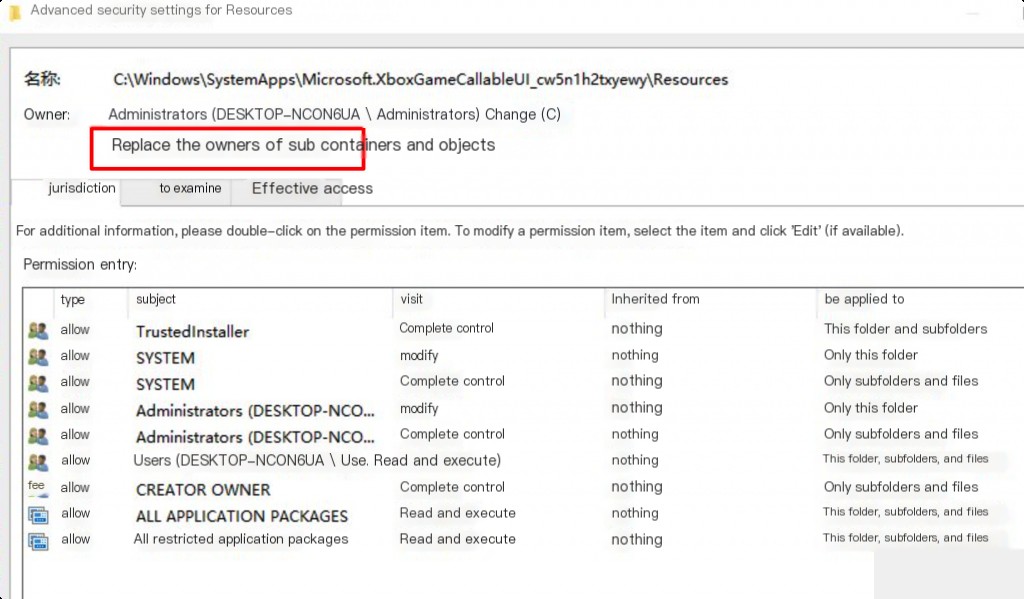
One-Click Obtain Permissions
Windows Registry Editor Version 5.00 [HKEY_CLASSES_ROOT\*\shell\runas] @="Obtain TrustedInstaller Permissions" [HKEY_CLASSES_ROOT\*\shell\runas\command] @="cmd.exe /c takeown /f \"%1\" && icacls \"%1\" /grant administrators:F" "IsolatedCommand"="cmd.exe /c takeown /f \"%1\" && icacls \"%1\" /grant administrators:F" [HKEY_CLASSES_ROOT\Directory\shell\runas] @="Obtain TrustedInstaller Permissions" "NoWorkingDirectory"="" [HKEY_CLASSES_ROOT\Directory\shell\runas\command] @="cmd.exe /c takeown /f \"%1\" /r /d y && icacls \"%1\" /grant administrators:F /t" "IsolatedCommand"="cmd.exe /c takeown /f \"%1\" /r /d y && icacls \"%1\" /grant administrators:F /t"
You can create a new txt file to save the above code, change the file extension to reg, and execute it. Alternatively, you can download and execute a ready-made script.
Click to download: TrustedInstaller.reg